Your Wifi Is Leaking: Inferring Private User Information Despite Encryption
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MOBILE Payments Market Guide 2013
MOBILE PAYMENTS MARKET GUIDE 2013 INSIGHTS IN THE WORLDWIDE MOBILE TRANSACTION SERVICES ECOSYSTEM OVER 350 COMPANIES WORLDWIDE INSIDE Extensive global distribution via worldwide industry events As the mobile payments ecosystem is becoming increasingly more crowded and competitive, the roles of established and new players in the mobile market is shifting, with new opportunities and challenges facing each category of service providers. Efma, the global organization that brings together more than 3,300 retail financial services companies from over 130 countries, welcomes the publication of the Mobile Payments Market Guide 2013 by The Paypers as a valuable source of information and guidance for all actors in the mobile transaction services space. Patrick Desmarès - CEO, Efma MOBILE PAYMENTS MARKET GUIDE 2013 INSIGHTS IN THE WORLDWIDE MOBILE TRANSACTION SERVICES ECOSYSTEM Authors Ionela Barbuta Sabina Dobrean Monica Gaza Mihaela Mihaila Adriana Screpnic RELEASE | VERSION 1.0 | APRIL 2013 | COPYRIGHT © THE Paypers BV | ALL RIGHTS reserved 2 MOBILE PAYMENTS MARKET GUIDE 2013 INTRODUCTION Introduction You are reading the Mobile Payments Market Guide 2013, a state- se and the way commerce is done. From a quick and accessible of-the-art overview of the global mobile transaction services channel for banking on the move to a sophisticated tool for shop- ecosystem and the most complete and up-to-date reference ping, price comparison and buying, the saga of the mobile device source for mobile payments, mobile commerce and mobile is an on-going story that unfolds in leaps and bounds within a banking-related information at global level. This guide is published progressively crowded (and potentially fragmented) ecosystem. -
Sites Using React · Facebook/React Wiki · Github
Personal Open source Business Explore Pricing Blog Support This repository Search Sign in Sign up facebook / react Watch 3,811 Star 53,928 Fork 9,588 Code Issues 493 Pull requests 97 Projects 0 Wiki Pulse Graphs Sites Using React Wylie Swanson edited this page Nov 14, 2016 · 622 revisions If you use React, don't be shy – edit this page! Pages 18 The Art Of Ping Pong Find a Page… 1stdibs ‐ Online marketplace for antique furniture, jewelry, fashion, and fine art 6play ‐ Video site for the "M6" french TV channel Home 6rooms 2015 03 20 90min 2015 03 27 9flats 2015 04 03 Accio 2015 04 10 Asciinema Adazzle 2015 04 17 AddThis 2015 04 24 ADN Articles and Videos AdRoll ‐ AdRoll Prospecting UI, component library Complementary Tools Afterclasse ‐ Educational website for french students Examples AgileMD Meeting Notes Aha! Algolia ‐ Hosted Search API Meetups Amaze UI ﴾in Chinese﴿ Polyfills Angie's List Projects Airbnb react AirHelp Show 3 more pages… African Exponent ‐ Premier source of reliable African and World news Alipay Clone this wiki locally Andy Tran ‐ CodePen Profile powered by React https://github.com/facebook/react.wiki.git Ant Design AnyList Clone in Desktop Appointment Reminder ARTE ‐ Video site for the ARTE french/german TV channel Asana Assembly Assertible ‐ QA for the Web Atlassian Automattic Avant Avaza Ayasan Backpack Page 1 of 14 Assembled by RunPDF.com BBC Benzinga Beroomers ‐ Find your ideal student home! BetBetr Beyondpad Biblebox BigDecisions ‐ Used React+Flux for calculators. BigRentz BilletFix ‐ Simple ticket management system -

THE MAINTENANCE of MUTUAL UNDERSTANDING in ONLINE SECOND LANGUAGE TALK ADAM BRANDT Thesis Submitted for the Degree of Doctor Of
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by OpenGrey Repository THE MAINTENANCE OF MUTUAL UNDERSTANDING IN ONLINE SECOND LANGUAGE TALK ADAM BRANDT Thesis submitted for the degree of Doctor of Philosophy Newcastle University School of Education, Communication and Language Sciences June 2011 Abstract Encounters in which at least one person is communicating in a second language (L2) are increasingly prevalent, and span many contexts and settings. However many of these settings remain under-researched, particularly those outside of formal language education (Firth & Wagner 1997, 2007; Wagner 2004). One such under-explored setting is the internet. In one particular internet context, L2 users of English have taken the opportunity to create voice-based chat rooms in which participants can practice their use of English. In such chat rooms, despite the huge variety in backgrounds and proficiencies, participants prove themselves to be highly skilled, resourceful and competent interactants, able to ensure mutual understanding as consistently and regularly as would be expected from first language users. However, as with any context involving any kind of interactants, there are occasions on which this mutual understanding appears to come under threat. This study applies conversation analysis (CA) to the examination of audio recordings of these online, voice-based chat rooms. More specifically, it provides a fine detailed examination of the work which is put in by the participants in order to pre-empt, and/or overcome, possible threats to mutual understanding (or ‘intersubjectivity’). Analysis show how participants are at times sensitive to such threats when dealing with (1) unspecified trouble in talk and (2) an absence of response to talk. -

