Red Hat Enterprise Linux 8 Installing, Managing, and Removing User-Space Components
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Learning to Program in Perl
Learning to Program in Perl by Graham J Ellis Languages of the Web Learning to Program in Perl version 1.7 Written by Graham Ellis [email protected] Design by Lisa Ellis Well House Consultants, Ltd. 404, The Spa, Melksham, Wiltshire SN12 6QL England +44 (0) 1225 708 225 (phone) +44 (0) 1225 707 126 (fax) Find us on the World Wide Web at: http://www.wellho.net Or contact us at: [email protected] Copyright © 2003 by Well House Consultants, Ltd. Printed in Great Britain. Printing History May 1999 1.0 First Edition February 2000 1.1 Minor additions June 2000 1.2 Compliation of modules October 2000 1.3 Name change, revisions April 2002 1.4 Added modules September 2002 1.5 Added modules January 2003 1.6 Updated modules February 2003 1.7 Updated modules This manual was printed on 21 May 2003. Notice of Rights All rights reserved. No part of this manual, including interior design, may be reproduced or translated into any language in any form, or transmitted in any form or by any means electronic, mechanical, photocopying, recording or otherwise, without prior written permission of Well House Consultants except in the case of brief quotations embodied in critical articles and reviews. For more information on getting permission for reprints and excerpts, contact Graham Ellis at Well House Consultants. This manual is subject to the condition that it shall not, by way of trade or otherwise, be lent, sold, hired out or otherwise circulated without the publisher's prior consent, incomplete nor in any form of binding or cover other than in which it is published and without a similar condition including this condition being imposed on the subsequent receiver. -

How to Secure Your Web Site Picked up SQL Injection and Cross-Site Scripting As Sample Cases of Failure Because These Two Are the Two Most Reported Vulnerabilities
How to Secure your Website rd 3 Edition Approaches to Improve Web Application and Web Site Security June 2008 IT SECURITY CENTER (ISEC) INFORMATION-TECHNOLOGY PROMOTION AGENCY, JAPAN This document is a translation of the original Japanese edition. Please be advises that most of the references referred in this book are offered in Japanese only. Both English and Japanese edition are available for download at: http://www.ipa.go.jp/security/english/third.html (English web page) http://www.ipa.go.jp/security/vuln/websecurity.html (Japanese web page) Translated by Hiroko Okashita (IPA), June 11 2008 Contents Contents ......................................................................................................................................... 1 Preface ........................................................................................................................................... 2 Organization of This Book ........................................................................................................... 3 Intended Reader ......................................................................................................................... 3 Fixing Vulnerabilities – Fundamental Solution and Mitigation Measure - .................................... 3 1. Web Application Security Implementation ............................................................................... 5 1.1 SQL Injection .................................................................................................................... 6 1.2 -

Vpro-1085-R Course for RHV/Ovirt/OLVM Implementation & Administration Lab Exercises
vPro-1085-R - Storware vProtect - Implementation & Administration Lab Exercises - v7.md 2/24/2021 vPro-1085-R Course for RHV/oVirt/OLVM Implementation & Administration Lab Exercises Credentials and access details Attribute Value Download URL http://10.40.0.253/lab-materials/vprotect/vpro-1085 vProtect host 10.41.0.4 vProtect username root vProtect password St0rL@bs vProtect Web UI https://10.41.0.4 vProtect Web UI username admin vProtect Web UI password vPr0tect RHV manager UI https://rhv-m.storware.lab/ovirt-engine RHV user admin@internal in vProtect in UI, and admin in RHV manager UI RHV password St0rL@bs Lab 1 - Demo of all-in-one installation In this section we'll show you how to install vProtect components quickly using all-in-one setup scripts. Before installation steps please update and then reboot system dnf -y update Remote repository (option 1) 1. Export VPROTECT_REPO variable to point to the repository URL export VPROTECT_REPO=http://10.40.0.253/vprotect/current/el8 2. Execute script: bash < <(curl -s http://repo.storware.eu/vprotect/vprotect-local-install.sh) 1 / 31 vPro-1085-R - Storware vProtect - Implementation & Administration Lab Exercises - v7.md 2/24/2021 Lab 2 - Installation with RPMs In this section you're going to install vProtect using RPMs - so that all necessary steps are done Prerequisites 1. Access vlab.vpro.proxy.v3 2. Open putty on your vlab.vpro.proxy.v3 3. Connect to vProtect machine with a root access 4. Use your CentOS 8 minimal 5. Make sure your OS is up to date: dnf -y update If kernel is updated, then You need to reboot your operating system. -

