Prediction of Pneumonia Disease by Using Deep Convolutional Neural Networks R
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fuzzy Base Artificial Neural Network Model for Text Extraction from Images
Journal of Critical Reviews ISSN- 2394-5125 Vol 7, Issue 6, 2020 Review Article FUZZY BASE ARTIFICIAL NEURAL NETWORK MODEL FOR TEXT EXTRACTION FROM IMAGES V. Lakshman Narayana1, B. Naga Sudheer2, Venkata Rao Maddumala3,P.Anusha4 1Department of Information Technology, Vignan’s Nirula Institute of Technology & Science for Women, Peda Palakaluru, Guntur, Andhra Pradesh, India. [email protected] 2Asst.Professor, Department of IT, Vignan's Foundation for Science, Technology & Research (Deemed to be University), Vadlamudi, Guntur, Andhra Pradesh, India. [email protected] 3Department of Information Technology, Vignan’s Nirula Institute of Technology & Science for Women, Peda Palakaluru, Guntur, Andhra Pradesh, India. 4Department of Information Technology, Vignan’s Nirula Institute of Technology & Science for Women, Peda Palakaluru, Guntur, Andhra Pradesh, India. Received: 15.02.2020 Revised: 19.03.2020 Accepted: 05.04.2020 Abstract Content Extraction assumes a significant job in discovering essential and important data. Content extraction includes discovery, restriction, following, binarization, extraction, improvement and acknowledgment of the content from the given picture. This paper proposes a bi-leveled picture characterization framework to group printed and transcribed reports into totally unrelated predefined classes. In the present article, we propose a Fuzzy guideline guided novel strategy that is utilitarian without any outer intercession during execution. The Fuzzy validation processor utilizes subtleties of divider speed and force, just as change, to decide if the deliberate reverberation signal part to be separated genuinely speaks to the divider speed as it were. Test results propose that this methodology is a proficient one in contrast with various different strategies widely tended to in writing. -
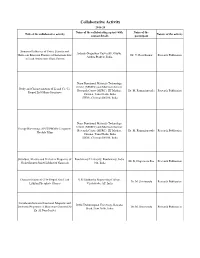
Final 12112020Web Branch Wise Collaborative.Xlsx
Collaborative Activity 2019-20 Name of the collaborating agency with Name of the Title of the collaborative activity Nature of the activity contact details participant Structural Influence of Yttria, Scandia and Acharya Nagarjuna University, Guntur, Hafnia on Emission Features of Samarium Ions Dr. V. Ravi Kumar Research Publication Andhra Pradesh, India. in Lead Antimonate Glass System Nano Functional Materials Technology Centre (NFMTC) and Materials Science Study and Characterization of Li and Co, Co- Research Centre (MSRC), IIT Madras, Dr. M. Ramanjaneyulu Research Publication Doped ZnO Micro Structures Chennai, Tamil Nadu, India (IITM), Chennai 600036, India Nano Functional Materials Technology Centre (NFMTC) and Materials Science Energy Harvesting of PZT/PMMA Composite Research Centre (MSRC), IIT Madras, Dr. M. Ramanjaneyulu Research Publication Flexible Films Chennai, Tamil Nadu, India (IITM), Chennai 600036, India Structural, Electric and Dielectric Properties of Pondicherry University, Pondicherry, India. Dr. B. Nageswara Rao Research Publication Nickel Doped Spinel LiMn2O4 Nanorods 014, India Characterization of Cr3+ Doped Zinc Lead V R Siddhartha Engineering College, Dr. M. Srinivasulu Research Publication Lithium Phosphate Glasses Vijayawada, AP, India Correlation between Structural, Magnetic and Delhi Technological University, Bawana Dielectric Properties of Microwave Sintered Ni- Dr. M. Srinivasulu Research Publication Road, New Delhi, India Zn-Al Nanoferrites An Efficient Synthesis of Darunavir Granules India Limited – R&D Center, Substantially Free from Impurities: Synthesis Dr. N. Srinivasu Research Publication Hyderabad, India. and Characterization of Novel Impurities Design, synthesis and Anti-Tumour Activity of Acharya Nagarjuna University, Guntur, Dr. N. Srinivasu Research Publication New Pyrimidinepyrrole Appended Triazoles A.P., India. Determination of Flecainide Acetate and its NACL Industries Limited (R&D Center), Dr. -

2021 Placement Record
2021 Placement Record Package Lakhs Parent Phone Eamcet/ ECET / ICET Name and Address of the Student Photo Branch Selected Company per Number Rank Annum DASARI AMRUTHA CHOWDARY CSE TCS Digital 7 9441650671 15504 SANGADI GUNTA, GUNTUR KANNEGANTI TEJASWI CSE TCS Digital 7 7416709879 14559 TANK BUND ROAD, ITHANAGAR DEEPAK REDDY KOLAGATLA CSE Wiley Next, Virtusa Polaris 7, 4 7730052939 11632 BRODIPET GUNTUR VISWANATH SAI VENKATESH TCS Digital, Global Edge CSE 7, 3.5 9885646180 36600 ARUNDALPET GUNTUR Software Package Lakhs Parent Phone Eamcet/ ECET / ICET Name and Address of the Student Photo Branch Selected Company per Number Rank Annum SURAPARAJU DURGA ANUSHA CSE TCS Digital, TechM 7, 3.5 9985263502 31409 TARAKA RAMA NAGAR, 2ND LINE GUNTUR GOPINADH CHENNAM ECE ACS Solutions, Revature 5.16, 5 9295450402 14266 BHAVANIPURAM, GUNTUR NAKKANABOINA RAJESH ECE ACS Solutions, Accenture 5.16, 4.5 9491297579 51603 SIMHADRIPURAM MUSUNURU VAKKAPATLA GAYATHRI ECE ACS Solutions, Accenture 5.16, 4.5 9441692691 67106 MORRISPET TENALI JONNADULA NAGA ROHIT ECE ACS Solutions, TechM 5.16, 3.5 9290509560 37073 CHINARAVURU THOTA TENALI SK.JAKEER SANA CSE ADP, Revature 5.05, 5 9390636558 39501 GOPI DESI VARI STREET TENALI M.THULASI IT ADP, Revature 5.05, 5 9963776316 32514 MAINROAD MADDIPADU JANAPALA SUKANYA EEE Revature 5 9502089258 35653 VENGALAYA PALEM GUNTUR Package Lakhs Parent Phone Eamcet/ ECET / ICET Name and Address of the Student Photo Branch Selected Company per Number Rank Annum PALLE MALLIKARJUNA -

South India to North America Journey of Journalist
