What PDF Security Options Are Available?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Breaking PDF Encryption
Practical Decryption exFiltration: Breaking PDF Encryption Jens Müller Fabian Ising Vladislav Mladenov [email protected] [email protected] [email protected] Ruhr University Bochum, Chair for Münster University of Applied Ruhr University Bochum, Chair for Network and Data Security Sciences Network and Data Security Christian Mainka Sebastian Schinzel Jörg Schwenk [email protected] [email protected] [email protected] Ruhr University Bochum, Chair for Münster University of Applied Ruhr University Bochum, Chair for Network and Data Security Sciences Network and Data Security ABSTRACT Home/Trusted Environment The Portable Document Format, better known as PDF, is one of the Decrypted Document 1. Victim opens 2. Exfiltrating Tax Declaration decrypted content most widely used document formats worldwide, and in order to en- an encrypted PDF file Scrooge McDuck with their password via the Internet sure information confidentiality, this file format supports document TOP SECRET Victim encryption. In this paper, we analyze PDF encryption and show Attacker two novel techniques for breaking the confidentiality of encrypted Victim’s PC documents. First, we abuse the PDF feature of partially encrypted documents to wrap the encrypted part of the document within Figure 1: An overview of the attack scenario: The victim attacker-controlled content and therefore, exfiltrate the plaintext opens an encrypted PDF document and unintentionally once the document is opened by a legitimate user. Second, we abuse leaks the decrypted content to an attacker-controlled server. a flaw in the PDF encryption specification to arbitrarily manipulate The encrypted PDF file was manipulated by the attacker be- encrypted content. -

Ebook HELP FREQUENTLY ASKED QUESTIONS ACCESSING YOUR
eBook HELP FREQUENTLY ASKED QUESTIONS What is the difference between an EPUB and PDF ebook? An EPUB ebook reflows according to the size of the screen it is being read on. A PDF ebook is fixed in layout (to match the print edition) and does not reflow to fit different screen sizes. How long will my ebook take to arrive? If you have purchased an ebook, you will receive two emails: one confirming your order, and the other containing a link to continue to your download. These emails are automated and should arrive immediately after purchase; if you have not received an email within two hours, please email: [email protected] If you have requested a review or inspection copy, it will need to be approved by a Bloomsbury staff member. They will endeavour to process your request as soon as possible, but please be aware that this is done during office hours of 9am – 5pm, Monday to Friday. Can I read an ebook that I’ve downloaded from Bloomsbury.Com on my Kindle? Ebooks purchased on Bloomsbury.com cannot be accessed via a Kindle eReader. To purchase a Bloomsbury book for Kindle, you will need to either: a) Visit the Kindle Store on the Amazon website b) Locate the ebook on Bloomsbury.com and click Buy from Other Retailers. If the ebook is available for Kindle, you will see a link to take you straight to its Amazon page. Can I get a refund on my ebook purchase? If you have not yet downloaded your ebook, then you have the right to a refund for up to 14 days after your purchase. -

