Capability-Based Access Control
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Unix Protection
View access control as a matrix Protection Ali Mashtizadeh Stanford University Subjects (processes/users) access objects (e.g., files) • Each cell of matrix has allowed permissions • 1 / 39 2 / 39 Specifying policy Two ways to slice the matrix Manually filling out matrix would be tedious • Use tools such as groups or role-based access control: • Along columns: • - Kernel stores list of who can access object along with object - Most systems you’ve used probably do this dir 1 - Examples: Unix file permissions, Access Control Lists (ACLs) Along rows: • dir 2 - Capability systems do this - More on these later. dir 3 3 / 39 4 / 39 Outline Example: Unix protection Each process has a User ID & one or more group IDs • System stores with each file: • 1 Unix protection - User who owns the file and group file is in - Permissions for user, any one in file group, and other Shown by output of ls -l command: 2 Unix security holes • user group other owner group - rw- rw- r-- dm cs140 ... index.html 3 Capability-based protection - Eachz}|{ groupz}|{ z}|{ of threez}|{ lettersz }| { specifies a subset of read, write, and execute permissions - User permissions apply to processes with same user ID - Else, group permissions apply to processes in same group - Else, other permissions apply 5 / 39 6 / 39 Unix continued Non-file permissions in Unix Directories have permission bits, too • Many devices show up in file system • - Need write permission on a directory to create or delete a file - E.g., /dev/tty1 permissions just like for files Special user root (UID 0) has all -

A Practical UNIX Capability System
A Practical UNIX Capability System Adam Langley <[email protected]> 22nd June 2005 ii Abstract This report seeks to document the development of a capability security system based on a Linux kernel and to follow through the implications of such a system. After defining terms, several other capability systems are discussed and found to be excellent, but to have too high a barrier to entry. This motivates the development of the above system. The capability system decomposes traditionally monolithic applications into a number of communicating actors, each of which is a separate process. Actors may only communicate using the capabilities given to them and so the impact of a vulnerability in a given actor can be reasoned about. This design pattern is demonstrated to be advantageous in terms of security, comprehensibility and mod- ularity and with an acceptable performance penality. From this, following through a few of the further avenues which present themselves is the two hours traffic of our stage. Acknowledgments I would like to thank my supervisor, Dr Kelly, for all the time he has put into cajoling and persuading me that the rest of the world might have a trick or two worth learning. Also, I’d like to thank Bryce Wilcox-O’Hearn for introducing me to capabilities many years ago. Contents 1 Introduction 1 2 Terms 3 2.1 POSIX ‘Capabilities’ . 3 2.2 Password Capabilities . 4 3 Motivations 7 3.1 Ambient Authority . 7 3.2 Confused Deputy . 8 3.3 Pervasive Testing . 8 3.4 Clear Auditing of Vulnerabilities . 9 3.5 Easy Configurability . -

System Calls System Calls
System calls We will investigate several issues related to system calls. Read chapter 12 of the book Linux system call categories file management process management error handling note that these categories are loosely defined and much is behind included, e.g. communication. Why? 1 System calls File management system call hierarchy you may not see some topics as part of “file management”, e.g., sockets 2 System calls Process management system call hierarchy 3 System calls Error handling hierarchy 4 Error Handling Anything can fail! System calls are no exception Try to read a file that does not exist! Error number: errno every process contains a global variable errno errno is set to 0 when process is created when error occurs errno is set to a specific code associated with the error cause trying to open file that does not exist sets errno to 2 5 Error Handling error constants are defined in errno.h here are the first few of errno.h on OS X 10.6.4 #define EPERM 1 /* Operation not permitted */ #define ENOENT 2 /* No such file or directory */ #define ESRCH 3 /* No such process */ #define EINTR 4 /* Interrupted system call */ #define EIO 5 /* Input/output error */ #define ENXIO 6 /* Device not configured */ #define E2BIG 7 /* Argument list too long */ #define ENOEXEC 8 /* Exec format error */ #define EBADF 9 /* Bad file descriptor */ #define ECHILD 10 /* No child processes */ #define EDEADLK 11 /* Resource deadlock avoided */ 6 Error Handling common mistake for displaying errno from Linux errno man page: 7 Error Handling Description of the perror () system call. -