South India to North America Journey of Journalist South India to North America Journey of Journalist Narisetti Innaiah South India to North America Journey of Journalist Page 1 Contents 1. Childhood - Sweet and Sour 4 2. Twists and turns at college level 11 3. College life is not that smooth (1953-58) 15 4. University Education 28 5. Taste of Politics 32 6. Untrained teacher 38 7. Entered Married Life 43 8. Encounter Different Personalities 47 9. Beyond Religion 49 10. A.B.Shah - Leader of Secular Movement 52 11. Joyful Life - Naveena, Raju 56 12. Can Reason Appeal 58 13. Komala Unique Person 60 14. Meandering into Research 63 15. Facing New Phase 66 16. Friendship with Chief Justice 68 17. A Decade of Experience 71 18. Reporting Legislative discussions 74 19. Helping Elected Representatives 78 20. Joyful Humanism 80 19. Bureau chief of Telugu daily 82 20. V.R. Narla dedicates his last play 89 21. Writer with human face 92 22. Chief Minister with difference 95 23. A friend in deed 98 South India to North America Journey of Journalist Page 2 24. Facing hardships 104 25. Encounter with academic cheats 107 26. At last owned a house 113 27. Unscientific alternatives 116 28. Playing with blind believers 119 29. Widening humanist horizon 128 30. Friendship with Rationalist, Skeptics 135 31. Feeling the Cosmos 141 32. India once again 145 33. Regional Associations in America 154 34. Thinkers groups 157 36. A story of Thesis 160 37. Pictures to remember South India to North America Journey of Journalist Page 3 111.1.. -

Annexure 1B 18416
Annexure 1 B List of taxpayers allotted to State having turnover of more than or equal to 1.5 Crore Sl.No Taxpayers Name GSTIN 1 BROTHERS OF ST.GABRIEL EDUCATION SOCIETY 36AAAAB0175C1ZE 2 BALAJI BEEDI PRODUCERS PRODUCTIVE INDUSTRIAL COOPERATIVE SOCIETY LIMITED 36AAAAB7475M1ZC 3 CENTRAL POWER RESEARCH INSTITUTE 36AAAAC0268P1ZK 4 CO OPERATIVE ELECTRIC SUPPLY SOCIETY LTD 36AAAAC0346G1Z8 5 CENTRE FOR MATERIALS FOR ELECTRONIC TECHNOLOGY 36AAAAC0801E1ZK 6 CYBER SPAZIO OWNERS WELFARE ASSOCIATION 36AAAAC5706G1Z2 7 DHANALAXMI DHANYA VITHANA RAITHU PARASPARA SAHAKARA PARIMITHA SANGHAM 36AAAAD2220N1ZZ 8 DSRB ASSOCIATES 36AAAAD7272Q1Z7 9 D S R EDUCATIONAL SOCIETY 36AAAAD7497D1ZN 10 DIRECTOR SAINIK WELFARE 36AAAAD9115E1Z2 11 GIRIJAN PRIMARY COOPE MARKETING SOCIETY LIMITED ADILABAD 36AAAAG4299E1ZO 12 GIRIJAN PRIMARY CO OP MARKETING SOCIETY LTD UTNOOR 36AAAAG4426D1Z5 13 GIRIJANA PRIMARY CO-OPERATIVE MARKETING SOCIETY LIMITED VENKATAPURAM 36AAAAG5461E1ZY 14 GANGA HITECH CITY 2 SOCIETY 36AAAAG6290R1Z2 15 GSK - VISHWA (JV) 36AAAAG8669E1ZI 16 HASSAN CO OPERATIVE MILK PRODUCERS SOCIETIES UNION LTD 36AAAAH0229B1ZF 17 HCC SEW MEIL JOINT VENTURE 36AAAAH3286Q1Z5 18 INDIAN FARMERS FERTILISER COOPERATIVE LIMITED 36AAAAI0050M1ZW 19 INDU FORTUNE FIELDS GARDENIA APARTMENT OWNERS ASSOCIATION 36AAAAI4338L1ZJ 20 INDUR INTIDEEPAM MUTUAL AIDED CO-OP THRIFT/CREDIT SOC FEDERATION LIMITED 36AAAAI5080P1ZA 21 INSURANCE INFORMATION BUREAU OF INDIA 36AAAAI6771M1Z8 22 INSTITUTE OF DEFENCE SCIENTISTS AND TECHNOLOGISTS 36AAAAI7233A1Z6 23 KARNATAKA CO-OPERATIVE MILK PRODUCER\S FEDERATION -
