Loxin – a Solution to Password-Less Universal Login
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Comparative Analysis and Framework Evaluating Web Single Sign-On Systems
Comparative Analysis and Framework Evaluating Web Single Sign-On Systems FURKAN ALACA, School of Computing, Queen’s University, [email protected] PAUL C. VAN OORSCHOT, School of Computer Science, Carleton University, [email protected] We perform a comprehensive analysis and comparison of 14 web single sign-on (SSO) systems proposed and/or deployed over the last decade, including federated identity and credential/password management schemes. We identify common design properties and use them to develop a taxonomy for SSO schemes, highlighting the associated trade-offs in benefits (positive attributes) offered. We develop a framework to evaluate the schemes, in which weidentify14 security, usability, deployability, and privacy benefits. We also discuss how differences in priorities between users, service providers (SPs), and identity providers (IdPs) impact the design and deployment of SSO schemes. 1 INTRODUCTION Password-based authentication has numerous documented drawbacks. Despite the many password alternatives, no scheme has thus far offered improved security without trading off deployability or usability [8]. Single Sign-On (SSO) systems have the potential to strengthen web authentication while largely retaining the benefits of conventional password-based authentication. We analyze in depth the state-of-the art ofwebSSO through the lens of usability, deployability, security, and privacy, to construct a taxonomy and evaluation framework based on different SSO architecture design properties and their associated benefits and drawbacks. SSO is an umbrella term for schemes that allow users to rely on a single master credential to access a multitude of online accounts. We categorize SSO schemes across two broad categories: federated identity systems (FIS) and credential managers (CM). -

Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments
UNIVERSITY OF BEIRA INTERIOR Engineering Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments Liliana Filipa Baptista Soares Dissertation Submitted in Partial Fulfillment of the Requirement for the Degree of Master of Science in Computer Science and Engineering (2nd Cycle Studies) Supervised by Prof. Dr. Pedro Ricardo Morais Inácio Covilhã, October 2013 ii To my beloved family, especially to my grandparents. iv Acknowledgements The endurance to overcome obstacles or predisposed objectives in life depends on how each one envisages them. It is up to each one to extract the most valuable lessons from each journey and transform them into knowledge. Without the guidance and support of very particular persons, it would have not been possible to accomplish this dissertation and many lessons would have not been learned. I hereby thank my mother and father, to whom I am mostly grateful, for helping me to achieve my goals, particularly those of my academic quest. I would like to thank my sister, Cátia, for her immeasurable support, and my grandparents, for always demonstrating their love and will to live. I am also grateful to my supervisor, Prof. Dr. Pedro Ricardo Morais Inácio, not only for the help, charisma and readiness he demonstrated to complete this stage, but also for being resourceful in aiding throughout other steps of my professional life. I also acknowledge the Multimedia Signal Processing – Covilhã Group at the Instituto de Telecomunicações, which hosted this dis- sertation work and the final project of my first degree, and the research folk in it, particularly Miguel Neto for lending me a smartcard reader temporarily. -

Analisi Del Progetto Mozilla
Università degli studi di Padova Facoltà di Scienze Matematiche, Fisiche e Naturali Corso di Laurea in Informatica Relazione per il corso di Tecnologie Open Source Analisi del progetto Mozilla Autore: Marco Teoli A.A 2008/09 Consegnato: 30/06/2009 “ Open source does work, but it is most definitely not a panacea. If there's a cautionary tale here, it is that you can't take a dying project, sprinkle it with the magic pixie dust of "open source", and have everything magically work out. Software is hard. The issues aren't that simple. ” Jamie Zawinski Indice Introduzione................................................................................................................................3 Vision .........................................................................................................................................4 Mozilla Labs...........................................................................................................................5 Storia...........................................................................................................................................6 Mozilla Labs e i progetti di R&D...........................................................................................8 Mercato.......................................................................................................................................9 Tipologia di mercato e di utenti..............................................................................................9 Quote di mercato (Firefox).....................................................................................................9 -

Firefox OS Overview Ewa Janczukowicz
Firefox OS Overview Ewa Janczukowicz To cite this version: Ewa Janczukowicz. Firefox OS Overview. [Research Report] Télécom Bretagne. 2013, pp.28. hal- 00961321 HAL Id: hal-00961321 https://hal.archives-ouvertes.fr/hal-00961321 Submitted on 24 Apr 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Collection des rapports de recherche de Télécom Bretagne RR-2013-04-RSM Firefox OS Overview Ewa JANCZUKOWICZ (Télécom Bretagne) This work is part of the project " Étude des APIs Mozilla Firefox OS" supported by Orange Labs / TC PASS (CRE API MOZILLA FIREFOX OS - CTNG13025) ACKNOWLEGMENTS Above all, I would like to thank Ahmed Bouabdallah and Arnaud Braud for their assistance, support and guidance throughout the contract. I am very grateful to Gaël Fromentoux and Stéphane Tuffin for giving me the possibility of working on the Firefox OS project. I would like to show my gratitude to Jean-Marie Bonnin, to all members of Orange NCA/ARC team and RSM department for their help and guidance. RR-2013-04-RSM 1 RR-2013-04-RSM 2 SUMMARY Firefox OS is an operating system for mobile devices such as smartphones and tablets. -

A Hybrid Approach to Detect Tabnabbing Attacks
A Hybrid Approach to Detect Tabnabbing Attacks by Hana Sadat Fahim Hashemi A thesis submitted to the School of Computing in conformity with the requirements for the degree of Master of Science Queen's University Kingston, Ontario, Canada August 2014 Copyright c Hana Sadat Fahim Hashemi, 2014 Abstract Phishing is one of the most prevalent types of modern attacks, costing significant financial losses to enterprises and users each day. Despite the emergence of various anti-phishing tools and techniques, not only there has been a dramatic increase in the number of phishing attacks but also more sophisticated forms of these attacks have come into existence. One of the most complicated and deceptive forms of phishing attacks is the tabnabbing attack. This newly discovered threat takes advantage of the user's trust and inattention to the open tabs in the browser and changes the appearance of an already open malicious page to the appearance of a trusted website that demands confidential information from the user. As one might imagine, the tabnabbing attack mechanism makes it quite probable for even an attentive user to be lured into revealing his or her confidential information. Few tabnabbing detection and prevention techniques have been proposed thus far. The majority of these techniques block scripts that are susceptible to perform malicious actions or violate the browser security policy. However, most of these techniques cannot effectively prevent the other variant of the tabnabbing attack that is launched without the use of scripts. In this thesis, we propose a hybrid tabnabbing detection approach with the aim i of overcoming the shortcomings of the existing anti-tabnabbing approaches and tech- niques. -

Technical Design of Open Social Web for Crowdsourced Democracy
Project no. 610349 D-CENT Decentralised Citizens ENgagement Technologies Specific Targeted Research Project Collective Awareness Platforms D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Version Number: 1 Lead beneficiary: OKF Due Date: 31 October 2014 Author(s): Pablo Aragón, Francesca Bria, Primavera de Filippi, Harry Halpin, Jaakko Korhonen, David Laniado, Smári McCarthy, Javier Toret Medina, Sander van der Waal Editors and reviewers: Robert Bjarnason, Joonas Pekkanen, Denis Roio, Guido Vilariño Dissemination level: PU Public X PP Restricted to other programme participants (including the Commission Services) RE Restricted to a group specified by the consortium (including the Commission Services) CO Confidential, only for members of the consortium (including the Commission Services) Approved by: Francesca Bria Date: 31 October 2014 This report is currently awaiting approval from the EC and cannot be not considered to be a final version. FP7 – CAPS - 2013 D-CENT D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Contents 1 Executive Summary ........................................................................................................................................................ 6 Description of the D-CENT Open Democracy pilots ............................................................................................. 8 Description of the lean development process .......................................................................................................... 10 Hypotheses statements -
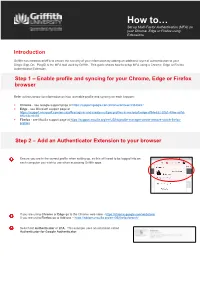
How to Install MFA Browser Authenicator Extension
How to… Set up Multi-Factor Authentication (MFA) on your Chrome, Edge or Firefox using Extensions Introduction Griffith has introduced MFA to ensure the security of your information by adding an additional layer of authentication to your Single Sign-On. PingID is the MFA tool used by Griffith. This guide shows how to setup MFA using a Chrome, Edge or Firefox Authenticator Extension. Step 1 – Enable profile and syncing for your Chrome, Edge or Firefox browser Refer to links below for information on how to enable profile and syncing for each browser: • Chrome - see Google support page at https://support.google.com/chrome/answer/2364824? • Edge - see Microsoft support page at https://support.microsoft.com/en-us/office/sign-in-and-create-multiple-profiles-in-microsoft-edge-df94e622-2061-49ae-ad1d- 6f0e43ce6435 • Firefox - see Mozilla support page at https://support.mozilla.org/en-US/kb/profile-manager-create-remove-switch-firefox- profiles Step 2 – Add an Authenticator Extension to your browser Ensure you are in the correct profile when setting up, as this will need to be logged into on each computer you wish to use when accessing Griffith apps. If you are using Chrome or Edge go to the Chrome web store - https://chrome.google.com/webstore/ If you are using Firefox go to Add-ons – https://addons.mozilla.org/en-GB/firefox/search/ Search for Authenticator or 2FA. This example uses an extension called Authenticator for Google Authenticator. Select Add Select Add Extension Your browser will confirm the extension has been added. Step 3 – Set up the Authenticator Extension as the primary authenticating method Once the Authenticator extension is added, click on the extension icon then click on the Pencil icon. -

User Controlled Trust and Security Level of Web Real-Time Communications Kevin CORRE
User Controlled Trust and Security Level of Web Real-Time Communications THESE DE DOCTORAT DE L’UNIVERSITE DE RENNES 1 COMUE UNIVERSITE BRETAGNE LOIRE Ecole Doctorale N° 601 Mathèmatique et Sciences et Technologies de l’Information et de la Communication Spécialité : Informatique Thèse présentée et soutenue à RENNES, le 31 MAI 2018 par Kevin CORRE Unité de recherche : IRISA (UMR 6074) Institut de Recherche en Informatique et Systemes Aléatoires Thèse N° : Rapporteurs avant soutenance : Maryline LAURENT, Professeur, TELECOM SudParis Yvon KERMARREC, Professeur, IMT Atlantique Composition du jury : Présidente : Maryline LAURENT, Professeur, TELECOM SudParis Examinateurs : Yvon KERMARREC, Professeur, IMT Atlantique Walter RUDAMETKIN, Maître de Conférences, Université de Lille Dominique HAZAEL-MASSIEUX, Ingenieur de Recherche, W3C Vincent FREY, R&D Software Engineer, Orange Labs Dir. de thèse : Olivier BARAIS, Professeur, Université de Rennes 1 Co-dir. de thèse : Gerson SUNYÉ, Maître de Conférences, Université de Nantes “Fide, sed cui vide”. - Locution latine “Du père qui m’a donné la vie : la modestie et la virilité, du moins si je m’en rapporte à la réputation qu’il a laissée et au souvenir personnel qui m’en reste”. - Marcus Catilius Severus i Résumé en Français Contexte Communication, du latin communicatio [13], est défini par le dictionnaire Oxford comme étant “the imparting or exchanging of information” et “the means of sending or receiving information, such as telephone lines or computers” [14]. Face à une incertitude ou à un risque, un tel échange n’est possible que si une relation de confiance peut être établie entre l’émetteur et le récepteur. Cette relation de confiance doit aussi concerner les moyens utilisés pour communiquer. -

Benítez Bravo, Rubén; Liu, Xiao; Martín Mor, Adrià, Dir
This is the published version of the article: Benítez Bravo, Rubén; Liu, Xiao; Martín Mor, Adrià, dir. Proyecto de local- ización de Waterfox al catalán y al chino. 2019. 38 p. This version is available at https://ddd.uab.cat/record/203606 under the terms of the license Trabajo de TPD LOCALIZACIÓN DE WATERFOX EN>CA/ZH Ilustración 1. Logo de Waterfox Rubén Benítez Bravo y Xiao Liu 1332396 | 1532305 [email protected] [email protected] Màster de tradumàtica: Tecnologies de la traducció 2018-2019 Índice de contenidos 1. Introducción ........................................................................................ 4 2. Tabla resumen .................................................................................... 5 3. Descripción del proceso de localización ............................................. 6 3.1 ¿Qué es Waterfox? ........................................................................ 6 3.2 ¿Qué uso tiene?............................................................................. 6 3.3 Preparando la traducción ............................................................... 7 4. Análisis de la traducción ................................................................... 11 5. Análisis técnico ................................................................................. 21 6. Fase de testing ................................................................................. 29 7. Conclusiones .................................................................................... 35 8. Bibliografía -

Download Google Authenticator App Download Google Authenticator App
download google authenticator app Download google authenticator app. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67aa6d6ed8c98498 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Google Authenticator 4+ Google Authenticator works with 2-Step Verification for your Google Account to provide an additional layer of security when signing in. With 2-Step Verification, signing into your account will require both your password and a verification code you can generate with this app. Once configured, you can get verification codes without the need for a network or cellular connection. Features include: - Automatic setup via QR code - Support for multiple accounts - Support for time-based and counter-based code generation - Transfer accounts between devices via QR code. To use Google Authenticator with Google, you need to enable 2-Step Verification on your Google Account. Visit http://www.google.com/2step to get started. What’s New. - Added the ability to transfer many accounts to a different device - Added the ability of search for accounts - Added the ability to turn on Privacy Screen. -

Dao Research: Securing Data and Applications in the Cloud
WHITE PAPER Securing Data and Applications in the Cloud Comparison of Amazon, Google, Microsoft, and Oracle Cloud Security Capabilities July 2020 Dao Research is a competitive intelligence firm working with Fortune-500 companies in the Information Technology sector. Dao Research is based in San Francisco, California. Visit www.daoresearch.com to learn more about our competitive intelligence services. Securing Data and Applications in the Cloud Contents Introduction .............................................................................................................................................................. 3 Executive Summary ................................................................................................................................................. 4 Methodology ............................................................................................................................................................6 Capabilities and Approaches .................................................................................................................................. 8 Perimeter Security ........................................................................................................................................ 9 Network Security ........................................................................................................................................ 10 Virtualization/Host ..................................................................................................................................... -

Mfa) with the Payback Information Management System (Pims)
MULTIFACTOR AUTHENTICATION (MFA) WITH THE PAYBACK INFORMATION MANAGEMENT SYSTEM (PIMS) What is MFA? MFA is a security process that requires a user to verify their identity in multiple ways to gain system access. Why use MFA for the PIMS? Use of MFA for PIMS greatly reduces the chance of unauthorized access to your account thereby protecting personally identifiable information (PII) and significantly reducing the risk of a system-wide data breach. To use Multifactor Authentication for the PIMS, follow the steps below: Download and Install Google Authenticator on your smartphone 1 This free app is available through the Apple App Store or Google Play Store by searching for “Google Authenticator”. You can also look for one of the icons below on your smartphone home screen or within your smartphone’s applications section: Apple app store Android Google Play store Follow the prompts to download Google Authenticator to your smartphone. When you have successfully downloaded the app, you should see the icon below on your smartphone: Navigate to the PIMS site 2 On the device you’d like to sign into the PIMS on, navigate to https://pdp.ed.gov/RSA and click “Secure Login” in the upper right corner. Log into the PIMS Log into the PIMS using your regular 3 username and password. INSTRUCTIONS FOR ENROLLING IN MULTIFACTOR AUTHENTICATION FOR THE PIMS For assistance, contact the PIMS Help Desk at [email protected] or 1-800-832-8142 from 8am - 8pm EST. Open the 4 enrollment page Upon initial login, you will be directed to the enrollment page (see Figure 1), which will include a QR code and a place to enter the code generated by your Google Authenticator app.