Strategies for Effective Wi-Fi Offload
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Integrating Wi-Fi and Femtocells a Feasibility Study Based on a Techno Economic Comparison of the Two Technologies
Integrating Wi-Fi and Femtocells A feasibility study based on a techno economic comparison of the two technologies RAZVAN POPESCU Master of Science Thesis Stockholm, Sweden 2013 Integrating Wi-Fi and Femtocells A feasibility study based on a techno economic comparison of the two technologies Student Razvan Popescu Supervisor Ashraf Awadelakrim Widaa Ahmed Examiner Jan I Markendahl Wireless@KTH School of Information and Communication Technology, KTH-Royal Institute of Technology, Stockholm, Sweden June 2013 Abstract At the end of 2009 mobile industry reached an inevitable milestone; the aggregated mobile data traffic exceeded voice traffic in the mobile networks. Starting with this point, data consumption has been continuously increasing and there are no signs that this behaviour will change in the future. For this reason mobile operators face nowadays a new paradox: they have to invest massively in their networks in order to sustain the increasing traffic while revenues are not expected to rise. This means that in order to survive, operators have to add extra capacity in a cost-efficient way. Using indoor solutions and mobile data offloading has been considered one right approach for solving this issue. While indoor solutions like Distributed Antenna Systems and repeaters have been used in the mobile networks for some time now, data offloading represents a relatively newcomer in the mobile industry. Using this concept, data traffic generated by mobile devices is moved towards alternative networks releasing the congestion in the operators’ macrocell layers. Among indoor solutions, two technologies stepped forward, Wi-Fi and Femtocells. This MSc thesis studies these two technologies, making a techno- economic comparison between them with respect on QoS level, interference, security and capacity-cost ratio. -

A Techno-Economic Comparison Between Outdoor Macro-Cellular and Indoor Offloading Solutions
A techno-economic comparison between outdoor macro-cellular and indoor offloading solutions FEIDIAS MOULIANITAKIS Master's Degree Project Stockholm, Sweden August 2015 TRITA-ICT-EX-2015:224 A techno-economic comparison between outdoor macro-cellular and indoor offloading solutions Feidias Moulianitakis 2015-08-31 Master’s Thesis Examiner Academic adviser Prof. Jan Markendahl Ashraf A. Widaa Ahmed School of Information and Communication Technology (ICT) KTH Royal Institute of Technology Stockholm, Sweden Abstract Mobile penetration rates have already exceeded 100% in many countries. Nowadays, mobile phones are part of our daily lives not only for voice or short text messages but for a plethora of multimedia services they provide via their internet connection. Thus, mobile broadband has become the main driver for the evolution of mobile networks and it is estimated that until 2018 the mobile broadband traffic will exceed the level of 15 exabytes. This estimation is a threat to the current mobile networks which have to significantly improve their capacity performance. Furthermore, another important aspect is the fact that 80% of the mobile broadband demand comes from indoor environments which add to the signal propagation the burden of building penetration loss. Keeping these facts in mind, there are many potential solutions that can solve the problem of the increasing indoor mobile broadband demand. In general, there are two approaches; improve the existing macro-cellular networks by for example enhancing them with carrier aggregation or enter the buildings and deploy small cell solutions such as femtocells or WiFi APs. Both the academia and the industry have already shown interest in these two approaches demonstrating the importance of the problem. -

Aptilo Carrier-Class Wi-Fi Solution Datasheet