Durchleuchtet PDF Ist Der Standard Für Den Austausch Von Dokumenten, Denn PDF-Dateien Sehen Auf
WORKSHOP PDF-Dateien © alphaspirit, 123RF © alphaspirit, PDF-Dateien verarbeiten und durchsuchbar machen Durchleuchtet PDF ist der Standard für den Austausch von Dokumenten, denn PDF-Dateien sehen auf Daniel Tibi, allen Rechnern gleich aus. Für Linux gibt es zahlreiche Tools, mit denen Sie alle Möglich- Christoph Langner, Hans-Georg Eßer keiten dieses Dateiformats ausreizen. okumente unterschiedlichster Art, in einem gedruckten Text, Textstellen mar- denen Sie über eine Texterkennung noch von Rechnungen über Bedie- kieren oder Anmerkungen hinzufügen. eine Textebene hinzufügen müssen. D nungsanleitungen bis hin zu Bü- Als Texterkennungsprogramm für Linux chern und wissenschaftlichen Arbeiten, Texterkennung empfiehlt sich die OCR-Engine Tesseract werden heute digital verschickt, verbrei- Um die Möglichkeiten des PDF-Formats [1]. Die meisten Distributionen führen das tet und genutzt – vorzugsweise im platt- voll auszureizen, sollten PDF-Dateien Programm in ihren Paketquellen: formunabhängigen PDF-Format. Durch- durchsuchbar sein. So durchstöbern Sie l Unter OpenSuse installieren Sie tesse suchbare Dokumente erleichtern das etwa gleich mehrere Dokumente nach be- ractocr und eines der Sprachpakete, schnelle Auffinden einer bestimmten stimmten Wörtern und finden innerhalb z. B. tesseractocrtraineddatagerman. Stelle in der Datei, Metadaten liefern zu- einer Datei über die Suchfunktion des (Das Paket für die englische Sprache sätzliche Informationen. PDF-Betrachters schnell die richtige Stelle. richtet OpenSuse automatisch mit ein.) Zudem gibt es zahlreiche Möglichkei- PDF-Dateien, die Sie mit LaTeX oder Libre- l Für Ubuntu und Linux Mint wählen ten, PDF-Dokumente zu bearbeiten: Ganz Office erstellen, lassen sich üblicherweise Sie tesseractocr und ein Sprachpaket, nach Bedarf lassen sich Seiten entfernen, bereits durchsuchen. Anders sieht es je- wie etwa tesseractocrdeu. -

Quick Start Instructions for Downloading OVERDRIVE Ebooks What You Need to Get Started: Minutes
Quick Start Instructions for Downloading OVERDRIVE eBooks What you need to get started: minutes. If you Continue Browsing” for 30 minutes or more, the 1. A valid library card from any eligible public library in Montgomery selected titles will disappear from your cart. County. Check with your local public library. 10. Click on “Proceed to Checkout.” 2. Access to the Internet (preferably broadband) 11. Make sure that Adobe Digital Editions is open. 3. Free downloadable software for the computer and/or device on 12. If you are not yet logged in, you will be prompted to do so. which you wish to use the material you download from this site 13. Your books are now ready to download. Large files may take some time to download depending upon the speed of Steps to get started: your connection and the size of the file. You can download 1. Log on to the library’s website at www.mc-npl.org. the complete book with one download. 14. To transfer your Adobe eBook from your computer to your 2. Click on the download audiobooks eBooks link compatible eBook device using Adobe Digital Editions: 3. Download and Install the Free Software to your computer. a. Some devices must be turned on and connected to your If you have a PC or Mac, download Adobe Digital Editions . computer before you open the Adobe Digital Editions . If you have an iPhone or Android, download OverDrive Media software. Console app for iPhone or Android b. Open the Adobe Digital Editions software. Activate the software/app on your computer/device. -

Reading EPUB/PDF Books Using Adobe Digital Editions
Reading EPUB/PDF Books Using Adobe Digital Editions You can check out EPUB and PDF eBooks within Axis 360 and read them using Adobe Digital Editions (ADE) on your desktop and/or eReader device via a USB connection. To download ADE for your desktop, click here. For ADE-specific help, click here. Check Out EPUB/PDF Titles 1. Find the EPUB/PDF title you wish to check out on your school or library’s Axis 360 website. 2. Select EPUB or PDF for the Format and click Checkout. 3. Click OK on the confirmation message to proceed. If you haven’t already downloaded ADE to your desktop, click on the App Zone link within the confirmation message to find a download link. 4. Click the Download link that appears next to your book and save it to your desktop. Make a note of where you saved the file, as you will need to access it to read your eBook. Read EPUB/PDF eBooks On Your Desktop Double-click on your downloaded eBook file. It will automatically open within ADE and you can begin reading from there. You can also set ADE to automatically open ACSM files after downloading. Read EPUB/PDF eBooks On Your E-Ink Reader 1. Double-click on your downloaded eBook file. It will automatically open within ADE. 2. Connect your e-ink reader to your computer via a USB cable. You should see your eReader listed under Devices. 3. Drag the eBook title you wish to transfer to your eReader over the name of your eReader. -

