Stealthwatch V7.3 Default Application Definitions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

FCC-06-11A1.Pdf
Federal Communications Commission FCC 06-11 Before the FEDERAL COMMUNICATIONS COMMISSION WASHINGTON, D.C. 20554 In the Matter of ) ) Annual Assessment of the Status of Competition ) MB Docket No. 05-255 in the Market for the Delivery of Video ) Programming ) TWELFTH ANNUAL REPORT Adopted: February 10, 2006 Released: March 3, 2006 Comment Date: April 3, 2006 Reply Comment Date: April 18, 2006 By the Commission: Chairman Martin, Commissioners Copps, Adelstein, and Tate issuing separate statements. TABLE OF CONTENTS Heading Paragraph # I. INTRODUCTION.................................................................................................................................. 1 A. Scope of this Report......................................................................................................................... 2 B. Summary.......................................................................................................................................... 4 1. The Current State of Competition: 2005 ................................................................................... 4 2. General Findings ....................................................................................................................... 6 3. Specific Findings....................................................................................................................... 8 II. COMPETITORS IN THE MARKET FOR THE DELIVERY OF VIDEO PROGRAMMING ......... 27 A. Cable Television Service .............................................................................................................. -

Facebook Response to the ACCC's Digital Platform Services Inquiry
Facebook response to the ACCC’s Digital Platform Services Inquiry September 2020 Interim Report 8 March 2021 Executive Summary The growth in the use of messaging apps (private messaging services as referred to in the Digital Platform Services Inquiry (D SPI) Interim Report September 2020 (I nterim Report )) has been one of the key trends of the digital ecosystem in recent years, and this has accelerated during the COVID 19 pandemic as many families, friends and workplaces have used small group conversations and direct messaging to stay in touch. Many different competitive solutions have been developed to respond to this consumer demand - whether it is pre-installed and default messaging apps like iMessage and Android Messages which also have exclusive access to support SMS as well as their own proprietary protocols (along with similar device maker SMS solutions); the wide variety of downloadable apps offering messaging services such as Facebook Messenger, WhatsApp, Telegram, Signal, Snapchat, Discord, TikTok, Twitch or Google Chat (among others); or enterprise platforms such as Slack, Teams and Google Hangouts. Given the important role that messaging apps play in keeping Australian households connected and work colleagues productive, the inquiry as part of the DPSI by the Australian Competition and Consumer Commission ( ACCC ) into private messaging is timely. Following the release of the Interim Report, Facebook provides this submission in order to set forth its concerns with the conclusions reached in the Interim Report. In the Interim Report, the ACCC finds that Facebook’s online private messaging services (Facebook Messenger and WhatsApp) are not “competitively constrained” by other private messaging services, implying that - even though there is a broad array of competing private messaging services - they do not provide effective competition against Facebook’s services. -

TV Universe—UK, Germany, Sweden: HOW PEOPLE WATCH TELEVISION TODAY Author: Colin Dixon, Founder and Chief Analyst, Nscreenmedia | 2019
TV Universe—UK, Germany, Sweden: HOW PEOPLE WATCH TELEVISION TODAY Author: Colin Dixon, Founder and Chief Analyst, nScreenMedia | 2019 I NTRODUCTION Technology has become such a part of our daily lives that sometimes it seems that it is an end unto itself. However, in the world of the consumer, it has a particular role to play. Tim O’Reilly, who coined the term “open source,” put Online TV is now the second it this way: most popular source of “What technology does is create new opportunities to do a job that customers want done.”1 Home entertainment is most certainly a job that people “want done.” Ninety years ago, broadcast television television content in the UK, technology was the new opportunity to deliver it in an entirely new way.2 Based on the data from our most recent survey in Europe, the internet has become the next new opportunity to provide television entertainment to the home. Germany, and Sweden. Today, there are three primary sources of TV entertainment available to consumers: free-to-air (FTA), pay TV, and online TV. Free-to-air TV channels are typically received via an antenna but can also arrive over satellite and cable. Examples include BBC1, SVT1, and Das Erste. Pay TV services distribute linear TV over cable, satellite, and telco TV systems. Examples include Virgin Media, Sky Deutschland, and Com Hem. Online TV allows viewers to stream or download shows and movies over mobile and broadband data networks. Examples of services include Netflix, Now TV, and Amazon Prime Video. Just twelve years after Netflix first introduced streaming services, online TV has become the second most popular TV source in the UK, Germany, and Sweden. -

