Openwrtdocs - Openwrt
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On Applicability of Wireless Routers to Deployment of Smart Spaces in Internet of Things Environments Sergey A
The 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications 21-23 September 2017, Bucharest, Romania On Applicability of Wireless Routers to Deployment of Smart Spaces in Internet of Things Environments Sergey A. Marchenkov, Dmitry G. Korzun Petrozavodsk State University (PetrSU) Petrozavodsk, Russia fmarchenk, [email protected] Abstract – The use of wireless technologies is now in- to extend the platform architecture with other protocols evitable in smart spaces development for Internet of Things. by adding new modules. Consequently, the use of wired A smart space is created by deploying a Semantic Informa- and wireless TCP/IP networks is inevitable in Smart-M3- tion Broker (SIB) on a host device. This paper examines the applicability of a wireless router for being a SIB host based development of smart spaces. device to deployment of smart spaces in Internet of Things Wi-Fi is the most common wireless technology to environments. CuteSIB is one of SIB implementations of interconnect different IoT-enabled devices. Almost every the Smart-M3 platform and focus is on Qt-based devices. smart space environment is equipped with a wireless We provide a technique for creating an OpenWrt-based embedded system composed of CuteSIB software compo- access point (a wireless router) to ensure interaction nents for a smart spaces deployment using a cross-compiling between SIB and agents that operate on mobile devices method. The resulting embedded system is used to deploy (e.g. smartphones, tablets). In this configuration, SIB is the SmartRoom system—a Smart-M3-based application that deployed on a dedicated host device (e.g. -
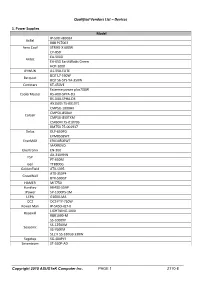
Qualified Vendors List – Devices
Qualified Vendors List – Devices 1. Power Supplies Model IP-500 HB9024 AcBel R88 PC7063 Aero Cool STRIKE-X 600W CP-850 EA-500D Antec EA-650 EarthWatts Green HCP-1000 AYWUN A1-550-ELITE BQT L7-530W Be quiet BQT S6-SYS-YA-350W Comstars KT-450VE Extreme power plus700W CoolerMaster RS-A00-SPPA-D3 RS-D00-SPHA-D3 AX1500i 75-001971 CMPSU-1000HX CMPSU-850AX Corsair CMPSU-850TXM CS450M 75-010706 RM750 75-001937 Delux DLP-650PG EPM850EWT EnerMAX ERV1050EWT MAXREVO Enertronix EN-300 AX-310HHN FSP PT-650M Geil TTB800G GoldenField ATX-S395 ATX-350P4 GreatWall BTX-500GT HAMER MIT750 Huntkey HK400-55AP JPower SP-1000PS-1M LEPA G1600-MA OCZ OCZ-FTY-750W Power Man IP-S450HQ7-0 LIGHTNING-1000 Rosewill RBR1000-M SS-1000XP SS-1250XM Seasonic SS-760KM S12 II SS-330GB 330W Segotep SG-400PYJ Seventeam ST-550P-AD Copyright 2015 ASUSTeK Computer Inc. PAGE 1 Z170-E Model ST-552PAP Seventeam ST-800PGD SST-ST1500 SST-ST40F-ES Silverstone SST-ST85F-GS SST-60F-P SF-350P14XE Super Flower SF-550P14PE TOUGHPOWER TPX775 TOUGHPOWER1500A Thermaltake TP-1050AH3CSG TPX-1275M TR2-RX-1200AH3CH 2. Hard Drives 2.1. HDD Devices Type Model HDS723030ALA640 Hitachi HDS724040ALE640 HD103SM Samsung HD322GM ST1000DM003 ST1000DX001 ST2000NM0033 ST3000DM001 Seagate ST4000DM000 ST500DM002 ST500LM000-3Y/P SATA 6G ST750LX003 WD1002FAEX WD10EZEX WD2002FAEX WD20EFRX WD25EZRX WD WD30EFRX WD30EZRX WD4001FAEX WD5000AAKX WD5000HHTZ Type Model Hitachi HDS721050CLA362 ST3750528AS Seagate ST95005620AS SATA 3G HDP725050GLA360 Simmtrnics WD10EADS Toshiba MK5061SYN Copyright 2015 ASUSTeK Computer Inc. -