Reading, Discovering, Sharing Ebooks
Reading Discovering Sharing Reading, Discovering, Sharing eBooks Sayamindu Dasgupta One Laptop Per Child FOSS.IN 2009 Sayamindu Dasgupta Reading, Discovering, Sharing eBooks Reading A Brief History & Current Status Discovering The EPUB standard Sharing EPUB Readers A Brief History Can be traced back to 1971 (Project Gutenberg) Considered a niche area/product till recent times Major pain points Multiple formats, some proprietary, some not Lack of specialized devices Display (mostly resolution related) issues Sayamindu Dasgupta Reading, Discovering, Sharing eBooks Reading A Brief History & Current Status Discovering The EPUB standard Sharing EPUB Readers A Brief History Can be traced back to 1971 (Project Gutenberg) Considered a niche area/product till recent times Major pain points Multiple formats, some proprietary, some not Lack of specialized devices Display (mostly resolution related) issues Sayamindu Dasgupta Reading, Discovering, Sharing eBooks Reading A Brief History & Current Status Discovering The EPUB standard Sharing EPUB Readers A Brief History Can be traced back to 1971 (Project Gutenberg) Considered a niche area/product till recent times Major pain points Multiple formats, some proprietary, some not Lack of specialized devices Display (mostly resolution related) issues Sayamindu Dasgupta Reading, Discovering, Sharing eBooks Reading A Brief History & Current Status Discovering The EPUB standard Sharing EPUB Readers A Brief History Can be traced back to 1971 (Project Gutenberg) Considered a niche area/product till recent times -

To Kindle in Ten Steps
Build Your Own eBooks For Free! A Step-by-Step Guide to Formatting and Converting Your Manuscript into ePub and Kindle Books Using Free Software M. A. Demers Published by Egghead Books, Canada www.mademers.com Copyright © 2017 Michelle A. Demers INSI 0000 0003 5669 426X Published by Egghead Books, 2017 All rights reserved under International and Pan-American Copyright Conventions. No part of this book may be reproduced in any form or by any electronic or mechanical means, including information storage and retrieval systems, without permission in writing from the author, except by reviewer, who may quote brief passages in a review. Cover design by Michelle A. Demers. Background design based on an image by Gerd Altmann. Many thanks. Library and Archives Canada Cataloguing in Publication Demers, M. A., 1964-, author Build your own eBooks for free! : a step-by-step guide to formatting and converting your manuscript into ePub and Kindle books using free software / M.A. Demers. Issued in print and electronic formats. ISBN 978-0-9916776-7-2 (softcover).--ISBN 978-0-9916776-8-9 (EPUB).-- ISBN 978-0-9916776-9-6 (Kindle) 1. Electronic publishing--Handbooks, manuals, etc. 2. Self-publishing-- Handbooks, manuals, etc. 3. Kindle (Electronic book reader). 4. Electronic books. 5. File conversion (Computer science)--Handbooks, manuals, etc. I. Title. Z286.E43.D446 2017 070.50285’416 C2017-901669-5 C2017-901670-9 Contents Is This Book For You? 1 What You Will Need 3 eBook Development 6 Characteristics of eBooks 7 Reflowable eBooks 7 Fixed Layout eBooks -

