Bscout: Direct Whole Patch Presence Test for Java Executables
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
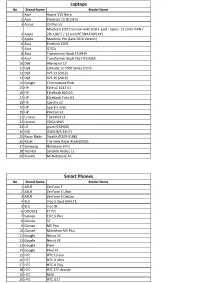
Type-C Compatible Device List 1.Xlsx
Laptops No Brand Name Model Name 1 Acer Aspire V15 Nitro 2 Acer Predator 15 (N15P3) 3 Aorus X3 Plus v5 MacBook (2015 version with USB-C port - Specs: 13.1mm THIN / 4 Apple 2lb. LIGHT / 12-inch RETINA DISPLAY) 5 Apple MacBook Pro (Late 2016 Version) 6 Asus EeeBook E202 7 Asus G752v 8 Asus Transformer Book T100HA 9 Asus Transformer Book Flip (TP200SA) 10 Dell Alienware 17 11 Dell Latitude 12 7000 Series (7275 12 Dell XPS 13 (2016) 13 Dell XPS 15 (2016) 14 Google Chromebook Pixel 15 HP Elite x2 1012 G1 16 HP EliteBook 840 G3 17 HP EliteBook Folio G1 18 HP Spectre x2 19 HP Spectre x360 20 HP Pavilion x2 21 Lenovo ThinkPad 13 22 Lenovo YOGA 900S 23 LG gram (15Z960) 24 MSI GS60 (MS-16H7) 25 Razer Blade Stealth (RZ09-0168) 26 Razer The New Razer Blade(2016) 27 Samsung Notebook 9 Pro 28 Toshiba Satellite Radius 12 29 Xiaomi Mi Notebook Air Smart Phones No Brand Name Model Name 1 ASUS ZenFone 3 2 ASUS ZenFone 3 Ultra 3 ASUS ZenFone 3 Deluxe 4 BLU Vivo 5 Dual SIM LTE 5 BLU Vivo XL 6 DOOGEE F7 Pro 7 Gionee Elife S Plus 8 Gionee S6 9 Gionee M5 Plus 10 Gionee Marathon M5 Plus 11 Google Nexus 5X 12 Google Nexus 6P 13 Google Pixel 14 Google Pixel XL 15 HTC HTC 10 evo 16 HTC HTC U Ultra 17 HTC HTC U Play 18 HTC HTC 10 Lifestyle 19 HTC M10 20 HTC HTC U11 21 Huawei Honor 22 Huawei Honor 8 23 Huawei Honor 9 24 Huawei Honor Magic 25 Huawei Hornor V9 26 Huawei Mate 9 27 Huawei Mate 9 Pro 28 Huawei Mate 9 Porsche Design 29 Huawei Nexus 6P 30 Huawei Nova2 31 Huawei P9 32 Huawei P10 33 Huawei P10 Plus 34 Huawei V8 35 Lenovo ZUK Z1(China) 36 Lenovo Zuk Z2 37 -

Statistics of Chinese SEP Cases in 2011-2019
Statistics of Chinese SEP Cases in 2011-2019 ZHAO Qishan, LU Zhe LexField Law Offices From 2011 to December 2019, Chinese courts accepted 160 cases related to SEPs. Most of the cases involve foreign entities and relate to the telecommunication industry. Most of the cases were filed with the courts in Beijing, Guangdong, Shanghai and Jiangsu. Most of the cases are patent infringement disputes, while cases asking the court to determine FRAND terms during license negotiations are also on the rise. This report includes a quantitative analysis from annual distribution, parties involved, geographic distribution of the courts, causes of action, adjudication progress and final outcomes, and also provides a particular summary of the SEP cases accepted in 2018 and 2019.1 From 2011 to 2019, Chinese courts have accepted over one hundred cases involving standard essential patents (“SEPs”) and Chinese judges have accumulated considerable judicial experience in hearing the cases. Aiming to provide a complete overview, this report analyzes information related to these SEP cases from various aspects based on the following methodology: (1) Scope of cases reviewed: The cases covered in the report are those accepted by civil courts in mainland China where the plaintiffs claimed or the defendants argued that the asserted patents were SEPs. Such cases are collectively referred to as "SEP cases" in this report. Cases that were withdrawn or dismissed due to the invalidation of asserted patents are also covered. (2) Time span: The cases included in the report are accepted by Chinese court from 2011 to December 2019. Since 2011, the number of Chinses SEP cases has gradually increased, and types of the cases have also become diversified. -

