A History of Telegraphy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Alpha • Bravo • Charlie
ALPHA • BRAVO • CHARLIE Inspired by Alpha, Bravo, Charlie (published by Phaidon) these Perfect activity sheets introduce young people to four different nautical codes. There are messages to decode, questions to answer for curious and some fun facts to share with friends and family. 5-7 year olds FLAG IT UP These bright, colorful flags are known as signal flags. There is one flag for each letter of the alphabet. 1. What is the right-hand side of a ship called? Use the flags to decode the answer! 3. Draw and color the flag that represents the first letter of your name. 2. Draw and color flags to spell out this message: SHIP AHOY SH I P AHOY FUN FACT Each flag also has its own To purchase your copy of meaning when it's flown by 2. Alpha, Bravo, Charlie visit phaidon.com/childrens2016 itself. For example, the N flag by STARBOARD 1. itself means "No" or "Negative". Answers: ALPHA OSCAR KILO The Phonetic alphabet matches every letter with a word so that letters can’t be mixed up and sailors don’t get the wrong message. 1. Write in the missing first letters from these words in the Phonetic alphabet. What word have you spelled out? Write it in here: HINT: The word for things that are transported by ship. 2. Can you decode the answer to this question: What types of cargo did Clipper ships carry in the 1800s? 3. Use the Phonetic alphabet to spell out your first name. FUN FACT The Phonetic alphabet’s full name is the GOLD AND WOOL International Radiotelephony Spelling Alphabet. -
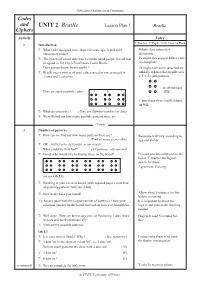
UNIT 2 Braille
Mathematics Enhancement Programme Codes and UNIT 2 Braille Lesson Plan 1 Braille Ciphers Activity Notes T: Teacher P: Pupil Ex.B: Exercise Book 1 Introduction T: What code, designed more than 150 years ago, is still used Whole class interactive extensively today? discussion. T: The system of raised dots which enables blind people to read was Ps might also suggest Morse code designed in 1833 by a Frenchman, Louis Braille. or semaphore. Does anyone know how it works? Ps might have some ideas but are T: Braille uses a system of dots, either raised or not, arranged in unlikely to know that Braille uses 3 rows and 2 columns. a 32× configuration. on whiteboard Here are some possible codes: ape (WB). T puts these three Braille letters on WB. T: What do you notice? (They use different numbers of dots) T: We will find out how many possible patterns there are. 10 mins 2 Number of patterns T: How can we find out how many patterns there are? Response will vary according to (Find as many as possible) age and ability. T: OK – but let us be systematic in our search. What could we first find? (All patterns with one dot) T: Good; who would like to display these on the board? P(s) put possible solutions on the board; T stresses the logical search for these. Agreement. Praising. (or use OS 2.1) T: Working in your exercise books (with squared paper), now find all possible patterns with just 2 dots. T: How many have you found? Allow about 5 minutes for this before reviewing. -

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

Samuel B. Morse, Painter (PDF)
Motto/Logo ( Nicole Greaney) Thesis (Group) Influences and Comparison to Leonardo DaVinci (Joe Fiore) Biography (Traci Gottlieb) Works (Nicole Greaney) Slide Sh ow o f Wor ks /Des igns (Nico le G reaney ) Place (Kristen Alldredge) Itinerary (()Traci Gottlieb) Lesson Plan (Kristen Alldredge) Mock Web Site (Joe Fiore) Web Page for Guidebook (Traci Gottlieb) Conclusion (Group) Without Samuel Finley Breese Morse’s expansive imagination, consequent creatiiivity and perseverance developed through artistry, he would not have been cappgable of making his other contributions to the world, such as Locust Grove and the telegraph. Morse is the American Leonardo because he is an ideal Renaissance Man, with mastery in the dualisms of art and science. •Why an artist? • as a boy, favorite activity was drawing • while attending Yale , drew pictures of classmates/sold them for spending money • setbacks: Self Portrait • art still new in America, not much of a demand • ititimpatient, expect tdittihed instant riches • acquired an enhanced sense of determination • eventually led to his success as an inventor • became ppyrominently known as an artist in the 1820s and 1830s • foundation of the National Academy of Design • offered a position as a professor of painting/sculpture at NYU • an idea caught Morse’s imagination • struggled with invention; never gave up • SUCCESS • purchase of Locust Grove • remembered as an inventor, not an artist.. Self Portrait Landscape Paintings Thomas Cole Portraits Inventions • Natural Talent Samuel Morse • Hudson River School of Art • European Styles Morse as a Renaissance Man Mastery of the “duality of science and art” Inner genius of the painter/inventor Further Comparisons 1808. -