No one knows carrier Wi-Fi better than we do! Aptilo Carrier-Class Wi-Fi Solution Datasheet Partner Network Roaming OSS / BSS Integration Wi-Fi User Experience Hotel BYOD Home Wi-Fi Flexible APIs ServiceGlue Captive Portal Guest Internet Existing portals B2B Adaptors Policy OCS / Prepaid Prepaid / & OFCS / Billing Charging Charging PCRF Smart Advanced Wi-Fi Sub Office Wi-Fi CRM Lookups Configurable Database Other databases Logic Quota Mgmt EAP TLS Wi-Fi Policy DNS EAP TTLS EAP-SIM/AKA Public Wi-Fi HLR / HSS 3GPP AAA Wi-Fi AAA DHCP Diameter SS7 Trusted / Diameter RADIUS Untrusted RADIUS Local SOAP Access Gateway Adaptors (VSA) Break-out Mobile Core Integration Wi-Fi Service Control Small Cell Wi-Fi Wi-Fi Backhaul to mobile core through tunnels Gateway EAP-SIM/AKA non-SIM Carrier-Class Wi-Fi. Your challenge, our speciality The Aptilo Service Management Platform™ (SMP) With more than 90 service provider Wi-Fi customers in 60 coun- Aptilo offers a fast-track for launching Wi-Fi services with our tries under our belt, we understand that building a carrier-class optional pre-integrated functions for subscriber management, Wi-Fi service is a challenging task with a lot of considerations, prepaid & charging, web portals, access control as well as statis- • How to integrate with my existing OSS/BSS? tics and reporting; all optimized to work together on a single scal- • How to efficiently roll-out new sites? able system – the Aptilo Service Management Platform™ (SMP). • How to make Wi-Fi attractive to venue owners? What this means for you as a service provider is faster time-to- • Which business models should I use? market and happy subscribers with the best user experience avail- • Which Wi-Fi radio vendor should I select? able today. -

Graphical System Visualization and Flow Display a Visual Representation of an Authentication, Authorization, and Accounting Backend
DEGREE PROJECT IN INFORMATION TECHNOLOGY, SECOND LEVEL STOCKHOLM, SWEDEN 2016 Graphical system visualization and flow display A visual representation of an authentication, authorization, and accounting backend JOAKIM AF SANDEBERG KTH ROYAL INSTITUTE OF TECHNOLOGY INFORMATION AND COMMUNICATION TECHNOLOGY Graphical system visualization and flow display A visual representation of an authentication, authorization, and accounting backend Joakim af Sandeberg Master of Science Thesis Communication Systems School of Information and Communication Technology KTH Royal Institute of Technology Stockholm, Sweden 28 July 2016 Examiner: Gerald Q. Maguire Jr. c Joakim af Sandeberg, 28 July 2016 Abstract Displaying the architecture of a software system is not a simple task. Showing all of the available information will unnecessarily complicate the view, while showing too little might render the view unhelpful. Furthermore, showing the dynamics of the operation of such a system is even more challenging. This thesis project describes the development of a graphical tool that can both display the configuration of an advanced authentication, authorization, and accounting (AAA) system and the messages passed between nodes in the system. The solution described uses force-based graph layouts coupled with adaptive filters as well as vector-based rendering to deliver a view of the status of the system. Force-based layout spreads out the nodes in an adaptive fashion. The adaptive filters starts by showing what is most often the most relevant information, but can be configured by the user. Finally, the vector based rendering offers unlimited zoom into the individual nodes in the graph in order to display additional detailed information. Unified Modeling Language (UML) sequence charts are used to display the message flow inside the system (both between nodes and inside individual nodes). -

Connection Manager User Guide.Book
XFINITY® Connection Manager Version 1.06 Take Fast With You User Guide http://customer.comcast.com/2go 1-800-COMCAST Copyright 2011, Smith Micro Software, Inc. All rights reserved. This document is the property of Smith Micro Software, Inc. and contains confidential and proprietary information owned by Smith Micro Software, Inc. Any unauthorized copying, use or disclosure of it without the prior written permission of Smith Micro Software, Inc. is strictly prohibited. Table of Contents Chapter 1 — Getting Started System Requirements. .5 Installing the XFINITY Connection Manager Software . .6 Launching the XFINITY Connection Manager . .6 Chapter 2 — The XFINITY Connection