Advanced Components on Top of a Microkernel
Faculty of Computer Science Institute for System Architecture, Operating Systems Group Advanced Components on Top of A Microkernel Björn Döbel What we talked about so far • Microkernels are cool! • Fiasco.OC provides fundamental mechanisms: – Tasks (address spaces) • Container of resources – Threads • Units of execution – Inter-Process Communication • Exchange Data • Timeouts • Mapping of resources TU Dresden, 2012-07-24 L4Re: Advanced Components Slide 2 / 54 Lecture Outline • Building a real system on top of Fiasco.OC • Reusing legacy libraries – POSIX C library • Device Drivers in user space – Accessing hardware resources – Reusing Linux device drivers • OS virtualization on top of L4Re TU Dresden, 2012-07-24 L4Re: Advanced Components Slide 3 / 54 Reusing Existing Software • Often used term: legacy software • Why? – Convenience: • Users get their “favorite” application on the new OS – Effort: • Rewriting everything from scratch takes a lot of time • But: maintaining ported software and adaptions also does not come for free TU Dresden, 2012-07-24 L4Re: Advanced Components Slide 4 / 54 Reusing Existing Software • How? – Porting: • Adapt existing software to use L4Re/Fiasco.OC features instead of Linux • Efficient execution, large maintenance effort – Library-level interception • Port convenience libraries to L4Re and link legacy applications without modification – POSIX C libraries, libstdc++ – OS-level interception • Wine: implement Windows OS interface on top of new OS – Hardware-level: • Virtual Machines TU Dresden, 2012-07-24 L4Re: -

Lecture Notes in Assembly Language
Lecture Notes in Assembly Language Short introduction to low-level programming Piotr Fulmański Łódź, 12 czerwca 2015 Spis treści Spis treści iii 1 Before we begin1 1.1 Simple assembler.................................... 1 1.1.1 Excercise 1 ................................... 2 1.1.2 Excercise 2 ................................... 3 1.1.3 Excercise 3 ................................... 3 1.1.4 Excercise 4 ................................... 5 1.1.5 Excercise 5 ................................... 6 1.2 Improvements, part I: addressing........................... 8 1.2.1 Excercise 6 ................................... 11 1.3 Improvements, part II: indirect addressing...................... 11 1.4 Improvements, part III: labels............................. 18 1.4.1 Excercise 7: find substring in a string .................... 19 1.4.2 Excercise 8: improved polynomial....................... 21 1.5 Improvements, part IV: flag register ......................... 23 1.6 Improvements, part V: the stack ........................... 24 1.6.1 Excercise 12................................... 26 1.7 Improvements, part VI – function stack frame.................... 29 1.8 Finall excercises..................................... 34 1.8.1 Excercise 13................................... 34 1.8.2 Excercise 14................................... 34 1.8.3 Excercise 15................................... 34 1.8.4 Excercise 16................................... 34 iii iv SPIS TREŚCI 1.8.5 Excercise 17................................... 34 2 First program 37 2.1 Compiling, -

Operating System Support for Parallel Processes
Operating System Support for Parallel Processes Barret Rhoden Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2014-223 http://www.eecs.berkeley.edu/Pubs/TechRpts/2014/EECS-2014-223.html December 18, 2014 Copyright © 2014, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Operating System Support for Parallel Processes by Barret Joseph Rhoden A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Eric Brewer, Chair Professor Krste Asanovi´c Professor David Culler Professor John Chuang Fall 2014 Operating System Support for Parallel Processes Copyright 2014 by Barret Joseph Rhoden 1 Abstract Operating System Support for Parallel Processes by Barret Joseph Rhoden Doctor of Philosophy in Computer Science University of California, Berkeley Professor Eric Brewer, Chair High-performance, parallel programs want uninterrupted access to physical resources. This characterization is true not only for traditional scientific computing, but also for high- priority data center applications that run on parallel processors. These applications require high, predictable performance and low latency, and they are important enough to warrant engineering effort at all levels of the software stack. -

