The Data Link Layer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ipv6 … a Simplified Explanation
IPv6 … A Simplified Explanation Presented by Bryan Crisler Senior Network Engineer Time Warner Cable Housekeeping • Take this time to locate: – Emergency Exits – Bathrooms – Breakroom/Water Fountain – Note taking utensils • Put your Phones on Vibrate – If you need to take a call, feel free to step out of the room. About your Speaker • Bryan Crisler – Started in Cable @ Charter Communications, Riverside, CA in June 2005 – Currently a Senior Network Engineer at Time Warner Cable About your Speaker • Held following positions: – Broadband Technician I-IV (Charter) – Network Operations Specialist (Charter) – Network Technician (Charter) – Network Engineer (Charter & TWC) – SR Network Engineer (TWC) About your Speaker • Email: [email protected] • LinkedIn: linkedin.com/in/bcrisler Today’s Lesson Plan • Session 1: So What About IPv6? • Session 2: Every Day IPv6 and You So What About IPv6? Session 1 Basic History of IP • IP – Internet Protocol • Defined in RFC 791, dated 1981, written by Information Sciences Institute @ USC • Written for DARPA (Defense Advanced Research Projects Agency) Basic History of IP • “… Internet Protocol is designed for use in interconnected systems of packet-switched computer communication networks…provides for transmitting blocks of data called datagrams from sources to destinations… identified by fixed length addresses.” (RFC 791, section 1.1) Versions of IP • IPv0 – 3: Experimental Only • IPv4: Defined in 1981 by RFC 760 & 791. First version to implemented publically. Still in use today. • IPv5: Also experimental, called Internet Stream Protocol. • IPv6: Also called IP Next Generation (IPng), Defined in 1998 by RFC 2460-2467 IP Addressing • Layer 3 (Network) form of Addressing • Two different forms of IP Address: – IPv4 • Uses Dotted Decimal (192.168.0.1) • Has 4,294,967,296 total address (public & private) • 32 bit address – IPv6 • Uses Hexadecimal Notation (FE80::1) • Has 3.4×1038 total address (public & private) • 128 bit address IP Addressing – cont. -

Solutions to Chapter 2
CS413 Computer Networks ASN 4 Solutions Solutions to Assignment #4 3. What difference does it make to the network layer if the underlying data link layer provides a connection-oriented service versus a connectionless service? [4 marks] Solution: If the data link layer provides a connection-oriented service to the network layer, then the network layer must precede all transfer of information with a connection setup procedure (2). If the connection-oriented service includes assurances that frames of information are transferred correctly and in sequence by the data link layer, the network layer can then assume that the packets it sends to its neighbor traverse an error-free pipe. On the other hand, if the data link layer is connectionless, then each frame is sent independently through the data link, probably in unconfirmed manner (without acknowledgments or retransmissions). In this case the network layer cannot make assumptions about the sequencing or correctness of the packets it exchanges with its neighbors (2). The Ethernet local area network provides an example of connectionless transfer of data link frames. The transfer of frames using "Type 2" service in Logical Link Control (discussed in Chapter 6) provides a connection-oriented data link control example. 4. Suppose transmission channels become virtually error-free. Is the data link layer still needed? [2 marks – 1 for the answer and 1 for explanation] Solution: The data link layer is still needed(1) for framing the data and for flow control over the transmission channel. In a multiple access medium such as a LAN, the data link layer is required to coordinate access to the shared medium among the multiple users (1). -

~DRAFT~ CHAPTER 5: Link Layer
~DRAFT~ CHAPTER 5: Link layer Contents Network notes – Link layer ..................................................................................................................... 1 1 Context of Chapter .................................................................................................................. 2 2 Introduction ............................................................................................................................. 2 3 Objectives of Chapter/module ................................................................................................ 3 4 Services of the link layer ......................................................................................................... 4 5 Error detection ........................................................................................................................ 4 a. Parity check ............................................................................................................................. 4 b. Cyclic Redundancy Check ...................................................................................................... 5 6 Error Correction ...................................................................................................................... 5 7 MAC ....................................................................................................................................... 6 a. Fixed assigned MAC .............................................................................................................. -

