Towards Least Privilege Principle: Limiting Unintended Accesses in Software Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Integrity Checking of Operating Systems with Respect to Kernel Level Malware”
To Bianca, for being who you are. Abstract Kernel-mode rootkits have gained a considerable momentum within the blackhat com- munity. They represent a considerable threat to any computer system, as they pro- vide an intruder with the ability to hide the presence of his malicious activity. These rootkits make changes to the operating system’s kernel, thereby providing particularly stealthy hiding techniques. Considering the kernel rootkit threat and other threats, the collection of reliable information from a compromised system becomes a central problem within the domain of computer security. This thesis addresses this problem. It looks at the possibility of using virtualization as a means to facilitate kernel-mode rootkit detection through integrity checking. The thesis describes several areas within the Linux kernel, which are commonly subverted by kernel-mode rootkits. It introduces the reader to the concept of virtual- ization and describes several technologies employing virtualization. The kernel-mode rootkit threat is then addressed through a description of their hiding methodologies. Some of the existing methods for malware detection are also addressed and analysed. A number of general requirements, which need to be satisfied by a general model enabling kernel-mode rootkit detection, are identified. A model addressing these requirements is suggested, and a framework implementing the model is set-up. The detection capabilities of the framework are tested on a couple of rootkits. iii Preface This report presents the results of my master thesis “Integrity checking of operating systems with respect to kernel level malware”. It is written as part of the Master de- gree (Sivilingeniør) in Computer Science at the Norwegian University of Science and Technology (NTNU), during Spring 2005. -

Security in Ordinary Operating Systems
39 C H A P T E R 4 Security in Ordinary Operating Systems In considering the requirements of a secure operating system,it is worth considering how far ordinary operating systems are from achieving these requirements. In this chapter, we examine the UNIX and Windows operating systems and show why they are fundamentally not secure operating systems. We first examine the history these systems, briefly describe their protection systems, then we show, using the requirements of a secure operating system defined in Chapter 2, why ordinary operating systems are inherently insecure. Finally, we examine common vulnerabilities in these systems to show the need for secure operating systems and the types of threats that they will have to overcome. 4.1 SYSTEM HISTORIES 4.1.1 UNIX HISTORY UNIX is a multiuser operating system developed by Dennis Ritchie and Ken Thompson at AT&T Bell Labs [266]. UNIX started as a small project to build an operating system to play a game on an available PDP-7 computer. However, UNIX grew over the next 10 to 15 years into a system with considerable mindshare, such that a variety of commercial UNIX efforts were launched. The lack of coherence in these efforts may have limited the market penetration of UNIX, but many vendors, even Microsoft, had their own versions. UNIX remains a significant operating system today, embodied in many systems, such as Linux, Sun Solaris, IBM AIX, the various BSD systems, etc. Recall from Chapter 3 that Bell Labs was a member of the Multics consortium. However, Bell Labs dropped out of the Multics project in 1969, primarily due to delays in the project. -

A Brief Study and Comparison Of, Open Source Intrusion Detection System Tools
International Journal of Advanced Computational Engineering and Networking, ISSN: 2320-2106, Volume-1, Issue-10, Dec-2013 A BRIEF STUDY AND COMPARISON OF, OPEN SOURCE INTRUSION DETECTION SYSTEM TOOLS 1SURYA BHAGAVAN AMBATI, 2DEEPTI VIDYARTHI 1,2Defence Institute of Advanced Technology (DU) Pune –411025 Email: [email protected], [email protected] Abstract - As the world becomes more connected to the cyber world, attackers and hackers are becoming increasingly sophisticated to penetrate computer systems and networks. Intrusion Detection System (IDS) plays a vital role in defending a network against intrusion. Many commercial IDSs are available in marketplace but with high cost. At the same time open source IDSs are also available with continuous support and upgradation from large user community. Each of these IDSs adopts a different approaches thus may target different applications. This paper provides a quick review of six Open Source IDS tools so that one can choose the appropriate Open Source IDS tool as per their organization requirements. Keywords - Intrusion Detection, Open Source IDS, Network Securit, HIDS, NIDS. I. INTRODUCTION concentrate on the activities in a host without considering the activities in the computer networks. Every day, intruders are invading countless homes On the other hand, NIDS put its focus on computer and organisations across the country via virus, networks without examining the hosts’ activities. worms, Trojans, DoS/DDoS attacks by inserting bits Intrusion Detection methodologies can be classified of malicious code. Intrusion detection system tools as Signature based detection, Anomaly based helps in protecting computer and network from a detection and Stateful Protocol analysis based numerous threats and attacks. -

