HUNTING for VULNERABILITIES in SIGNAL JP Aumasson & Markus Vervier
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Bbg), 2011-2015
Description of document: FOIA Logs for the Broadcasting Board of Governors (BBG), 2011-2015 Requested date: 02-March-2016 Released date: 06-May-2016 Posted date: 08-August-2016 Source of document: BBG FOIA Office Room 3349 330 Independence Ave. SW Washington, D.C. 20237 Fax: (202) 203-4585 The governmentattic.org web site (“the site”) is noncommercial and free to the public. The site and materials made available on the site, such as this file, are for reference only. The governmentattic.org web site and its principals have made every effort to make this information as complete and as accurate as possible, however, there may be mistakes and omissions, both typographical and in content. The governmentattic.org web site and its principals shall have neither liability nor responsibility to any person or entity with respect to any loss or damage caused, or alleged to have been caused, directly or indirectly, by the information provided on the governmentattic.org web site or in this file. The public records published on the site were obtained from government agencies using proper legal channels. Each document is identified as to the source. Any concerns about the contents of the site should be directed to the agency originating the document in question. GovernmentAttic.org is not responsible for the contents of documents published on the website. Broadcasting 330 Independence Ave.SW T 202.203.4550 Board of Cohen Building, Room 3349 F 202.203.4585 Governors Washington, DC 20237 Office ofthe General Counsel Freedom ofInformation and Privacy Act Office May6, 2016 RE: Request Pursuant to the Freedom of Information Act-FOIA #16-035 This letter is in response to your Freedom of Information Act (FOIA) request dated March 2, 2016 to the Broadcasting Board of Governors (BBG), which the Agency received on March 14, 2016. -

Crypto Projects That Might Not Suck
Crypto Projects that Might not Suck Steve Weis PrivateCore ! http://bit.ly/CryptoMightNotSuck #CryptoMightNotSuck Today’s Talk ! • Goal was to learn about new projects and who is working on them. ! • Projects marked with ☢ are experimental or are relatively new. ! • Tried to cite project owners or main contributors; sorry for omissions. ! Methodology • Unscientific survey of projects from Twitter and mailing lists ! • Excluded closed source projects & crypto currencies ! • Stats: • 1300 pageviews on submission form • 110 total nominations • 89 unique nominations • 32 mentioned today The People’s Choice • Open Whisper Systems: https://whispersystems.org/ • Moxie Marlinspike (@moxie) & open source community • Acquired by Twitter 2011 ! • TextSecure: Encrypt your texts and chat messages for Android • OTP-like forward security & Axolotl key racheting by @trevp__ • https://github.com/whispersystems/textsecure/ • RedPhone: Secure calling app for Android • ZRTP for key agreement, SRTP for call encryption • https://github.com/whispersystems/redphone/ Honorable Mention • ☢ Networking and Crypto Library (NaCl): http://nacl.cr.yp.to/ • Easy to use, high speed XSalsa20, Poly1305, Curve25519, etc • No dynamic memory allocation or data-dependent branches • DJ Bernstein (@hashbreaker), Tanja Lange (@hyperelliptic), Peter Schwabe (@cryptojedi) ! • ☢ libsodium: https://github.com/jedisct1/libsodium • Portable, cross-compatible NaCL • OpenDNS & Frank Denis (@jedisct1) The Old Standbys • Gnu Privacy Guard (GPG): https://www.gnupg.org/ • OpenSSH: http://www.openssh.com/ -