Data Link Layer
Data link layer Goals: ❒ Principles behind data link layer services ❍ Error detection, correction ❍ Sharing a broadcast channel: Multiple access ❍ Link layer addressing ❍ Reliable data transfer, flow control: Done! ❒ Example link layer technology: Ethernet Link layer services Framing and link access ❍ Encapsulate datagram: Frame adds header, trailer ❍ Channel access – if shared medium ❍ Frame headers use ‘physical addresses’ = “MAC” to identify source and destination • Different from IP address! Reliable delivery (between adjacent nodes) ❍ Seldom used on low bit error links (fiber optic, co-axial cable and some twisted pairs) ❍ Sometimes used on high error rate links (e.g., wireless links) Link layer services (2.) Flow Control ❍ Pacing between sending and receiving nodes Error Detection ❍ Errors are caused by signal attenuation and noise. ❍ Receiver detects presence of errors signals sender for retrans. or drops frame Error Correction ❍ Receiver identifies and corrects bit error(s) without resorting to retransmission Half-duplex and full-duplex ❍ With half duplex, nodes at both ends of link can transmit, but not at same time Multiple access links / protocols Two types of “links”: ❒ Point-to-point ❍ PPP for dial-up access ❍ Point-to-point link between Ethernet switch and host ❒ Broadcast (shared wire or medium) ❍ Traditional Ethernet ❍ Upstream HFC ❍ 802.11 wireless LAN MAC protocols: Three broad classes ❒ Channel Partitioning ❍ Divide channel into smaller “pieces” (time slots, frequency) ❍ Allocate piece to node for exclusive use ❒ Random -

Networking Packet Broadcast Storms
Lesson Learned Networking Packet Broadcast Storms Primary Interest Groups Balancing Authorities (BAs) Generator Operators (GOPs) Reliability Coordinators (RCs) Transmission Operators (TOPs) Transmission Owners (TOs) that own and operate an Energy Management System (EMS) Problem Statement When a second network cable was connected from a voice over internet protocol (VOIP) phone to a network switch lacking proper settings, a packet broadcast storm prevented network communications from functioning, and supervisory control and data acquisition (SCADA) was lost for several hours. Broadcast storm events have also arisen from substation local area network (LAN) issues. Details A conference room was set up for a training class that needed to accommodate multiple PCs. The bridge protocol data unit (BPDU) packet propagation prevention setting was disabled on a port in the conference room in order to place a network switch off of that port. Upon completion of the training, the network switch was removed; however, the BPDU packet propagation setting was inadvertently not restored. As part of a telephone upgrade project, the traditional phone in this conference room was recently replaced by a VOIP phone. Later, an additional network cable was connected to the output port of this VOIP phone into a secondary network jack within the conference room. When the second network cable was connected from a VOIP phone to a network switch lacking proper settings, a switching loop resulted. Spanning tree protocol is normally used to prevent switching loops from propagating broadcast packets continuously until the network capacity is overwhelmed. A broadcast packet storm from the switching loop prevented network communications from functioning and SCADA was lost for several hours. -

Br-Asi01 Br-Asx01
BR-ASI01 BR-ASX01 Data Comm for Business, Inc. 807 Pioneer Street Champaign, IL 61820 217-352-3207 Rev. Date: October 17, 1996 This manual applies to both the “I” and “X” router models. The “I” model (BR-ASI01) is single protocol TCP/IP only. The “X” model (BR-ASX01) is a multi-protocol router that routes TCP/IP, IPX, DECnet, and Appletalk. When using this manual with “I” model router, ignore the manual sections pertaining to protocols other than TCP/IP. CHAPTER 1 - INTRODUCTION 7 ABOUT THE BR ROUTER 7 Getting Started 7 Hardware Installation 7 RouterView Software Installation 8 Command Line Preparation 8 Quickstart Configuration 8 Appendices and Index 8 CHAPTER 2 - GETTING STARTED 9 A FEW NOTES 9 Please Read The Manuals 9 Warranty and Service 9 Getting Help With the BR Router 9 WHAT YOU WILL NEED TO GET STARTED 9 Supplied with the BR Router 9 Needed For Installation 10 Ethernet Connection Requirements 10 Thick Ethernet 10 Thin Ethernet 10 10Base-T Twisted-Pair Ethernet 10 Telco Line Connection Requirements 11 RS-232 Port 11 CHAPTER 3 - HARDWARE INSTALLATION 13 Mounting the Router 13 Connecting the Router to the Ethernet 14 Connecting to Thick Ethernet 14 Connecting to Thin Ethernet 14 Connecting to Twisted-Pair Ethernet 14 Connecting a Line Device to the BR Router 14 Connecting Devices to the RS-232C Port 15 Connecting an Out-of-Band Management Console 15 Powering Up the Router 15 CHAPTER 4 - ROUTERVIEW SOFTWARE INSTALLATION 17 RouterView for Windows 17 System Requirements 17 Installing and Running RouterView for Windows 17 RouterView -

Discussion Chapter#9 Services of Data-Link
The Islamic University of Gaza ECOM 4314: Data Communication Faculty of Engineering Instructor: Dr. Aiman Abu Samra Department of Computer Engineering T.A.: Eng. Alaa O. Shama Discussion Chapter#9 The data-link layer of a node (host or router) is responsible for delivering a datagram to the next node in the path. The data-link layer is located between the physical and the network layers. The datalink layer provides services to the network layer; it receives services from the physical layer. data-link layer of the source host needs only to encapsulate the datagram received from the network in a frame, the data-link layer of the destination host needs to decapsulate the datagram from the frame, but each intermediate node needs to both encapsulate and decapsulate, because each link may be using a different protocol with a different frame format. Even if one link and the next are using the same protocol, encapsulation and decapsulation are needed because the link-layer addresses are normally different. Services of Data-Link: 1. Framing The data-link layer at each node needs to encapsulate the datagram (packet received from the network layer) in a frame before sending it to the next node. The node also needs to decapsulate the datagram from the frame received on the logical channel. 2. Flow control If the rate of produced frames is higher than the rate of consumed frames, frames at the receiving end need to be buffered while waiting to be consumed (processed). Definitely, we cannot have an unlimited buffer size at the receiving side. -

OSI Data Link Layer
OSI Data Link Layer Network Fundamentals – Chapter 7 © 2007 Cisco Systems, Inc. All rights reserved. Cisco Public 1 Objectives Explain the role of Data Link layer protocols in data transmission. Describe how the Data Link layer prepares data for transmission on network media. Describe the different types of media access control methods. Identify several common logical network topologies and describe how the logical topology determines the media access control method for that network. Explain the purpose of encapsulating packets into frames to facilitate media access. Describe the Layer 2 frame structure and identify generic fields. Explain the role of key frame header and trailer fields including addressing, QoS, type of protocol and Frame Check Sequence. © 2007 Cisco Systems, Inc. All rights reserved. Cisco Public 2 Data Link Layer – Accessing the Media Describe the service the Data Link Layer provides as it prepares communication for transmission on specific media © 2007 Cisco Systems, Inc. All rights reserved. Cisco Public 3 Data Link Layer – Accessing the Media Describe why Data Link layer protocols are required to control media access © 2007 Cisco Systems, Inc. All rights reserved. Cisco Public 4 Data Link Layer – Accessing the Media Describe the role of framing in preparing a packet for transmission on a given media © 2007 Cisco Systems, Inc. All rights reserved. Cisco Public 5 Data Link Layer – Accessing the Media Describe the role the Data Link layer plays in linking the software and hardware layers © 2007 Cisco Systems, Inc. All rights reserved. Cisco Public 6 Data Link Layer – Accessing the Media Identify several sources for the protocols and standards used by the Data Link layer © 2007 Cisco Systems, Inc. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
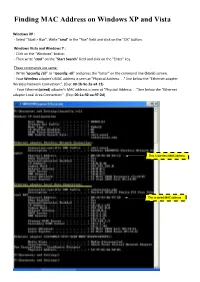
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001