RISC-V ASSEMBLY LANGUAGE Programmer Manual Part I
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PDF with Red/Green Hyperlinks
Elements of Programming Elements of Programming Alexander Stepanov Paul McJones (ab)c = a(bc) Semigroup Press Palo Alto • Mountain View Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. The authors and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. Copyright c 2009 Pearson Education, Inc. Portions Copyright c 2019 Alexander Stepanov and Paul McJones All rights reserved. Printed in the United States of America. This publication is protected by copyright, and permission must be obtained from the publisher prior to any prohibited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, or likewise. For information regarding permissions, request forms and the appropriate contacts within the Pearson Education Global Rights & Permissions Department, please visit www.pearsoned.com/permissions/. ISBN-13: 978-0-578-22214-1 First printing, June 2019 Contents Preface to Authors' Edition ix Preface xi 1 Foundations 1 1.1 Categories of Ideas: Entity, Species, -

PERL – a Register-Less Processor
PERL { A Register-Less Processor A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy by P. Suresh to the Department of Computer Science & Engineering Indian Institute of Technology, Kanpur February, 2004 Certificate Certified that the work contained in the thesis entitled \PERL { A Register-Less Processor", by Mr.P. Suresh, has been carried out under my supervision and that this work has not been submitted elsewhere for a degree. (Dr. Rajat Moona) Professor, Department of Computer Science & Engineering, Indian Institute of Technology, Kanpur. February, 2004 ii Synopsis Computer architecture designs are influenced historically by three factors: market (users), software and hardware methods, and technology. Advances in fabrication technology are the most dominant factor among them. The performance of a proces- sor is defined by a judicious blend of processor architecture, efficient compiler tech- nology, and effective VLSI implementation. The choices for each of these strongly depend on the technology available for the others. Significant gains in the perfor- mance of processors are made due to the ever-improving fabrication technology that made it possible to incorporate architectural novelties such as pipelining, multiple instruction issue, on-chip caches, registers, branch prediction, etc. To supplement these architectural novelties, suitable compiler techniques extract performance by instruction scheduling, code and data placement and other optimizations. The performance of a computer system is directly related to the time it takes to execute programs, usually known as execution time. The expression for execution time (T), is expressed as a product of the number of instructions executed (N), the average number of machine cycles needed to execute one instruction (Cycles Per Instruction or CPI), and the clock cycle time (), as given in equation 1. -

Undecidability of the Word Problem for Groups: the Point of View of Rewriting Theory
Universita` degli Studi Roma Tre Facolta` di Scienze M.F.N. Corso di Laurea in Matematica Tesi di Laurea in Matematica Undecidability of the word problem for groups: the point of view of rewriting theory Candidato Relatori Matteo Acclavio Prof. Y. Lafont ..................................... Prof. L. Tortora de falco ...................................... questa tesi ´estata redatta nell'ambito del Curriculum Binazionale di Laurea Magistrale in Logica, con il sostegno dell'Universit´aItalo-Francese (programma Vinci 2009) Anno Accademico 2011-2012 Ottobre 2012 Classificazione AMS: Parole chiave: \There once was a king, Sitting on the sofa, He said to his maid, Tell me a story, And the maid began: There once was a king, Sitting on the sofa, He said to his maid, Tell me a story, And the maid began: There once was a king, Sitting on the sofa, He said to his maid, Tell me a story, And the maid began: There once was a king, Sitting on the sofa, . " Italian nursery rhyme Even if you don't know this tale, it's easy to understand that this could continue indefinitely, but it doesn't have to. If now we want to know if the nar- ration will finish, this question is what is called an undecidable problem: we'll need to listen the tale until it will finish, but even if it will not, one can never say it won't stop since it could finish later. those things make some people loose sleep, but usually children, bored, fall asleep. More precisely a decision problem is given by a question regarding some data that admit a negative or positive answer, for example: \is the integer number n odd?" or \ does the story of the king on the sofa admit an happy ending?". -