The Problem Faced and the Solution of Xiaomi Company in India
ISSN: 2278-3369 International Journal of Advances in Management and Economics Available online at: www.managementjournal.info RESEARCH ARTICLE The Problem Faced and the Solution of Xiaomi Company in India Li Kai-Sheng International Business School, Jinan University, Qianshan, Zhuhai, Guangdong, China. Abstract This paper mainly talked about the problem faced and the recommend solution of Xiaomi Company in India. The first two parts are introduction and why Xiaomi targeting at the India respectively. The third part is the three problems faced when Xiaomi operate on India, first is low brand awareness can’t attract consumes; second, lack of patent reserves and Standard Essential Patent which result in patent dispute; at last, the quality problems after-sales service problems which will influence the purchase intention and word of mouth. The fourth part analysis the cause of the problem by the SWOT analysis of Xiaomi. The fifth part is the decision criteria and alternative solutions for the problems proposed above. The last part has described the recommend solution, in short, firstly, make good use of original advantage and increase the advertising investment in spokesman and TV show; then, in long run, improve the its ability of research and development; next, increase the number of after-sales service staff and service centers, at the same, the quality of service; finally, train the local employee accept company’s culture, enhance the cross-culture management capability of managers, incentive different staff with different programs. Keywords: Cross-cultural Management, India, Mobile phone, Xiaomi. Introduction Xiaomi was founded in 2010 by serial faces different problem inevitably. -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,203 DEVICE PROFILES +1,528 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER COMMON/KNOWN HIGHLIGHTS System Images IMAGE FILTER ◼ Temporary root (ADB) solution for selected Android Focus on the relevant media files and devices running OS 4.3-5.1.1 – this capability enables file get to the evidence you need fast system and physical extraction methods and decoding from devices running OS 4.3-5.1.1 32-bit with ADB enabled. In addition, this capability enables extraction of apps data for logical extraction. This version EXTRACT DATA FROM BLOCKED APPS adds this capability for 110 devices and many more will First in the Industry – Access blocked application data with file be added in coming releases. system extraction ◼ Enhanced physical extraction while bypassing lock of 27 Samsung Android devices with APQ8084 chipset (Snapdragon 805), including Samsung Galaxy Note 4, Note Edge, and Note 4 Duos. This chipset was previously supported with UFED, but due to operating system EXCLUSIVE: UNIFY MULTIPLE EXTRACTIONS changes, this capability was temporarily unavailable. In the world of devices, operating system changes Merge multiple extractions in single unified report for more frequently, and thus, influence our support abilities. efficient investigations As our ongoing effort to continue to provide our customers with technological breakthroughs, Cellebrite Logical 10K items developed a new method to overcome this barrier. Physical 20K items 22K items ◼ File system and logical extraction and decoding support for iPhone SE Samsung Galaxy S7 and LG G5 devices. File System 15K items ◼ Physical extraction and decoding support for a new family of TomTom devices (including Go 1000 Point Trading, 4CQ01 Go 2505 Mm, 4CT50, 4CR52 Go Live 1015 and 4CS03 Go 2405). -

