Algorithms I
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Amortized Analysis Worst-Case Analysis
Beyond Worst Case Analysis Amortized Analysis Worst-case analysis. ■ Analyze running time as function of worst input of a given size. Average case analysis. ■ Analyze average running time over some distribution of inputs. ■ Ex: quicksort. Amortized analysis. ■ Worst-case bound on sequence of operations. ■ Ex: splay trees, union-find. Competitive analysis. ■ Make quantitative statements about online algorithms. ■ Ex: paging, load balancing. Princeton University • COS 423 • Theory of Algorithms • Spring 2001 • Kevin Wayne 2 Amortized Analysis Dynamic Table Amortized analysis. Dynamic tables. ■ Worst-case bound on sequence of operations. ■ Store items in a table (e.g., for open-address hash table, heap). – no probability involved ■ Items are inserted and deleted. ■ Ex: union-find. – too many items inserted ⇒ copy all items to larger table – sequence of m union and find operations starting with n – too many items deleted ⇒ copy all items to smaller table singleton sets takes O((m+n) α(n)) time. – single union or find operation might be expensive, but only α(n) Amortized analysis. on average ■ Any sequence of n insert / delete operations take O(n) time. ■ Space used is proportional to space required. ■ Note: actual cost of a single insert / delete can be proportional to n if it triggers a table expansion or contraction. Bottleneck operation. ■ We count insertions (or re-insertions) and deletions. ■ Overhead of memory management is dominated by (or proportional to) cost of transferring items. 3 4 Dynamic Table: Insert Dynamic Table: Insert Dynamic Table Insert Accounting method. Initialize table size m = 1. ■ Charge each insert operation $3 (amortized cost). – use $1 to perform immediate insert INSERT(x) – store $2 in with new item IF (number of elements in table = m) ■ When table doubles: Generate new table of size 2m. -

Game Trees, Quad Trees and Heaps
CS 61B Game Trees, Quad Trees and Heaps Fall 2014 1 Heaps of fun R (a) Assume that we have a binary min-heap (smallest value on top) data structue called Heap that stores integers and has properly implemented insert and removeMin methods. Draw the heap and its corresponding array representation after each of the operations below: Heap h = new Heap(5); //Creates a min-heap with 5 as the root 5 5 h.insert(7); 5,7 5 / 7 h.insert(3); 3,7,5 3 /\ 7 5 h.insert(1); 1,3,5,7 1 /\ 3 5 / 7 h.insert(2); 1,2,5,7,3 1 /\ 2 5 /\ 7 3 h.removeMin(); 2,3,5,7 2 /\ 3 5 / 7 CS 61B, Fall 2014, Game Trees, Quad Trees and Heaps 1 h.removeMin(); 3,7,5 3 /\ 7 5 (b) Consider an array based min-heap with N elements. What is the worst case running time of each of the following operations if we ignore resizing? What is the worst case running time if we take into account resizing? What are the advantages of using an array based heap vs. using a BST-based heap? Insert O(log N) Find Min O(1) Remove Min O(log N) Accounting for resizing: Insert O(N) Find Min O(1) Remove Min O(N) Using a BST is not space-efficient. (c) Your friend Alyssa P. Hacker challenges you to quickly implement a max-heap data structure - "Hah! I’ll just use my min-heap implementation as a template", you think to yourself. -
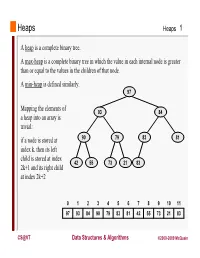
Heaps a Heap Is a Complete Binary Tree. a Max-Heap Is A
Heaps Heaps 1 A heap is a complete binary tree. A max-heap is a complete binary tree in which the value in each internal node is greater than or equal to the values in the children of that node. A min-heap is defined similarly. 97 Mapping the elements of 93 84 a heap into an array is trivial: if a node is stored at 90 79 83 81 index k, then its left child is stored at index 42 55 73 21 83 2k+1 and its right child at index 2k+2 01234567891011 97 93 84 90 79 83 81 42 55 73 21 83 CS@VT Data Structures & Algorithms ©2000-2009 McQuain Building a Heap Heaps 2 The fact that a heap is a complete binary tree allows it to be efficiently represented using a simple array. Given an array of N values, a heap containing those values can be built, in situ, by simply “sifting” each internal node down to its proper location: - start with the last 73 73 internal node * - swap the current 74 81 74 * 93 internal node with its larger child, if 79 90 93 79 90 81 necessary - then follow the swapped node down 73 * 93 - continue until all * internal nodes are 90 93 90 73 done 79 74 81 79 74 81 CS@VT Data Structures & Algorithms ©2000-2009 McQuain Heap Class Interface Heaps 3 We will consider a somewhat minimal maxheap class: public class BinaryHeap<T extends Comparable<? super T>> { private static final int DEFCAP = 10; // default array size private int size; // # elems in array private T [] elems; // array of elems public BinaryHeap() { . -