Superh RISC Engine SH-1/SH-2
SuperH RISC Engine SH-1/SH-2 Programming Manual September 3, 1996 Hitachi America Ltd. Notice When using this document, keep the following in mind: 1. This document may, wholly or partially, be subject to change without notice. 2. All rights are reserved: No one is permitted to reproduce or duplicate, in any form, the whole or part of this document without Hitachi’s permission. 3. Hitachi will not be held responsible for any damage to the user that may result from accidents or any other reasons during operation of the user’s unit according to this document. 4. Circuitry and other examples described herein are meant merely to indicate the characteristics and performance of Hitachi’s semiconductor products. Hitachi assumes no responsibility for any intellectual property claims or other problems that may result from applications based on the examples described herein. 5. No license is granted by implication or otherwise under any patents or other rights of any third party or Hitachi, Ltd. 6. MEDICAL APPLICATIONS: Hitachi’s products are not authorized for use in MEDICAL APPLICATIONS without the written consent of the appropriate officer of Hitachi’s sales company. Such use includes, but is not limited to, use in life support systems. Buyers of Hitachi’s products are requested to notify the relevant Hitachi sales offices when planning to use the products in MEDICAL APPLICATIONS. Introduction The SuperH RISC engine family incorporates a RISC (Reduced Instruction Set Computer) type CPU. A basic instruction can be executed in one clock cycle, realizing high performance operation. A built-in multiplier can execute multiplication and addition as quickly as DSP. -

Computer Architecture Basics
V03: Computer Architecture Basics Prof. Dr. Anton Gunzinger Supercomputing Systems AG Technoparkstrasse 1 8005 Zürich Telefon: 043 – 456 16 00 Email: [email protected] Web: www.scs.ch Supercomputing Systems AG Phone +41 43 456 16 00 Technopark 1 Fax +41 43 456 16 10 8005 Zürich www.scs.ch Computer Architecture Basic 1. Basic Computer Architecture Diagram 2. Basic Computer Architectures 3. Von Neumann versus Harvard Architecture 4. Computer Performance Measurement 5. Technology Trends 2 Zürich 20.09.2019 © by Supercomputing Systems AG CONFIDENTIAL 1.1 Basic Computer Architecture Diagram Sketch the basic computer architecture diagram Describe the functions of the building blocks 3 Zürich 20.09.2019 © by Supercomputing Systems AG CONFIDENTIAL 1.2 Basic Computer Architecture Diagram Describe the execution of a single instruction 5 Zürich 20.09.2019 © by Supercomputing Systems AG CONFIDENTIAL 2 Basic Computer Architecture 2.1 Sketch an Accumulator Machine 2.2 Sketch a Register Machine 2.3 Sketch a Stack Machine 2.4 Sketch the analysis of computing expression in a Stack Machine 2.5 Write the micro program for an Accumulator, a Register and a Stack Machine for the instruction: C:= A + B and estimate the numbers of cycles 2.6 Write the micro program for an Accumulator, a Register and a Stack Machine for the instruction: C:= (A - B)2 + C and estimate the numbers of cycles 2.7 Compare Accumulator, Register and Stack Machine 7 Zürich 20.09.2019 © by Supercomputing Systems AG CONFIDENTIAL 2.1 Accumulator Machine Draw the Accumulator Machine 8 Zürich -

CS411-2015F-14 Counter Machines & Recursive Functions
Automata Theory CS411-2015F-14 Counter Machines & Recursive Functions David Galles Department of Computer Science University of San Francisco 14-0: Counter Machines Give a Non-Deterministic Finite Automata a counter Increment the counter Decrement the counter Check to see if the counter is zero 14-1: Counter Machines A Counter Machine M = (K, Σ, ∆,s,F ) K is a set of states Σ is the input alphabet s ∈ K is the start state F ⊂ K are Final states ∆ ⊆ ((K × (Σ ∪ ǫ) ×{zero, ¬zero}) × (K × {−1, 0, +1})) Accept if you reach the end of the string, end in an accept state, and have an empty counter. 14-2: Counter Machines Give a Non-Deterministic Finite Automata a counter Increment the counter Decrement the counter Check to see if the counter is zero Do we have more power than a standard NFA? 14-3: Counter Machines Give a counter machine for the language anbn 14-4: Counter Machines Give a counter machine for the language anbn (a,zero,+1) (a,~zero,+1) (b,~zero,−1) (b,~zero,−1) 0 1 14-5: Counter Machines Give a 2-counter machine for the language anbncn Straightforward extension – examine (and change) two counters instead of one. 14-6: Counter Machines Give a 2-counter machine for the language anbncn (a,zero,zero,+1,0) (a,~zero,zero,+1,0) (b,~zero,~zero,-1,+1) (b,~zero,zero,−1,+1) 0 1 (c,zero,~zero,0,-1) 2 (c,zero,~zero,0,-1) 14-7: Counter Machines Our counter machines only accept if the counter is zero Does this give us any more power than a counter machine that accepts whenever the end of the string is reached in an accept state? That is, given -