Technology 6 November 2017
INDUSTRY NOTE China | Technology 6 November 2017 Technology EQUITY RESEARCH China Summit Takeaway: AI, Semi, Smartphone Value Chain Key Takeaway We hosted several experts and 24 A/H corporates at our China Summit and Digital Disruption tour last week. Key takeaways: 1) AI shifting from central cloud to the edge (end devices), driving GPU/FPGA demand in near term, 2) AI leaders in China rolling out own ASICs in the next 2~3 years, 3) China's new role in semi, forging ahead in design and catching up in foundry. In smartphone value chain, maintain AAC as top pick for lens opportunity and Xiaomi strength. CHINA Artificial Intelligence - From cloud to edge computing: The rise of AI on the edge (terminal devices, like surveillance cameras, smartphones) from central cloud, can solve one key weakness of AI: the brains are located thousands of miles away from the applications. The benefits of AI on the edge include: 1) better analysis based on non-compressed raw data, which contains more information, 2) lower requirement on bandwidth, as transmitted data has been pre-processed, 3) faster response. This will keep driving the demands for GPUs and FPGAs in near term. Meanwhile, China's leading AI companies including Hikvision (002415 CH) and Unisound (private, leader in voice recognition) also noted they may develop own ASICs in the next 2~3 years, for better efficiency and low power. While machines getting smarter, we notice increasing concerns on data privacy. Governments are not only implementing Big Data laws and policies, also starts investing AI leaders, like Face ++ (computer vision) in China. -

Handset ODM Industry White Paper
Publication date: April 2020 Authors: Robin Li Lingling Peng Handset ODM Industry White Paper Smartphone ODM market continues to grow, duopoly Wingtech and Huaqin accelerate diversified layout Brought to you by Informa Tech Handset ODM Industry White Paper 01 Contents Handset ODM market review and outlook 2 Global smartphone market continued to decline in 2019 4 In the initial stage of 5G, China will continue to decline 6 Outsourcing strategies of the top 10 OEMs 9 ODM market structure and business model analysis 12 The top five mobile phone ODMs 16 Analysis of the top five ODMs 18 Appendix 29 © 2020 Omdia. All rights reserved. Unauthorized reproduction prohibited. Handset ODM Industry White Paper 02 Handset ODM market review and outlook In 2019, the global smartphone market shipped 1.38 billion units, down 2.2% year-over- year (YoY). The mature markets such as North America, South America, Western Europe, and China all declined. China’s market though is going through a transition period from 4G to 5G, and the shipments of mid- to high-end 4G smartphone models fell sharply in 2H19. China’s market shipped 361 million smartphones in 2019, a YoY decline of 7.6%. In the early stage of 5G switching, the operator's network coverage was insufficient. Consequently, 5G chipset restrictions led to excessive costs, and expectations of 5G led to short-term consumption suppression. The proportion of 5G smartphone shipments was relatively small while shipments of mid- to high-end 4G models declined sharply. The overall shipment of smartphones from Chinese mobile phone manufacturers reached 733 million units, an increase of 4.2% YoY. -
3D Time-Of-Flight Module in Meizu 17 Pro the First 3D Tof Camera from Samsung with Lumentum’S VCSEL
REVERSE COSTING® – STRUCTURAL, PROCESS & COST REPORT 3D Time-of-Flight Module in Meizu 17 Pro The first 3D ToF camera from Samsung with Lumentum’s VCSEL SP20571 - IMAGING report by Taha AYARI Laboratory analysis by Youssef EL GMILI November 2020 - Sample 22 bd Benoni Goullin 44200 NANTES - FRANCE +33 2 40 18 09 16 [email protected] www.systemplus.fr ©2020 by System Plus Consulting | SP20571 - 3D Time-o-Flight Module in Meizu 17 Pro | Sample 1 Table of Contents Overview / Introduction 4 Manufacturing Process 79 o Executive Summary o Global Overview o Reverse Costing Methodology o NIR Sensor Die Front-End Process & Fabrication Unit Company Profile 11 o NIR VCSEL Process Flow & Fabrication Unit o VCSEL Driver Die Front-End Process & Fabrication Unit Market Analysis 15 Cost Analysis 92 Physical Analysis 19 o Summary of the Cost Analysis o Summary of the Physical Analysis o Yields Explanation & Hypotheses o 3D Sensing System Assembly o NIR Camera Module ✓ Module Views ✓ Pixel Array, BSI & Optical Front-End Cost ✓ Module Opening ✓ NIR ToF Image Sensor Wafer & Die Cost ✓ System Cross-Section o Flood Illuminator Module o NIR Camera Module ✓ NIR VCSEL Front-End Cost ✓ Module Views & Dimensions ✓ NIR VCSEL Probe Test, Thinning & Dicing ✓ Module Cross-Section ✓ NIR VCSEL Die Wafer Cost o NIR CMOS Image Sensor ✓ Component Cost ✓ Die Overview & Dimensions o VCSEL Driver ✓ Die Process ✓ Front-End Cost ✓ Die Cross-Section ✓ Probe Test, Thinning & Dicing ✓ Die Process Characteristics ✓ Die Cost o Flood Illuminator ✓ Module Views & Dimensions o ToF Module ✓ Module Cross-Section ✓ Complete Module Cost ✓ Complete Module Price o NIR VCSEL Die ✓ Die Views & Dimensions Technical and Cost Comparison 121 ✓ Die Process o Meizu 17 Pro vs. -

Market Disruption Strategies: the Transformation of Xiaomi
Case Study Market Disruption Strategies: The Transformation of Xiaomi Source: Xiaomi 02/2021-6608 This case study was written by Haiyang Yang, Associate Professor of Marketing at the Johns Hopkins Carey Business School, Johns Hopkins University; Jingjing Ma, Assistant Professor of Marketing at the National School of Development, Peking University; Neal Roese, the SC Johnson Chair in Global Marketing at the Kellogg School of Management, Northwestern University; and Amitava Chattopadhyay, the GlaxoSmithKline Chaired Professor of Corporate Innovation at INSEAD. The case is intended to be used as a basis for class discussion rather than to illustrate either effective or ineffective handling of an administrative situation. The authors thank LEI Jun (Cofounder, Chairman and CEO), WANG Xiang (President), LIU De (Cofounder, Senior VP), CHEW Shou Zi (Senior VP, President of Internationalization), ZHANG Jianhui (Vice President of Xiaomi China), LI Weixing (Vice Chairman of Technology Committee), XU Jieyun (General Manager of Public Relations), YAO Liang (General Manager of Marketing) and ZHANG Huan (Director of Public Relations) of Xiaomi, as well as SU Jun (Founder and CEO) of Smartmi for their help during the development of this case. Extra teaching materials are available at https://publishing.insead.edu/case/xiaomi Copyright © 2021 INSEAD COPIES MAY NOT BE MADE WITHOUT PERMISSION. NO PART OF THIS PUBLICATION MAY BE COPIED, STORED, TRANSMITTED, TRANSLATED, REPRODUCED OR DISTRIBUTED IN ANY FORM OR MEDIUM WHATSOEVER WITHOUT THE PERMISSION OF THE COPYRIGHT OWNER. Introduction Despite numerous long meetings, executives at Xiaomi were still agonizing over what to do to reignite the brand’s growth in China. Although Xiaomi had achieved unprecedented success in launching and marketing smartphones a few years earlier, its market share had since stagnated and then declined. -