Insight MFR By
Manufacturers, Publishers and Suppliers by Product Category 11/6/2017 10/100 Hubs & Switches ASCEND COMMUNICATIONS CIS SECURE COMPUTING INC DIGIUM GEAR HEAD 1 TRIPPLITE ASUS Cisco Press D‐LINK SYSTEMS GEFEN 1VISION SOFTWARE ATEN TECHNOLOGY CISCO SYSTEMS DUALCOMM TECHNOLOGY, INC. GEIST 3COM ATLAS SOUND CLEAR CUBE DYCONN GEOVISION INC. 4XEM CORP. ATLONA CLEARSOUNDS DYNEX PRODUCTS GIGAFAST 8E6 TECHNOLOGIES ATTO TECHNOLOGY CNET TECHNOLOGY EATON GIGAMON SYSTEMS LLC AAXEON TECHNOLOGIES LLC. AUDIOCODES, INC. CODE GREEN NETWORKS E‐CORPORATEGIFTS.COM, INC. GLOBAL MARKETING ACCELL AUDIOVOX CODI INC EDGECORE GOLDENRAM ACCELLION AVAYA COMMAND COMMUNICATIONS EDITSHARE LLC GREAT BAY SOFTWARE INC. ACER AMERICA AVENVIEW CORP COMMUNICATION DEVICES INC. EMC GRIFFIN TECHNOLOGY ACTI CORPORATION AVOCENT COMNET ENDACE USA H3C Technology ADAPTEC AVOCENT‐EMERSON COMPELLENT ENGENIUS HALL RESEARCH ADC KENTROX AVTECH CORPORATION COMPREHENSIVE CABLE ENTERASYS NETWORKS HAVIS SHIELD ADC TELECOMMUNICATIONS AXIOM MEMORY COMPU‐CALL, INC EPIPHAN SYSTEMS HAWKING TECHNOLOGY ADDERTECHNOLOGY AXIS COMMUNICATIONS COMPUTER LAB EQUINOX SYSTEMS HERITAGE TRAVELWARE ADD‐ON COMPUTER PERIPHERALS AZIO CORPORATION COMPUTERLINKS ETHERNET DIRECT HEWLETT PACKARD ENTERPRISE ADDON STORE B & B ELECTRONICS COMTROL ETHERWAN HIKVISION DIGITAL TECHNOLOGY CO. LT ADESSO BELDEN CONNECTGEAR EVANS CONSOLES HITACHI ADTRAN BELKIN COMPONENTS CONNECTPRO EVGA.COM HITACHI DATA SYSTEMS ADVANTECH AUTOMATION CORP. BIDUL & CO CONSTANT TECHNOLOGIES INC Exablaze HOO TOO INC AEROHIVE NETWORKS BLACK BOX COOL GEAR EXACQ TECHNOLOGIES INC HP AJA VIDEO SYSTEMS BLACKMAGIC DESIGN USA CP TECHNOLOGIES EXFO INC HP INC ALCATEL BLADE NETWORK TECHNOLOGIES CPS EXTREME NETWORKS HUAWEI ALCATEL LUCENT BLONDER TONGUE LABORATORIES CREATIVE LABS EXTRON HUAWEI SYMANTEC TECHNOLOGIES ALLIED TELESIS BLUE COAT SYSTEMS CRESTRON ELECTRONICS F5 NETWORKS IBM ALLOY COMPUTER PRODUCTS LLC BOSCH SECURITY CTC UNION TECHNOLOGIES CO FELLOWES ICOMTECH INC ALTINEX, INC. -

J: Formatting with Jutoh
Self-Publishing: Easy as ABC Meredith Bond www.anessabooks.com [email protected] J: Formatting with Jutoh For those of you who are not so computer savvy or just want an easier way of formatting your book, you can also convert your Word document into an epub and mobi file using the paid program, Jutoh. Jutoh is a program created for authors to convert their work into an ebook. That is its originally intention, unlike Calibre which has been used that way despite the fact that that’s not what it was meant for. Because it was meant for authors, it has a lot of great features which make formatting beautiful books easy, as you’re about to see. It’s not very expensive ($39) and has a devoted following of people who happily share information on how to use the program—there’s even a Yahoo group devoted to it where the developer answers questions that others cannot. Jutoh will use the clean, formatted document you created at the beginning of this lesson to organize and create your ebook. Basically, you are doing most of the formatting in Microsoft Word and then adding in all the fun stuff using Jutoh. If you want, you can directly import your cleaned Word document into Jutoh and then add all the styles and page breaks there, but Word is easier to work in (the window is larger and the text is easier to see). Before you begin to read this long and detailed explanation of how to format your book in Jutoh, please know that I created a video that shows you how to do all of this. -