Computers, Complexity, and Controversy
Instruction Sets and Beyond: Computers, Complexity, and Controversy Robert P. Colwell, Charles Y. Hitchcock m, E. Douglas Jensen, H. M. Brinkley Sprunt, and Charles P. Kollar Carnegie-Mellon University t alanc o tyreceived Instruction set design is important, but lt1Mthi it should not be driven solely by adher- ence to convictions about design style, ,,tl ica' ch m e n RISC or CISC. The focus ofdiscussion o09 Fy ipt issues. RISC should be on the more general question of the assignment of system function- have guided ality to implementation levels within years. A study of an architecture. This point of view en- d yield a deeper un- compasses the instruction set-CISCs f hardware/software tend to install functionality at lower mputer performance, the system levels than RISCs-but also JOCUS on rne assignment iluence of VLSI on processor design, takes into account other design fea- ofsystem functionality to and many other topics. Articles on tures such as register sets, coproces- RISC research, however, often fail to sors, and caches. implementation levels explore these topics properly and can While the implications of RISC re- within an architecture, be misleading. Further, the few papers search extend beyond the instruction and not be guided by that present comparisons with com- set, even within the instruction set do- whether it is a RISC plex instruction set computer design main, there are limitations that have or CISC design. often do not address the same issues. not been identified. Typical RISC As a result, even careful study of the papers give few clues about where the literature is likely to give a distorted RISC approach might break down. -
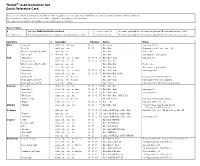
Thumb® 16-Bit Instruction Set Quick Reference Card
Thumb® 16-bit Instruction Set Quick Reference Card This card lists all Thumb instructions available on Thumb-capable processors earlier than ARM®v6T2. In addition, it lists all Thumb-2 16-bit instructions. The instructions shown on this card are all 16-bit in Thumb-2, except where noted otherwise. All registers are Lo (R0-R7) except where specified. Hi registers are R8-R15. Key to Tables § See Table ARM architecture versions. <loreglist+LR> A comma-separated list of Lo registers. plus the LR, enclosed in braces, { and }. <loreglist> A comma-separated list of Lo registers, enclosed in braces, { and }. <loreglist+PC> A comma-separated list of Lo registers. plus the PC, enclosed in braces, { and }. Operation § Assembler Updates Action Notes Move Immediate MOVS Rd, #<imm> N Z Rd := imm imm range 0-255. Lo to Lo MOVS Rd, Rm N Z Rd := Rm Synonym of LSLS Rd, Rm, #0 Hi to Lo, Lo to Hi, Hi to Hi MOV Rd, Rm Rd := Rm Not Lo to Lo. Any to Any 6 MOV Rd, Rm Rd := Rm Any register to any register. Add Immediate 3 ADDS Rd, Rn, #<imm> N Z C V Rd := Rn + imm imm range 0-7. All registers Lo ADDS Rd, Rn, Rm N Z C V Rd := Rn + Rm Hi to Lo, Lo to Hi, Hi to Hi ADD Rd, Rd, Rm Rd := Rd + Rm Not Lo to Lo. Any to Any T2 ADD Rd, Rd, Rm Rd := Rd + Rm Any register to any register. Immediate 8 ADDS Rd, Rd, #<imm> N Z C V Rd := Rd + imm imm range 0-255. -

A Microcontroller Based Fan Speed Control Using PID Controller Theory
A Microcontroller Based Fan Speed Control Using PID Controller Theory Thu Thu Zue Zin and Hlaing Thida Oo University of Computer Studies, Yangon thuthuzuezin @gmail.com Abstract PIC control application is widely used and User define popular in modern elections. The aim of this paper Microcontroller speed PIC 16F877 is design and construct the fan speed control system Duty cycle with microcontroller. PIC 16F877 and photo transistor is used for the system. User define speed can be selected by keypads for various speed. Motor is controlled by the pulse width modulation. Driver The system can be operate with normal mode and circuit timer mode. Delay time for timer mode is 10 seconds. The feedback signal from sensor is controlled by the proportional integral derivative equations to reproduce the desire duty cycle. Sensor Motor 1. Introduction Figure 1. Block Diagram of the System Motors are widely used in many applications, such as air conditioners , slide doors, washing machines and control areas. Motors are 2. Background Theory derivate it’s output performance due to the PID Controller tolerances, operating conditions, process error and Proportional Integral Derivative controller is measurement error. Pulse Width Modulation a generic control loop feedback mechanism widely control technique is better for control the DC motor used in industrial control systems. A PID controller than others techniques. PWM control the speed of attempts to correct the error between a measured motor without changing the voltage supply to process variable and a desired set point by calculating motor. Series of pulse define the speed of the and then outputting a corrective action that can adjust motor. -

Copyright © 1998, by the Author(S). All Rights Reserved
Copyright © 1998, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. WHATS DECIDABLE ABOUT HYBRID AUTOMATA by Thomas A. Henzinger, Peter W. Kopke, Anuj Puri, and Pravin Varaiya Memorandum No. UCB/ERL M98/22 15 April 1998 WHAT'S DECIDABLE ABOUT HYBRID AUTOMATA by Thomas A. Henzinger,Peter W. Kopke, Anuj Puri, and Pravin Varaiya Memorandum No. UCB/ERL M98/22 15 April 1998 ELECTRONICS RESEARCH LABORATORY College ofEngineering University of California, Berkeley 94720 What's Decidable About Hybrid Automata?*^ Thomas A. Henzinger^ Peter W. Kopke^ Anuj Puri^ Pravin Varaiya^ Abstract. Hybrid automata model systems with both digital and analog compo nents, such as embedded control programs. Many verification tasks for such programs can be expressed as reachabibty problems for hybrid automata. By improving on pre vious decidability and undecidability results, we identify a precise boundary between decidability and undecidability for the reachabibty problem of hybrid automata. On the positive side, we give an (optimal) PSPACE reachabibty algorithmfor the case of initiabzed rectangular automata, where ab analog variables foUow independent tra jectories within piecewise-bnear envelopes and are reinitiabzed whenever the envelope changes. Our algorithm is based on the construction ofa timedautomaton that contains ab reachabibty information about a given initiabzed rectangular automaton. -

Readingsample
Embedded Robotics Mobile Robot Design and Applications with Embedded Systems Bearbeitet von Thomas Bräunl Neuausgabe 2008. Taschenbuch. xiv, 546 S. Paperback ISBN 978 3 540 70533 8 Format (B x L): 17 x 24,4 cm Gewicht: 1940 g Weitere Fachgebiete > Technik > Elektronik > Robotik Zu Inhaltsverzeichnis schnell und portofrei erhältlich bei Die Online-Fachbuchhandlung beck-shop.de ist spezialisiert auf Fachbücher, insbesondere Recht, Steuern und Wirtschaft. Im Sortiment finden Sie alle Medien (Bücher, Zeitschriften, CDs, eBooks, etc.) aller Verlage. Ergänzt wird das Programm durch Services wie Neuerscheinungsdienst oder Zusammenstellungen von Büchern zu Sonderpreisen. Der Shop führt mehr als 8 Millionen Produkte. CENTRAL PROCESSING UNIT . he CPU (central processing unit) is the heart of every embedded system and every personal computer. It comprises the ALU (arithmetic logic unit), responsible for the number crunching, and the CU (control unit), responsible for instruction sequencing and branching. Modern microprocessors and microcontrollers provide on a single chip the CPU and a varying degree of additional components, such as counters, timing coprocessors, watchdogs, SRAM (static RAM), and Flash-ROM (electrically erasable ROM). Hardware can be described on several different levels, from low-level tran- sistor-level to high-level hardware description languages (HDLs). The so- called register-transfer level is somewhat in-between, describing CPU compo- nents and their interaction on a relatively high level. We will use this level in this chapter to introduce gradually more complex components, which we will then use to construct a complete CPU. With the simulation system Retro [Chansavat Bräunl 1999], [Bräunl 2000], we will be able to actually program, run, and test our CPUs. -

Programmable Digital Microcircuits - a Survey with Examples of Use
- 237 - PROGRAMMABLE DIGITAL MICROCIRCUITS - A SURVEY WITH EXAMPLES OF USE C. Verkerk CERN, Geneva, Switzerland 1. Introduction For most readers the title of these lecture notes will evoke microprocessors. The fixed instruction set microprocessors are however not the only programmable digital mi• crocircuits and, although a number of pages will be dedicated to them, the aim of these notes is also to draw attention to other useful microcircuits. A complete survey of programmable circuits would fill several books and a selection had therefore to be made. The choice has rather been to treat a variety of devices than to give an in- depth treatment of a particular circuit. The selected devices have all found useful ap• plications in high-energy physics, or hold promise for future use. The microprocessor is very young : just over eleven years. An advertisement, an• nouncing a new era of integrated electronics, and which appeared in the November 15, 1971 issue of Electronics News, is generally considered its birth-certificate. The adver• tisement was for the Intel 4004 and its three support chips. The history leading to this announcement merits to be recalled. Intel, then a very young company, was working on the design of a chip-set for a high-performance calculator, for and in collaboration with a Japanese firm, Busicom. One of the Intel engineers found the Busicom design of 9 different chips too complicated and tried to find a more general and programmable solu• tion. His design, the 4004 microprocessor, was finally adapted by Busicom, and after further négociation, Intel acquired marketing rights for its new invention.