Android Supported Devices
Android Supported Devices Mobile Track Call Notifications Call Notifications Text Notifications Music Control Make Model OS Required Requires Google Play Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.4+ Services (Charge, Charge HR) (Surge) (Surge) (Surge) Samsung Galaxy S3 — ✓ ✓ ✓ — Galaxy S3 Mini (excluding Samsung — — “Value Edition” GT-i8200) ✓ ✓ ✓ Samsung Galaxy S4 — ✓ ✓ ✓ ✓ Samsung Galaxy S4 mini — ✓ ✓ ✓ ✓ Samsung Galaxy S4 Active — ✓ ✓ ✓ ✓ Samsung Galaxy S4 Zoom — ✓ ✓ ✓ ✓ Samsung Galaxy S5 — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Mini — ✓ ✓ ✓ ✓ Samsung Galaxy S6 — ✓ ✓ ✓ ✓ Samsung Galaxy S6 Edge — ✓ ✓ ✓ ✓ Samsung Galaxy Note II — ✓ ✓ ✓ ✓ Samsung Galaxy Note II Duos — ✓ ✓ ✓ ✓ Samsung Galaxy Young 2 Duos — ✓ ✓ ✓ ✓ Samsung Galaxy Note III — ✓ ✓ ✓ ✓ Samsung Galaxy Note III Round — ✓ ✓ ✓ ✓ Samsung Galaxy Note 4 — ✓ ✓ ✓ ✓ Samsung Galaxy Note Edge — ✓ ✓ ✓ ✓ Samsung Galaxy Note 8.0 — ✓ ✓ ✓ ✓ Samsung Galaxy Note 10.1 — ✓ ✓ ✓ ✓ Samsung Galaxy Rugby Pro — ✓ ✓ ✓ ✓ Samsung Galaxy Mega — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Active — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Sport — ✓ ✓ ✓ ✓ Fitbit | Android Supported Devices Page 1 of 7 Android Supported Devices Mobile Track Call Notifications Call Notifications Text Notifications Music Control Make Model OS Required Requires Google Play Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.4+ Services (Charge, Charge HR) (Surge) (Surge) (Surge) Samsung Galaxy S3 Neo — ✓ ✓ ✓ — Samsung Galaxy S3 Slim — ✓ ✓ ✓ — Samsung Galaxy Ace Style — ✓ ✓ ✓ ✓ Samsung Galaxy Tab 3 — ✓ ✓ ✓ ✓ Samsung Galaxy Tab S — ✓ ✓ ✓ ✓ -

DAIICHI 846 263.Xlsx
No. Equipment models/ Brand system version 1 APPLE iPhone 6s (A1700) 2 SAMSUNG S8+ 3 SONY xperia z3 compact 4 LG NEXUS4 5 LG NEXUS5 6 SONY XPERIA XA ULTRA 7 APPLE iPhone 6P(A1524) 8 NOKIA Nokia3 9 MOTOLOLA NEXUS6 10 APPLE iPhone 8 11 APPLE iPhone 6(A1589) 12 APPLE iPhone 5s 13 LG v20 15 HUAWEI NEXUS6P 16 APPLE iPhone7 17 APPLE iPhoneSE 18 APPLE iPhone 6s plus 19 HUAWEI P20 lite 20 GOOGLE pixel 21 GOOGLE pixel2 22 HTC D610T 23 ipod touch A1509 24 HUAWEI 6X 25 APPLE A1431 26 HUAWEI Mate 8(HUAWEI NXT-AL10) 27 LG LG-H791(nexus5X) 28 HUAWEI MHA-AL00(Mate 9) 29 ZTE BA520 30 OPPO A31t 31 LENOVO A320t 32 OPPO A33 34 VIVO Y51A 35 Coolpad Coolpad 8737 36 SAMSUNG SM-G3509 37 VIVO Y31 38 XIAOMI Redmi Note 4X 39 HUAWEI FRD-DL00 40 SAMSUNG Galaxy S7 41 APPLE Iphone 6(64G) 42 APPLE Iphone SE(64G) 43 HUAWEI WAS-AL00 44 HUAWEI H60-L01(Honor6) 45 HUAWEI C8817D(Honor4) 46 vivo Y937 47 SONY Xperia Z3(L55u) 48 APPLE A1529 49 XIAOMI Redmi note2 50 SAMSUNG SM-G9008W 51 Smartisan YQ601 52 SAMSUNG S6(SM-G9250) 53 SAMSUNG S6(SM-G920P) 54 HUAWEI HUAWEI G750-T00 55 SAMSUNG SM-N9008 56 NOKIA 1520 58 HUAWEI P7-L00 59 ZTE ZTE S2002 60 SAMSUNG SM-N7506V 61 HTC HTC M8St 62 HUAWEI Honor X1(7D-503L) 63 LG Nexus 5 64 SAMSUNG GT-I9300 65 APPLE iphone5 66 HUAWEI Honor 7i (ATH-AL00) 67 MEIZU note2 68 HUAWEI Mate7-TL00 69 Leshi Letv X800+ 70 KONKA L550 71 Hisense H910 72 XIAOMI Mi 4(2G) 73 OPPO OPPO X9007 74 HONOR H30-T00 75 VIVO vivo X3S W 76 SAMSUNG SPH-D710 77 SAMSUNG SM-G3818 78 SAMSUNG GT-I8552 79 HTC HTC Z520 80 SAMSUNG I997 81 SAMSUNG 9100 82 SAMSUNG I9500 83 MEIZU MXM032 -