Manager Interface Getting Connected . .8 Supported Networks List: In Detail . .9 The Main Window . .11 Minimizing the Main Window. .14 Using the System Tray Icon . .15 Chapter 3 — Establishing Mobile Connections Manually Connecting to a Mobile Network . .17 Chapter 4 — Establishing WiFi Connections Manually Connecting to a WiFi Network . .20 Options for Connecting to a New Network . .21 The List of WiFi Networks . .22 WiFi Info . .23 What is a Closed Network?. .23 How to Access a Closed Network . .23 Introduction to WiFi Encryption . .24 Connecting to an Encrypted Network . .26 Chapter 5 — Network Profiles What is a Network Profile? . .27 The Network Profiles Window . .27 Creating a Profile for a WiFi Network . .29 Configuring WiFi Data Encryption . .31 Automatic Profile Creation Settings . .32 Editing a Network Profile. .32 Deleting a Network Profile. .33 Profile Properties: WiFi . .33 Profile Properties: General . .34 – 3 – Chapter 6 — Virtual Private Networks (VPNs) What is a Virtual Private Network? . .37 Supported Clients . .37 Configuring a VPN Connection . -

N Ot for Distribution Or Reproduction
www.pipelinepub.com Volume 13, Issue 2 Monthly News Digest By: Jim Schakenbach The summer is all but behind us, but there are no telecommunications doldrums in sight. The big news in July began with Ericsson’s CEO Hans Vestberg suddenly stepping down, temporarily replaced by company CFO Jan Frykhammar. The company released a statement from the Board of Directors in which board chairman Leif Johanssan said, mobile security. “Hans Vestberg has led the company for seven years through significant industry and company transformation. A new BT and KPMG report warns of emerging threats Hans has been instrumental in building strong from profit-oriented, highly-organized cyber-criminal relationships with key customers around the world and enterprises that are posing an increasingly dangerous his leadership and energy have been an inspiration to threat to legitimate digital enterprises. Only 20 percent employees and leaders across Ericsson. However, in the of IT decision makers in large multinational corporations current environment are confident that their organizations are fully prepared and as the company against the threat accelerates its of cyber-criminals. strategy execution, The vast majority the Board of of companies feel Directors has decided constrained by that the time is right regulation, available for a new leader resources, and a to drive the next dependence on phase in Ericsson’s third parties when development.” responding to attacks, according to The other big the report. news of the month immediately followed Increasingly- the Ericsson announcement. Verizon announced it will organized criminals are finding new ways to do harm. A acquire Yahoo’s operating business for almost five new report released in July by Corero Network Security billion dollars in cash. -

View Annual Report
e10vk 5/6/2008 12:27 PM Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2007 TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File Number 0-26536 SMITH MICRO SOFTWARE, INC. (Exact name of registrant as specified in its charter) Delaware 33-0029027 (State or other jurisdiction of incorporation or organization) (I.R.S. Employer Identification Number) 51 Columbia, Suite 200, Aliso Viejo, CA 92656 (Address of principal executive offices) (Zip Code) Registrant’s telephone number, including area code: (949) 362-5800 Common Stock, $.001 par value The NASDAQ Stock Market LLC (Title of each class) (NASDAQ Global Market) (Name of each exchange on which registered) Securities registered pursuant to Section 12(b) of the Act: Common Stock, $.001 par value Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as define d in Rule 405 of the Securities Act. YES NO If this report is an annual or transition report, indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or 15(d) of the Securities Exchange Act of 1934 YES NO Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

View Annual Report
Dear Shareholder: Attached you will find the year 2002 annual report for Smith Micro Software, Inc. (Nasdaq: SMSI). The economy continued to struggle throughout 2002 and it was a challenge for us as well, but we set a goal for 2002 to solidify the corporate infrastructure, continue to solidify our existing wireless customer base, add new wireless customers, upgrade our existing product line and make available new products that can assist in a return to profitability. Through our efforts in 2002, we were able to grow our cash reserves and reduce our liabilities. As a result, I believe we put ourselves in a good position to achieve our goals going into 2003, which we believe will be productive for our shareholders. As can be seen in the first quarter, we think we have positioned ourselves appropriately in the market and will be able to effectively address the market as the as it improves. I am optimistic about 2003 for Smith Micro and here are my reasons why. Some of the most promising developments continue to occur in our Wireless & Broadband Division, as reflected in a leadership position of providing our QuickLink Mobile to the number one and number two wireless carriers in North America, Verizon Wireless and Cingular Wireless respectively. Also, we recently announced the new QuickLink Mobile Wi-Fi at the CTIA Show in New Orleans this past March. QuickLink Mobile Wi-Fi allows the consumer to freely migrate from a wireless data connection to a Wi-Fi hotspot without needing to logoff the data connection and having to login to the Wi-Fi hotspot. -
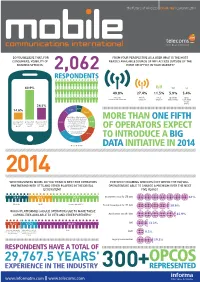
Telecoms.Com Intelligence Global Industry Survey
the future of wireless ISSUE 182 FEBRUARY 2014 DO YOU BELIEVE THAT, FOR FROM YOUR PERSPECTIVE AS A USER WHAT IS THE MOST CONSUMERS, VISIBILITY OF READILY AVAILABLE SOURCE OF WIFI ACCESS OUTSIDE OF THE ROAMING SPEND IS: HOME OR OFFICE IN YOUR MARKET? RESPONDENTS 60.9% 49.8% 27.4% 11.5% 5.9% 5.4% Amenity Mobile Fixed Specialist Open (café, shop, mall, stadium etc) operator operator wifi provider residential access points 24.5% 5.5% 14.6% 11.2% 12.2% How likely is it that operators in your market will use shared MORE THAN ONE FIFTH spectrum (licensed shared Less important As important More important 21.6% 10.8% access/authorised shared than amount as amount than amount access/white space, etc) spent? spent? spent? for some of their capacity in the next five years? OF OPERATORS EXPECT (1 – 7, where 1 is highly unlikely and 7 is highly likely) 16.9% 21.9% TO INTRODUCE A BIG 123456 7 DATA INITIATIVE IN 2014 TELECOMS.COM INTELLIGENCE 2014 GLOBAL INDUSTRY SURVEY WHICH BUSINESS MODEL DO YOU THINK IS BEST FOR OPERATORS FOR WHICH ROAMING SERVICES (NOT WITHIN THE EU) WILL PARTNERING WITH OTTS AND OTHER PLAYERS IN THE DIGITAL OPERATORS BE ABLE TO CHARGE A PREMIUM OVER THE NEXT ECOSYSTEM? FIVE YEARS? 24.6% 25.6% 50.1% Guaranteed QoS for LTE data 61% Wholesale Retail Revenue share with OTT Tiered throughput for LTE data 38.6% WHICH PLATFORM(S) SHOULD OPERATORS USE TO MAKE THESE CAPABILITIES AVAILABLE TO OTTS AND OTHER PARTNERS? Application-specific data 45.9% 16.2% 17.7% 66.1% SMS 13.3% Only through industry-wide Only through their own B2B Both initiatives such as the GSMA's collaboration platform, enabling MMS OneAPI Exchange? partners to create mash-up 9.3% services? Legacy voice services 19.3% RESPONDENTS HAVE A TOTAL OF EXPERIENCE IN THE INDUSTRY OFC_MCI182.indd 1 10/02/2014 08:18 FRONT Editorial 02 CONTENTS FEBRUARY14 Analysis 04 Heavyweight Vodafone Carrier Services makes a big investment in IPX capabilities and threatens the The leading provider existence of smaller IPX providers. -

Sweden-Nigeria Business Forum
SWEDEN-NIGERIA BUSINESS FORUM STOCKHOLM, SWEDEN 18-19 MAY 2020 Partnerships between Sweden and Nigeria on ICT, Energy and Transport towards building a Smarter and Innovation Driven Cities www.eqtpartners.com ABOUT DELEGATION HIGH-LEVEL NIGERIAN BUSINESS DELEGATION TO SWEDEN LED BY MINISTER FOR TRADE & INVESTMENT, NIGERIA, H.E. OTUNBA ADENIYI ADEBAYO, STOCKHOLM, SWEDEN, MAY 18TH -19TH 2020 Sweden is a global leader in innovation and ranked first in Europe according to the European innovation scoreboard. Sweden spends more on Research & Development than any European nation (3% of GDP) and excels in promoting training and transfer of knowledge with partner countries and businesses. Over the years, this has given Swedish