Nothing to Hide, Nothing to Fear? Tools and Suggestions for Digital Data Protection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
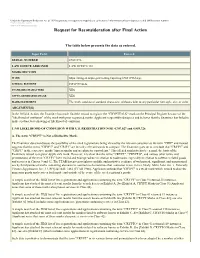
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -
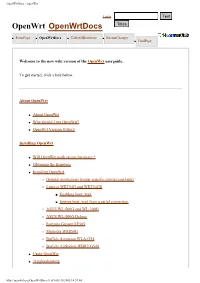
Openwrtdocs - Openwrt
OpenWrtDocs - OpenWrt Login OpenWrt OpenWrtDocs ● FrontPage ● OpenWrtDocs ● TableOfHardware ● RecentChanges ● FindPage Welcome to the new wiki version of the OpenWrt userguide. To get started, click a link below. About OpenWrt ● About OpenWrt ● Why should I run OpenWrt? ● OpenWrt Version History Installing OpenWrt ● Will OpenWrt work on my hardware ? ● Obtaining the firmware ● Installing OpenWrt ❍ General instructions (router specific instructions later) ❍ Linksys WRT54G and WRT54GS ■ Enabling boot_wait ■ Setting boot_wait from a serial connection ❍ ASUS WL-500G and WL-300G ❍ ASUS WL-500G Deluxe ❍ Siemens Gigaset SE505 ❍ Motorola WR850G ❍ Buffalo Airstation WLA-G54 ❍ Buffalo AirStation WBR2-G54S ● Using OpenWrt ● Troubleshooting http://openwrt.org/OpenWrtDocs (1 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt Using OpenWrt ● Using OpenWrt for the first time ● Firstboot / jffs2 ● Editing Files ● ipkg ● Configuration OpenWrt Configuration ● NVRAM ● Network configuration ❍ Sample network configurations ❍ The ethernet switch ■ Normal Behavior ■ Using Robocfg ● Wireless configuration ❍ Basic settings ❍ WEP encryption ❍ WPA encryption ❍ Wireless Distribution System (WDS) / Repeater / Bridge ❍ OpenWrt as client / wireless bridge ● Software configuration ❍ System ■ dnsmasq ■ nas ■ wl ■ TimeZone and NTP ■ Crontab ■ PPPoE Internet Connection ■ Access to syslog ❍ Applications ■ httpd ■ socks-Proxy http://openwrt.org/OpenWrtDocs (2 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt ■ uPnP ■ CUPS - Printing system with spooling ● Hardware ❍ LED OpenWrt -

Whatsapp Security and Role of Metadata in Preserving Privacy
WhatsApp security and role of metadata in preserving privacy Nidhi Rastogi, James Hendler Rensselaer Polytechnic Institute, Troy, NY, USA [email protected] [email protected] Abstract: WhatsApp messenger is arguaBly the most popular moBile app availaBle on all smart-phones. Over one billion people worldwide for free messaging, calling, and media sharing use it. In April 2016, WhatsApp switched to a default end-to-end encrypted service. This means that all messages (SMS), phone calls, videos, audios, and any other form of information exchanged cannot Be read By any unauthorized entity since WhatsApp version 2.16.2 (released April 2016). In this paper we analyze the WhatsApp messaging platform and critique its security architecture along with a focus on its privacy preservation mechanisms. We report that the Signal Protocol, which forms the Basis of WhatsApp end-to-end encryption, does offer protection against forward secrecy, and MITM to a large extent. Finally, we argue that simply encrypting the end-to-end channel cannot preserve privacy. The metadata can reveal just enough information to show connections Between people, their patterns, and personal information. This paper elaborates on the security architecture of WhatsApp and performs an analysis on the various protocols used. This enlightens us on the status quo of the app security and what further measures can be used to fill existing gaps without compromising the usability. We start By descriBing the following (i) important concepts that need to be understood to properly understand security, (ii) the security architecture, (iii) security evaluation, (iv) followed By a summary of our work. -

Technische Berichte Des Hasso-Plattner-Instituts Für Softwaresystemtechnik an Der Universität Potsdam
Proceedings of the 2nd International Workshop on e- learning and Virtual and Remote Laboratories Bernhard Rabe, Andreas Rasche (eds.) Technische Berichte Nr. 21 des Hasso-Plattner-Instituts für Softwaresystemtechnik an der Universität Potsdam Technische Berichte des Hasso-Plattner-Instituts für Softwaresystemtechnik an der Universität Potsdam Nr. 21 Proceedings of the 2nd International Workshop on e-learning and Virtual and Remote Laboratories Bernhard Rabe, Andreas Rasche (eds.) Potsdam 2008 Bibliografische Information der Deutschen Nationalbibliothek Die Deutsche Nationalbibliothek verzeichnet diese Publikation in der Deutschen Nationalbibliografie; detaillierte bibliografische Daten sind im Internet über http://dnb.d-nb.de abrufbar Die Reihe Technische Berichte des Hasso-Plattner-Instituts für Softwaresystemtechnik an der Universität Potsdam erscheint aperiodisch. Herausgeber: Professoren des Hasso-Plattner-Instituts für Softwaresystemtechnik an der Universität Potsdam Redaktion: Bernhard Rabe, Andreas Rasche E-Mail: {bernhard.rabe; andreas.rasche}@.hpi.uni-potsdam.de Verlag: Universitätsverlag Potsdam Am Neuen Palais 10, 14469 Potsdam Fon +49 (0) 331 977 4517 Fax +49 (0) 331 977 4625 e-mail: ubpub@uni-potsdamde http://info.ub.uni-potsdam.de/verlag.htm Druck: allprintmedia gmbH Blomberger Weg 6a 13437 Berlin email: [email protected] © Hasso-Plattner-Institut für Softwaresystemtechnik an der Universität Potsdam, 2008 Das Manuskript ist urheberrechtlich geschützt. Heft Nr. 21 (2008) ISSN 1613-5652 ISBN 978-3-940793-17-1 Foreword It is our pleasure to welcome all participants to VIRTUAL-LAB’2008, the 2nd International Workshop on e-learning and Virtual & Remote Laboratories, at Hasso-Plattner-Institute for Software Systems En- gineering at University of Potsdam, Germany. The workshop is a successor of the successful VIRTUAL- LAB’04 workshop held in Setubal,´ Portugal. -

Co-Ordinating Developers and High-Risk Users of Privacy-Enhanced Secure Messaging Protocols Harry Halpin, Ksenia Ermoshina, Francesca Musiani
Co-ordinating Developers and High-Risk Users of Privacy-Enhanced Secure Messaging Protocols Harry Halpin, Ksenia Ermoshina, Francesca Musiani To cite this version: Harry Halpin, Ksenia Ermoshina, Francesca Musiani. Co-ordinating Developers and High-Risk Users of Privacy-Enhanced Secure Messaging Protocols. SSR 2018 - Security Standardisation Research Conference, Nov 2018, Darmstadt, Germany. hal-01966560 HAL Id: hal-01966560 https://hal.inria.fr/hal-01966560 Submitted on 28 Dec 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Co-ordinating Developers and High-Risk Users of Privacy-Enhanced Secure Messaging Protocols Harry Halpin1, Ksenia Ermoshina2, and Francesca Musiani2 1 Inria 2 Rue Simone Iff [email protected] 2 Institute for Communication Sciences, CNRS 20 rue Berbier-du-Mets 75013 Paris, France Abstract. Due to the increased deployment of secure messaging pro- tocols, differences between what developers \believe" are the needs of their users and their actual needs can have real consequences. Based on 90 interviews with both high and low-risk users, as well as the developers of popular secure messaging applications, we mapped the design choices of the protocols made by developers to the relevance of these features to threat models of both high-risk and low-risk users. -

The Signal Protocol for Non-Cryptographers
The Signal Protocol for non-Cryptographers An Explanation of the Signal Protocol and its Security Properties Master’s thesis in Computer Science - algorithms, languages and logic Lamiya Yagublu Department of Computer Science and Engineering CHALMERS UNIVERSITY OF TECHNOLOGY Gothenburg, Sweden 2018 Master’s thesis 2018 The Signal Protocol for non-Cryptographers An Explanation of the Signal Protocol and its Security Properties Lamiya Yagublu Department of Computer Science and Engineering Chalmers University of Technology Gothenburg, Sweden 2018 The Signal Protocol for non-Cryptographers An Explanation of the Signal Protocol and its Security Properties Lamiya Yagublu © Lamiya Yagublu, 2018. Supervisor: Gerardo Schneider, Department of Computer Science and Engineering Advisor: Elena Pagnin, Carlo Brunetta, Chalmers University of Technology Examiner: Andrei Sabelfeld, Department of Computer Science and Engineering Master’s Thesis 2018 Department of Computer Science and Engineering Chalmers University of Technology SE-412 96 Gothenburg Telephone +46 31 772 1000 Typeset in LATEX Gothenburg, Sweden 2018 ——————————————————— ——————————————————– 4 Investigating the Security of the Signal Protocol An Explanation of the Signal Protocol and the its Security Properties Lamiya Yagublu Department of Computer Science and Engineering Chalmers University of Technology Abstract People tend to socialize and today many people use messaging applications to communicate. While people communicate, they share personal information between each other and they do not want others to observe or access their information and use it against them. Therefore, it is important to keep this information private. The Signal protocol is a communication protocol used to provide security guarantees and keep the users’ information private while they communicate. Since many messaging applications, including WhatsApp and Facebook messenger, uses the Signal protocol and a lot of people use these applications, any flaw in the Signal protocol might affect a large number of users’ private communication. -

Clone Detection in Secure Messaging: Improving Post-Compromise Security in Practice
Clone Detection in Secure Messaging: Improving Post-Compromise Security in Practice Cas Cremers Jaiden Fairoze CISPA Helmholtz Center for Information Security CISPA Helmholtz Center for Information Security Saarbrücken, Germany Saarbrücken, Germany [email protected] [email protected] Benjamin Kiesl Aurora Naska CISPA Helmholtz Center for Information Security CISPA Helmholtz Center for Information Security Saarbrücken, Germany Saarbrücken, Germany [email protected] [email protected] ABSTRACT Practice . In Proceedings of the 2020 ACM SIGSAC Conference on Computer and We investigate whether modern messaging apps achieve the strong Communications Security (CCS ’20), November 9–13, 2020, Virtual Event, USA. post-compromise security guarantees offered by their underlying ACM, New York, NY, USA, 15 pages. https://doi.org/10.1145/3372297.3423354 protocols. In particular, we perform a black-box experiment in which a user becomes the victim of a clone attack; in this attack, the user’s full state (including identity keys) is compromised by 1 INTRODUCTION an attacker who clones their device and then later attempts to The advent of modern secure messaging, and the widespread de- impersonate them, using the app through its user interface. ployment of the Signal protocol library in particular, has brought Our attack should be prevented by protocols that offer post- modern security mechanisms to millions of users. Specifically, this compromise security, and thus, by all apps that are based on Signal’s includes the double-ratchet algorithm [23] and the security prop- double-ratchet algorithm (for instance, the Signal app, WhatsApp, erties it can provide, such as post-compromise security [6], which and Facebook Secret Conversations). -

Advanced Cryptographic Engineering
Chapter 20 Advanced Cryptographic Engineering Give me a rock on which to stand, and I will move the world. – Archimedes Whoever thinks his problem can be solved using cryptography, doesn’t understand his problem and doesn’t understand cryptography – Attributed by Roger Needham and Butler Lampson to each other 20.1 Introduction Cryptography is often used to build a trustworthy component on which more complex designs can rely. Such designs come from three rather di↵erent back- grounds. The first is the government systems world we described in Chapter 9, where the philosophy is to minimise the trusted computing base using mech- anisms like data diodes and multilevel secure encryption devices. The second is the world of banking described in Chapter 12 where smartcards are used as authentication tokens while HSMs are used to protect PINs and keys. The third is the world of cryptography research in the 1980s and 1990s where people dreamed of solving social problems using mathematics: of creating anonymous communications so that oppressed groups could evade state surveillance, lead- ing to censorship-resistant publishing, untraceable digital cash and electronic elections that would be impossible to rig. In all these cases, real life turned out to be somewhat messier than we anticipated. There are even more complex cryptographic components that we use as platforms. But the engineering isn’t just about reducing the attack surface, or simplifying our fault tree analysis. In most cases there’s a significant interaction with policy, liability and other complicating factors. In this chapter I’m going to discuss six examples of cryptographic engineering 587 20.2. -

Internet Engineering Task Force (IETF) D. Bider Request For
Internet Engineering Task Force (IETF) D. Bider Request for Comments: 8308 Bitvise Limited Updates: 4251, 4252, 4253, 4254 March 2018 Category: Standards Track ISSN: 2070-1721 Extension Negotiation in the Secure Shell (SSH) Protocol Abstract This memo updates RFCs 4251, 4252, 4253, and 4254 by defining a mechanism for Secure Shell (SSH) clients and servers to exchange information about supported protocol extensions confidentially after SSH key exchange. Status of This Memo This is an Internet Standards Track document. This document is a product of the Internet Engineering Task Force (IETF). It represents the consensus of the IETF community. It has received public review and has been approved for publication by the Internet Engineering Steering Group (IESG). Further information on Internet Standards is available in Section 2 of RFC 7841. Information about the current status of this document, any errata, and how to provide feedback on it may be obtained at https://www.rfc-editor.org/info/rfc8308. Copyright Notice Copyright (c) 2018 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust's Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. Code Components extracted from this document must include Simplified BSD License text as described in Section 4.e of the Trust Legal Provisions and are provided without warranty as described in the Simplified BSD License.