Afterimages of the Floppy Disk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Attribution and Response to Cybercrime/Terrorism/Warfare Susan W
Journal of Criminal Law and Criminology Volume 97 Article 2 Issue 2 Winter Winter 2007 At Light Speed: Attribution and Response to Cybercrime/Terrorism/Warfare Susan W. Brenner Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation Susan W. Brenner, At Light Speed: Attribution and Response to Cybercrime/Terrorism/Warfare, 97 J. Crim. L. & Criminology 379 (2006-2007) This Symposium is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. 0091-4169/07/9702-0379 THE JOURNALOF CRIMINAL LAW & CRIMINOLOGY Vol. 97. No. 2 Copyright 0 2007 by NorthwesternUniversity. Schoolof Low Printedin U.S.A. "AT LIGHT SPEED": ATTRIBUTION AND RESPONSE TO CYBERCRIME/TERRORISM/WARFARE SUSAN W. BRENNER* This Article explains why and how computer technology complicates the related processes of identifying internal (crime and terrorism) and external (war) threats to social order of respondingto those threats. First, it divides the process-attribution-intotwo categories: what-attribution (what kind of attack is this?) and who-attribution (who is responsiblefor this attack?). Then, it analyzes, in detail, how and why our adversaries' use of computer technology blurs the distinctions between what is now cybercrime, cyberterrorism, and cyberwarfare. The Article goes on to analyze how and why computer technology and the blurring of these distinctions erode our ability to mount an effective response to threats of either type. -
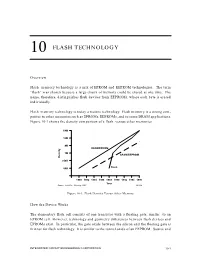
Section 10 Flash Technology
10 FLASH TECHNOLOGY Overview Flash memory technology is a mix of EPROM and EEPROM technologies. The term “flash” was chosen because a large chunk of memory could be erased at one time. The name, therefore, distinguishes flash devices from EEPROMs, where each byte is erased individually. Flash memory technology is today a mature technology. Flash memory is a strong com- petitor to other memories such as EPROMs, EEPROMs, and to some DRAM applications. Figure 10-1 shows the density comparison of a flash versus other memories. 64M 16M 4M DRAM/EPROM 1M SRAM/EEPROM Density 256K Flash 64K 1980 1982 1984 1986 1988 1990 1992 1994 1996 Year Source: Intel/ICE, "Memory 1996" 18613A Figure 10-1. Flash Density Versus Other Memory How the Device Works The elementary flash cell consists of one transistor with a floating gate, similar to an EPROM cell. However, technology and geometry differences between flash devices and EPROMs exist. In particular, the gate oxide between the silicon and the floating gate is thinner for flash technology. It is similar to the tunnel oxide of an EEPROM. Source and INTEGRATED CIRCUIT ENGINEERING CORPORATION 10-1 Flash Technology drain diffusions are also different. Figure 10-2 shows a comparison between a flash cell and an EPROM cell with the same technology complexity. Due to thinner gate oxide, the flash device will be more difficult to process. CMOS Flash Cell CMOS EPROM Cell Mag. 10,000x Mag. 10,000x Flash Memory Cell – Larger transistor – Thinner floating gate – Thinner oxide (100-200Å) Photos by ICE 17561A Figure 10-2. -