Skype® for Dummies‰
01_048917 ffirs.qxp 12/8/06 8:26 PM Page iii Skype® FOR DUMmIES‰ by Loren and Susan Abdulezer and Howard Dammond Foreword by Niklas Zennström CEO and co-founder of Skype 01_048917 ffirs.qxp 12/8/06 8:26 PM Page ii 01_048917 ffirs.qxp 12/8/06 8:26 PM Page i Skype® FOR DUMmIES‰ 01_048917 ffirs.qxp 12/8/06 8:26 PM Page ii 01_048917 ffirs.qxp 12/8/06 8:26 PM Page iii Skype® FOR DUMmIES‰ by Loren and Susan Abdulezer and Howard Dammond Foreword by Niklas Zennström CEO and co-founder of Skype 01_048917 ffirs.qxp 12/8/06 8:26 PM Page iv Skype® For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 www.wiley.com Copyright © 2007 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permit- ted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

What Are the Uses of Skype? What Does It Do? Who Uses Skype?
Skype Unknown macro: {align} Unknown macro: {logo} http://wiki.itap.purdue.edu/download/attachments/4293019/rsz_logo_-_skype-1.jpg "> Unknown macro: {align} Unknown macro: {logo} http://wiki.itap.purdue.edu/download/attachments/4293019/rsz_logo_-_skype-1.jpg What Are the Uses of Skype? What Does It Do? The main purpose of Skype is to connect people. People from around the world can connect through many different ways. They can connect through one or two way audio, one or two way video, one or two way audio and video or through text. People can also call any telephone around the world though this costs money, but talking between Skype users does not cost a thing. It can be used on Windows, Mac, and Linux operating systems so almost all computers are compatible. It also works with many different cell phones and mobile devices so individuals can use it whenever/wherever they want. It also can be used by a teacher who is teaching an online class. Unknown macro: {center} Who Uses Skype? Skype in Business Skype is used for businesses that need to reach people around the country or world for as cheap as possible. When business workers use Skype they can get more done, talk more to your clients, and cut your phone bill. Business workers can make free calls to people when they are using Skype and if they choose to call mobile phones or landlines it is very cheap.They can also use Skype from many mobile phones so you can use it anywhere. Skype also allows users to make video calls so business workers can make conference calls for free anytime, anywhere. -

Exploring CALL Options for Teaching EFL in Vietnam Nhon Thanh Dang Minnesota State University - Mankato
Minnesota State University, Mankato Cornerstone: A Collection of Scholarly and Creative Works for Minnesota State University, Mankato Theses, Dissertations, and Other Capstone Projects 2011 Exploring CALL Options for Teaching EFL in Vietnam Nhon Thanh Dang Minnesota State University - Mankato Follow this and additional works at: http://cornerstone.lib.mnsu.edu/etds Part of the Bilingual, Multilingual, and Multicultural Education Commons Recommended Citation Dang, Nhon Thanh, "Exploring CALL Options for Teaching EFL in Vietnam" (2011). Theses, Dissertations, and Other Capstone Projects. Paper 273. This APP is brought to you for free and open access by Cornerstone: A Collection of Scholarly and Creative Works for Minnesota State University, Mankato. It has been accepted for inclusion in Theses, Dissertations, and Other Capstone Projects by an authorized administrator of Cornerstone: A Collection of Scholarly and Creative Works for Minnesota State University, Mankato. Exploring CALL Options for Teaching EFL in Vietnam By Nhon Thanh Dang An Alternate Plan Paper Submitted In Partial Fulfillment of the Requirements for the Degree Master of Arts In Teaching English as a Second Language (TESL) Minnesota State University, Mankato Mankato, Minnesota May 2011 Date: March 29 th , 2011 This Alternate Paper Plan has been examined and approved. Examining Committee: _____________________________________________ Dr. ESTHER SMIDT, Committee Chair, Department of English ______________________________________________ Prof. & Dr. STEPHEN STOYNOFF, Committee -