Encryption and Anonymity Follow-Up Report
PALAIS DES NATIONS • 1211 GENEVA 10, SWITZERLAND www.ohchr.org • TEL: +41 22 917 9000 • FAX: +41 22 917 9008 • E-MAIL: [email protected] Mandate of the Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression Research Paper 1/2018 June 2018 Encryption and Anonymity follow-up report Contents I. INTRODUCTION ............................................................................................................................... 2 II. TRENDS IN STATE RESTRICTIONS ON ENCRYPTION AND ANONYMITY .............................. 3 A. An Overview of State Obligations ........................................................................................................... 3 B. State practice: examples and concerns ..................................................................................................... 4 (i) Bans on Use and Dissemination of Encryption Tools ......................................................................... 5 (ii) Licensing and Registration Requirements .......................................................................................... 5 (iii) Intentional Weakening of Encryption ................................................................................................ 5 (iv) Government Hacking ......................................................................................................................... 7 (v) Mandatory Data Localization and Key Escrows ................................................................................. 8 (vi) -

TECH TOOLS for ACTIVISTS Published : 2012-10-04 License : CC-BY T ABLE of CONT ENT S
TECH TOOLS FOR ACTIVISTS Published : 2012-10-04 License : CC-BY T ABLE OF CONT ENT S Tech Tools For Activism 1 An introduction to this booklet 2 2 Securing your email 4 3 Anonymous Blogs and Websites 7 4 Microblogging Beyond Twitter 9 5 Browsing the Internet 11 6 Organising and Networking Online 14 7 Mobile Phone Security and Android Apps 18 8 Publishing and Networking News 21 9 Producing and Publishing Media to the Internet 23 10 Green Computing 25 11 Hiding & Deleting Things on your PC 27 TECH TOOLS FOR ACTIVISM 1. AN INTRODUCTION TO THIS BOOKLET 2. SECURING YOUR EMAIL 3. ANONYMOUS BLOGS AND WEBSITES 4. MICROBLOGGING BEYOND TWITTER 5. BROWSING THE INTERNET 6. ORGANISING AND NETWORKING ONLINE 7. MOBILE PHONE SECURITY AND ANDROID APPS 8. PUBLISHING AND NETWORKING NEWS 9. PRODUCING AND PUBLISHING MEDIA TO THE INTERNET 10. GREEN COMPUTING 11. HIDING & DELETING THINGS ON YOUR PC 1 1. AN INT RODUCT ION T O T HIS BOOKLET T his booklet will help you to: use email securely publish news and upload media anonymously make your web browsing more anonymous and secure use Facebook and Twitter more securely get organised online without relying on corporate social networking sites use encrypted messaging on mobile phones hide stuff on your computer so it can't be found find a more secure and decentralised replacement for Twitter support free software, open licences and decentralised/ federated communication. Why this booklet is important: This booklet provides an introduction to the effective use of technology for activism, with links to step-by-step guides and further information. -

The Double Ratchet Algorithm
The Double Ratchet Algorithm Trevor Perrin (editor) Moxie Marlinspike Revision 1, 2016-11-20 Contents 1. Introduction 3 2. Overview 3 2.1. KDF chains . 3 2.2. Symmetric-key ratchet . 5 2.3. Diffie-Hellman ratchet . 6 2.4. Double Ratchet . 13 2.6. Out-of-order messages . 17 3. Double Ratchet 18 3.1. External functions . 18 3.2. State variables . 19 3.3. Initialization . 19 3.4. Encrypting messages . 20 3.5. Decrypting messages . 20 4. Double Ratchet with header encryption 22 4.1. Overview . 22 4.2. External functions . 26 4.3. State variables . 26 4.4. Initialization . 26 4.5. Encrypting messages . 27 4.6. Decrypting messages . 28 5. Implementation considerations 29 5.1. Integration with X3DH . 29 5.2. Recommended cryptographic algorithms . 30 6. Security considerations 31 6.1. Secure deletion . 31 6.2. Recovery from compromise . 31 6.3. Cryptanalysis and ratchet public keys . 31 1 6.4. Deletion of skipped message keys . 32 6.5. Deferring new ratchet key generation . 32 6.6. Truncating authentication tags . 32 6.7. Implementation fingerprinting . 32 7. IPR 33 8. Acknowledgements 33 9. References 33 2 1. Introduction The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. Typically the parties will use some key agreement protocol (such as X3DH [1]) to agree on the shared secret key. Following this, the parties will use the Double Ratchet to send and receive encrypted messages. The parties derive new keys for every Double Ratchet message so that earlier keys cannot be calculated from later ones. -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