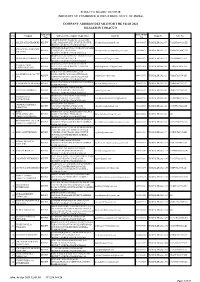
Print Report
TOBACCO BOARD::GUNTUR (MINISTRY OF COMMERCE & INDUSTRIES, GOVT. OF INDIA) COMPANY ADDRESS DETAILS FOR THE YEAR 2021 DEALER IN TOBACCO Apllication phone/Mobile S.No. Company Address of the company (Regd.office) Email-id Regn.No. GST.No. Type No "ALLIED HOUSE" DOOR NO.10-2-26 2ND 1 ALLIED AGRO TRADERS RENEW LANE, SAMBASIVAPET GUNTUR,GUNTUR [email protected] 9866146097 TB/DEALER/2021/07 37AADFA6861A1ZR DISTRICT,ANDHRA PRADESH,522001 OPPOSITE OLD APF.NO.24 TOBACCO BOARD ANNAPURNA TOBACCO 2 RENEW TANGUTURU ,PRAKASAM [email protected] 9949114692 TB/DEALER/2021/19 37AHOPN8204C1ZB COMPANY DISTRICT,ANDHRA PRADESH,523274 DOOR NO:13-7-13 6TH LINE , GUNTURIVARI 3 ARAVIND ENTERPRISES RENEW THOTA GUNTUR,GUNTUR [email protected] 9246485697 TB/DEALER/2021/21 37ACPPD4632A1ZY DISTRICT,ANDHRA PRADESH,522001 CLOTH BAZAAR CHOWTRA CENTER ASHOK KUMAR 4 RENEW GUNTUR ,GUNTUR DISTRICT,ANDHRA [email protected] 9849093201 TB/DEALER/2021/25 37ADSPK7649G1ZV GOUTHAMCHAND PRADESH,522003 TOBACCO COLONY P.B.NO.62 GT A.S. KRISHNA & CO. PVT. ROAD,(NORTH) MANGALAGIRI ROAD 5 RENEW [email protected] 9866432509 TB/DEALER/2021/29 37AAECA5395F1ZJ LTD. TOBACCO COLONY GUNTUR,GUNTUR DISTRICT,ANDHRA PRADESH,522001 AMARAVATHI,GUNTUR DISTRICT,ANDHRA 6 A.VENKATESWARA RAO RENEW [email protected] 9394153154 TB/DEALER/2021/30 37ABSPA6131F1ZS PRADESH,522020 ONGOLE ROAD M.NIDAMANURU 7 SURYA ENTERPRISES RENEW TANGUTUR MANDAL,PRAKASAM [email protected] 9440853810 TB/DEALER/2021/42 37BHLPS2796E1ZR DISTRICT,ANDHRA PRADESH,523279 DOOR NO:21-13-58 -
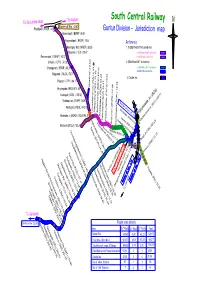
Evolution of Guntur Division
To Kazipet South Central Railway Border at Km. 4.50 Pagidipalli ( PGDP ) 4.02 Guntur Division - Jurisdiction map Bommaipalli ( BMMP ) 8.60 Nagireddipalli ( NRDP ) 19.44 Reference Mamdapur Halt ( MNDP ) 26.35 1. Sr.DEN/North/GNT Jurisdiction Valigonda ( VLG ) 29.47 a. ADEN/North/GNT Jurisdiction Ramannapet ( RMNP ) 42.12 b. ADEN/NLDA Jurisdiction Chityala ( CTYL ) 51.08 2. DEN/West/GNT Jurisdiction Srirampuram ( SRMR ) 66.31 c. ADEN/West/GNT Jurisdiction d. ADEN/NDL Jurisdiction Nalgonda ( NLDA ) 76.71 3. Double line Thipparti ( TPPI ) 94.11 Miryalaguda (MRGA)114.40 Janpahad (10.64) Kodrapol ( KDGL ) 125.56 Vishnupuram (VNUP) 134.97 Border at km. 25.36 Pondugala (PDGL) 143.78 Mangalagiri (MAG) 20.28 Piduguralla (PGRL) 74.10 Bellamkonda (BMKD) 60.42 Tummalacheruvu (TMLU) 83.34 Vijayawada Jn..(BZA) Nadikude Jn.(NDKD) 152.69/95.25 Reddigudem (REM) 54.29 Nambur (NBR) 8.67 Sattenapalli (SAP) 42.37 Nudurupadu (NDPU) 28.19 Pedakurapadu (PKPU) 29.64 Reddipalem (REP) 2.47 Krishna canal Jn..(KCC) 423.71 Phirangipuram (PPM) 21.07Siripuram (SRPM) 22.96 Macherla (MCLA) 130.26 Bandarupalli (BDPL) 13.58 Satulur (STUR) 34.29 Perecherla (PRCA) 11.26 Cheekateegalapalem ( CEM ) 89.55 Nallapadu (NLPD) 5.00 Gundlakamma (GKM) 95.85 Tenali Jn.