Bash − the GNU Shell*
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -
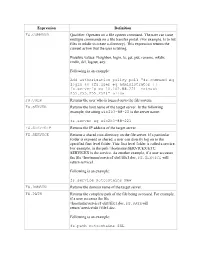
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Programming Project #2 Due: Thursday, May 13Th, 2004, 11:59 Pm
CS155: Computer Security Spring 2004 Programming Project #2 Due: Thursday, May 13th, 2004, 11:59 pm 1 Introduction 1.1 Summary In this project, you will write Josh, the journaling operator shell. Josh is a setuid-root shell that allows users to undertake a subset of root’s capabilities. Your starting point is OSH, a minimal shell developed by Gunnar Ritter. You may work alone, or in pairs. You should not collaborate with others outside your group. You will use the Boxes system again. Remember to test your Josh in a closedbox. This as- signment specification is quite long, but much of it is intended to clarify points of confusion raised by previous years’ students. Please be sure to read it carefully before beginning to code. 1.2 The Problem As discussed in class, the classical Unix permissions model does not manage privilege delegation effectively. To perform routine administrative tasks (such as cleaning out the /tmp directory), one must possess the root password, and can therefore perform other, undesirable actions (such as reading users’ mail). This limitation manifests itself most acutely in large Unix installations, where there are typically many administrators tasked with various duties. Finer granularity of access is required for such systems, along with the ability to correctly log the important events for post-attack analysis. Various systems have been devised to overcome this limitation, and allow unprivileged users to un- dertake some subset of root’s capabilities. A commonly-used example is Sudo (http://www.sudo.ws/). We will take an approach more like that taken by OSH, the Operator Shell by Michael Neuman. -

Learning Objectives ECHO Commands. Command. 10. Explain
. SA Learning Objectives After completing this chapter you will be able to: 1. List commands used in batch files. 2. List and explain batch file rules. 3. Use a batch file with a shortcut. 3. Explore the function of the REM, 4. Use the SHIFT command to move param- ECHO commands. eters. 4. Explain the use of batch files with shortcuts. 5. Use the IF command with strings for condi- 5. Explain the purpose and function of the tional processing. GOTO command. 6. Test for null values in a batch file. 6. Explain the purpose and function of the 7. Use the IF EXIST /IF SHIFT command. test for the existence of a file or a 7. Explain the purpose and function of the IF subdirectory. command. 8. Use the SET command. 8. Explain the purpose and function of the IF 9. Use the environment and environmental EXIST /IF variables in batch files. 9. Explain the purpose and function of the IF 10. Use the IF ERRORLEVEL command ERRORLEVEL command. XCOpy to write a batch file for testing exit 10. Explain the purpose and function of writing codes. programs. 11. Use the FOR...IN...OO command for repeti- 11. Explain the purpose and function of the tive processing. environment and environmental variables. 12. Use the CALL command in a batch file. 12. Explain the use of the SET command. 13. Explain the purpose and function of the Chapter Overview FOR...IN...OO command. You learned in Chapter 10 how to write simple 14. Explain the purpose and function of the batch files and use replaceable parameters. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -

Niagara Networking and Connectivity Guide
Technical Publications Niagara Networking & Connectivity Guide Tridium, Inc. 3951 Westerre Parkway • Suite 350 Richmond, Virginia 23233 USA http://www.tridium.com Phone 804.747.4771 • Fax 804.747.5204 Copyright Notice: The software described herein is furnished under a license agreement and may be used only in accordance with the terms of the agreement. © 2002 Tridium, Inc. All rights reserved. This document may not, in whole or in part, be copied, photocopied, reproduced, translated, or reduced to any electronic medium or machine-readable form without prior written consent from Tridium, Inc., 3951 Westerre Parkway, Suite 350, Richmond, Virginia 23233. The confidential information contained in this document is provided solely for use by Tridium employees, licensees, and system owners. It is not to be released to, or reproduced for, anyone else; neither is it to be used for reproduction of this control system or any of its components. All rights to revise designs described herein are reserved. While every effort has been made to assure the accuracy of this document, Tridium shall not be held responsible for damages, including consequential damages, arising from the application of the information given herein. The information in this document is subject to change without notice. The release described in this document may be protected by one of more U.S. patents, foreign patents, or pending applications. Trademark Notices: Metasys is a registered trademark, and Companion, Facilitator, and HVAC PRO are trademarks of Johnson Controls Inc. Black Box is a registered trademark of the Black Box Corporation. Microsoft and Windows are registered trademarks, and Windows 95, Windows NT, Windows 2000, and Internet Explorer are trademarks of Microsoft Corporation. -

SUPERTRAK EX4650, EX8650, EX8654, EX8658, EX16650 USER MANUAL Version 3.0 SR3 Supertrak EX Series User Manual
SUPERTRAK EX4650, EX8650, EX8654, EX8658, EX16650 USER MANUAL Version 3.0 SR3 SuperTrak EX Series User Manual Copyright © 2009 Promise Technology, Inc. All Rights Reserved. Copyright by Promise Technology, Inc. (Promise Technology). No part of this manual may be reproduced or transmitted in any form without the expressed, written permission of Promise Technology. Trademarks Promise, and the Promise logo are registered in U.S. Patent and Trademark Office. All other product names mentioned herein may be trademarks or registered trademarks of their respective companies. Important data protection information You should back up all data before installing any drive controller or storage peripheral. Promise Technology is not responsible for any loss of data resulting from the use, disuse or misuse of this or any other Promise Technology product. Notice Although Promise Technology has attempted to ensure the accuracy of the content of this manual, it is possible that this document may contain technical inaccuracies, typographical, or other errors. Promise Technology assumes no liability for any error in this publication, and for damages, whether direct, indirect, incidental, consequential or otherwise, that may result from such error, including, but not limited to loss of data or profits. Promise Technology provides this publication “as is” without warranty of any kind, either express or implied, including, but not limited to implied warranties of merchantability or fitness for a particular purpose. The published information in the manual is subject to change without notice. Promise Technology reserves the right to make changes in the product design, layout, and driver revisions without notification to its users. This version of the User Manual supersedes all previous versions. -

The Linux Command Line
The Linux Command Line Second Internet Edition William E. Shotts, Jr. A LinuxCommand.org Book Copyright ©2008-2013, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, 171 Second Street, Suite 300, San Fran- cisco, California, 94105, USA. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. This book is also available in printed form, published by No Starch Press and may be purchased wherever fine books are sold. No Starch Press also offers this book in elec- tronic formats for most popular e-readers: http://nostarch.com/tlcl.htm Release History Version Date Description 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. 09.11 November 19, 2009 Fourth draft with almost all reviewer feedback incorporated and edited through chapter 37. 09.10 October 3, 2009 Third draft with revised table formatting, partial application of reviewers feedback and edited through chapter 18. 09.08 August 12, 2009 Second draft incorporating the first editing pass. 09.07 July 18, 2009 Completed first draft. Table of Contents Introduction....................................................................................................xvi -

Windows Command Line?
Table of contents 1. Why an ebook on the Windows Command Line? 2. Make an example directory 3. A little exercise: open the Windows Command Prompt window and go to the example directory 3.1 The prompt 3.2 Moving into a (sub)directory 4. Pattern-matching 5. Command ‘DIR’ and Glob patterns 6. The ‘COPY’ command and Glob patterns 6.1 Copy files from the current directory into a subdirectory 6.2 Copy files from the current directory into a subdirectory in binary mode 6.3 Combine ASCII-files and put the result into a subdirectory 6.4 Combine binary files and put the result into a subdirectory 6.5 Are the files copied correctly? 6.6 Copy a selection of files with the ‘FOR’ loop 7. The ‘DEL’ command and Glob patterns 7.1 Delete files from the current directory 7.2 Delete files from the subdirectory ‘my Doc’ -1 7.3 Delete files from the subdirectory ‘my Doc’ -2 7.3.1 An alternative 7.3.2 ROBOCOPY 8. Passing multiple commands 9. The ‘REN’ or ‘RENAME’ command 9.1 Change subdirectory name 9.2 Change file extensions 9.3 Modify filenames from the current directory: basic examples 9.4 Truncate a filename by using ‘?’ 9.5 Modify filenames in the subdirectory ‘my Doc’: basic example 10. More complex replacements 10.1 Add a prefix to filenames with the same characters at the beginning 10.2 Add a prefix to filenames with the same extensions 10.3 Add a suffix at the end of filenames with the same extensions 10.4 Substitute a character in a specific position 11. -

Yes, SAS Can Do! Manage External Files with SAS Programming
Yes, SAS® Can Do! --- Manage External Files With SAS Programming (Paper 3262 - 2015) Justin Jia, TransUnion Canada Amanda Lin, CIBC, Canada April 26-29, 2015 Dallas, Texas, USA Overview . Introduction . I. System Statements and Shell Commands X command and statement / %Sysexec macro statement/ Systask command . II. SAS Piping Functionality . III. SAS Call System Routine and System Function . IV. New SAS File Management Functions DCREATE function/ RENAME function/ FDELETE function/DLCREATEDIR option . V. Application Examples . Conclusion 2 Introduction . A good file management system is important for efficient documentation and project management. It would be beneficial to automate and standardize repetitive routine tasks via SAS programming: create, rename, move, copy, delete. Proc DATASETS, though powerful, is only effective for managing SAS files. How can we manage non-SAS external files or directories? 3 I. System Statements and Shell Commands . X <'command '> ; X " mkdir "&path.\ WLMU 999" "; . %Sysexec macro statement %sysexec mkdir "&path.\WLMU 999" ; . Systask statement systask command %unquote(%str(%') mkdir "&path.\WLMU 999" %str(%')); 4 Pros / Cons of System Statements/Commands . Advantages Not easy to monitor the execution status of submitted commands They use simple and easy DOS or (no return code). Unix commands. They cannot perform conditional Able to perform all kinds of file management tasks (create, execution since they are global. rename, copy, move, delete). data _null_; They are global commands and Action= 0; can exist anywhere in a SAS if Action=1 then do; program. X "mkdir "&path.\Try“ " ; . Disadvantages end; run; The X command will be executed every They prompt annoying flashing DOS window. time and the new directory Try will be created regardless of the value of Action.