Easybuild Documentation Release 20210907.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Recursive Approach in Sparse Matrix LU Factorization
51 Recursive approach in sparse matrix LU factorization Jack Dongarra, Victor Eijkhout and the resulting matrix is often guaranteed to be positive Piotr Łuszczek∗ definite or close to it. However, when the linear sys- University of Tennessee, Department of Computer tem matrix is strongly unsymmetric or indefinite, as Science, Knoxville, TN 37996-3450, USA is the case with matrices originating from systems of Tel.: +865 974 8295; Fax: +865 974 8296 ordinary differential equations or the indefinite matri- ces arising from shift-invert techniques in eigenvalue methods, one has to revert to direct methods which are This paper describes a recursive method for the LU factoriza- the focus of this paper. tion of sparse matrices. The recursive formulation of com- In direct methods, Gaussian elimination with partial mon linear algebra codes has been proven very successful in pivoting is performed to find a solution of Eq. (1). Most dense matrix computations. An extension of the recursive commonly, the factored form of A is given by means technique for sparse matrices is presented. Performance re- L U P Q sults given here show that the recursive approach may per- of matrices , , and such that: form comparable to leading software packages for sparse ma- LU = PAQ, (2) trix factorization in terms of execution time, memory usage, and error estimates of the solution. where: – L is a lower triangular matrix with unitary diago- nal, 1. Introduction – U is an upper triangular matrix with arbitrary di- agonal, Typically, a system of linear equations has the form: – P and Q are row and column permutation matri- Ax = b, (1) ces, respectively (each row and column of these matrices contains single a non-zero entry which is A n n A ∈ n×n x where is by real matrix ( R ), and 1, and the following holds: PPT = QQT = I, b n b, x ∈ n and are -dimensional real vectors ( R ). -

Red Hat Enterprise Linux 8 Installing, Managing, and Removing User-Space Components
Red Hat Enterprise Linux 8 Installing, managing, and removing user-space components An introduction to AppStream and BaseOS in Red Hat Enterprise Linux 8 Last Updated: 2021-06-25 Red Hat Enterprise Linux 8 Installing, managing, and removing user-space components An introduction to AppStream and BaseOS in Red Hat Enterprise Linux 8 Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. -

Abstract 1 Introduction
Implementation in ScaLAPACK of Divide-and-Conquer Algorithms for Banded and Tridiagonal Linear Systems A. Cleary Department of Computer Science University of Tennessee J. Dongarra Department of Computer Science University of Tennessee Mathematical Sciences Section Oak Ridge National Laboratory Abstract Described hereare the design and implementation of a family of algorithms for a variety of classes of narrow ly banded linear systems. The classes of matrices include symmetric and positive de - nite, nonsymmetric but diagonal ly dominant, and general nonsymmetric; and, al l these types are addressed for both general band and tridiagonal matrices. The family of algorithms captures the general avor of existing divide-and-conquer algorithms for banded matrices in that they have three distinct phases, the rst and last of which arecompletely paral lel, and the second of which is the par- al lel bottleneck. The algorithms have been modi ed so that they have the desirable property that they are the same mathematical ly as existing factorizations Cholesky, Gaussian elimination of suitably reordered matrices. This approach represents a departure in the nonsymmetric case from existing methods, but has the practical bene ts of a smal ler and more easily hand led reduced system. All codes implement a block odd-even reduction for the reduced system that al lows the algorithm to scale far better than existing codes that use variants of sequential solution methods for the reduced system. A cross section of results is displayed that supports the predicted performance results for the algo- rithms. Comparison with existing dense-type methods shows that for areas of the problem parameter space with low bandwidth and/or high number of processors, the family of algorithms described here is superior. -