Chapter 12: Mass-Storage Systems
Chapter 12: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space Management RAID Structure Disk Attachment Stable-Storage Implementation Tertiary Storage Devices Operating System Issues Performance Issues Objectives Describe the physical structure of secondary and tertiary storage devices and the resulting effects on the uses of the devices Explain the performance characteristics of mass-storage devices Discuss operating-system services provided for mass storage, including RAID and HSM Overview of Mass Storage Structure Magnetic disks provide bulk of secondary storage of modern computers Drives rotate at 60 to 200 times per second Transfer rate is rate at which data flow between drive and computer Positioning time (random-access time) is time to move disk arm to desired cylinder (seek time) and time for desired sector to rotate under the disk head (rotational latency) Head crash results from disk head making contact with the disk surface That’s bad Disks can be removable Drive attached to computer via I/O bus Busses vary, including EIDE, ATA, SATA, USB, Fibre Channel, SCSI Host controller in computer uses bus to talk to disk controller built into drive or storage array Moving-head Disk Mechanism Overview of Mass Storage Structure (Cont.) Magnetic tape Was early secondary-storage medium Relatively permanent and holds large quantities of data Access time slow Random access ~1000 times slower than disk Mainly used for backup, storage of infrequently-used data, transfer medium between systems Kept in spool and wound or rewound past read-write head Once data under head, transfer rates comparable to disk 20-200GB typical storage Common technologies are 4mm, 8mm, 19mm, LTO-2 and SDLT Disk Structure Disk drives are addressed as large 1-dimensional arrays of logical blocks, where the logical block is the smallest unit of transfer. -
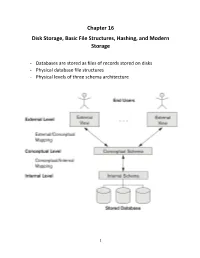
Chapter 16 Disk Storage, Basic File Structures, Hashing, and Modern Storage
Chapter 16 Disk Storage, Basic File Structures, Hashing, and Modern Storage - Databases are stored as files of records stored on disks - Physical database file structures - Physical levels of three schema architecture 1 - The collection of data in a DB must be stored on some storage medium. The DBMS software can retrieve, update, and process this data as needed - Storage media forms a hierarchy 2 -primary, secondary, tertiary, etc.. - offline storage, archiving databases (larger capacity, less cost, slower access, not directly accessible by CPU) Memory Hierarchies and Storage Devices - Cache, static RAM (Prefetch, Pipeline) - Dynamic RAM (main memory( Secondary and Tertiary Storage -mass storage (magnetic disks, CD, DVD (measured in KB, MB, TB, PB - programs are in main memory (DRAM) -permanent databases reside in secondary storage - main memory buffers are used to read and write to secondary storage - Flash memory: non volatile, NAND and NOR flash based - Optical disks: CDs (700MB) and DVDs (4.5 – 15GB), Blue Ray (54GB) - Magnetic Tapes and Juke Boxes Depending upon the intended use and application requirements, data is kept in one or more levels of hierarchy 3 Storage Organization of Database -Large amount of data that must persist for a long period of time (called persistent data) - parts of this data are accessed and processed repeatedly during the storage period - transient data during the period of execution - most DBs are stored on secondary storage (magnetic disks) - DB is too large to fit in main memory - permanent loss on disk is less likely - less cost on disk than primary storage 4 5 6 - A range of cylinders have the same number of sectors per arc. -

Olympus Optical Disc Archiving Systems & Discstor 900 Optical
Olympus Optical Disc Archiving Systems & DiscStor 900 Optical Disc Storage System Solution Overview All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Company – All Pro Solutions, Inc. – Leading manufacturer of automated disc duplicating, printing & publishing systems. – Started in 1996 manufacturing floppy disk duplication systems. – Family-owned and operated. – In South Carolina since 2009. – Provides services like document scanning, imaging, converting. – Expanded into data storage and archiving industry. – Whatever the problem, we find a solution. All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Challenge Worldwide Corporate Data Growth Unstructured text Structured data Source: IDC The Digital Universe 2010 80% of Corporate Data is Unstructured File Data Active Less Active Inactive Hot Cold 10% Warm 20% 70% All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Solution Blu-Ray Disc – The ideal media for long-term archival • Longevity • Capacity - Extendable • Security • Removability • Data Migration • Accessibility • Compliance • Compatibility • Green Technology • Power Consumption Networked Client Workstations LAN Primary Network Servers All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Solution Blu-Ray Disc – The ideal media for long-term archival • Longevity • Capacity - Extendable • Security • Removability • Data Migration • Accessibility • Compliance • Compatibility • Green Technology • Power Consumption Networked Client Workstations Olympus Archiving System LAN DiscStor 900 Storage System Primary Network Servers All Pro Solutions, Inc. -

Secure Data Storage – White Paper Storage Technologies 2008
1 Secure Data Storage – White Paper Storage Technologies 2008 Secure Data Storage - An overview of storage technology - Long time archiving from extensive data supplies requires more then only big storage capacity to be economical. Different requirements need different solutions! A technology comparison repays. Author: Dr. Klaus Engelhardt Dr. K. Engelhardt 2 Secure Data Storage – White Paper Storage Technologies 2008 Secure Data Storage - An overview of storage technology - Author: Dr. Klaus Engelhardt Audit-compliant storage of large amounts of data is a key task in the modern business world. It is a mistake to see this task merely as a matter of storage technology. Instead, companies must take account of essential strategic and economic parameters as well as legal regulations. Often one single technology alone is not sufficient to cover all needs. Thus storage management is seldom a question of one solution verses another, but a combination of solutions to achieve the best possible result. This can frequently be seen in the overly narrow emphasis in many projects on hard disk-based solutions, an approach that is heavily promoted in advertising, and one that imprudently neglects the considerable application benefits of optical storage media (as well as those of tape-based solutions). This overly simplistic perspective has caused many professional users, particularly in the field of long-term archiving, to encounter unnecessary technical difficulties and economic consequences. Even a simple energy efficiency analysis would provide many users with helpful insights. Within the ongoing energy debate there is a simple truth: it is one thing to talk about ‘green IT’, but finding and implementing a solution is a completely different matter. -