Fax, Modem, and Text Support Over IP Configuration Guide, Cisco IOS Release 15M&T
Fax, Modem, and Text Support over IP Configuration Guide, Cisco IOS Release 15M&T Last Modified: 2015-07-31 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Fast Detection of Forgery Image Using Discrete Cosine Transform Four Step Search Algorithm
Journal of Korea Multimedia Society Vol. 22, No. 5, May 2019(pp. 527-534) https://doi.org/10.9717/kmms.2019.22.5.527 Fast Detection of Forgery Image using Discrete Cosine Transform Four Step Search Algorithm Yong-Dal Shin†, Yong-Suk Cho†† ABSTRACT Recently, Photo editing softwares such as digital cameras, Paintshop Pro, and Photoshop digital can create counterfeit images easily. Various techniques for detection of tamper images or forgery images have been proposed in the literature. A form of digital forgery is copy-move image forgery. Copy-move is one of the forgeries and is used wherever you need to cover a part of the image to add or remove information. Copy-move image forgery refers to copying a specific area of an image itself and pasting it into another area of the same image. The purpose of copy-move image forgery detection is to detect the same or very similar region image within the original image. In this paper, we proposed fast detection of forgery image using four step search based on discrete cosine transform and a four step search algorithm using discrete cosine transform (FSSDCT). The computational complexity of our algorithm reduced 34.23 % than conventional DCT three step search algorithm (DCTTSS). Key words: Duplicated Forgery Image, Discrete Cosine Transform, Four Step Search Algorithm 1. INTRODUCTION and Fig. 1(b) shows an original image and a copy- moved forged image respectively. Digital cameras and smart phones, and digital J. Fridrich [1] proposed an exacting match image processing software such as Photoshop, method for the forged image detection of a copy- Paintshop Pro, you can duplicate digital counterfeit move forged image. -

THE CABLE THAT WIRED the WORLD 41 the CABLE THAT WIRED the WORLD Today We Take Global Attractive Proposition to the Cotton Communications for Granted
INFORM NETWORK DEVELOP NIGEL LINGE, BILL BURNS THE CABLE THAT WIRED THE WORLD 41 THE CABLE THAT WIRED THE WORLD Today we take global attractive proposition to the cotton communications for granted. NIGEL LINGE, merchants and growers. However, it was an American, Cyrus Field (see Figure 1), who on Whether telephoning someone in BILL BURNS 6 November 1856 established the Atlantic America, sending emails to Telegraph Company and sought to raise Australia or simply browsing the Xxxx xxxx xxxx £350,000 to manufacture and lay a web, we accept that our global telegraph cable between Britain and North America. To appreciate the scale of what telecommunications networks was being proposed, 1,600 nautical miles of will make it all happen. cable would be required to cross the Atlantic Nevertheless, life hasn’t always at its shortest width between the west coast been this convenient and this of Ireland and the east coast of Newfoundland, Canada. The longest year we are celebrating the 150th successful undersea cable that had been anniversary of a significant event constructed up until that time was a mere that proved to be the catalyst for 300 miles in length under the Black Sea, linking the Crimea to Varna on the Bulgarian a telecommunications revolution coast. that laid the foundations of the global connectivity that we all Nevertheless, the Victorian can-do attitude enjoy today – the first fully- prevailed and on 31 July 1857, HMS Agamemnon and USA Niagara set sail from operational telecommunications Figure 1: Cyrus Field (1819-1892), Pioneer of the Valentia in Ireland and headed west towards cable to be laid under the Trans-Atlantic Telegraph Trinity Bay in Newfoundland. -