Meizu-17-Pro-Msmart-5G-Phone-8GB-128GB Datasheet
Meizu-17-Pro-mSmart-5G-Phone-8GB-128GB Datasheet Get a Quote Overview Meizu 17 Pro mSmart 5G Phone 8GB+128GB, Meizu 5G Phone, 6.6-inch 90Hz custom Samsung AMOLED display, premium ceramic body; Qualcomm Snapdragon 865 Octa-core processor, Adreno 650 GPU; Sony IMX686 64MP+8MP+32MP+0.3MP 3D depth-sensing five rear cameras, a 20.0MP front camera. Quick Spec Table 1 shows the Quick Specs. Product Code Meizu 17 Pro mSmart 5G Phone 8GB+128GB Operating System Flyme 8.1 UI OS base on Android 10 OS Network GSM, WCDMA, TD-LTE, LTE-FDD, SA & NSA Dual 5G Mode, Wi-Fi 6 Band 5G: N41/N78/N79; 2G GSM: B2/B3/B8; 3G WCDMA: B1/B2/B5/B8, FDD-LTE: B1/B3/B5/B7/B8; TD- LTE: B34/B39/B40/B41 Carrier Unlocked Google Play Yes Screen 6.6 inch Super AMOLED screen, 90Hz punch-hole FHD+ display, a 19.5:9 aspect ratio and 92.2% screen to body ratio, premium ceramic body Processor CPU: 7nm+ Qualcomm Snapdragon 865 Octa-Core processor, Adreno 650 GPU Product Details Meizu 17 Pro mSmart 5G Phone provides these features: * Flyme 8.1 Based on Android 10 OS Installs Flyme 8.1 OS base on Android 10 operating system, allows you to stay connected and productive on the go. * Multi-Language Support Support English, Simplified / Traditional Chinese, German, Turkish, Dutch, Italian, Spanish, Portuguese, French, Croatian, Czech, Romanian, Polish, Russian, Greek Indonesian, Malay, Thai, Urdu, Vietnamese, Arabic, Bengali, Khmer, Burmese, Hungarian, Finnish, Slovak, Slovenian and more. * 6.6-inch Super AMOLED 90Hz FHD+ Screen Meizu 17 Pro features custom Samsung AMOLED display with a 19.5:9 aspect ratio and 92.2% screen to body ratio. -

Supported Devices Epihunter Companion App
Supported devices epihunter companion app Manufacturer Model Name RAM (TotalMem) Ascom Wireless Solutions Ascom Myco 3 1000-3838MB Ascom Wireless Solutions Ascom Myco 3 1000-3838MB Lanix ilium Pad E7 1000MB RCA RLTP5573 1000MB Clementoni Clempad HR Plus 1001MB Clementoni My First Clempad HR Plus 1001MB Clementoni Clempad 5.0 XL 1001MB Auchan S3T10IN 1002MB Auchan QILIVE 1002MB Danew Dslide1014 1002MB Dragontouch Y88X Plus 1002MB Ematic PBS Kids PlayPad 1002MB Ematic EGQ347 1002MB Ematic EGQ223 1002MB Ematic EGQ178 1002MB Ematic FunTab 3 1002MB ESI Enterprises Trinity T101 1002MB ESI Enterprises Trinity T900 1002MB ESI Enterprises DT101Bv51 1002MB iGet S100 1002MB iRulu X40 1002MB iRulu X37 1002MB iRulu X47 1002MB Klipad SMART_I745 1002MB Lexibook LexiTab 10'' 1002MB Logicom LEMENTTAB1042 1002MB Logicom M bot tab 100 1002MB Logicom L-EMENTTAB1042 1002MB Logicom M bot tab 70 1002MB Logicom M bot tab 101 1002MB Logicom L-EMENT TAB 744P 1002MB Memorex MTAB-07530A 1002MB Plaisio Turbo-X Twister 1002MB Plaisio Coral II 1002MB Positivo BGH 7Di-A 1002MB Positivo BGH BGH Y210 1002MB Prestigio MULTIPAD WIZE 3027 1002MB Prestigio MULTIPAD WIZE 3111 1002MB Spectralink 8744 1002MB USA111 IRULU X11 1002MB Vaxcare VAX114 1002MB Vestel V Tab 7010 1002MB Visual Land Prestige Elite9QL 1002MB Visual Land Prestige Elite8QL 1002MB Visual Land Prestige Elite10QS 1002MB Visual Land Prestige Elite10QL 1002MB Visual Land Prestige Elite7QS 1002MB Dragontouch X10 1003MB Visual Land Prestige Prime10ES 1003MB iRulu X67 1020MB TuCEL TC504B 1020MB Blackview A60 1023MB