Paradise Lost , Book III, Line 18
_Paradise Lost_, book III, line 18 %%%%%%%%%%%%%%%%%%%%%%%% ++++++++++Hacker's Encyclopedia++++++++ ===========by Logik Bomb (FOA)======== <http://www.xmission.com/~ryder/hack.html> ---------------(1997- Revised Second Edition)-------- ##################V2.5################## %%%%%%%%%%%%%%%%%%%%%%%% "[W]atch where you go once you have entered here, and to whom you turn! Do not be misled by that wide and easy passage!" And my Guide [said] to him: "That is not your concern; it is his fate to enter every door. This has been willed where what is willed must be, and is not yours to question. Say no more." -Dante Alighieri _The Inferno_, 1321 Translated by John Ciardi Acknowledgments ---------------------------- Dedicated to all those who disseminate information, forbidden or otherwise. Also, I should note that a few of these entries are taken from "A Complete List of Hacker Slang and Other Things," Version 1C, by Casual, Bloodwing and Crusader; this doc started out as an unofficial update. However, I've updated, altered, expanded, re-written and otherwise torn apart the original document, so I'd be surprised if you could find any vestiges of the original file left. I think the list is very informative; it came out in 1990, though, which makes it somewhat outdated. I also got a lot of information from the works listed in my bibliography, (it's at the end, after all the quotes) as well as many miscellaneous back issues of such e-zines as _Cheap Truth _, _40Hex_, the _LOD/H Technical Journals_ and _Phrack Magazine_; and print magazines such as _Internet Underground_, _Macworld_, _Mondo 2000_, _Newsweek_, _2600: The Hacker Quarterly_, _U.S. News & World Report_, _Time_, and _Wired_; in addition to various people I've consulted. -

An Introduction to Microcontrollers and Embedded Systems
AN INTRODUCTION TO MICROCONTROLLERS AND EMBEDDED SYSTEMS Tyler Ross Lambert MECH 4240/4250 Supplementary Information Last Revision: 6/7/2017 5:30 PM Summary Embedded systems in robotics are the framework that allows electro-mechanical systems to be implemented into modern machines. The key aspects of this framework are C programming in embedded controllers, circuits for interfacing microcontrollers with sensors and actuators, and proper filtering and control of those hardware components. This document will cover the basics of C/C++ programming, including the basics of the C language in hardware interfacing, communication, and algorithms for state machines and controllers. In order to interface these controllers with the world around us, this document will also cover electrical circuits required to operate controllers, sensors, and actuators accurately and effectively. Finally, some of the more commonly used hardware that is interfaced with microcontrollers is gone over. Table of Contents 1. Introduction ....................................................................................................................................... 4 2. Numbering Systems .......................................................................................................................... 5 3. Variable Types and Memory............................................................................................................. 6 4. Basic C/C++ Notes and Code::Blocks ............................................................................................. -

Tangled Web : Tales of Digital Crime from the Shadows of Cyberspace
TANGLED WEB Tales of Digital Crime from the Shadows of Cyberspace RICHARD POWER A Division of Macmillan USA 201 West 103rd Street, Indianapolis, Indiana 46290 Tangled Web: Tales of Digital Crime Associate Publisher from the Shadows of Cyberspace Tracy Dunkelberger Copyright 2000 by Que Corporation Acquisitions Editor All rights reserved. No part of this book shall be reproduced, stored in a Kathryn Purdum retrieval system, or transmitted by any means, electronic, mechanical, pho- Development Editor tocopying, recording, or otherwise, without written permission from the Hugh Vandivier publisher. No patent liability is assumed with respect to the use of the infor- mation contained herein. Although every precaution has been taken in the Managing Editor preparation of this book, the publisher and author assume no responsibility Thomas Hayes for errors or omissions. Nor is any liability assumed for damages resulting from the use of the information contained herein. Project Editor International Standard Book Number: 0-7897-2443-x Tonya Simpson Library of Congress Catalog Card Number: 00-106209 Copy Editor Printed in the United States of America Michael Dietsch First Printing: September 2000 Indexer 02 01 00 4 3 2 Erika Millen Trademarks Proofreader Benjamin Berg All terms mentioned in this book that are known to be trademarks or ser- vice marks have been appropriately capitalized. Que Corporation cannot Team Coordinator attest to the accuracy of this information. Use of a term in this book should Vicki Harding not be regarded as affecting the validity of any trademark or service mark. Design Manager Warning and Disclaimer Sandra Schroeder Every effort has been made to make this book as complete and as accurate Cover Designer as possible, but no warranty or fitness is implied. -