SSL/TLS Interception Proxies and Transitive Trust Jeff Jarmoc Dell Secureworks Counter Threat Unit℠ Threat Intelligence
SSL/TLS Interception Proxies and Transitive Trust Jeff Jarmoc Dell SecureWorks Counter Threat Unit℠ Threat Intelligence Presented at Black Hat Europe – March 14, 2012. Introduction Secure Sockets Layer (SSL) [1] and its successor Transport Layer Security (TLS) [2] have become key components of the modern Internet. The privacy, integrity, and authenticity [3] [4] provided by these protocols are critical to allowing sensitive communications to occur. Without these systems, e- commerce, online banking, and business-to-business exchange of information would likely be far less frequent. Threat actors have also recognized the benefits of transport security, and they are increasingly turning to SSL to hide their activities. Advanced Persistent Threat (APT) attackers [5], botnets [6], and even commodity web attacks can leverage SSL encryption to evade detection. To counter these tactics, organizations are increasingly deploying security controls that intercept end- to-end encrypted channels. Web proxies, data loss prevention (DLP) systems, specialized threat detection solutions, and network intrusion prevention systems (NIPS) offer functionality to intercept, inspect, and filter encrypted traffic. Similar functionality is present in lawful intercept systems and solutions enabling the broad surveillance of encrypted communications by governments. Broadly classified as “SSL/TLS interception proxies,” these solutions act as a “man in the middle,” violating the end-to-end security promises of SSL. This type of interception comes at a cost. Intercepting SSL-encrypted connections sacrifices a degree of privacy and integrity for the benefit of content inspection, often at the risk of authenticity and endpoint validation. Implementers and designers of SSL interception proxies should consider these risks and understand how their systems operate in unusual circumstances. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
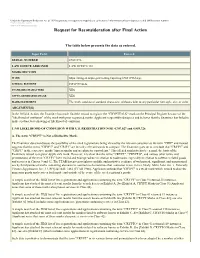
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

The Most Dangerous Code in the World: Validating SSL Certificates In
The Most Dangerous Code in the World: Validating SSL Certificates in Non-Browser Software Martin Georgiev Subodh Iyengar Suman Jana The University of Texas Stanford University The University of Texas at Austin at Austin Rishita Anubhai Dan Boneh Vitaly Shmatikov Stanford University Stanford University The University of Texas at Austin ABSTRACT cations. The main purpose of SSL is to provide end-to-end security SSL (Secure Sockets Layer) is the de facto standard for secure In- against an active, man-in-the-middle attacker. Even if the network ternet communications. Security of SSL connections against an is completely compromised—DNS is poisoned, access points and active network attacker depends on correctly validating public-key routers are controlled by the adversary, etc.—SSL is intended to certificates presented when the connection is established. guarantee confidentiality, authenticity, and integrity for communi- We demonstrate that SSL certificate validation is completely bro- cations between the client and the server. Authenticating the server is a critical part of SSL connection es- ken in many security-critical applications and libraries. Vulnerable 1 software includes Amazon’s EC2 Java library and all cloud clients tablishment. This authentication takes place during the SSL hand- based on it; Amazon’s and PayPal’s merchant SDKs responsible shake, when the server presents its public-key certificate. In order for transmitting payment details from e-commerce sites to payment for the SSL connection to be secure, the client must carefully verify gateways; integrated shopping carts such as osCommerce, ZenCart, that the certificate has been issued by a valid certificate authority, Ubercart, and PrestaShop; AdMob code used by mobile websites; has not expired (or been revoked), the name(s) listed in the certifi- Chase mobile banking and several other Android apps and libraries; cate match(es) the name of the domain that the client is connecting Java Web-services middleware—including Apache Axis, Axis 2, to, and perform several other checks [14, 15].