(TEL) 397.25 Kurichedu (KCD) 107.27 Vemuru (VMU) 13.77 Potlapadu (POO) 113.85 Jaggam Bhotla Krishnapuram (JBK) 176.94 Donakonda (DKD) 120.08 Gajjalakonda (GJJ) 130.78 Narasaraopet (NRT) 45.30 Markapur Rd. (MRK) 143.97 Munumaka (MUK) 52.99 Repalle (RAL) 33.85 Santhamagulur (SAB) 61.51 Savalyapuram (SYM) 72.84 Guntur Jn.(GNT)0.00GNT atVejendla km.25.47 (VJA) 14.00 Tarlupadu (TLU) 156.44 Vinukonda (VKN) 82.85 Cumbum (CBM) 170.04 Somidevipalli (SDV) 188.94 Sangam jagarlamudi (SJL) 8.27 Yadavalli (YADA) 196.03 To Chennai Giddalur (GID) 203.78 To Guntakal Border at km. -

First Name Middle Name Last Name Father/Husb and First Name Father/Husba Nd Middle Name Father/Husband Last Name Address Country
First Name Middle Name Last Name Father/Husb Father/Husba Father/Husband Address Country State District PINCode Folio Number of Investment Type Amount Proposed Date of and First nd Middle Last Name Securities Due(in Rs.) transfer to IEPF Name Name (DD-MON-YYYY) H NO 10 2 46 NEAR RAMA TALKIES KOTHAGUDEM POST KHAMMAM CYBEIN30102220 Amount for unclaimed A ANURADHA A SRINIVAS DIST INDIA ANDHRA PRADESH 507101 177924 and unpaid dividend 9.00 30-Nov-2018 NO. 371 6TH CROSS KAMAKSHI HOSPITAL ROAD DOUBLE ROAD B V KUVEMPUNAGAR CYBEIN30192610 Amount for unclaimed A B ANNIGERI ANNIGERI MYSORE INDIA KARNATAKA 570009 597666 and unpaid dividend 22.00 30-Nov-2018 A K A R MOHAN RAMALINGA 1 KAMARAJAR CYBEIN30037810 Amount for unclaimed RAM M ROAD MADURAI INDIA TAMIL NADU 625009 033174 and unpaid dividend 5.00 30-Nov-2018 NEAR K M C OLD MENS HOSTEL KAPRIGUDDA NEW CYBEIN30088813 Amount for unclaimed A S KAUSAR NA ROAD MANGALORE INDIA KARNATAKA 575001 945632 and unpaid dividend 125.00 30-Nov-2018 C/O A SRINIVASA RAO PLOT NO 17 SBI STAFF COLONY GANDHI NAGAR CYBEIN30102210 Amount for unclaimed A SUJATHA NA HYDERABAD INDIA ANDHRA PRADESH 500080 430705 and unpaid dividend 18.00 30-Nov-2018 30/3 NEW CIRCUIT HOUSE COLONY TVS K TOLGATE TRICHY T CYBE000000000 Amount for unclaimed A UMA VIJAY VIJAYARAM N INDIA MAHARASHTRA 999999 0002026 and unpaid dividend 225.00 30-Nov-2018 AAKRITI 19, G.M. Sarafa SECURITIES Complex Holi Gate CYBEIN30175810 Amount for unclaimed PVT LTD NA Mathura (U.P.) INDIA UTTAR PRADESH 281001 000385 and unpaid dividend 65.00 30-Nov-2018 72 BANDUKWALA -

Guntur Division - Jurisdiction Map Bommaipalli ( BMMP ) 8.60
To Kazipet South Central Railway Border at Km. 4.50 Pagidipalli ( PGDP ) 4.02 Guntur Division - Jurisdiction map Bommaipalli ( BMMP ) 8.60 Nagireddipalli ( NRDP ) 19.44 Reference 1. Sr.DEN/North/GNT Jurisdiction Valigonda ( VLG ) 29.47 a. ADEN/North/GNT Jurisdiction Ramannapet ( RMNP ) 42.12 Nalgonda b. ADEN/NLDA Jurisdiction Chityala ( CTYL ) 51.08 Telangana 2. DEN/West/GNT Jurisdiction Srirampuram ( SRMR ) 66.31 c. ADEN/West/GNT Jurisdiction d. ADEN/NDL Jurisdiction Nalgonda ( NLDA ) 76.71 3. Double line Thipparthi ( TPPI ) 94.11 Krishna River crossing @ Km. 138.75 Miryalaguda (MRGA)114.40 Janpahad(JNPD)(10.64) Kodrapol ( KDGL ) 125.92 Vishnupuram (VNUP) 134.97 Border at km. 25.36 Pondugala (PDGL) 143.78 Mangalagiri (MAG) 20.28 Piduguralla (PGRL) 74.10 Bellamkonda (BMKD) 60.42 Tummalacheruvu (TMLU) 83.34 Reddigudem (REM) 54.29 Namburu (NBR) 8.97 Vijayawada Jn..