Perl DBI API Reference
H Perl DBI API Reference This appendix describes the Perl DBI application programming interface. The API consists of a set of methods and attributes for communicating with database servers and accessing databases from Perl scripts. The appendix also describes MySQL-specific extensions to DBI provided by DBD::mysql, the MySQL database driver. I assume here a minimum version of DBI 1.50, although most of the material applies to earlier versions as well. DBI 1.50 requires at least Perl 5.6.0 (with 5.6.1 preferred). As of DBI 1.611, the minimum Perl version is 5.8.1. I also assume a minimum version of DBD::mysql 4.00. To determine your versions of DBI and DBD::mysql (assuming that they are installed), run this program: #!/usr/bin/perl # dbi-version.pl - display DBI and DBD::mysql versions use DBI; print "DBI::VERSION: $DBI::VERSION\n"; use DBD::mysql; print "DBD::mysql::VERSION: $DBD::mysql::VERSION\n"; If you need to install the DBI software, see Appendix A , “Software Required to Use This Book.” Some DBI methods and attributes are not discussed here, either because they do not apply to MySQL or because they are experimental methods that may change as they are developed or may even be dropped. Some MySQL-specific DBD methods are not discussed because they are obsolete. For more information about new or obsolete methods, see the DBI or DBD::mysql documentation, available at http://dbi.perl.org or by running the following commands: % perldoc DBI % perldoc DBI::FAQ % perldoc DBD::mysql The examples in this appendix are only brief code fragments. -

Using the Mysql Yum Repository Abstract
Using the MySQL Yum Repository Abstract This document provides some basic instructions for using the MySQL Yum Repository to install and upgrade MySQL. It is excerpted from the MySQL 5.6 Reference Manual. For legal information, see the Legal Notices. For help with using MySQL, please visit the MySQL Forums, where you can discuss your issues with other MySQL users. Document generated on: 2021-09-23 (revision: 70881) Table of Contents Preface and Legal Notices ............................................................................................................ v 1 Installing MySQL on Linux Using the MySQL Yum Repository ..................................................... 1 2 Replacing a Third-Party Distribution of MySQL Using the MySQL Yum Repository ........................ 5 3 Upgrading MySQL with the MySQL Yum Repository ................................................................... 9 iii iv Preface and Legal Notices This document provides some basic instructions for using the MySQL Yum Repository to install and upgrade MySQL. It is excerpted from the MySQL 5.6 Reference Manual. Licensing information—MySQL 5.6. This product may include third-party software, used under license. If you are using a Commercial release of MySQL 5.6, see the MySQL 5.6 Commercial Release License Information User Manual for licensing information, including licensing information relating to third-party software that may be included in this Commercial release. If you are using a Community release of MySQL 5.6, see the MySQL 5.6 Community Release License Information User Manual for licensing information, including licensing information relating to third-party software that may be included in this Community release. Licensing information—MySQL NDB Cluster 7.3. This product may include third-party software, used under license. If you are using a Commercial release of NDB Cluster 7.3, see the MySQL NDB Cluster 7.3 Commercial Release License Information User Manual for licensing information relating to third-party software that may be included in this Commercial release. -
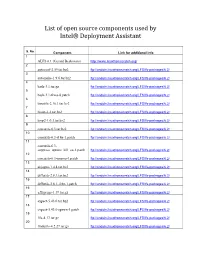
List of Open Source Components Used by Intel® Deployment Assistant
List of open source components used by Intel® Deployment Assistant S. No Component Link for additional info 1 ALFS 6.1 (Gerard Beekmans) http://www.linuxfromscratch.org/ 2 autoconf-2.59.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 3 automake-1.9.6.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 4 bash-3.1.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 5 bash-3.1-fixes-8.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 6 binutils-2.16.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 7 bison-2.2.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 8 bzip2-1.0.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 9 coreutils-6.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 10 coreutils-6.3-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 11 coreutils-6.3- suppress_uptime_kill_su-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 12 coreutils-6.3-uname-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 13 dejagnu-1.4.4.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 14 diffutils-2.8.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 15 diffutils-2.8.1-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 16 e2fsprogs-1.39.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 17 expect-5.43.0.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 18 expect-5.43.0-spawn-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ -

Release Notes for Fedora 22
Fedora 22 Release Notes Release Notes for Fedora 22 Edited by The Fedora Docs Team Copyright © 2015 Fedora Project Contributors. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries. All other trademarks are the property of their respective owners. -