OTT and Related On-Line Services in Arab Region
OTT and related on-line services in Arab Region Release 1.1 31/01/2017 Reality of OTTs in Arab Region The objective of the study is: 1- to have a global view on OTT and on-line services worldwide with the impact and trends of these services on national players and economies, 2- to have an overview on associated practices and relevant public policies worldwide and in the Region, 3- to propose recommendations on methods and approaches for preparation of associated policies and frameworks. _____________________________ The present document is the first release of the report. A draft questionnaire is proposed with this release and is intended to be submittedfor a survey to Regulators/policy Makers and Operators in the Region. The outcome of the survey with the related findings will be commented and included in a next version of this report. It is to note that, as the subject of OTT is being regularly debated in almost all regions with potential move and change in the related positions and decisions, some information reported in the present report may become outdated. __________________________________________________________________ OTT and related on-line services in Arab Region Executive Summary With the increase of global mobile broadband penetration, as well as the rapid adoption of connected devices, consumers have been provided with an access to a wide variety of on-line services which go beyond the traditional voice and messaging services provided by telecom operators (alias telcos *). These on-line services are reshaping the entire telecommunication eco-system, and are of great benefit to consumers worldwide, to the global economy and ubiquitous connectivity. -

An Investigation Into the Security and Privacy of Ios VPN Applications
An Investigation Into the Security and Privacy of iOS VPN Applications Jack Wilson Division of Cybersecurity School of Design and Informatics Abertay University, Dundee A thesis submitted for the degree of Bachelor of Science with Honours in Ethical Hacking 1st May 2018 Word Count: 11,448 Abstract Due to the increasing number of recommendations for people to use VPN’s for privacy reasons, more app developers are creating VPN apps and publishing them on the Apple App Store and Google Play Store. In this ‘gold rush’, apps are being developed quickly and, in turn, not being developed with security fully in mind. This paper investigated a selection of free VPN applications available on the Apple App Store (for iOS devices) and test the apps for security and privacy. This includes testing for any traffic being transmitted over plain HTTP, DNS leakage and transmission of personally-identifiable information (such as phone number, IMEI 1, email address, MAC address) and evaluating the security of the tunnelling protocol used by the VPN. The testing methodology involved installing free VPN apps on a test device (an iPhone 6 running iOS 11), simulating network traffic for a pre-defined period of time and capturing the traffic (either through ARP spoofing, or through a proxy program such as Burpsuite). This allows for all traffic to be analysed to check for anything being sent without encryption. Other issues that often cause de-anonymisation with VPN applications such as DNS leakage can be tested using websites such as dnsleaktest.com. The research found several common security issues with the VPN applications that were tested, with a large majority of the applications tested failing to implement HTTPS. -

Foxtel Partners with Brightcove to Live Stream Mayweather-Mcgregor Main Event
August 25, 2017 Foxtel Partners With Brightcove to Live Stream Mayweather-McGregor Main Event Biggest boxing bout of the year to be available to non-Foxtel subscribers SYDNEY--(BUSINESS WIRE)-- Ahead of the biggest boxing bout of the year and one of the most anticipated fights in the history of the sport, Foxtel has partnered with Brightcove Inc. (NASDAQ: BCOV), the leading provider of cloud services for video, to livestream the Floyd Mayweather vs. Conor McGregor fight on August 27 (AEST). In addition to being able to watch the Pay-Per-View event at home, or at licensed venues, all Australian viewers can also subscribe to and stream the fight online. The offering will complement Foxtel's existing Main Event service available over cable/satellite and in licensed venues. The announcement follows a soft launch of the online offering last month, with Foxtel live streaming Jeff Horn's victory match over Manny Pacquiao to thousands of Australians. Ed Follows, Director of Product Technology Development at Foxtel, commented, "In recent years, we've focused our efforts on finding new ways to increase customer choices, and effortlessly give customers access to our content. This is another way we're doing just that. Previously, Main Event content like this has only been available to Foxtel customers. But with the dedicated online experience, anyone can sign up, buy a ticket and immediately watch the fight, with no ongoing subscription required. It means more Australians can subscribe to ground-breaking bouts like this than ever before." "Brightcove has been a fantastic partner, managing the entire process and bringing some key partners into the mix that make this all possible," Follows said. -

