Credit Counseling/Debtor Education System (CC/DE System)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sovereign Defaults and Debt Restructurings: Historical Overview
Sovereign Defaults and Debt Restructurings: 1 Historical Overview Debt crises and defaults by sovereigns—city-states, kingdoms, and empires—are as old as sovereign borrowing itself. The first recorded default goes back at least to the fourth century B.C., when ten out of thirteen Greek municipalities in the Attic Maritime Association de- faulted on loans from the Delos Temple (Winkler 1933). Most fiscal crises of European antiquity, however, seem to have been resolved through ‘‘currency debasement’’—namely, inflations or devaluations— rather than debt restructurings. Defaults cum debt restructurings picked up in the modern era, beginning with defaults in France, Spain, and Portugal in the mid-sixteenth centuries. Other European states fol- lowed in the seventeenth century, including Prussia in 1683, though France and Spain remained the leading defaulters, with a total of eight defaults and six defaults, respectively, between the sixteenth and the end of the eighteenth centuries (Reinhart, Rogoff, and Savastano 2003). Only in the nineteenth century, however, did debt crises, defaults, and debt restructurings—defined as changes in the originally envis- aged debt service payments, either after a default or under the threat of default—explode in terms of both numbers and geographical inci- dence. This was the by-product of increasing cross-border debt flows, newly independent governments, and the development of modern fi- nancial markets. In what follows, we begin with an overview of the main default and debt restructuring episodes of the last two hundred years.1 We next turn to the history of how debt crises were resolved. We end with a brief review of the creditor experience with sovereign debt since the 1850s. -

FERC Vs. Bankruptcy Courts—The Battle Over Jurisdiction Continues
FERC vs. Bankruptcy Courts—The Battle over Jurisdiction Continues By Hugh M. McDonald and Neil H. Butterklee* In energy industry bankruptcies, the issue of whether a U.S. bankruptcy court has sole and exclusive jurisdiction to determine a debtor’s motion to reject an executory contract has mostly involved a jurisdictional struggle involving the Federal Energy Regulatory Commission. The dearth of judicial (and legislative) guidance on this issue has led to shifting decisions and inconsistent outcomes leaving counterparties to contracts in still uncertain positions when a contract counterparty commences a bankruptcy case. The authors of this article discuss the jurisdiction conundrum. The COVID-19 pandemic has put pressure on all aspects of the United States economy, including the energy sector. Counterparties to energy-related contracts, such as power purchase agreements (“PPAs”) and transportation services agreements (“TSAs”), may need to commence bankruptcy cases to restructure their balance sheets and, as part of such restructuring, may seek to shed unprofitable or out-of-market contracts. However, this situation has created a new stage for the decades-old jurisdictional battle between bankruptcy courts and energy regulators. The U.S. Bankruptcy Code allows a debtor to assume or reject executory contracts with the approval of the bankruptcy judge presiding over the case.1 The standard employed by courts when assessing the debtor’s request to assume or reject is the business judgment standard. A debtor merely has to demonstrate that assumption or rejection is in the best interest of the estate and the debtor’s business. However, most energy-related contracts are subject to regulatory oversight by federal and/or state regulatory bodies, which, depending on the type of contract that is being terminated, apply different standards—most of which take into account public policy concerns. -

UK (England and Wales)
Restructuring and Insolvency 2006/07 Country Q&A UK (England and Wales) UK (England and Wales) Lyndon Norley, Partha Kar and Graham Lane, Kirkland and Ellis International LLP www.practicallaw.com/2-202-0910 SECURITY AND PRIORITIES ■ Floating charge. A floating charge can be taken over a variety of assets (both existing and future), which fluctuate from 1. What are the most common forms of security taken in rela- day to day. It is usually taken over a debtor's whole business tion to immovable and movable property? Are any specific and undertaking. formalities required for the creation of security by compa- nies? Unlike a fixed charge, a floating charge does not attach to a particular asset, but rather "floats" above one or more assets. During this time, the debtor is free to sell or dispose of the Immovable property assets without the creditor's consent. However, if a default specified in the charge document occurs, the floating charge The most common types of security for immovable property are: will "crystallise" into a fixed charge, which attaches to and encumbers specific assets. ■ Mortgage. A legal mortgage is the main form of security interest over real property. It historically involved legal title If a floating charge over all or substantially all of a com- to a debtor's property being transferred to the creditor as pany's assets has been created before 15 September 2003, security for a claim. The debtor retained possession of the it can be enforced by appointing an administrative receiver. property, but only recovered legal ownership when it repaid On default, the administrative receiver takes control of the the secured debt in full. -