The Next-Gen Apertis Application Framework 1 Contents
The next-gen Apertis application framework 1 Contents 2 Creating a vibrant ecosystem ....................... 2 3 The next-generation Apertis application framework ........... 3 4 Application runtime: Flatpak ....................... 4 5 Compositor: libweston ........................... 6 6 Audio management: PipeWire and WirePlumber ............ 7 7 Session management: systemd ....................... 7 8 Software distribution: hawkBit ...................... 8 9 Evaluation .................................. 8 10 Focus on the development user experience ................ 12 11 Legacy Apertis application framework 13 12 High level implementation plan for the next-generation Apertis 13 application framework 14 14 Flatpak on the Apertis images ...................... 15 15 The Apertis Flatpak application runtime ................. 15 16 Implement a new reference graphical shell/compositor ......... 16 17 Switch to PipeWire for audio management ................ 16 18 AppArmor support ............................. 17 19 The app-store ................................ 17 20 As a platform, Apertis needs a vibrant ecosystem to thrive, and one of the 21 foundations of such ecosystem is being friendly to application developers and 22 product teams. Product teams and application developers are more likely to 23 choose Apertis if it offers flows for building, shipping, and updating applications 24 that are convenient, cheap, and that require low maintenance. 25 To reach that goal, a key guideline is to closely align to upstream solutions 26 that address those needs and integrate them into Apertis, to provide to appli- 27 cation authors a framework that is made of proven, stable, complete, and well 28 documented components. 29 The cornerstone of this new approach is the adoption of Flatpak, the modern 30 application system already officially supported on more than 20 Linux distribu- 1 31 tions , including Ubuntu, Fedora, Red Hat Enterprise, Alpine, Arch, Debian, 32 ChromeOS, and Raspian. -

Managing Software with Yum
Fedora Core 4 Managing software with yum Stuart Ellis Edited by Paul W. Frields Copyright © 2005 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. All other trademarks are the property of their respective owners. 1. Introduction ............................................................................................................................. 2 1.1. Purpose ....................................................................................................................... 2 1.2. Audience .................................................................................................................... -

Bigfix Patch Centos User Guide
BigFix Patch for CentOS User's Guide Special notice Before using this information and the product it supports, read the information in Notices (on page 91). Edition notice This edition applies to version 9.5 of BigFix and to all subsequent releases and modifications until otherwise indicated in new editions. Contents Special notice................................................................................................................................ 2 Edition notice............................................................................................................................... 3 Chapter 1. Overview.......................................................................................................... 1 What's new in this update release....................................................................................... 2 Supported platforms and updates.......................................................................................8 Supported CentOS repositories..........................................................................................10 Site subscription..................................................................................................................12 Patching method................................................................................................................. 12 Chapter 2. Using the download plug-in........................................................................... 14 Manage Download Plug-ins dashboard overview.............................................................15 -

Oracle® Linux Virtualization Manager Getting Started Guide
Oracle® Linux Virtualization Manager Getting Started Guide F25124-11 September 2021 Oracle Legal Notices Copyright © 2019, 2021 Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

Perl Variables Scalar ($) Array (@) Hash (%)
Practical Extraction and Report Language « Perl is a language of getting your job done » « There is more than one way to do it » Larry Wall VI, October 2006 Page 1 Perl Outline : History Structure of a simple Perl script Perl variables scalar ($) array (@) hash (%) Operators (numeric, string & logical) Statement modifiers (if/elsif/else, for/foreach, while) VI, October 2006 Page 2 Practical Extraction and Report Language http://perl.oreilly.com " Perl is both a programming language and an application on your computer that runs those programs " VI, October 2006 Page 3 Perl history A few dates: 1969 UNIX was born at Bell Labs. 1970 Brian Kernighan suggested the name "Unix" and the operating system we know today was born. 1972 The programming language C is born at the Bell Labs (C is one of Perl's ancestors). 1973 “grep” is introduced by Ken Thompson as an external utility: Global REgular expression Print. 1976 Steven Jobs and Steven Wozniak found Apple Computer (1 April). 1977 The computer language awk is designed by Alfred V. Aho, Peter J. Weinberger, and Brian W. Kernighan (awk is one of Perl's ancestors). VI, October 2006 Page 4 Perl history 1987 Perl 1.000 is unleashed upon the world NAME perl | Practical Extraction and Report Language SYNOPSIS perl [options] filename args DESCRIPTION Perl is a interpreted language optimized for scanning arbitrary text files, extracting information from those text files, and printing reports based on that information. It's also a good language for many system management tasks. The language is intended to be practical (easy to use, efficient, complete) rather than beautiful (tiny, elegant, minimal).