List of Brands
Global Consumer 2019 List of Brands Table of Contents 1. Digital music 2 2. Video-on-Demand 4 3. Video game stores 7 4. Digital video games shops 11 5. Video game streaming services 13 6. Book stores 15 7. eBook shops 19 8. Daily newspapers 22 9. Online newspapers 26 10. Magazines & weekly newspapers 30 11. Online magazines 34 12. Smartphones 38 13. Mobile carriers 39 14. Internet providers 42 15. Cable & satellite TV provider 46 16. Refrigerators 49 17. Washing machines 51 18. TVs 53 19. Speakers 55 20. Headphones 57 21. Laptops 59 22. Tablets 61 23. Desktop PC 63 24. Smart home 65 25. Smart speaker 67 26. Wearables 68 27. Fitness and health apps 70 28. Messenger services 73 29. Social networks 75 30. eCommerce 77 31. Search Engines 81 32. Online hotels & accommodation 82 33. Online flight portals 85 34. Airlines 88 35. Online package holiday portals 91 36. Online car rental provider 94 37. Online car sharing 96 38. Online ride sharing 98 39. Grocery stores 100 40. Banks 104 41. Online payment 108 42. Mobile payment 111 43. Liability insurance 114 44. Online dating services 117 45. Online event ticket provider 119 46. Food & restaurant delivery 122 47. Grocery delivery 125 48. Car Makes 129 Statista GmbH Johannes-Brahms-Platz 1 20355 Hamburg Tel. +49 40 2848 41 0 Fax +49 40 2848 41 999 [email protected] www.statista.com Steuernummer: 48/760/00518 Amtsgericht Köln: HRB 87129 Geschäftsführung: Dr. Friedrich Schwandt, Tim Kröger Commerzbank AG IBAN: DE60 2004 0000 0631 5915 00 BIC: COBADEFFXXX Umsatzsteuer-ID: DE 258551386 1. -
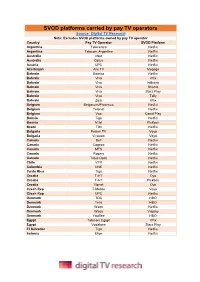
SVOD Platforms Carried by Pay TV Operators
SVOD platforms carried by pay TV operators Source: Digital TV Research Note: Excludes SVOD platforms owned by pay TV operator Country Pay TV Operator SVOD Platform Argentina Telecentro Netflix Argentina Telecom Argentina Netflix Australia iiNet Netflix Australia Optus Netflix Austria UPC Netflix Azerbaijan Aile TV Megogo Bahrain Batelco Netflix Bahrain Viva Icflix Bahrain Viva Istikana Bahrain Viva Shahid Bahrain Viva Starz Play Bahrain Viva Telly Bahrain Zain Icflix Belgium Belgacom/Proximus Netflix Belgium Telenet Netflix Belgium Voo Canal Play Bolivia Tigo Netflix Bosnia M:tel Pickbox Brazil TIM Netflix Bulgaria Fusion TV Voyo Bulgaria Vivacom Voyo Canada Bell Netflix Canada Cogeco Netflix Canada MTS Netflix Canada Rogers Netflix Canada Telus Optik Netflix Chile VTR Netflix Colombia UNE Netflix Costa Rica Tigo Netflix Croatia T-HT Oyo Croatia T-HT Pickbox Croatia Vipnet Oyo Czech Rep T-Mobile Voyo Czech Rep UPC Netflix Denmark TDC HBO Denmark Telia HBO Denmark Waoo Netflix Denmark Waoo Viaplay Denmark YouSee HBO Egypt Telecom Egypt Icflix Egypt Vodafone Starz Play El Salvador Tigo Netflix Estonia Elion Netflix SVOD platforms carried by pay TV operators Source: Digital TV Research Note: Excludes SVOD platforms owned by pay TV operator Finland DNA C More Finland Elisa HBO Finland Elisa Netflix Finland Telia C More Finland Telia HBO Finland Telia Netflix France Bouygues Telecom Netflix France Free Canal Play France Free Filmo France Numericable Filmo France Orange Filmo France Orange Netflix France SFR Netflix Germany Deutsche Telekom -