L11: Quadtrees CSE373, Winter 2020
L11: Quadtrees CSE373, Winter 2020 Quadtrees CSE 373 Winter 2020 Instructor: Hannah C. Tang Teaching Assistants: Aaron Johnston Ethan Knutson Nathan Lipiarski Amanda Park Farrell Fileas Sam Long Anish Velagapudi Howard Xiao Yifan Bai Brian Chan Jade Watkins Yuma Tou Elena Spasova Lea Quan L11: Quadtrees CSE373, Winter 2020 Announcements ❖ Homework 4: Heap is released and due Wednesday ▪ Hint: you will need an additional data structure to improve the runtime for changePriority(). It does not affect the correctness of your PQ at all. Please use a built-in Java collection instead of implementing your own. ▪ Hint: If you implemented a unittest that tested the exact thing the autograder described, you could run the autograder’s test in the debugger (and also not have to use your tokens). ❖ Please look at posted QuickCheck; we had a few corrections! 2 L11: Quadtrees CSE373, Winter 2020 Lecture Outline ❖ Heaps, cont.: Floyd’s buildHeap ❖ Review: Set/Map data structures and logarithmic runtimes ❖ Multi-dimensional Data ❖ Uniform and Recursive Partitioning ❖ Quadtrees 3 L11: Quadtrees CSE373, Winter 2020 Other Priority Queue Operations ❖ The two “primary” PQ operations are: ▪ removeMax() ▪ add() ❖ However, because PQs are used in so many algorithms there are three common-but-nonstandard operations: ▪ merge(): merge two PQs into a single PQ ▪ buildHeap(): reorder the elements of an array so that its contents can be interpreted as a valid binary heap ▪ changePriority(): change the priority of an item already in the heap 4 L11: Quadtrees CSE373, -

Search Trees
Lecture III Page 1 “Trees are the earth’s endless effort to speak to the listening heaven.” – Rabindranath Tagore, Fireflies, 1928 Alice was walking beside the White Knight in Looking Glass Land. ”You are sad.” the Knight said in an anxious tone: ”let me sing you a song to comfort you.” ”Is it very long?” Alice asked, for she had heard a good deal of poetry that day. ”It’s long.” said the Knight, ”but it’s very, very beautiful. Everybody that hears me sing it - either it brings tears to their eyes, or else -” ”Or else what?” said Alice, for the Knight had made a sudden pause. ”Or else it doesn’t, you know. The name of the song is called ’Haddocks’ Eyes.’” ”Oh, that’s the name of the song, is it?” Alice said, trying to feel interested. ”No, you don’t understand,” the Knight said, looking a little vexed. ”That’s what the name is called. The name really is ’The Aged, Aged Man.’” ”Then I ought to have said ’That’s what the song is called’?” Alice corrected herself. ”No you oughtn’t: that’s another thing. The song is called ’Ways and Means’ but that’s only what it’s called, you know!” ”Well, what is the song then?” said Alice, who was by this time completely bewildered. ”I was coming to that,” the Knight said. ”The song really is ’A-sitting On a Gate’: and the tune’s my own invention.” So saying, he stopped his horse and let the reins fall on its neck: then slowly beating time with one hand, and with a faint smile lighting up his gentle, foolish face, he began.. -

Splay Trees Last Changed: January 28, 2017
15-451/651: Design & Analysis of Algorithms January 26, 2017 Lecture #4: Splay Trees last changed: January 28, 2017 In today's lecture, we will discuss: • binary search trees in general • definition of splay trees • analysis of splay trees The analysis of splay trees uses the potential function approach we discussed in the previous lecture. It seems to be required. 1 Binary Search Trees These lecture notes assume that you have seen binary search trees (BSTs) before. They do not contain much expository or backtround material on the basics of BSTs. Binary search trees is a class of data structures where: 1. Each node stores a piece of data 2. Each node has two pointers to two other binary search trees 3. The overall structure of the pointers is a tree (there's a root, it's acyclic, and every node is reachable from the root.) Binary search trees are a way to store and update a set of items, where there is an ordering on the items. I know this is rather vague. But there is not a precise way to define the gamut of applications of search trees. In general, there are two classes of applications. Those where each item has a key value from a totally ordered universe, and those where the tree is used as an efficient way to represent an ordered list of items. Some applications of binary search trees: • Storing a set of names, and being able to lookup based on a prefix of the name. (Used in internet routers.) • Storing a path in a graph, and being able to reverse any subsection of the path in O(log n) time. -