enterprises a unique head-start on the global scene with innovations like Bluetooth, Spotify, Skype and global companies like Ericsson, Scania, Volvo and ABB. Sweden´s capital Stockholm is currently producing the highest number of so-called ‘unicorns’ (or billion-dollar tech companies) per capita after Silicon Valley. Sweden is also ranked as the world´s most digitized economy. Investments and advancement in ICT have played a crucial role in diversifying the economy, creating new companies and jobs and developed smart new solutions in various sectors, including energy and transport. Nigeria is the biggest country and economy in Africa, with a population of approximately 200 million, accounting for 47% of West Africa’s population and over 65% of West Africa’s GDP. With abundant natural resources and a young, dynamic population, the country has long played an important role on the continent and it has the potential to be a wider global player in the coming decades. -
Verizon Wireless: Vzaccess Manager User's Guide
Verizon Wireless VZAccess SM Manager User's Guide I Verizon Wireless VZAccess Manager Table of Contents Part I Introduction 3 1 Supported Services........... ........................................................................................................................ 3 2 System Requirements............... .................................................................................................................... 3 3 Setup Overview.... ............................................................................................................................... 4 Part II Installation and Configuration 4 1 The VZAccess.. .Manager.............. .Setup.......... .Program............... ....................................................................................... 5 2 The VZAccess.. .Manager.............. .Setup.......... .Wizard............ .......................................................................................... 6 Part III Using VZAccess Manager 9 1 Features ................................................................................................................................... 9 2 Getting Started..... .............................................................................................................................. 10 3 Connecting ................................................................................................................................... 11 4 Warning Messages............ ...................................................................................................................... -
Mobility Public Safety: Secure Connectivity
› mobility Public Safety: Secure Connectivity Public safety departments demand an adaptable network connectivity solution that provides secure, seamless, and persistent mobile access to 3G, 4G, and Wi-Fi networks. For field personnel, they must stay connected to critical dispatch systems or risk losing valuable time responding to emergencies. As a result, public safety organizations are being challenged with: • Ensuring field personnel aren’t losing valuable time reconnecting to the network • Managing multiple types of software and devices • Securing those devices and the mobile connections made on the field • Keeping data expenses from breaking the budget The Smith Micro End-to-End Solution While many solutions may address one or some of these challenges, QuickLink Mobility® from Smith Micro is an end-to-end solution that incorporates best-of-breed mobile connection management and mobile VPN security. In addition, QuickLink Mobility provides policy management and software deployment in an integrated, easy-to-use solution. Equip Law QuickLink Mobility represents decades of deploying millions of mobility Enforcement management products as the connection management provider to with AT&T, Sprint, Verizon, and many others. It is a time-tested, proven solution that millions have trusted for their secure connection Secure, Persistent management needs. Mobile Access QuickLink Mobility Solves Your Connectivity Key Features Challenges in Public Safety Reliable and persistent connection no matter where you are: Seamless Give field personnel peace