Ten Strategies of a World-Class Cybersecurity Operations Center Conveys MITRE’S Expertise on Accumulated Expertise on Enterprise-Grade Computer Network Defense
Bleed rule--remove from file Bleed rule--remove from file MITRE’s accumulated Ten Strategies of a World-Class Cybersecurity Operations Center conveys MITRE’s expertise on accumulated expertise on enterprise-grade computer network defense. It covers ten key qualities enterprise- grade of leading Cybersecurity Operations Centers (CSOCs), ranging from their structure and organization, computer MITRE network to processes that best enable effective and efficient operations, to approaches that extract maximum defense Ten Strategies of a World-Class value from CSOC technology investments. This book offers perspective and context for key decision Cybersecurity Operations Center points in structuring a CSOC and shows how to: • Find the right size and structure for the CSOC team Cybersecurity Operations Center a World-Class of Strategies Ten The MITRE Corporation is • Achieve effective placement within a larger organization that a not-for-profit organization enables CSOC operations that operates federally funded • Attract, retain, and grow the right staff and skills research and development • Prepare the CSOC team, technologies, and processes for agile, centers (FFRDCs). FFRDCs threat-based response are unique organizations that • Architect for large-scale data collection and analysis with a assist the U.S. government with limited budget scientific research and analysis, • Prioritize sensor placement and data feed choices across development and acquisition, enteprise systems, enclaves, networks, and perimeters and systems engineering and integration. We’re proud to have If you manage, work in, or are standing up a CSOC, this book is for you. served the public interest for It is also available on MITRE’s website, www.mitre.org. more than 50 years. -

User-Driven Access Control: Rethinking Permission Granting in Modern Operating Systems
This paper appears at the 33rd IEEE Symposium on Security and Privacy (Oakland 2012). User-Driven Access Control: Rethinking Permission Granting in Modern Operating Systems Franziska Roesner, Tadayoshi Kohno Alexander Moshchuk, Bryan Parno, Helen J. Wang Crispin Cowan ffranzi, [email protected] falexmos, parno, [email protected] [email protected] University of Washington Microsoft Research Microsoft Abstract— Modern client platforms, such as iOS, Android, Thus, a pressing open problem is how to allow users to Windows Phone, Windows 8, and web browsers, run each ap- grant applications access to user-owned resources: privacy- plication in an isolated environment with limited privileges. A and cost-sensitive devices and sensors (e.g., the camera, GPS, pressing open problem in such systems is how to allow users to grant applications access to user-owned resources, e.g., to or SMS), system services and settings (e.g., the contact list privacy- and cost-sensitive devices like the camera or to user or clipboard), and user content stored with various applica- data residing in other applications. A key challenge is to en- tions (e.g., photos or documents). To address this problem, able such access in a way that is non-disruptive to users while we advocate user-driven access control, whereby the system still maintaining least-privilege restrictions on applications. captures user intent via authentic user actions in the context In this paper, we take the approach of user-driven access con- trol, whereby permission granting is built into existing user ac- of applications. Prior work [22, 32, 33] applied this principle tions in the context of an application, rather than added as an largely in the context of least-privilege file picking, where an afterthought via manifests or system prompts. -
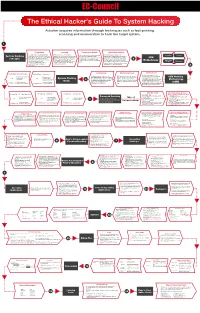
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Network Security Jim Binkley
Tools Network Security Jim Binkley. Jim Binkley 1 Outline basic tools netcat intrusion detection – network monitors – net-based audit/analysis (nessus) – net-based signature analysis (snort) (see ASCII lecture) – host-based anomaly analysis (tripwire) web audit/analysis wireless (kismet/netstumbler) attack tools (dsniff, ettercap) remote control/backdoor tools Jim Binkley 2 a few intro thoughts some of these tools can be grouped into different categories BUT then both tripwire and ourmon are intrusion detection tools (what do they have in common?) ID tools may have problems with false-positives attack tools can always be used for defensive purposes or offensive purposes: – nmap used to check for open ports ... any tool may be used for ill (even ping) Jim Binkley 3 information sources: Anti-Hacker Toolkit, Jones, Shema, Johnson. Osborne 2002 Snort FAQ (and book) nmap documentation Hacker’s Exposed in numerous editions Jim Binkley 4 basic tools ping and relatives traceroute tcpdump and other sniffers – ethereal whois and the whois database dig/nslookup and the DNS scanners problem: given email handout, what can you learn about its origin? Jim Binkley 5 ping ping may be used to test basic 2-way connectivity or determine if an ip address space is populated – to stuff an ARP database (HPOV does this) » so that we can see how many hosts we have – to enable a port query because J. Hacker has an exploit Jim Binkley 6 ping may have these options -c <count> - send count pings -n <count> - windows, the same thing -f - -

Proceedings of the 12Th USENIX Security Symposium
USENIX Association Proceedings of the 12th USENIX Security Symposium Washington, D.C., USA August 4–8, 2003 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION © 2003 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. Preventing Privilege Escalation Niels Provos Markus Friedl Peter Honeyman CITI, University of Michigan GeNUA CITI, University of Michigan Abstract gain extra privilege after successful authentication lim- its the degree of escalation because the user is already Many operating system services require special priv- authorized to hold some privilege. On the other hand, ilege to execute their tasks. A programming error in a a remote adversary gaining superuser privilege with no privileged service opens the door to system compromise authentication presents a greater degree of escalation. in the form of unauthorized acquisition of privileges. In For services that are part of the critical Internet the worst case, a remote attacker may obtain superuser infrastructure is it particularly important to protect privileges. In this paper, we discuss the methodology against programming errors. Sometimes these services and design of privilege separation, a generic approach need to retain special privilege throughout their life- that lets parts of an application run with different levels time. For example, in SSH, the SSH daemon needs to of privilege. -
Implementing Least Privilege in Windows 2000, Part I: Stand-Alone W2k
84-02-04 DATA SECURITY MANAGEMENT IMPLEMENTING LEAST PRIVILEGE IN WINDOWS 2000, PART I: STAND-ALONE W2K Roberta Bragg, CISSP INSIDE Groups; Default Groups; Implicit Groups; User Rights; Default Object Access — Object Permissions; Group Scope; Practical Implications; Best Practices The key to understanding how to apply least privilege lies in understand- ing four W2K concepts: 1. groups 2. user rights 3. object permissions 4. group scope The meaning of these concepts is often obscured by a discussion of W2K domains and Active Directory issues. To start with the basics, the discussion is divided into two parts. This article deals primarily with the PAYOFF IDEA implementation of least privilege on One of the most critical tenets of information sys- W2K systems that are not joined in a tem security is the principle of least privilege, that W2K domain. Another article, Part II, is, the application of a policy that provides each user of the system with the most restrictive set of will enlarge the discussion to include access and privileges that will still allow the user W2K systems that have been joined to get his or her job done. One can implement this in a W2K domain. Included in that principle in Windows 2000 as it protects access discussion will be additional features to system operation and to object access by re- of Active Directory (delegation of quiring authenticated system access, assign- ment of privileges, and granular assignment of authority, object permissions) that object permissions. The key to understanding can be used to further enhance the how to apply this principle lies in understanding process. -

Beginner's Guide to Open Source Intrusion Detection Tools
BEGINNER’S GUIDE to Open Source Intrusion Detection Tools www.alienvault.com Introduction to Open Source Intrusion Detection Threat and intrusion detection have become a top priority in cybersecurity, making it more important than ever before. If you aren’t already running an intrusion detection system (IDS) in your network, you should start now. Is Open Source Security a Good Route? There are a wealth of great tools out there that can dramatically improve the security of your network. Open source security goes back decades, and there is a large, active community behind many of the tools. In fact, some of these tools are used by commercial security vendors in their products, and these vendors contribute to the tools to keep them current. Before getting started, we’d be remiss not to address the pros and cons of going the open source route. Open source might be a good solution for you if: • Your company has the expertise in both security and system administration needed to deploy several tools with only community support. • You want “complete control” over your security architecture and are willing to do extra work to make that happen. • You develop a plan for keeping these tools up-to-date. Unlike most software, failure to keep security tools current with the latest versions and security updates (which may come weekly, daily, or even hourly) renders the tools themselves almost useless after a short time. • You have a very low budget to buy products, but have the staff needed to maintain open source tools. • Your use-case and security concerns don’t align well with commercial products. -

Open Source Intrusion Detection Tools
Beginner’s guide: Open source intrusion detection tools 1 Threat and intrusion Is open source detection have security a become a top priority in cybersecurity, good route? making it more important than ever before. If you aren’t already running an intrusion detection system (IDS) in your network, you should start now. This document is intended to include general information for beginners learning about open source intrusion detection. Use of names of 2 third party companies in the document are for informational purposes only and do not constitute any endorsement by AT&T Cybersecurity. Introduction There are a wealth of great tools out there that can dramatically improve the security of your network. Open source security goes back decades, and there is a large, active community behind many of the tools. In fact, some of these tools are used by commercial security vendors in their products, and these vendors contribute to the tools to keep them current. Before getting started, we’d be remiss not to address the pros and cons of going the open source route. Open source might be a good solution for you if: Open source is easier than ever to install and maintain. • Your company has the expertise in both security and system However, on the “con” side, there are a few important administration needed to deploy several tools with only concerns. If you are going to design a security solution for community support. your company, please keep in mind: • You will have to do your own support. There are great • You want “complete control” over your security architecture communities behind some of these tools, but you are the only and are willing to do extra work to make that happen. -

Configuration Recommendations of a Gnu/Linux System
.. CONFIGURATION RECOMMENDATIONS OF A GNU/LINUX SYSTEM ANSSI GUIDELINES ANSSI-BP-028-EN 22/02/2019 TARGETED AUDIENCE: Developers Administrators IT security managers IT managers Users . .. Information Warning This document, written by ANSSI, the French National Information Security Agency, presents the “Configuration recommendations of a GNU/LINUX system”. It is freely avail- able at www.ssi.gouv.fr/en/. It is an original creation from ANSSI and it is placed under the “Open Licence v2.0” published by the Etalab mission [12]. According to the Open Licence v2.0, this guide can be freely reused, subject to mentionning its paternity (source and date of last update). Reuse means the right to communicate, distribute, redistribute, publish, transmit, reproduce, copy, adapt, modify, extract, transform and use, including for commercial purposes These recommendations are provided as is and are related to threats known at the publi- cation time. Considering the information systems diversity, ANSSI cannot guarantee direct application of these recommendations on targeted information systems. Applying the fol- lowing recommendations shall be, at first, validated by IT administrators and/or IT security managers. This document is a courtesy translation of the initial French document “Recommandations de configuration d’un système GNU/Linux”, available at www.ssi.gouv.fr. In case of con- .flicts between these two documents, the latter is considered as the only reference. Document changelog: VERSION DATE CHANGELOG 1.2 22/02/2019 English version based on a courtesy translation provided by Red Hat CONFIGURATION RECOMMENDATIONS OF A GNU/LINUX SYSTEM – 1 . Contents 1 Glossary 4 2 Preamble 5 2.1 Foreword ..........................................