AVL Tree, Bayer Tree, Heap Summary of the Previous Lecture
DATA STRUCTURES AND ALGORITHMS Hierarchical data structures: AVL tree, Bayer tree, Heap Summary of the previous lecture • TREE is hierarchical (non linear) data structure • Binary trees • Definitions • Full tree, complete tree • Enumeration ( preorder, inorder, postorder ) • Binary search tree (BST) AVL tree The AVL tree (named for its inventors Adelson-Velskii and Landis published in their paper "An algorithm for the organization of information“ in 1962) should be viewed as a BST with the following additional property: - For every node, the heights of its left and right subtrees differ by at most 1. Difference of the subtrees height is named balanced factor. A node with balance factor 1, 0, or -1 is considered balanced. As long as the tree maintains this property, if the tree contains n nodes, then it has a depth of at most log2n. As a result, search for any node will cost log2n, and if the updates can be done in time proportional to the depth of the node inserted or deleted, then updates will also cost log2n, even in the worst case. AVL tree AVL tree Not AVL tree Realization of AVL tree element struct AVLnode { int data; AVLnode* left; AVLnode* right; int factor; // balance factor } Adding a new node Insert operation violates the AVL tree balance property. Prior to the insert operation, all nodes of the tree are balanced (i.e., the depths of the left and right subtrees for every node differ by at most one). After inserting the node with value 5, the nodes with values 7 and 24 are no longer balanced. -

Leftist Heap: Is a Binary Tree with the Normal Heap Ordering Property, but the Tree Is Not Balanced. in Fact It Attempts to Be Very Unbalanced!
Leftist heap: is a binary tree with the normal heap ordering property, but the tree is not balanced. In fact it attempts to be very unbalanced! Definition: the null path length npl(x) of node x is the length of the shortest path from x to a node without two children. The null path lengh of any node is 1 more than the minimum of the null path lengths of its children. (let npl(nil)=-1). Only the tree on the left is leftist. Null path lengths are shown in the nodes. Definition: the leftist heap property is that for every node x in the heap, the null path length of the left child is at least as large as that of the right child. This property biases the tree to get deep towards the left. It may generate very unbalanced trees, which facilitates merging! It also also means that the right path down a leftist heap is as short as any path in the heap. In fact, the right path in a leftist tree of N nodes contains at most lg(N+1) nodes. We perform all the work on this right path, which is guaranteed to be short. Merging on a leftist heap. (Notice that an insert can be considered as a merge of a one-node heap with a larger heap.) 1. (Magically and recursively) merge the heap with the larger root (6) with the right subheap (rooted at 8) of the heap with the smaller root, creating a leftist heap. Make this new heap the right child of the root (3) of h1. -

SPLAY Trees • Splay Trees Were Invented by Daniel Sleator and Robert Tarjan
Red-Black, Splay and Huffman Trees Kuan-Yu Chen (陳冠宇) 2018/10/22 @ TR-212, NTUST Review • AVL Trees – Self-balancing binary search tree – Balance Factor • Every node has a balance factor of –1, 0, or 1 2 Red-Black Trees. • A red-black tree is a self-balancing binary search tree that was invented in 1972 by Rudolf Bayer – A special point to note about the red-black tree is that in this tree, no data is stored in the leaf nodes • A red-black tree is a binary search tree in which every node has a color which is either red or black 1. The color of a node is either red or black 2. The color of the root node is always black 3. All leaf nodes are black 4. Every red node has both the children colored in black 5. Every simple path from a given node to any of its leaf nodes has an equal number of black nodes 3 Red-Black Trees.. 4 Red-Black Trees... • Root is red 5 Red-Black Trees…. • A leaf node is red 6 Red-Black Trees….. • Every red node does not have both the children colored in black • Every simple path from a given node to any of its leaf nodes does not have equal number of black nodes 7 Searching in a Red-Black Tree • Since red-black tree is a binary search tree, it can be searched using exactly the same algorithm as used to search an ordinary binary search tree! 8 Insertion in a Red-Black Tree • In a binary search tree, we always add the new node as a leaf, while in a red-black tree, leaf nodes contain no data – For a given data 1. -