Other Departments and Institutes Courses 1
Other Departments and Institutes Courses 1 Other Departments and Institutes Courses About Course Numbers: 02-250 Introduction to Computational Biology Each Carnegie Mellon course number begins with a two-digit prefix that Spring: 12 units designates the department offering the course (i.e., 76-xxx courses are This class provides a general introduction to computational tools for biology. offered by the Department of English). Although each department maintains The course is divided into two halves. The first half covers computational its own course numbering practices, typically, the first digit after the prefix molecular biology and genomics. It examines important sources of biological indicates the class level: xx-1xx courses are freshmen-level, xx-2xx courses data, how they are archived and made available to researchers, and what are sophomore level, etc. Depending on the department, xx-6xx courses computational tools are available to use them effectively in research. may be either undergraduate senior-level or graduate-level, and xx-7xx In the process, it covers basic concepts in statistics, mathematics, and courses and higher are graduate-level. Consult the Schedule of Classes computer science needed to effectively use these resources and understand (https://enr-apps.as.cmu.edu/open/SOC/SOCServlet/) each semester for their results. Specific topics covered include sequence data, searching course offerings and for any necessary pre-requisites or co-requisites. and alignment, structural data, genome sequencing, genome analysis, genetic variation, gene and protein expression, and biological networks and pathways. The second half covers computational cell biology, including biological modeling and image analysis. It includes homework requiring Computational Biology Courses modification of scripts to perform computational analyses. -

University of North Carolina at Charlotte Belk College of Business
University of North Carolina at Charlotte Belk College of Business BPHD 8220 Financial Bayesian Analysis Fall 2019 Course Time: Tuesday 12:20 - 3:05 pm Location: Friday Building 207 Professor: Dr. Yufeng Han Office Location: Friday Building 340A Telephone: (704) 687-8773 E-mail: [email protected] Office Hours: by appointment Textbook: Introduction to Bayesian Econometrics, 2nd Edition, by Edward Greenberg (required) An Introduction to Bayesian Inference in Econometrics, 1st Edition, by Arnold Zellner Doing Bayesian Data Analysis: A Tutorial with R, JAGS, and Stan, 2nd Edition, by Joseph M. Hilbe, de Souza, Rafael S., Emille E. O. Ishida Bayesian Analysis with Python: Introduction to statistical modeling and probabilistic programming using PyMC3 and ArviZ, 2nd Edition, by Osvaldo Martin The Oxford Handbook of Bayesian Econometrics, 1st Edition, by John Geweke Topics: 1. Principles of Bayesian Analysis 2. Simulation 3. Linear Regression Models 4. Multivariate Regression Models 5. Time-Series Models 6. State-Space Models 7. Volatility Models Page | 1 8. Endogeneity Models Software: 1. Stan 2. Edward 3. JAGS 4. BUGS & MultiBUGS 5. Python Modules: PyMC & ArviZ 6. R, STATA, SAS, Matlab, etc. Course Assessment: Homework assignments, paper presentation, and replication (or project). Grading: Homework: 30% Paper presentation: 40% Replication (project): 30% Selected Papers: Vasicek, O. A. (1973), A Note on Using Cross-Sectional Information in Bayesian Estimation of Security Betas. Journal of Finance, 28: 1233-1239. doi:10.1111/j.1540- 6261.1973.tb01452.x Shanken, J. (1987). A Bayesian approach to testing portfolio efficiency. Journal of Financial Economics, 19(2), 195–215. https://doi.org/10.1016/0304-405X(87)90002-X Guofu, C., & Harvey, R. -