Computer Peripheral Memory System Forecast
OF NBS H^^LK,!,, STAND S. TECH PUBLICATIONS | COMPUTER SUici^CZ^i TECHNOLOGY: COMPUTER PERIPHERAL MEMORY SYSTEM FORECAST QC 100 U57 NBS Special Publication 500-45 #500-45 U.S. DEPARTMENT OF COMMERCE 1979 National Bureau of Standards NATIONAL BUREAU OF STANDARDS The National Bureau of Standards' was established by an act of Congress March 3, 1901 . The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to promote public safety. The Bureau's technical work is performed by the National Measurement Laboratory, the National Engineering Laboratory, and the Institute for Computer Sciences and Technology. THE NATIONAL MEASUREMENT LABORATORY provides the national system of physical and chemical and materials measurement; coordinates the system with measurement systems of other nations and furnishes essential services leading to accurate and uniform physical and chemical measurement throughout the Nation's scientific community, industry, and commerce; conducts materials research leading to improved methods of measurement, standards, and data on the properties of materials needed by industry, commerce, educational institutions, and Government; provides advisory and research services to other Government Agencies; develops, produces, and distributes Standard Reference Materials; and provides calibration services. The Laboratory consists of the following centers: Absolute Physical Quantities^ — Radiation Research — Thermodynamics and Molecular Science — Analytical Chemistry — Materials Science. -

Digital Preservation Guide: 3.5-Inch Floppy Disks Caralie Heinrichs And
DIGITAL PRESERVATION GUIDE: 3.5-Inch Floppy Disks Digital Preservation Guide: 3.5-Inch Floppy Disks Caralie Heinrichs and Emilie Vandal ISI 6354 University of Ottawa Jada Watson Friday, December 13, 2019 DIGITAL PRESERVATION GUIDE 2 Table of Contents Introduction ................................................................................................................................................. 3 History of the Floppy Disk ......................................................................................................................... 3 Where, when, and by whom was it developed? 3 Why was it developed? 4 How Does a 3.5-inch Floppy Disk Work? ................................................................................................. 5 Major parts of a floppy disk 5 Writing data on a floppy disk 7 Preservation and Digitization Challenges ................................................................................................. 8 Physical damage and degradation 8 Hardware and software obsolescence 9 Best Practices ............................................................................................................................................. 10 Storage conditions 10 Description and documentation 10 Creating a disk image 11 Ensuring authenticity: Write blockers 11 Ensuring reliability: Sustainability of the disk image file format 12 Metadata 12 Virus scanning 13 Ensuring integrity: checksums 13 Identifying personal or sensitive information 13 Best practices: Use of hardware and software 14 Hardware -

Unit 5: Memory Organizations
Memory Organizations Unit 5: Memory Organizations Introduction This unit considers the organization of a computer's memory system. The characteristics of the most important storage technologies are described in detail. Basically memories are classified as main memory and secondary memory. Main memory with many different categories are described in Lesson 1. Lesson 2 focuses the secondary memory including the details of floppy disks and hard disks. Lesson 1: Main Memory 1.1 Learning Objectives On completion of this lesson you will be able to : • describe the memory organization • distinguish between ROM, RAM, PROM, EEPROM and • other primary memory elements. 1.2 Organization Computer systems combine binary digits to form groups called words. The size of the word varies from system to system. Table 5.1 illustrates the current word sizes most commonly used with the various computer systems. Two decades ago, IBM introduced their 8-bit PC. This was Memory Organization followed a few years later by the 16-bit PC AT microcomputer, and already it has been replaced with 32- and 64-bit systems. The machine with increased word size is generally faster because it can process more bits of information in the same time span. The current trend is in the direction of the larger word size. Microcomputer main memories are generally made up of many individual chips and perform different functions. The ROM, RAM, Several types of semi- PROM, and EEPROM memories are used in connection with the conductor memories. primary memory of a microcomputers. The main memory generally store computer words as multiple of bytes; each byte consisting of eight bits.