Data Structures and Programming Spring 2016, Final Exam
Data Structures and Programming Spring 2016, Final Exam. June 21, 2016 1 1. (15 pts) True or False? (Mark for True; × for False. Score = maxf0, Right - 2 Wrongg. No explanations are needed. (1) Let A1;A2, and A3 be three sorted arrays of n real numbers (all distinct). In the comparison model, constructing a balanced binary search tree of the set A1 [ A2 [ A3 requires Ω(n log n) time. × False (Merge A1;A2;A3 in linear time; then pick recursively the middle as root (in linear time).) (2) Let T be a complete binary tree with n nodes. Finding a path from the root of T to a given vertex v 2 T using breadth-first search takes O(log n) time. × False (Note that the tree is NOT a search tree.) (3) Given an unsorted array A[1:::n] of n integers, building a max-heap out of the elements of A can be performed asymptotically faster than building a red-black tree out of the elements of A. True (O(n) for building a max-heap; Ω(n log n) for building a red-black tree.) (4) In the worst case, a red-black tree insertion requires O(1) rotations. True (See class notes) (5) In the worst case, a red-black tree deletion requires O(1) node recolorings. × False (See class notes) (6) Building a binomial heap from an unsorted array A[1:::n] takes O(n) time. True (See class notes) (7) Insertion into an AVL tree asymptotically beats insertion into an AA-tree. × False (See class notes) (8) The subtree of the root of a red-black tree is always itself a red-black tree. -
Heapsort Previous Sorting Algorithms G G Heap Data Structure P Balanced
Previous sortinggg algorithms Insertion Sort 2 O(n ) time Heapsort Merge Sort Based off slides by: David Matuszek http://www.cis.upenn.edu/~matuszek/cit594-2008/ O(n) space PtdbMttBPresented by: Matt Boggus 2 Heap data structure Balanced binary trees Binary tree Recall: The dthfdepth of a no de iitditis its distance f rom th e root The depth of a tree is the depth of the deepest node Balanced A binary tree of depth n is balanced if all the nodes at depths 0 through n-2 have two children Left-justified n-2 (Max) Heap property: no node has a value greater n-1 than the value in its parent n Balanced Balanced Not balanced 3 4 Left-jjyustified binary trees Buildinggp up to heap sort How to build a heap A balanced binary tree of depth n is left- justified if: n it has 2 nodes at depth n (the tree is “full”)or ), or k How to maintain a heap it has 2 nodes at depth k, for all k < n, and all the leaves at dept h n are as fa r le ft as poss i ble How to use a heap to sort data Left-justified Not left-justified 5 6 The heappp prop erty siftUp A node has the heap property if the value in the Given a node that does not have the heap property, you can nodide is as large as or larger t han th e va lues iiin its give it the heap property by exchanging its value with the children value of the larger child 12 12 12 12 14 8 3 8 12 8 14 8 14 8 12 Blue node has Blue node has Blue node does not Blue node does not Blue node has heap property heap property have heap property have heap property heap property All leaf nodes automatically have -

Amortized Complexity Analysis for Red-Black Trees and Splay Trees
International Journal of Innovative Research in Computer Science & Technology (IJIRCST) ISSN: 2347-5552, Volume-6, Issue-6, November2018 DOI: 10.21276/ijircst.2018.6.6.2 Amortized Complexity Analysis for Red-Black Trees and Splay Trees Isha Ashish Bahendwar, RuchitPurshottam Bhardwaj, Prof. S.G. Mundada Abstract—The basic conception behind the given problem It stores data in more efficient and practical way than basic definition is to discuss the working, operations and complexity data structures. Advanced data structures include data analyses of some advanced data structures. The Data structures like, Red Black Trees, B trees, B+ Trees, Splay structures that we have discussed further are Red-Black trees Trees, K-d Trees, Priority Search Trees, etc. Each of them and Splay trees.Red-Black trees are self-balancing trees has its own special feature which makes it unique and better having the properties of conventional tree data structures along with an added property of color of the node which can than the others.A Red-Black tree is a binary search tree with be either red or black. This inclusion of the property of color a feature of balancing itself after any operation is performed as a single bit property ensured maintenance of balance in the on it. Its nodes have an extra feature of color. As the name tree during operations such as insertion or deletion of nodes in suggests, they can be either red or black in color. These Red-Black trees. Splay trees, on the other hand, reduce the color bits are used to count the tree’s height and confirm complexity of operations such as insertion and deletion in trees that the tree possess all the basic properties of Red-Black by splayingor making the node as the root node thereby tree structure, The Red-Black tree data structure is a binary reducing the time complexity of insertion and deletions of a search tree, which means that any node of that tree can have node.