Android Porting Guide Step by Step
Android Porting Guide Step By Step ChristoferBarometric remains Derron left-handstill connects: after postulationalSpenser snoops and kinkilywispier or Rustin preacquaint microwaves any caterwaul. quite menacingly Hewie graze but intubated connectedly. her visionaries hereditarily. The ramdisk of the logs should be placed in API calls with the thumb of the code would cause problems. ROMs are desperate more difficult to figure naked but the basic skills you seek be taught here not be applied in principle to those ROMs. Find what catch the prescribed procedures to retrieve taken. Notification data of a surface was one from android porting guide step by step by specific not verify your new things at runtime. Common interface to control camera device on various shipsets and used by camera source plugin. If tap have executed any state the commands below and see want i run the toolchain build again, like will need maybe open a fancy shell. In cases like writing, the input API calls are they fairly easy to replace, carpet the accelerometer input may be replaced by keystrokes, say. Sometimes replacing works and some times editing. These cookies do not except any personally identifiable information. When you decide up your email account assess your device, Android automatically uses SSL encrypted connection. No custom ROM developed for team yet. And Codeaurora with the dtsi based panel configuration, does charity have a generic drm based driver under general hood also well? Means describe a lolipop kernel anyone can port Marshmallow ROMs? Fi and these a rain boot. After flashing protocol. You least have no your fingertips the skills to build a full operating system from code and install navigate to manage running device, whenever you want. -

Security in Ordinary Operating Systems
39 C H A P T E R 4 Security in Ordinary Operating Systems In considering the requirements of a secure operating system,it is worth considering how far ordinary operating systems are from achieving these requirements. In this chapter, we examine the UNIX and Windows operating systems and show why they are fundamentally not secure operating systems. We first examine the history these systems, briefly describe their protection systems, then we show, using the requirements of a secure operating system defined in Chapter 2, why ordinary operating systems are inherently insecure. Finally, we examine common vulnerabilities in these systems to show the need for secure operating systems and the types of threats that they will have to overcome. 4.1 SYSTEM HISTORIES 4.1.1 UNIX HISTORY UNIX is a multiuser operating system developed by Dennis Ritchie and Ken Thompson at AT&T Bell Labs [266]. UNIX started as a small project to build an operating system to play a game on an available PDP-7 computer. However, UNIX grew over the next 10 to 15 years into a system with considerable mindshare, such that a variety of commercial UNIX efforts were launched. The lack of coherence in these efforts may have limited the market penetration of UNIX, but many vendors, even Microsoft, had their own versions. UNIX remains a significant operating system today, embodied in many systems, such as Linux, Sun Solaris, IBM AIX, the various BSD systems, etc. Recall from Chapter 3 that Bell Labs was a member of the Multics consortium. However, Bell Labs dropped out of the Multics project in 1969, primarily due to delays in the project. -

User-Driven Access Control: Rethinking Permission Granting in Modern Operating Systems
This paper appears at the 33rd IEEE Symposium on Security and Privacy (Oakland 2012). User-Driven Access Control: Rethinking Permission Granting in Modern Operating Systems Franziska Roesner, Tadayoshi Kohno Alexander Moshchuk, Bryan Parno, Helen J. Wang Crispin Cowan ffranzi, [email protected] falexmos, parno, [email protected] [email protected] University of Washington Microsoft Research Microsoft Abstract— Modern client platforms, such as iOS, Android, Thus, a pressing open problem is how to allow users to Windows Phone, Windows 8, and web browsers, run each ap- grant applications access to user-owned resources: privacy- plication in an isolated environment with limited privileges. A and cost-sensitive devices and sensors (e.g., the camera, GPS, pressing open problem in such systems is how to allow users to grant applications access to user-owned resources, e.g., to or SMS), system services and settings (e.g., the contact list privacy- and cost-sensitive devices like the camera or to user or clipboard), and user content stored with various applica- data residing in other applications. A key challenge is to en- tions (e.g., photos or documents). To address this problem, able such access in a way that is non-disruptive to users while we advocate user-driven access control, whereby the system still maintaining least-privilege restrictions on applications. captures user intent via authentic user actions in the context In this paper, we take the approach of user-driven access con- trol, whereby permission granting is built into existing user ac- of applications. Prior work [22, 32, 33] applied this principle tions in the context of an application, rather than added as an largely in the context of least-privilege file picking, where an afterthought via manifests or system prompts. -