RZ/G Verified Linux Package for 64Bit Kernel V1.0.5-RT Release Note For
Release Note RZ/G Verified Linux Package for 64bit kernel Version 1.0.5-RT R01TU0311EJ0102 Rev. 1.02 Release Note for HTML5 Sep 7, 2020 Introduction This release note describes the contents, building procedures for HTML5 (Gecko) and important points of the RZ/G Verified Linux Package for 64bit kernel (hereinafter referred to as “VLP64”). In this release, Linux packages for HTML5 is preliminary and provided AS IS with no warranty. If you need information to build Linux BSPs without a GUI Framework of HTML5, please refer to “RZ/G Verified Linux Package for 64bit kernel Version 1.0.5-RT Release Note”. Contents 1. Release Items ................................................................................................................. 2 2. Build environment .......................................................................................................... 4 3. Building Instructions ...................................................................................................... 6 3.1 Setup the Linux Host PC to build images ................................................................................. 6 3.2 Building images to run on the board ........................................................................................ 8 3.3 Building SDK ............................................................................................................................. 12 4. Components ................................................................................................................. 13 5. Restrictions -
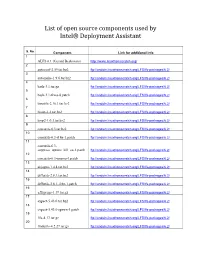
List of Open Source Components Used by Intel® Deployment Assistant
List of open source components used by Intel® Deployment Assistant S. No Component Link for additional info 1 ALFS 6.1 (Gerard Beekmans) http://www.linuxfromscratch.org/ 2 autoconf-2.59.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 3 automake-1.9.6.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 4 bash-3.1.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 5 bash-3.1-fixes-8.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 6 binutils-2.16.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 7 bison-2.2.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 8 bzip2-1.0.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 9 coreutils-6.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 10 coreutils-6.3-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 11 coreutils-6.3- suppress_uptime_kill_su-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 12 coreutils-6.3-uname-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 13 dejagnu-1.4.4.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 14 diffutils-2.8.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 15 diffutils-2.8.1-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 16 e2fsprogs-1.39.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 17 expect-5.43.0.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 18 expect-5.43.0-spawn-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ -
![[PDF] Beginning Raku](https://docslib.b-cdn.net/cover/0681/pdf-beginning-raku-210681.webp)
[PDF] Beginning Raku
Beginning Raku Arne Sommer Version 1.00, 22.12.2019 Table of Contents Introduction. 1 The Little Print . 1 Reading Tips . 2 Content . 3 1. About Raku. 5 1.1. Rakudo. 5 1.2. Running Raku in the browser . 6 1.3. REPL. 6 1.4. One Liners . 8 1.5. Running Programs . 9 1.6. Error messages . 9 1.7. use v6. 10 1.8. Documentation . 10 1.9. More Information. 13 1.10. Speed . 13 2. Variables, Operators, Values and Procedures. 15 2.1. Output with say and print . 15 2.2. Variables . 15 2.3. Comments. 17 2.4. Non-destructive operators . 18 2.5. Numerical Operators . 19 2.6. Operator Precedence . 20 2.7. Values . 22 2.8. Variable Names . 24 2.9. constant. 26 2.10. Sigilless variables . 26 2.11. True and False. 27 2.12. // . 29 3. The Type System. 31 3.1. Strong Typing . 31 3.2. ^mro (Method Resolution Order) . 33 3.3. Everything is an Object . 34 3.4. Special Values . 36 3.5. :D (Defined Adverb) . 38 3.6. Type Conversion . 39 3.7. Comparison Operators . 42 4. Control Flow . 47 4.1. Blocks. 47 4.2. Ranges (A Short Introduction). 47 4.3. loop . 48 4.4. for . 49 4.5. Infinite Loops. 53 4.6. while . 53 4.7. until . 54 4.8. repeat while . 55 4.9. repeat until. 55 4.10. Loop Summary . 56 4.11. if . .. -