Setting up the Linksys EA9300 Max-Stream AC4000 Tri-Band Wi-Fi Router
Setting up the Linksys EA9300 Max-Stream AC4000 Tri-Band Wi-Fi Router Setting up the Linksys EA9300 Max-Stream AC4000 Tri-Band Wi-Fi Router is made easy using the Smart Setup wizard which is embedded in the router's firmware and is available even if the router does not have an internet connection or the router is on factory default settings. Before you begin: Make sure you have a working internet connection. Power on your modem and connect an ethernet cable from the modem to the internet port of the router. NOTE: If you are replacing an existing router, make sure to disconnect and remove the old one. Connect the power adapter to the router and turn it ON. Wait until the Linksys logo light is solid. Step 1: Connect a wireless computer, tablet or smartphone to the default Wi-Fi network of your router. The wireless credentials are located on a label at the bottom of the device. NOTE: If you need to set up the router using a hardwired computer, connect your computer to one of the ethernet ports at the back of the router. Step 2: Launch a supported web browser and enter “linksyssmartwifi.com” in the Address bar then press [Enter]. NOTE: You can also enter “http://192.168.1.1” or “myrouter.local”. Step 3: Check the box beside I have read and accepted the License Terms for using this software. Then click Next to proceed. NOTE: Open the link to know the license terms and other information. If you prefer to manually set up the router, click on the Manual configuration link. -

Integrity Enhancements for Embedded Linux Devices
Integrity Enhancements for Embedded Linux Devices David Safford [email protected] This material is based on research sponsored by the Department of Homeland Security (DHS) Science and Technology Directorate, Homeland Security Advanced Research Projects Agency, Cyber Security Division (DHS S&T/HSARPA/CSD), BAA 11-02 and Air Force Research Laboratory, Information Directorate under agreement number FA8750-12-2-0243. The U.S. Government is authorized to reproduce and distribute reprints for Governmental purposes notwithstanding any copyright notation thereon. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of Department of Homeland Security, Air Force Research Laboratory or the U.S. Government. Embedded Linux Integrity ● Server $10K+ PB 4768 Crypto card Trusted and Secure Boot ● PC $1K TB TPM Trusted and Secure Boot (Win8) ● mobile $500 GB Restricted Boot ● embedded $50 MB Nothing ● Sensor $10 KB Nothing Example Embedded Linux Devices ● Pogoplug ● TP-Link MR3020 ● D-Link DIR-505 ● Linksys WRT54G MR-3020 Main Components Three main chips SoC (32 bit MIPS) RAM (32MB) SPI Flash (4MB) Partition Name Size Contents mtd0 “boot” 64KB u-boot mtd1 “kernel” 1024KB Linux Kernel mtd2 “rootfs” 2816KB Linux root filesystem mtd3 “config” 64KB config data mtd4 “ART” 64KB radio config data Recent Embedded Linux Vulnerabilities ● 2012: 4.5 Million home routers compromised in Brazil – https://www.securelist.com/en/blog/208193852/The_tale_of_one_thousand -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

WRT310N Wireless-N Gigabit Router
USER GUIDE Wireless-N Gigabit Router Model: WRT310N About This Guide About This Guide Icon Descriptions While reading through the User Guide you may see various icons that call attention to specific items. Below is a description of these icons: NOTE: This check mark indicates that there is a note of interest and is something that you should pay special attention to while using the product. WARNING: This exclamation point indicates that there is a caution or warning and it is something that could damage your property or product. WEB: This globe icon indicates a noteworthy website address or e-mail address. Online Resources Website addresses in this document are listed without http:// in front of the address because most current web browsers do not require it. If you use an older web browser, you may have to add http:// in front of the web address. Resource Website Linksys www.linksys.com Linksys International www.linksys.com/international Glossary www.linksys.com/glossary Network Security www.linksys.com/security Copyright and Trademarks Linksys is a registered trademark or trademark of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries. Copyright © 2008 Cisco Systems, Inc. All rights reserved. Other brands and product names are trademarks or registered trademarks of their respective holders. Wireless-N Gigabit Router i Table of Contents Chapter 1: Product Overview 4 Front Panel. 4 Back Panel . 4 Placement Positions . 4 Chapter 2: Wireless Security Checklist 6 General Network Security Guidelines . 6 Additional Security Tips . 6 Chapter 3: Advanced Configuration 7 Setup > Basic Setup . -