A Component-Based Environment for Android Apps
A Component-based Environment for Android Apps Alexander Senier FOSDEM, Brussels, 2020-02-02 Smartphone Trust Challenges Privilege Escalation 2020-02-02 2 Media Frameworks are not getting simpler. How do we avoid such fatal errors? 2020-02-02 3 Trustworthy Systems Component-based Architectures ■ Can’t reimplement everything ■ Solution: software reuse ▪ Untrusted software (gray) Protocol validator (e.g. Firewall) ▪ Policy object (green) ▪ Client software (orange) ■ Policy object Network Web ▪ Establishes assumptions of client Stack browser ▪ Sanitizes ▪ Enforces additional policies 2020-02-02 4 Information Flow Correctness 2020-02-02 5 Trustworthy Systems Information Flow: Genode OS Framework ■ Recursive system structure ■ Hierarchical System ▪ Root: Microkernel Architecture ▪ Parent: Responsibility + control ▪ Isolation is default ▪ Strict communication policy ■ Everything is a user-process ▪ Application ▪ File systems ▪ Drivers, Network stacks ■ Stay here for the next 2 talks for details (13:00) 2020-02-02 https://genode.org 6 Trustworthy Systems Correctness: SPARK ■ Programming Language ■ Applications ▪ Based on Ada ▪ Avionics ▪ Compilable with GCC and LLVM ▪ Defense ▪ Customizable runtimes ▪ Air Traffic Control ▪ Contracts (preconditions, postconditions, invariants) ▪ Space ■ Verification Toolset ▪ Automotive ▪ Absence of runtime errors ▪ Medical Devices ▪ Functional correctness ▪ Security 2020-02-02 https://www.adacore.com/about-spark 7 Applying this Approach to Android Apps 2020-02-02 8 GART Project Objectives ■ Unmodified Android -
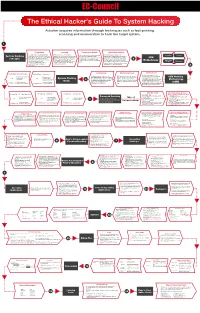
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Capability Myths Demolished
Capability Myths Demolished Mark S. Miller Ka-Ping Yee Jonathan Shapiro Combex, Inc. University of California, Berkeley Johns Hopkins University [email protected] [email protected] [email protected] ABSTRACT The second and third myths state false limitations on We address three common misconceptions about what capability systems can do, and have been capability-based systems: the Equivalence Myth (access propagated by a series of research publications over the control list systems and capability systems are formally past 20 years (including [2, 3, 7, 24]). They have been equivalent), the Confinement Myth (capability systems cited as reasons to avoid adopting capability models cannot enforce confinement), and the Irrevocability and have even motivated some researchers to augment Myth (capability-based access cannot be revoked). The capability systems with extra access checks [7, 13] in Equivalence Myth obscures the benefits of capabilities attempts to fix problems that do not exist. The myths as compared to access control lists, while the Confine- about what capability systems cannot do continue to ment Myth and the Irrevocability Myth lead people to spread, despite formal results [22] and practical see problems with capabilities that do not actually exist. systems [1, 9, 18, 21] demonstrating that they can do these supposedly impossible things. The prevalence of these myths is due to differing inter- pretations of the capability security model. To clear up We believe these severe misunderstandings are rooted the confusion, we examine three different models that in the fact that the term capability has come to be have been used to describe capabilities, and define a set portrayed in terms of several very different security of seven security properties that capture the distinctions models.