The Use of Social Media in Risk and Crisis Communication”
OECD Working Papers on Public Governance No. 24 The Use of Social Media Cécile Wendling, in Risk and Crisis Jack Radisch, Communication Stephane Jacobzone https://dx.doi.org/10.1787/5k3v01fskp9s-en WORKING PAPER “THE USE OF SOCIAL MEDIA IN RISK AND CRISIS COMMUNICATION” CÉCILE WENDLING, JACK RADISCH, STEPHANE JACOBZONE ABSTRACT This report highlights the changing landscape of risk and crisis communications and in particular how social media can be a beneficial tool, but also create challenges for crisis managers. It explores different practices of risk and crisis communications experts related to the use of social media and proposes a framework for monitoring the development of practices among countries in the use of social media for risk and crisis communications. The three step process spans passive to dynamic use of social media, and provides governments a self-assessment tool to monitor and track progress in the uptake of effective use of social media by emergency services or crisis managers. 2 NOTE BY THE SECRETARIAT This report addresses risk and crisis communications, a core policy area for the High Level Risk Forum. It draws on the outcome of the discussions held at a workshop organized jointly by the OECD and the International Risk Governance Council (IRGC), in Geneva (Switzerland), on 29 June 2012 on the theme of ''Risk and crisis communication: the challenges of social media''. This workshop gathered participants from 12 OECD countries, think tanks, academia, the private sector and international organizations to discuss the challenges that emergency services and public relations managers confront in relation to the emergence of social media. -

The Stage Is Set
The Stage Is Set: Developments before 1900 Leading to Practical Wireless Communication Darrel T. Emerson National Radio Astronomy Observatory1, 949 N. Cherry Avenue, Tucson, AZ 85721 In 1909, Guglielmo Marconi and Carl Ferdinand Braun were awarded the Nobel Prize in Physics "in recognition of their contributions to the development of wireless telegraphy." In the Nobel Prize Presentation Speech by the President of the Royal Swedish Academy of Sciences [1], tribute was first paid to the earlier theorists and experimentalists. “It was Faraday with his unique penetrating power of mind, who first suspected a close connection between the phenomena of light and electricity, and it was Maxwell who transformed his bold concepts and thoughts into mathematical language, and finally, it was Hertz who through his classical experiments showed that the new ideas as to the nature of electricity and light had a real basis in fact.” These and many other scientists set the stage for the rapid development of wireless communication starting in the last decade of the 19th century. I. INTRODUCTION A key factor in the development of wireless communication, as opposed to pure research into the science of electromagnetic waves and phenomena, was simply the motivation to make it work. More than anyone else, Marconi was to provide that. However, for the possibility of wireless communication to be treated as a serious possibility in the first place and for it to be able to develop, there had to be an adequate theoretical and technological background. Electromagnetic theory, itself based on earlier experiment and theory, had to be sufficiently developed that 1. -

Effective Communication”
Team – 184 San Academy, Pallikaranai PROBLEM CHOSEN “EFFECTIVE COMMUNICATION” STUDENTS NAMES Rakshan K.K Sam Rozario D Sachin U.S Saifudeen S SAN ACADEMY, PALLIKARANAI TEAM - 184 PREPARING PPT As a presenting tool our students used PPT to show the evolution of communication from cave age to modern age .Here are some glimpse of the PPT slide. THE SMOKE SIGNAL It is one of the oldest forms of long-distance communication It is a form of visual communications used over long distances In Ancient China, soldiers stationed along the Great Wall would alert each other of impending enemy attack by signaling from tower to tower In this way they were able to transmit a message as far away as 750 Km( 470 mi ) in just a few hours ELECTRICAL TELEGRAPH It is a telegraph that uses electrical signals, usually conveyed via telecommunications lines or radio. The electromagnetic telegraph is a device for human to human transmission of coded text messages It is the first form of electrical telecommunication Later this networks permitted people and commerce to almost instantly transmit messages across both continents and oceans PIGEON POST It is the use of homing pigeons to carry messages Pigeons were effective as messengers due to their natural homing abilities The pigeons were transported to a destination in cages, where they would be attached with messages , then naturally the pigeon would fly back to its home where the owner reads the mail Pigeons have been used to great effect in military situations SALE AND MARKETING SAN ACADEMY, PALLIKARANAI TEAM - 184 To develop a clarity and focus on what need to be done, students made a plan to promote some textbook. -

Battle Management Language: History, Employment and NATO Technical Activities
Battle Management Language: History, Employment and NATO Technical Activities Mr. Kevin Galvin Quintec Mountbatten House, Basing View, Basingstoke Hampshire, RG21 4HJ UNITED KINGDOM [email protected] ABSTRACT This paper is one of a coordinated set prepared for a NATO Modelling and Simulation Group Lecture Series in Command and Control – Simulation Interoperability (C2SIM). This paper provides an introduction to the concept and historical use and employment of Battle Management Language as they have developed, and the technical activities that were started to achieve interoperability between digitised command and control and simulation systems. 1.0 INTRODUCTION This paper provides a background to the historical employment and implementation of Battle Management Languages (BML) and the challenges that face the military forces today as they deploy digitised C2 systems and have increasingly used simulation tools to both stimulate the training of commanders and their staffs at all echelons of command. The specific areas covered within this section include the following: • The current problem space. • Historical background to the development and employment of Battle Management Languages (BML) as technology evolved to communicate within military organisations. • The challenges that NATO and nations face in C2SIM interoperation. • Strategy and Policy Statements on interoperability between C2 and simulation systems. • NATO technical activities that have been instigated to examine C2Sim interoperation. 2.0 CURRENT PROBLEM SPACE “Linking sensors, decision makers and weapon systems so that information can be translated into synchronised and overwhelming military effect at optimum tempo” (Lt Gen Sir Robert Fulton, Deputy Chief of Defence Staff, 29th May 2002) Although General Fulton made that statement in 2002 at a time when the concept of network enabled operations was being formulated by the UK and within other nations, the requirement remains extant. -

Alexander Graham Bell 1847-1922
NATIONAL ACADEMY OF SCIENCES OF THE UNITED STATES OF AMERICA BIOGRAPHICAL MEMOIRS VOLUME XXIII FIRST MEMOIR BIOGRAPHICAL MEMOIR OF ALEXANDER GRAHAM BELL 1847-1922 BY HAROLD S. OSBORNE PRESENTED TO THE ACADEMY AT THE ANNUAL MEETING, 1943 It was the intention that this Biographical Memoir would be written jointly by the present author and the late Dr. Bancroft Gherardi. The scope of the memoir and plan of work were laid out in cooperation with him, but Dr. Gherardi's untimely death prevented the proposed collaboration in writing the text. The author expresses his appreciation also of the help of members of the Bell family, particularly Dr. Gilbert Grosvenor, and of Mr. R. T. Barrett and Mr. A. M. Dowling of the American Telephone & Telegraph Company staff. The courtesy of these gentlemen has included, in addition to other help, making available to the author historic documents relating to the life of Alexander Graham Bell in the files of the National Geographic Society and in the Historical Museum of the American Telephone and Telegraph Company. ALEXANDER GRAHAM BELL 1847-1922 BY HAROLD S. OSBORNE Alexander Graham Bell—teacher, scientist, inventor, gentle- man—was one whose life was devoted to the benefit of mankind with unusual success. Known throughout the world as the inventor of the telephone, he made also other inventions and scientific discoveries of first importance, greatly advanced the methods and practices for teaching the deaf and came to be admired and loved throughout the world for his accuracy of thought and expression, his rigid code of honor, punctilious courtesy, and unfailing generosity in helping others.