Files: Cpan/Test-Harness/* Copyright: Copyright (C) 2007-2011
Files: cpan/Test-Harness/* Copyright: Copyright (c) 2007-2011, Andy Armstrong <[email protected]>. All rights reserved. License: GPL-1+ or Artistic Comment: This module is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Harness/lib/TAP/Parser.pm Copyright: Copyright 2006-2008 Curtis "Ovid" Poe, all rights reserved. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Harness/lib/TAP/Parser/YAMLish/Reader.pm Copyright: Copyright 2007-2011 Andy Armstrong. Portions copyright 2006-2008 Adam Kennedy. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Simple/* Copyright: Copyright 2001-2008 by Michael G Schwern <[email protected]>. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Simple/lib/Test/Builder.pm Copyright: Copyright 2002-2008 by chromatic <[email protected]> and Michael G Schwern E<[email protected]>. License: GPL-1+ or Artistic 801 Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. Files: cpan/Test-Simple/lib/Test/Builder/Tester/Color.pm Copyright: Copyright Mark Fowler <[email protected]> 2002. License: GPL-1+ or Artistic Comment: This program is free software; you can redistribute it and/or modify it under the same terms as Perl itself. -

Easybuild Documentation Release 20210907.0
EasyBuild Documentation Release 20210907.0 Ghent University Tue, 07 Sep 2021 08:55:41 Contents 1 What is EasyBuild? 3 2 Concepts and terminology 5 2.1 EasyBuild framework..........................................5 2.2 Easyblocks................................................6 2.3 Toolchains................................................7 2.3.1 system toolchain.......................................7 2.3.2 dummy toolchain (DEPRECATED) ..............................7 2.3.3 Common toolchains.......................................7 2.4 Easyconfig files..............................................7 2.5 Extensions................................................8 3 Typical workflow example: building and installing WRF9 3.1 Searching for available easyconfigs files.................................9 3.2 Getting an overview of planned installations.............................. 10 3.3 Installing a software stack........................................ 11 4 Getting started 13 4.1 Installing EasyBuild........................................... 13 4.1.1 Requirements.......................................... 14 4.1.2 Using pip to Install EasyBuild................................. 14 4.1.3 Installing EasyBuild with EasyBuild.............................. 17 4.1.4 Dependencies.......................................... 19 4.1.5 Sources............................................. 21 4.1.6 In case of installation issues. .................................. 22 4.2 Configuring EasyBuild.......................................... 22 4.2.1 Supported configuration -
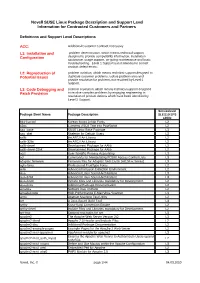
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP3 s390x 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-32bit An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 aalib-devel-32bit Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-32bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. L2 alsa-docs Additional Package Documentation. L2 amanda Network Disk Archiver L2 amavisd-new High-Performance E-Mail Virus Scanner L3 amtu Abstract Machine Test Utility L2 ant A Java-Based Build Tool L3 anthy Kana-Kanji Conversion Engine L2 anthy-devel Include Files and Libraries mandatory for Development. -

Selenium Python Bindings Release 2
Selenium Python Bindings Release 2 Baiju Muthukadan Sep 03, 2021 Contents 1 Installation 3 1.1 Introduction...............................................3 1.2 Installing Python bindings for Selenium.................................3 1.3 Instructions for Windows users.....................................3 1.4 Installing from Git sources........................................4 1.5 Drivers..................................................4 1.6 Downloading Selenium server......................................4 2 Getting Started 7 2.1 Simple Usage...............................................7 2.2 Example Explained............................................7 2.3 Using Selenium to write tests......................................8 2.4 Walkthrough of the example.......................................9 2.5 Using Selenium with remote WebDriver................................. 10 3 Navigating 13 3.1 Interacting with the page......................................... 13 3.2 Filling in forms.............................................. 14 3.3 Drag and drop.............................................. 15 3.4 Moving between windows and frames.................................. 15 3.5 Popup dialogs.............................................. 16 3.6 Navigation: history and location..................................... 16 3.7 Cookies.................................................. 16 4 Locating Elements 17 4.1 Locating by Id.............................................. 18 4.2 Locating by Name............................................ 18 4.3