Individual Voluntary Arrangement Factsheet What Is an Individual Voluntary Arrangement (IVA)? an IVA Is a Legally Binding
Individual Voluntary Arrangement Factsheet What is an An IVA is a legally binding arrangement supervised by a Licensed Unlike debt management products, an IVA is legally binding and Individual Insolvency Practitioner, the purpose of which is to enable an precludes all creditors from taking any enforcement action against Voluntary individual, sole trader or partner (the debtor) to reach a compromise the debtor post-agreement, assuming the debtor complies with the Arrangement with his creditors and avoid the consequences of bankruptcy. The his obligations in the IVA. (IVA)? compromise should offer a larger repayment towards the creditor’s debt than could otherwise be expected were the debtor to be made bankrupt. This is often facilitated by the debtor making contributions to the arrangement from his income over a designated period or from a third party contribution or other source that would not ordinarily be available to a trustee in bankruptcy. Who can An IVA is available to all individuals, sole traders and partners who It is also often used by sole traders and partners who have suffered benefit from are experiencing creditor pressure and it is used particularly by those problems with their business but wish to secure its survival as they it? who own their own property and wish to avoid the possibility of losing believe it will be profitable in the future. It enables them to make a it in the event they were made bankrupt. greater repayment to creditors than could otherwise be expected were they made bankrupt and the business consequently were to cease trading. The procedure In theory, it is envisaged that the debtor drafts proposals for In certain circumstances, when it is considered that the debtor in brief presentation to his creditors prior to instructing a nominee, (who requires protection from creditors taking enforcement action whilst must be a Licensed Insolvency Practitioner), to review them before the IVA proposal is being considered, the nominee can file the submission to creditors (or Court if seeking an Interim Order). -

Law Reform Commission of British Columbia Report on Floating Charges
LAW REFORM COMMISSION OF BRITISH COLUMBIA REPORT ON FLOATING CHARGES ON LAND LRC 103 JANUARY 1989 The Law Reform Commission of British Columbia was established by the Law Reform Commission Act in 1969 and began functioning in 1970. The Commissioners are: ARTHUR L. CLOSE, Chairman HON. RONALD I. CHEFFINS, Q.C., Vice-Chairman MARY V. NEWBURY LYMAN R. ROBINSON, Q.C. PETER T. BURNS, Q.C. Thomas G. Anderson is Counsel to the Commission. J. Bruce McKinnon and Linda Reid are Legal Research Officers to the Commission. Sharon St. Michael is Secretary to the Commission. Text processing and technical copy preparation by Linda Grant. The Commission offices are located at Suite 601, Chancery Place, 865 Hornby St., Vancouver, B.C. V6Z 2H4. Canadian Cataloguing in Publication Data Law Reform Commission of British Columbia. Report on floating charges on land (LRC, ISSN 0843-6053; 103) ISBN 0-7718-8748-5 1. Floating charges. 2. Commercial loans - Law and legislation - British Columbia. 3. Security (Law) - British Columbia. 4. Real property - British Columbia. I. Title. II. Title: Floating charges on land. III. Series: LRC (Law Reform Commission of British Columbia); 103 KEB271.A72L38 1989 346.711'074 C89-092073-7 Table of Contents I. INTRODUCTION 1 A. General 1 B. Methodology 1 C. The Need for Flexible Security Over Land 2 D. The Future of the Floating Charge 3 E. The Scope of Reform 4 F. This Report 4 II. THE NEED FOR REFORM 5 A. Introduction 5 B. Overview of the Current Law 5 1. Common Law 5 2. Land Title Registration 5 3. -

Debtor-In-Possession Financing
BANKRUPTCY Debtor-in-Possession Financing by Marshall S. Huebner an you imagine the reaction the first time a lender said, “Hey, let’s lend large sums of money to a bankrupt Ccompany!”? As it turns out, lending to a debtor in posses- sion can be a smart move. This article explains, in general terms, the hows and whys of DIP lending. t may seem counterintuitive In Chapter 11, pre-bankruptcy Chapter 11 debtors on C.O.D. or that banks and other institu- creditors are, for the most part, C.B.D. until the company stabi- I tions would compete fiercely stayed from enforcement reme- lizes and working capital financ- to provide loans to companies that dies and do not receive payment ing for the company’s ongoing have recently filed for protection of principal or interest while the operations is available. under Chapter 11 of the U.S. company seeks to rationalize its DIP loans are typically asset- Bankruptcy Code. But they do— business and formulate a plan of based, revolving working-capital and often. Indeed, “DIP loans,” reorganization to restructure its facilities put into place at the out- as they often are called, are big balance sheet. set of Chapter 11 to provide both business and can range from tens The DIP typically finds itself immediate cash as well as ongoing of thousands to billions of dollars. in need of credit immediately working capital during the reorga- Moreover, lending institutions of after initiating a Chapter 11 case. nization process. Perhaps most all sizes may be called on to While most of its pre-bankruptcy important, DIP financing helps extend further credit to a bank- liabilities are frozen, the company the company restore vendor and ruptcy debtor to “protect” an is likely to need cash immediately customer confidence in the com- existing loan position. -