Threat Modeling and Circumvention of Internet Censorship by David Fifield
Threat modeling and circumvention of Internet censorship By David Fifield A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor J.D. Tygar, Chair Professor Deirdre Mulligan Professor Vern Paxson Fall 2017 1 Abstract Threat modeling and circumvention of Internet censorship by David Fifield Doctor of Philosophy in Computer Science University of California, Berkeley Professor J.D. Tygar, Chair Research on Internet censorship is hampered by poor models of censor behavior. Censor models guide the development of circumvention systems, so it is important to get them right. A censor model should be understood not just as a set of capabilities|such as the ability to monitor network traffic—but as a set of priorities constrained by resource limitations. My research addresses the twin themes of modeling and circumvention. With a grounding in empirical research, I build up an abstract model of the circumvention problem and examine how to adapt it to concrete censorship challenges. I describe the results of experiments on censors that probe their strengths and weaknesses; specifically, on the subject of active probing to discover proxy servers, and on delays in their reaction to changes in circumvention. I present two circumvention designs: domain fronting, which derives its resistance to blocking from the censor's reluctance to block other useful services; and Snowflake, based on quickly changing peer-to-peer proxy servers. I hope to change the perception that the circumvention problem is a cat-and-mouse game that affords only incremental and temporary advancements. -

Channel 5, Playground and MASTERPIECE on PBS Announce Cast for All Creatures Great and Small
EMBARGOED UNTIL 7:01PM ET TUESDAY SEPTEMBER 24TH Channel 5, Playground And MASTERPIECE On PBS Announce Cast For All Creatures Great And Small Newcomer Nicholas Ralph to play beloved vet James Herriot opposite Samuel West, Anna Madeley, Callum Woodhouse and Rachel Shenton Channel 5, BAFTA and Golden Globe-winning production company Playground (Howards End, Wolf Hall) and MASTERPIECE on PBS today announced the casting of key roles for their upcoming adaptation of best-selling author James Herriot’s cherished collection of stories, written by Ben Vanstone (The Last Kingdom) and directed by Brian Percival (Downton Abbey). Exciting newcomer Nicholas Ralph will make his television debut as the iconic vet who became renowned for his inspiring compassion, humour and love of life. Samuel West (Mr. Selfridge, On Chesil Beach) joins as Siegfried Farnon, the wonderfully eccentric veteri- nary surgeon and proprietor of Skeldale House who reluctantly hires the recently qualified Herriot into his rural practice. Mrs Hall, the resident housekeeper and matriarch of Skeldale House will be played by Anna Madeley (The Child in Time, Patrick Melrose). Siegfried’s errant and charismatic younger brother, Tristan, will be played by Callum Woodhouse (The Durrells in Corfu). Rachel Shenton (Switched at Birth, White Gold) takes the role of Helen Alderson, an independent local farmer’s daughter who helps her father manage the family farm and care for her younger sister. “This is an exceptional cast made up of a wonderful mix of exciting new and established talent,” says executive producer Colin Callender. “Re-visiting the world of All Creatures Great and Small is like going home and re-discovering old friends whom we haven’t seen in years. -

Style Counsel: Seeing the (Random) Forest for the Trees in Adversarial Code Stylometry∗
Style Counsel: Seeing the (Random) Forest for the Trees in Adversarial Code Stylometry∗ Christopher McKnight Ian Goldberg Magnet Forensics University of Waterloo [email protected] [email protected] ABSTRACT worm based on an examination of the reverse-engineered code [17], The results of recent experiments have suggested that code stylom- casting style analysis as a forensic technique. etry can successfully identify the author of short programs from This technique, however, may be used to chill speech for soft- among hundreds of candidates with up to 98% precision. This poten- ware developers. There are several cases of developers being treated tial ability to discern the programmer of a code sample from a large as individuals of suspicion, intimidated by authorities and/or co- group of possible authors could have concerning consequences for erced into removing their software from the Internet. In the US, the open-source community at large, particularly those contrib- Nadim Kobeissi, the Canadian creator of Cryptocat (an online se- utors that may wish to remain anonymous. Recent international cure messaging application) was stopped, searched, and questioned events have suggested the developers of certain anti-censorship by Department of Homeland Security officials on four separate oc- and anti-surveillance tools are being targeted by their governments casions in 2012 about Cryptocat and the algorithms it employs [16]. and forced to delete their repositories or face prosecution. In November 2014, Chinese developer Xu Dong was arrested, pri- In light of this threat to the freedom and privacy of individual marily for political tweets, but also because he allegedly “committed programmers around the world, we devised a tool, Style Counsel, to crimes of developing software to help Chinese Internet users scale aid programmers in obfuscating their inherent style and imitating the Great Fire Wall of China” [4] in relation to proxy software he another, overt, author’s style in order to protect their anonymity wrote.