Supplemental Guide For: UC-P100-S and UC-P110-S-PLUS
UC-P100-S & UC-P110-S-PLUS Crestron Flex VoIP Desk Phones for Skype® for Business Supplemental Guide Crestron Electronics, Inc. Crestron product development software is licensed to Crestron dealers and Crestron Service Providers (CSPs) under a limited non-exclusive, non-transferable Software Development Tools License Agreement. Crestron product operating system software is licensed to Crestron dealers, CSPs, and end-users under a separate End-User License Agreement. Both of these Agreements can be found on the Crestron website at www.crestron.com/legal/software_license_agreement. The product warranty can be found at www.crestron.com/legal/sales-terms-conditions-warranties. The specific patents that cover Crestron products are listed at www.crestron.com/legal/patents. Certain Crestron products contain open source software. For specific information, visit www.crestron.com/legal/open- source-software. Crestron and the Crestron logo are either trademarks or registered trademarks of Crestron Electronics, Inc. in the United States and/or other countries. Active Directory, Microsoft Teams, and Skype for Business are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. Other trademarks, registered trademarks, and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Crestron disclaims any proprietary interest in the marks and names of others. Crestron is not responsible for errors in typography or photography.This document -
Digital Mission Programme 2010
Delegate Profiles Bareface Media www.barefacemedia.com Bareface Media is a full service creative and digital agency based in Birmingham, UK. Voted in The Drum magazine's Top 100 for Design and Digital 2013; with a strong Medical and Pharma focus, they are passionate about delivering intuitive and cost-effective solutions. Born out of existing agency relationships they were approached to develop mobile apps for treatment data collection. Mobile devices are transforming the way health information can be accessed and delivered. Recognising the opportunity presented to us, they created Engineered Apps, a start up between Bareface and Physicians, focused on developing apps for health care professionals. Bareface Media estimates the US market for our apps currently in development to be worth $135m within 3 years. Their team includes, business owners, surgeons, software developers and designers familiar with the challenges and complexities of working in the healthcare and digital sectors. Simon Morris Client Services Director [email protected] +44 (0) 121 270 0650 simon.barefacemedia.com Simon‘s background is in digital marketing and advertising. He has worked with clients such as Bic, Mercedes- Benz, Schwarzkopf and Hasbro to name a few. Simon‘s skills include design, digital strategy and project management expertise, he relishes a challenge no matter how big or small. Tom West Account Director [email protected] +44 (0)121 270 0650 tom.barefacemedia.com Tom has experience in sales and marketing from both sides of the table, as a buyer and an agency with keen insight, respect for the customer, and a firm belief in the power of creativity. -
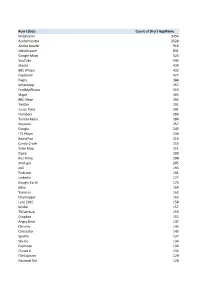
Row Labels Count of Short Appname Mobileiron 3454 Authenticator 2528
Row Labels Count of Short AppName MobileIron 3454 Authenticator 2528 Adobe Reader 916 vWorkspace 831 Google Maps 624 YouTube 543 iBooks 434 BBC iPlayer 432 Facebook 427 Pages 388 WhatsApp 357 FindMyiPhone 313 Skype 303 BBC News 292 Twitter 291 Junos Pulse 291 Numbers 289 TuneIn Radio 284 Keynote 257 Google 243 ITV Player 234 BoardPad 219 Candy Crush 215 Tube Map 211 Zipcar 209 Bus Times 208 mod.gov 205 4oD 193 Podcasts 191 LinkedIn 177 Google Earth 172 eBay 164 Yammer 163 Citymapper 163 Lync 2010 158 Kindle 157 TVCatchup 153 Dropbox 152 Angry Birds 147 Chrome 143 Calculator 143 Spotify 137 Sky Go 136 Evernote 134 iTunes U 132 FileExplorer 129 National Rail 128 iPlayer Radio 127 FasterScan 125 BBC Weather 125 FasterScan HD 124 Gmail 123 Instagram 116 Cleaner Brent 107 Viber 104 Find Friends 98 PDF Expert 95 Solitaire 91 SlideShark 89 Netflix 89 Dictation 89 com.amazon.AmazonUK 88 Flashlight 81 iMovie 79 Temple Run 2 77 Smart Office 2 74 Dictionary 72 UK & ROI 71 Journey Pro 71 iPhoto 70 TripAdvisor 68 Guardian iPad edition 68 Shazam 67 Messenger 65 Bible 64 BBC Sport 63 Rightmove 62 London 62 Sky Sports 61 Subway Surf 60 Temple Run 60 Yahoo Mail 58 thetrainline 58 Minion Rush 58 Demand 5 57 Documents 55 Argos 55 LBC 54 Sky+ 51 MailOnline 51 GarageBand 51 Calc 51 TV Guide 49 Phone Edition 49 Translate 48 Print Portal 48 Standard 48 Word 47 Skitch 47 CloudOn 47 Tablet Edition 46 MyFitnessPal 46 Bus London 46 Snapchat 45 Drive 42 4 Pics 1 Word 41 TED 39 Skyscanner 39 SoundCloud 39 PowerPoint 39 Zoopla 38 Flow Free 38 Excel 38 Radioplayer -