Locklizard Safeguard Secure PDF Viewer
Safeguard Viewer Product Manual for Windows Version 3.0 Revision 1.09 Table of Contents INSTALLATION & REGISTRATION ......................................................... 5 INTRODUCTION ............................................................................................. 5 INSTALLATION PRE-REQUISITES ......................................................................... 5 INSTALLING THE VIEWER.................................................................................. 6 INSTALLING THE VIEWER IN CORPORATE ENVIRONMENTS ......................................... 9 1.4.1 Silent (remote) Installation ............................................................................................................................ 9 1.4.2 License File Registration (silent mode) ..................................................................................................... 9 1.4.3 Disabling Automatic Updates ...................................................................................................................... 10 MANAGING PROXY SETTINGS ......................................................................... 10 1.5.1 Proxy server manual entry settings.......................................................................................................... 12 1.5.2 Proxy server installation settings.............................................................................................................. 13 REGISTERING THE VIEWER LICENSE ................................................................... 15 -
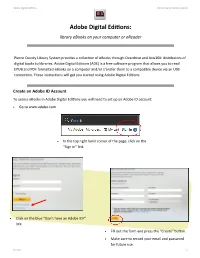
Adobe Digital Editions: Library Ebooks on Your Computer Or Ereader
Adobe Digital Editions Pierce County Library System Adobe Digital Editions: library eBooks on your computer or eReader Pierce County Library System provides a collection of eBooks through Overdrive and Axis360: distributors of digital books to libraries. Adobe Digital Editions (ADE) is a free software program that allows you to read EPUB and PDF formatted eBooks on a computer and/or transfer them to a compatible device via an USB connection. These instructions will get you started using Adobe Digital Editions. Create an Adobe ID Account To access eBooks in Adobe Digital Editions you will need to set up an Adobe ID account. Go to www.adobe.com. In the top right hand corner of the page, click on the “Sign in” link. Click on the blue “Don’t have an Adobe ID?” link. Fill out the form and press the “Create” button. Make sure to record your email and password for future use. MA 04/13 1 Adobe Digital Editions Pierce County Library System Download and Install Adobe Digital Editions (ADE) On the Adobe website (www.adobe.com) type “adobe digital editions” into the search box in the upper right hand corner of the page. Click on Adobe Digital Editions when it appears in the results list. Click on the “Download Now” link. Select the appropriate version of the ADE software for your computer: Windows or Macintosh (Apple), and allow the application to download and install. MA 04/13 2 Adobe Digital Editions Pierce County Library System Start the Adobe Digital Editions program. You may be prompted to enter your Adobe ID and password. -
Adobe® Ebook Platform: Authoring and Delivering Ebooks Across Devices
Adobe® eBook Platform White Paper Adobe® eBook Platform: Authoring and delivering eBooks across devices Table of contents Consumer preferences and publisher requirements 1: Consumer preferences and publisher require- The increasing popularity of eBooks demonstrates that they are not a passing phenomenon. With this rise in ments adoption comes a solidifying of consumer expectations: consumers want more from eBook experiences 2: The Adobe eBook than they’ve been offered in the past. As the market takes hold, it’s becoming clear that eBook readers Platform want: 3: How the Adobe eBook Platform helps meet • An open environment where readers can download books from a variety of sources consumer demands • Interoperability among devices 4: How the Adobe eBook • Ability to share books with friends Platform helps publish- ers Consumers are frustrated by “walled garden” approaches that limit their reading to a specific device and 4: E-reading apps for prevent sharing books with others. Amazon Kindle users, for example, cannot download EPUB files from their Apple devices public libraries to their devices. And those who want to access Apple’s iBookstore can do so only via their 5: Case study: The interoperability of the Apple devices, not PCs or Android devices. In fact, according to the Book Industry Study Group (BISG) report, Adobe eBook Platform “Consumer Attitudes Towards E-Book Reading – Part 2”: 5: Summary 5: For more information The inability to read e-books on different devices remained the biggest problem e-book acquirers identified about e-readers. Publishers have their own requirements as they meet the increase in consumer demand for eBooks.