(BZA) Nadikude Jn.(NDKD) 152.69/95.25 Pedakakani (PDKN) 6.13 Gurajala (GZA) 106.98 Sattenapalli (SAP) 42.37 Pedakurapadu (PKPU) 29.64 Reddipalem (REP) 2.47 Rentachintala (RCA) 115.16 Nudurupadu (NDPU)Gudipudi (GPDE) 35.71 28.19 Lingamguntla (LIM) 26.56 Krishna canal Jn..(KCC) 423.71 Phirangipuram (PPM) 21.07Siripuram (SRPM) 22.96 Macherla (MCLA) 130.26 Narasaraopet (NRT) 45.30 Mandapadu Halt (MDPD) 18.84 Bandarupalli (BDPL) 13.58 Satulur (STUR) 34.29Perecherla (PRCA) 11.26 Mahabubnagar Cheekateegalapalem ( CEM ) Munumaka89.55 (MUK) 52.99 Nallapadu (NLPD) 5.00 Gundlakamma (GKM) 95.85 Tenali Jn.(TEL) 397.25 Chinaravuru (CIV) 2.91 Guntur Zampani (ZPI) 9.80 Kurichedu (KCD) 107.27 Vemuru (VMU) 13.77 Potlapadu (POO) 113.85 Jaggam Bhotla Krishnapuram (JBK) 176.94 Donakonda (DKD) 120.08 Gajjalakonda (GJJ) 130.78 Markapur Rd. -
Municipal Administration and Urban Development Department
Chapter 9 - Municipal Administration and Urban Development Department 9.1 Department profile The Department of Municipal Administration and Urban Development (MAUD) is responsible for planning and development of urban areas, involving the following functions: Assisting the Government in town and country planning; Coordinating with various departments1 involved in development schemes; Offering technical recommendations to the Government in change of land use, alienation of lands and relaxation of rules; Preparation, implementation and regulation of plans for urban and industrial development; and Suggesting and implementing various schemes for environmental improvement, commercial and infrastructural development. MAUD discharges the above functions through multiple entities like Municipal Corporations and Municipalities, Urban Development Authorities and other specified agencies. We carried out a performance audit of the functioning of Vijayawada, Guntur, Tenali and Mangalagiri Urban Development Authority (VGTMUDA) during 2010-11 and our findings are discussed below. 9.2 Functioning of Vijayawada, Guntur, Tenali, Mangalagiri Urban Development Authority Background Vijayawada, Guntur, Tenali and Mangalagiri Urban Development Authority (Authority) was constituted in December, 1978 under Andhra Pradesh Urban Areas (Development) Act, 1975. Its jurisdiction extends over Vijayawada, Guntur, Tenali and Mangalagiri municipal corporations/municipalities constituted under AP Municipalities Act, 1965 and other areas specified in the Schedule, -
Crystal Reports