Voip Applications Is Internet Phone Service Right for You?
OUTSTANDING: mmmmm VERY GOOD: mmmm GOOD: mmm Reviews FLAWED: mm UNACCEPTABLE: m VoIP Applications Is Internet Phone Service Right for You? BY TED WALLINGFORD Voice over IP, or VoIP, is an emerging person using technology that allows you to use your traditional broadband Internet connection to place and standard phone receive voice and videophone calls. Internet- high-speed phone line server phone line based calls are less expensive than tradi- (operated by the tional calls (sometimes they’re even free), VoIP service) phone and many VoIP-based communication ser- company vices are compatible with the old-fashioned global phone network, so you can use these new VoIP tools to place calls to and receive them from traditional phone numbers. By adding some desktop VoIP software tools to your Mac, you, too, can take advantage of Internet Internet calling. We’ve reviewed four Mac-compatible desktop VoIP applications: Apple’s iChat AV 3.1.4, SIPPhone’s Gizmo Project 1.3.2, SightSpeed 4.5, and Skype 1.4. We also computer-to- checked out a unique product called Wengo- computer-to- phone call Phone; still in beta for the Mac, this VoIP computer call plug-in for Mozilla Firefox lets you make and receive calls via the browser. While each program has strengths and weaknesses, they all do basically the same computer-to-computer thing: they present you with a buddy list like conference call the one in an instant-messaging (IM) pro- gram, and they allow you to communicate by voice (and sometimes video) with the folks in that list. -

Skype for Business @ SUNY Cortland
Skype for Business @ SUNY Cortland About: Skype for Business is a powerful way to communicate with colleagues and students. It makes online communication more collaborative and engaging and you can use Skype for Business from nearly any computer or mobile device. Features of Skype for Business include: • Instant messaging • Audio-only calls on your computer or mobile device • Video calls on your computer or mobile device • Presence • Online meetings Skype for Business is not the same as Skype although the two do work together. Skype for Business is part of Microsoft Office 365 which is provided and managed by SUNY Cortland, whereas Skype is a consumer product available to anyone on the internet, and is not supported by the college. Also, regular Skype is for 1 to 1 calls (person to person), but Skype for Business is for 1 to 1 calls as well as 1 to many (conference calls, webinars), and it is a more robust and feature rich application. For full Skype for Business functionality, you must download and install the appropriate Skype for Business client for your computer or mobile device, and in order to use all of the Skype for Business features you will need a computer with a webcam and microphone or headset. The Memorial Library has laptops and webcams that can be "checked out" if you do not have a computer with these resources. IMPORTANT: All student, faculty and staff at SUNY Cortland are licensed for Skype for Business. In addition, although you must have an account to create meetings, anyone can join a Skype for Business meeting using only a Web browser. -

I 1. Voice.Tone.Dial 啊
1. voice.tone.dial 啊 i Microsoft Skype for Business Edition IP Phones Administrator Guide Copyright Copyright © 2019 YEALINK(XIAMEN) NETWORK TECHNOLOGY Copyright © 2019 Yealink (Xiamen) Network Technology CO., LTD. All rights reserved. No parts of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, photocopying, recording, or otherwise, for any purpose, without the express written permission of Yealink (Xiamen) Network Technology CO., LTD. Under the law, reproducing includes translating into another language or format. When this publication is made available on media, Yealink (Xiamen) Network Technology CO., LTD. gives its consent to downloading and printing copies of the content provided in this file only for private use but not for redistribution. No parts of this publication may be subject to alteration, modification or commercial use. Yealink (Xiamen) Network Technology CO., LTD. will not be liable for any damages arising from use of an illegally modified or altered publication. Trademarks Yealink®, the logo and the name and marks is trademark of Yealink (Xiamen) Network Technology CO., LTD, which are registered legally in China, the United States, EU (European Union) and other countries. All other trademarks belong to their respective owners. Without Yealink’s express written permission, recipient shall not reproduce or transmit any portion hereof in any form or by any means, with any purpose other than personal use. Warranty (1) Warranty THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS GUIDE ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS GUIDE ARE BELIEVED TO BE ACCURATE AND PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED.