Sylo Protocol: Secure Group Messaging
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A History of End-To-End Encryption and the Death of PGP
25/05/2020 A history of end-to-end encryption and the death of PGP Hey! I'm David, a security engineer at the Blockchain team of Facebook (https://facebook.com/), previously a security consultant for the Cryptography Services of NCC Group (https://www.nccgroup.com). I'm also the author of the Real World Cryptography book (https://www.manning.com/books/real-world- cryptography?a_aid=Realworldcrypto&a_bid=ad500e09). This is my blog about cryptography and security and other related topics that I Ûnd interesting. A history of end-to-end encryption and If you don't know where to start, you might want to check these popular the death of PGP articles: posted January 2020 - How did length extension attacks made it 1981 - RFC 788 - Simple Mail Transfer Protocol into SHA-2? (/article/417/how-did-length- extension-attacks-made-it-into-sha-2/) (https://tools.ietf.org/html/rfc788) (SMTP) is published, - Speed and Cryptography the standard for email is born. (/article/468/speed-and-cryptography/) - What is the BLS signature scheme? (/article/472/what-is-the-bls-signature- This is were everything starts, we now have an open peer-to-peer scheme/) protocol that everyone on the internet can use to communicate. - Zero'ing memory, compiler optimizations and memset_s (/article/419/zeroing-memory- compiler-optimizations-and-memset_s/) 1991 - The 9 Lives of Bleichenbacher's CAT: New Cache ATtacks on TLS Implementations The US government introduces the 1991 Senate Bill 266, (/article/461/the-9-lives-of-bleichenbachers- which attempts to allow "the Government to obtain the cat-new-cache-attacks-on-tls- plain text contents of voice, data, and other implementations/) - How to Backdoor Di¸e-Hellman: quick communications when appropriately authorized by law" explanation (/article/360/how-to-backdoor- from "providers of electronic communications services di¸e-hellman-quick-explanation/) and manufacturers of electronic communications - Tamarin Prover Introduction (/article/404/tamarin-prover-introduction/) service equipment". -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Security & Privacy for Mobile Phones
Security & Privacy FOR Mobile Phones Carybé, Lucas Helfstein July 4, 2017 Instituto DE Matemática E Estatística - USP What IS security? • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; 1 • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; 1 • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; 1 Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. 1 Security IS ... A System! Eve | | | Alice "Hi" <---------------> "Hi" Bob 2 Security IS ... Cryptography! Eve | | | Alice "Hi" <----"*****"------> "Hi" Bob 3 Security IS ... Impossible! The ONLY TRULY SECURE SYSTEM IS ONE THAT IS POWERED off, CAST IN A BLOCK OF CONCRETE AND SEALED IN A lead-lined ROOM WITH ARMED GUARDS - AND EVEN THEN I HAVE MY doubts. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
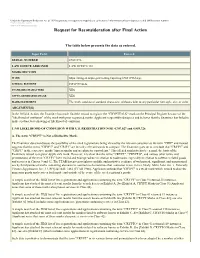
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

Modern End-To-End Encrypted Messaging for the Desktop
Die approbierte Originalversion dieser Diplom-/ Masterarbeit ist in der Hauptbibliothek der Tech- nischen Universität Wien aufgestellt und zugänglich. http://www.ub.tuwien.ac.at The approved original version of this diploma or master thesis is available at the main library of the Vienna University of Technology. http://www.ub.tuwien.ac.at/eng Modern End-to-End Encrypted Messaging for the Desktop DIPLOMARBEIT zur Erlangung des akademischen Grades Diplom-Ingenieur im Rahmen des Studiums Software Engineering and Internet Computing eingereicht von Richard Bayerle Matrikelnummer 1025259 an der Fakultät für Informatik der Technischen Universität Wien Betreuung: Privatdozent Dipl.Ing. Mag. Dr. Edgar Weippl Mitwirkung: Dr. Martin Schmiedecker Wien, 2. Oktober 2017 Richard Bayerle Edgar Weippl Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Modern End-to-End Encrypted Messaging for the Desktop DIPLOMA THESIS submitted in partial fulfillment of the requirements for the degree of Diplom-Ingenieur in Software Engineering and Internet Computing by Richard Bayerle Registration Number 1025259 to the Faculty of Informatics at the TU Wien Advisor: Privatdozent Dipl.Ing. Mag. Dr. Edgar Weippl Assistance: Dr. Martin Schmiedecker Vienna, 2nd October, 2017 Richard Bayerle Edgar Weippl Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Erklärung zur Verfassung der Arbeit Richard Bayerle Seestraße 67 78315 Radolfzell am Bodensee Deutschland Hiermit erkläre ich, dass ich diese Arbeit selbständig verfasst habe, dass ich die verwen- deten Quellen und Hilfsmittel vollständig angegeben habe und dass ich die Stellen der Arbeit – einschließlich Tabellen, Karten und Abbildungen –, die anderen Werken oder dem Internet im Wortlaut oder dem Sinn nach entnommen sind, auf jeden Fall unter Angabe der Quelle als Entlehnung kenntlich gemacht habe. -
Openwrtdocs - Openwrt
OpenWrtDocs - OpenWrt Login OpenWrt OpenWrtDocs ● FrontPage ● OpenWrtDocs ● TableOfHardware ● RecentChanges ● FindPage Welcome to the new wiki version of the OpenWrt userguide. To get started, click a link below. About OpenWrt ● About OpenWrt ● Why should I run OpenWrt? ● OpenWrt Version History Installing OpenWrt ● Will OpenWrt work on my hardware ? ● Obtaining the firmware ● Installing OpenWrt ❍ General instructions (router specific instructions later) ❍ Linksys WRT54G and WRT54GS ■ Enabling boot_wait ■ Setting boot_wait from a serial connection ❍ ASUS WL-500G and WL-300G ❍ ASUS WL-500G Deluxe ❍ Siemens Gigaset SE505 ❍ Motorola WR850G ❍ Buffalo Airstation WLA-G54 ❍ Buffalo AirStation WBR2-G54S ● Using OpenWrt ● Troubleshooting http://openwrt.org/OpenWrtDocs (1 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt Using OpenWrt ● Using OpenWrt for the first time ● Firstboot / jffs2 ● Editing Files ● ipkg ● Configuration OpenWrt Configuration ● NVRAM ● Network configuration ❍ Sample network configurations ❍ The ethernet switch ■ Normal Behavior ■ Using Robocfg ● Wireless configuration ❍ Basic settings ❍ WEP encryption ❍ WPA encryption ❍ Wireless Distribution System (WDS) / Repeater / Bridge ❍ OpenWrt as client / wireless bridge ● Software configuration ❍ System ■ dnsmasq ■ nas ■ wl ■ TimeZone and NTP ■ Crontab ■ PPPoE Internet Connection ■ Access to syslog ❍ Applications ■ httpd ■ socks-Proxy http://openwrt.org/OpenWrtDocs (2 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt ■ uPnP ■ CUPS - Printing system with spooling ● Hardware ❍ LED OpenWrt -

XEP-0384: OMEMO Encryption
XEP-0384: OMEMO Encryption Andreas Straub Daniel Gultsch Tim Henkes mailto:andy@strb:org mailto:daniel@gultsch:de mailto:me@syndace:dev xmpp:andy@strb:org xmpp:daniel@gultsch:de Klaus Herberth Paul Schaub Marvin Wißfeld xmpp:klaus@jsxc:org mailto:vanitasvitae@riseup:net mailto:xmpp@larma:de xmpp:vanitasvitae@jabberhead:tk xmpp:jabber@larma:de 2021-09-28 Version 0.8.0 Status Type Short Name Experimental Standards Track OMEMO This specification defines a protocol for end-to-end encryption in one-to-one chats, as well as group chats where each participant may have multiple clients per account. Legal Copyright This XMPP Extension Protocol is copyright © 1999 – 2020 by the XMPP Standards Foundation (XSF). Permissions Permission is hereby granted, free of charge, to any person obtaining a copy of this specification (the ”Specification”), to make use of the Specification without restriction, including without limitation the rights to implement the Specification in a software program, deploy the Specification in a network service, and copy, modify, merge, publish, translate, distribute, sublicense, or sell copies of the Specifi- cation, and to permit persons to whom the Specification is furnished to do so, subject to the condition that the foregoing copyright notice and this permission notice shall be included in all copies or sub- stantial portions of the Specification. Unless separate permission is granted, modified works that are redistributed shall not contain misleading information regarding the authors, title, number, or pub- lisher of the Specification, and shall not claim endorsement of the modified works by the authors, any organization or project to which the authors belong, or the XMPP Standards Foundation. -

Volume 160 May, 2020
Volume 160 May, 2020 Short Topix: Zoombombing Is A Crime, Not A Prank GIMP Tutorial: Photo Editing, Part 3 PCLinuxOS Magazine Friends & Family - jzakiya Champions Of Regnum On PCLinuxOS EBCDIC Handling Library, Part 2 PCLinuxOS Recipe Corner: Lemon Pepper Chicken ms_meme's Nook: The Linux Bounce Wallpaper Roundup, Revisited Finally! ShotCut Running On PCLinuxOS And more inside! PCLinuxOS Magazine Page 1 In This Issue... 3 From The Chief Editor's Desk... 5 Staying "Safe" While You Stream: DBD's Tips On Living DRM-Free During Quarantine The PCLinuxOS name, logo and colors are the trademark of 6 Screenshot Showcase Texstar. 7 PCLinuxOS Recipe Corner: Lemon Pepper Chicken The PCLinuxOS Magazine is a monthly online publication containing PCLinuxOS-related materials. It is published 8 Wallpaper Roundup, Revisited primarily for members of the PCLinuxOS community. The magazine staff is comprised of volunteers from the 13 Screenshot Showcase PCLinuxOS community. 14 ms_meme's Nook: I Want It That Way Visit us online at http://www.pclosmag.com 15 Short Topix: Zoombombing Is A Crime, Not A Prank This release was made possible by the following volunteers: 19 Screenshot Showcase Chief Editor: Paul Arnote (parnote) 20 GIMP Tutorial: Photo Editing, Part 3 Assistant Editor: Meemaw Artwork: Sproggy, Timeth, ms_meme, Meemaw 22 Better than Zoom: Magazine Layout: Paul Arnote, Meemaw, ms_meme HTML Layout: YouCanToo Try These Free Software Tools For Staying In Touch Staff: 25 PCLinuxOS Family Member Spotlight: jzakiya ms_meme CgBoy Meemaw YouCanToo 26 Screenshot Showcase Gary L. Ratliff, Sr. Pete Kelly Daniel Meiß-Wilhelm phorneker 27 Champions Of Regnum On PCLinuxOS daiashi Khadis Thok 32 Screenshot Showcase Alessandro Ebersol Smileeb 33 EBCDIC Handling Library, Part 2 Contributors: 44 PCLinuxOS Bonus Recipe Corner: jzakiya Mashed Potato Mac & Cheese Bake 45 Screenshot Showcase The PCLinuxOS Magazine is released under the Creative 46 Finally! ShotCut Running On PCLinuxOS! Commons Attribution-NonCommercial-Share-Alike 3.0 Unported license. -

Nutzung Von Openpgp Auf Android
Nutzung von OpenPGP auf Android Eine Anforderungsanalyse und Studie vorhandener OpenPGP- Implementierungen Autoren Vincent Breitmoser OpenKeychain Dominik Schürmann Institut für Betriebssysteme und Rechnerverbund, TU Braunschweig OpenKeychain Unter Mitwirkung von: Bernhard Reiter Emanuel Schütze Intevation GmbH Neuer Graben 17 49074 Osnabrück https://intevation.de Werner Koch g10 code GmbH Hüttenstr. 61 40699 Erkrath https://g10code.com Dieses Werk ist unter der Lizenz „Creative Commons Namensnennung-Weitergabe unter gleichen Bedingungen Deutschland“ in Version 3.0 (abgekürzt „CC-by-sa 3.0/de“) veröffentlicht. Den rechtsverbindlichen Lizenzvertrag finden Sie unter http://creativecommons.org/licenses/by-sa/3.0/de/legalcode. Bundesamt für Sicherheit in der Informationstechnik Postfach 20 03 63 53133 Bonn Tel.: +49 22899 9582-0 E-Mail: [email protected] Internet: https://www.bsi.bund.de © Bundesamt für Sicherheit in der Informationstechnik 2016 Änderungshistorie Version Datum Name Beschreibung 1.0 11.5.2016 siehe Autoren Initiale Version für die Veröffentlichung Inhaltsverzeichnis Inhaltsverzeichnis 1 Einleitung............................................................................................................................................................................................... 7 1.1 Ausgangssituation..........................................................................................................7 1.2 Ziel der Studie................................................................................................................7 -

Multi-Device Secure Instant Messaging
SoK: Multi-Device Secure Instant Messaging Antonio Dimeo, Felix Gohla, Daniel Goßen, Niko Lockenvitz {antonio.dimeo, felix.gohla, daniel.gossen, niko.lockenvitz}@student.hpi.de Hasso Plattner Institute, University of Potsdam April 17, 2021 Abstract The secure multi-device instant messaging ecosystem is diverse, varied, and under- represented in academia. We create a systematization of knowledge which focuses on the challenges of multi-device messaging in a secure context and give an overview of the current situation in the multi-device setting. For that, we analyze messenger documentation, white papers, and research that deals with multi-device messaging. This includes a detailed description of different patterns for data transfer between devices as well as device management, i.e. how clients are cryptographically linked or unlinked to or from an account and how the initial setup can be implemented. We then evaluate different instant messengers with regard to relevant criteria, e.g. whether they achieve specific security, usability, and privacy goals. In the end, we outline interesting areas for future research. Contents 1 Introduction3 1.1 Group Messaging vs. Multi-Device Messaging............... 4 1.2 Methodology.................................. 4 2 Multi-Device Messaging7 2.1 Context...................................... 7 2.2 Transferring Data Between Different Devices of One User........ 7 2.2.1 Storing Data on a Server........................ 8 2.2.2 Using Messages to Exchange Data.................. 9 2.3 Transferring Data to a Different User..................... 11 2.3.1 Without End-to-end Encryption................... 11 2.3.2 End-to-end Encryption With Shared Group Key.......... 13 2.3.3 End-to-end Encryption Per Recipient...............