PROVISIONAL MERIT LIST SPECIAL RECRUITMENT DRIVE FOR DIFFERENTLY ABLED PERSONS, 2020-21 FILLING OF BACKLOG VACANCIES RESERVED FOR DIFFERENTLY ABLED IN VARIOUS DEPARTMENTS, GUNTUR DISTRICT Group-IV * Name of Post: 01. Junior Assistant Category: OH Qualificaon: Any Degree & Knowledge in Computer Automaon No. of Posts: General-3 * The GPA percentage in the qualifying academic examinaons has been considered as standard of merit in calculang the merit of the candidates, where the Universies have awarded the GPA in their Marks Memorandum / Provisional Cerficate. In case, if the Universies have awarded marks in lieu of GPA, the Group Marks (Part-II) have been considered as merit. Sl. Appln. Name of the Candidate Father's Name & Address Disability Sadaram Date of Age as on Gender Employment Navity Qualificaon Marks Max. % of Addional Remarks Eligible / No. No. % Cerficate Birth 01-07-2020 M / F Regd. No. Local / Gained Marks Marks Aer Scruny Qualificaon Ineligible issued Non Marks Max. % of Y / N local Gained Marks Marks 12 3 4 56 7 8 910 1112 1314151617 18 19 20 21 151PAPARAJU K PAPARAJU ANJANEYA SARMA, 90 Y 05/20/198931y, 1m, 11d M F1/2007/05201 L B.SC Computers1136 190059.7895 1137195058.3077 B.SC Computers Eligible CHAITANYA 6-178 SAIRAM TOWENSHIP NEAR MEDICAL COMPLEX SATTENAPALLI ROAD NARASARAOPET, NARASARAOPETA (R), Narasaraopet, Phone: 7702421204 258DAVALA DAVALA SOLMON RAJU, SOLASA 88 Y 06/17/199327y, 0m, 14d M F1/2012/06791 L B.A 1342 170078.9412 7.901079.0000 B.A Eligible VEERAKUMAR VILLAGE, SOLASA, Edlapadu, Phone: 9700684207 364VENKATA -

S.No. State Name State Code District Name District Code Sub District
Sub State District Village/Town S.no. State Name District Name Sub District Name District Village/Town Name Name of DA Code Code Code Code 1 Andhra Pradesh 28 Ananthapur 553 Ananthapuram 5330 A.Narayanapuramu 595096 Anantapur–Hindupur Urban Development Authority 2 Andhra Pradesh 28 Ananthapur 553 Penukonda 5356 Adadakulapalli 595434 Anantapur–Hindupur Urban Development Authority 3 Andhra Pradesh 28 Ananthapur 553 Ananthapuram 5330 Alamuru 595088 Anantapur–Hindupur Urban Development Authority 4 Andhra Pradesh 28 Ananthapur 553 Uravakonda 5317 Amidala 594897 Anantapur–Hindupur Urban Development Authority 5 Andhra Pradesh 28 Ananthapur 553 Ananthapuram 5330 Anantapur (CT) 595098 Anantapur–Hindupur Urban Development Authority 6 Andhra Pradesh 28 Ananthapur 553 Beluguppa 5318 Ankampalli 594908 Anantapur–Hindupur Urban Development Authority 7 Andhra Pradesh 28 Ananthapur 553 Bathalapalli 5337 Apparacheruvu 595170 Anantapur–Hindupur Urban Development Authority 8 Andhra Pradesh 28 Ananthapur 553 Beluguppa 5318 Avulenna 594910 Anantapur–Hindupur Urban Development Authority 9 Andhra Pradesh 28 Ananthapur 553 Bukkarayasamudram 5329 B.K.Samudram 595075 Anantapur–Hindupur Urban Development Authority 10 Andhra Pradesh 28 Ananthapur 553 Kothacheruvu 5346 Bandlapalle 595304 Anantapur–Hindupur Urban Development Authority 11 Andhra Pradesh 28 Ananthapur 553 Bathalapalli 5337 Bathalapalli 595169 Anantapur–Hindupur Urban Development Authority 12 Andhra Pradesh 28 Ananthapur 553 Beluguppa 5318 Beluguppa 594905 Anantapur–Hindupur Urban Development Authority