FORMAL OPINION NO 2005-40 Conflicts of Interest, Current Clients: Representing Debtor and One Or More Creditors in Bankruptcy
FORMAL OPINION NO 2005-40 Conflicts of Interest, Current Clients: Representing Debtor and One or More Creditors in Bankruptcy Facts: Lawyer is asked to represent Individual A in bankruptcy. Indi- vidual A owes money to Secured Creditor B and Unsecured Creditor C, both of whom are also clients of Lawyer. Questions: 1. May Lawyer simultaneously represent Individual A, Secured Creditor B, and Unsecured Creditor C in the bankruptcy proceedings? 2. May Lawyer represent only Individual A in the bankruptcy proceedings? 3. Assume that Lawyer had never represented and is not asked to represent Individual A. Could Lawyer represent both Secured Creditor B and Unsecured Creditor C in Individual A’s bankruptcy? Conclusions: 1. No. 2. Yes. 3. Yes, qualified. Discussion: The critical sections that must be considered are Oregon RPC 1.7(a) and (b). Oregon RPC 1.7(a) provides: Except as provided in paragraph (b), a lawyer shall not represent a client if the representation involves a current conflict of interest. A current conflict of interest exists if: (1) the representation of one client will be directly adverse to another client; 2016 Revision Formal Opinion No 2005-40 (2) there is a significant risk that the representation of one or more clients will be materially limited by the lawyer’s respon- sibilities to another client, a former client or a third person or by a personal interest of the lawyer; or (3) the lawyer is related to another lawyer, as parent, child, sibling, spouse or domestic partner, in a matter adverse to a person whom the lawyer knows is represented by the other lawyer in the same matter. -

Sovereign Debt, Volatility, and Insurance
FEDERAL RESERVE BANK OF SAN FRANCISCO WORKING PAPER SERIES Sovereign Debt, Volatility and Insurance Kenneth Kletzer University of California, Santa Cruz February 2005 Working Paper 2006-05 http://www.frbsf.org/publications/economics/papers/2006/wp06-05bk.pdf The views in this paper are solely the responsibility of the authors and should not be interpreted as reflecting the views of the Federal Reserve Bank of San Francisco or the Board of Governors of the Federal Reserve System. This paper was produced under the auspices for the Center for Pacific Basin Studies within the Economic Research Department of the Federal Reserve Bank of San Francisco Sovereign Debt, Volatility and Insurance Kenneth Kletzer Department of Economics University of California Santa Cruz, CA 95064 August 2004 (revised, February 2005) Abstract External debt increases the vulnerability of indebted emerging market economies to macroeconomic volatility and financial crises. Capital account reversals often lead sovereign debt repayment crises that are only resolved after prolonged and difficult debt restructuring. Foreign indebtedness exacerbates domestic financial distress in crisis, increasing both the incidence and severity of emerging market crises. These outcomes contrast with the presumption that access to international capital markets should help countries to smooth domestic consumption and investment against macroeconomic shocks. This paper uses models of sovereign to reconsider the role of sovereign debt renegotiation for international risk sharing and presents an approach for analyzing contractual innovations for implementing contingent debt repayments. The financial innovations that might allow risk-sharing rather than risk-inducing capital flows go beyond contractual changes that ease debt renegotiation by separating contingent payments from bonds. -
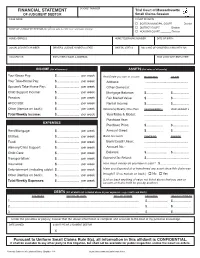
Financial Statement of Judgment Debtor English 11/18 INCOME and PROPERTY THAT ARE EXEMPT from PAYMENT ORDERS
DOCKET NUMBER FINANCIAL STATEMENT Trial Court of Massachusetts OF JUDGMENT DEBTOR Small Claims Session CASE NAME COURT DIVISION "BOSTON MUNICIPAL COURT ________ Division "DISTRICT COURT ________ Division NAME OF JUDGMENT DEBTOR (the person who lost the case and owes money) "HOUSING COURT ________ Division HOME ADDRESS HOME TELEPHONE NUMBER DATE OF BIRTH SOCIAL SECURITY NUMBER DRIVER’S LICENSE NUMBER & STATE MARITAL STATUS NO. & AGE OF CHILDREN LIVING WITH YOU OCCUPATION EMPLOYER’S NAME & ADDRESS HOW LONG WITH EMPLOYER? INCOME (list all sources) ASSETS (list value of all assets) Your Gross Pay: $ ........................ per week Real Estate you own or co-own RESIDENCE OTHER Your Take-Home Pay: $ ........................ per week Address: ............................................... Spouse’s Take-Home Pay: $ ........................ per week Other Owner(s): ................................................ Child Support Income: $ ........................ per week Mortgage Balance: $ .................. $ .................. Pension: $ ........................ per week Fair Market Value: $ .................. $ .................. AFDC/SSI: $ ........................ per week Rental Income: $ .................. $ .................. Other (itemize on back): $ ........................ per week Vehicle(s)/Boat(s) You Own VEHICLE/BOAT 1 VEHICLE/BOAT 2 Total Weekly Income: $ ........................ per week Year/Make & Model: ................................................ Purchase Year: ................................................ EXPENSES -

Agenda Advancing Economics in Business Individual Voluntary
Agenda Advancing economics in business Individual voluntary arrangements: cashing in on consumer debt? The popularity of individual voluntary arrangements in the UK has grown substantially in the past year, with over 44,000 taken out in 2006, a 118% increase on 2005 figures.1 With IVAs being increasingly used by consumers in debt as an alternative to bankruptcy—despite recent warnings about misleading advertising by some financial management businesses promoting IVAs—what are some of the drivers of this trend? Individual voluntary arrangements (IVAs) are intended to financial situation of the debtor and makes a proposal to offer consumers protection, giving debtors in financial the creditors of the debtor, specifying the total amount of difficulty the option of having a proportion of their debt debt the debtor can repay and the repayment period. written off and paying back the remainder of what they The proposal is discussed in a formal meeting with the owe over an agreed period, typically five years. Although creditors and the debtor. If 75% of creditors (in terms of consumer credit regulation and responsible lending amount of debt) agree, the agreement becomes binding practices are aimed at avoiding situations of on all parties. If the creditors do not agree to the over-indebtedness, in practice, there are always likely to proposal, they can either renegotiate or recommend be some borrowers who are not able to meet their other solutions to the debtor. financial obligations—for example, they may get into financial difficulty as a result of unanticipated events Debtors in financial difficulty have other options available such as unemployment or divorce. -

The Criminalization of Private Debt a Pound of Flesh the Criminalization of Private Debt
A Pound of Flesh The Criminalization of Private Debt A Pound of Flesh The Criminalization of Private Debt © 2018 AMERICAN CIVIL LIBERTIES UNION Contents Executive Summary .................................................................................................................................... 4 How the Court System Is Used to Send Debtors to Jail .................................................................... 5 The Role of Civil Court Judges ............................................................................................................. 6 Prosecutors and Debt Collectors as Business Partners ................................................................... 7 A System That Breeds Coercion and Abuse ....................................................................................... 7 Key Recommendations ......................................................................................................................... 7 A Nation of Debtors on the Financial Edge .............................................................................................. 9 The Debt-to-Jail Pipeline ............................................................................................................................12 State and Federal Laws That Allow the Jailing of Debtors .............................................................14 When Judges Reflexively Issue Arrest Warrants for Debtors .......................................................15 How Courts Use the Threat of Jail to Extract Payment ...................................................................16 -

Sovereign Default and International Trade
Sovereign Default and International Trade Charles Serfaty (MIT)∗ December 16, 2020 PLEASE CLICK HERE FOR THE LAST VERSION. Evidence suggests that sovereign defaults disrupt international trade. As a consequence, countries that are more open have more to lose from a sovereign default and are less inclined to renege on their debt. In turn, lenders should trust more open countries and charge them lower interest rate. In most cases, the country should also borrow more debt the more open it is. This paper formalizes this idea in a simple sovereign debt model à la Eaton and Gersovitz (1981). It also provides evidence using gravitational instrumental variables from Frankel and Romer (1999) and Feyrer (2019) as a source for exogenous variation for trade openness. ∗I am infinitely grateful to my PhD director, Arnaud Costinot, for his constant support and inventive suggestions, that went unabated by the 2020 crisis. I owe a great debt of gratitude to my PhD advisor Ivàn Werning for his incredibly helpful insights. I am also especially thankful to Ricardo Caballero and Daniel Cohen for insightful discussions about this paper. I want to thank Daron Acemoglu, Marios Angeletos, David Atkin, Martin Beraja, Dave Donaldson, Joel Flynn, Michele Fornino, Juliette Fournier, Masao Fukui, Clémence Idoux, Antoine Levy, Andrea Manera, Parinitha Sastry, Alp Simsek, Claudia Steinwender, John Sturm, Adrien Verdelhan as well as all MIT macro lunch and trade tea participants for their very useful comments. 1 1 Introduction The main peculiarity of sovereign debt contracts is that repayments are not easily enforce- able by the lender: a sovereign country with a strong enough army and divided enough lenders can default without expecting dire consequences.