Hacking Roomba®
Hacking Roomba® Tod E. Kurt Wiley Publishing, Inc. Hacking Roomba® Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2007 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN-13: 978-0-470-07271-4 ISBN-10: 0-470-07271-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. The advice and strategies contained herein may not be suitable for every situation. This work is sold with the understanding that the publisher is not engaged in rendering legal, accounting, or other professional services. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -
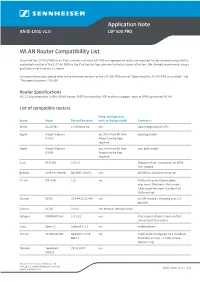
Application Note LSP 500 PRO WLAN Router Compatibility List
Application Note AN IS-1001 v1.0 LSP 500 PRO WLAN Router Compatibility List To control the LSP 500 PRO via an iPad, a wireless network (WLAN) and appropriate router are required. For guaranteed compatibility and reliable control of the LSP 500 PRO via the iPad Control App, we have tested a number of routers. We strongly recommend using a qualifi ed router from our list below. For more information, please refer to the following sections of the LSP 500 PRO manual “Operating the LSP 500 PRO via a tablet” and “The operating menu / WLAN”. Router Specifi cations 802.11 b/g compatible 2.4GHz WLAN Router, DHCP functionality, UDP multicast support, open or WPA2 protected WLAN List of compatible routers Initial confi guration Brand Model Tested Firmware with an iPad possible? Comments Allnet ALL02761 1.0 Release 04 yes slow recognition of LSPs Apple Airport Express yes, fi rst time OK then old plug model A1264 Airport confi g App required Apple Airport Express yes, fi rst time OK then new desk model A1392 Airport confi g App required Asus RT-N13U 2.0.2.0 Popup on iPad - connection on WAN- Port needed Buffalo WHR-HP-G300N DD-WRT v24SP2 yes DD-WRTas standard fi rmware! D-Link DIR-826L 1.01 no Multicasting must be enabled over menu (Network->Advanced- >Advanced Network->Enable IPv4 Multicasting) Huawei E5331 21.344.11.01.414 yes no SIM needed / charging over LSP possible Linksys E1200 2.0.04 yes (manual confi guration) Netgear WNDR3700v4 1.0.1.32 yes iPad shows hotspot screen on fi rst connect but then works Sony Xperia S Android 4.1.2 no mobile phone… TP Link TL-WR1043ND OpenWrt 12.09 no needs to be confi gured /w a standard Beta 2 PC before 1st use --> http://www. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -

C:\Users\John\Documents\Forums
Network speed between a given system adapter and the network Router is determined by the slowest network device. If the Router is an N Router, then your adapter mode is set for G. The problem is likely your Intel AGN Adapter settings - it's Wireless Mode is likely set to G, B/G, or A/B/G, but the N Mode setting probably isn't Enabled, which overrides the other Wireless Modes. Prior to the procedures below, go to Linksys Support, look up your Router, then download the latest firmware update. If it's the same as what you have, then download that. Linksys Support Standard Procedure for any Linksys Router problem with speed or signal begins with flashing the firmware prior to adjusting any other settings. I've added settings for your Router to match your adapter since I have the same hardware. You can look for your Router's firmware update at Linksys Support Enter your Model # and go from there to get the firmware update. The following assumes you have a Linksys Single Band N Router; though these settings are from my Linksys WRT600N Dual-Band, the Admin Panel is the same, except for the extra 5ghz Band setup on mine. Just in case, I've also added the 5ghz settings. With these settings and the AGN or my Linksys WUSB600N DBN Adapter, I average better than 200mbps+, usually around 240 or 260mbps. The settings for the AGN adapter after these settings are matched for the Router settings. On your Router: Access the Router Admin Panel & Wireless Settings from your Browser - http://192.168.1.1/BasicWirelessSettings.htm 1. -
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark.