Personal Communications 3270 Emulator User's Reference
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mul-T-Lock 2016 Product Catalog Mul-T-Lock High Security & Access Control Solutions
Mul-T-Lock 2016 Product Catalog Mul-T-Lock High Security & Access Control Solutions Effective January 1, 2016 TABLE OF CONTENTS Introduction 1 Grade 1 Hercular® Deadbolts 65 How to Order 4 Hercular® Anti-Ligature & Latch Locks 66 Multiple Platforms – A Security Level for Every Need 6 Grade 2 Cronus® Deadbolts 67 MT5®+ Platform Introduction 7 Locksets & Hardware 68 Interactive®+ Platform Introduction 8 Rim Locks 69 Integrator® Platform Introduction 9 Mortise Locks 70 Access Control, Keyless Entry & Smart Solutions 10 Lever & Knob Locks 71 WatchLock™ 11 Utility, Furniture & Retail Locks 73 Traka® Key & Asset Management Solutions 14 Padlocks 76 ENTR™ Smart Lock Solution 16 ArmaD Locks 79 Yale® Key Safes & Boxes 18 Mul-T-Lock Junior 82 CLIQ® E-Cylinders & Smart Key Solutions 20 Mul-T-Lock Parts 84 SMARTair® Access Control Solutions 26 Cylinder Parts - Pins 86 SMARTair® E-Motion Electronic Cabinet & Locker Locks 32 Cylinder Parts 100 Yale® Shine™ Glass Digital Door Locks 36 Hercular® Deadbolt Parts 138 Code-It™ Electronic Pushbutton Levers 38 Anti-Ligature Deadbolt & Gate Latch Lock Parts 142 GotU®+ Digital Door Viewers 40 Top Guard® Parts 143 Mul-T-Lock Keys, Keying Options & Services 42 Utility & Furniture Lock Parts 144 Keys & Cards 43 Padlock Parts 160 Services 47 Key Cutting Machine Parts 170 Machinery, Pinkits & Tools 48 Standard Ordering Form 174 Locksmith Tools 49 Master Keying Information 175 Cylinders 51 Key & Cylinder Maintenance 178 Mortise Cylinders 52 Warranty 180 Mogul Cylinders 52 Conditions of Sale 182 Rim Cylinders 53 Available Finishes 187 Large Format Interchangeable Cores 53 Knob, Lever and Deadbolt Replacement Cylinders 54 Foreign Cylinders 62 Deadbolts & Deadlatches 64 Established in 1973, Mul-T-Lock is a worldwide leader in the developing, manufacturing, and marketing of high security products for Institutional, Commercial, Industrial, and Residential customers. -

Boot Mode Considerations: BIOS Vs UEFI
Boot Mode Considerations: BIOS vs. UEFI An overview of differences between UEFI Boot Mode and traditional BIOS Boot Mode Dell Engineering June 2018 Revisions Date Description October 2017 Initial release June 2018 Added DHCP Server PXE configuration details. The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2017 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA [1/15/2020] [Deployment and Configuration Guide] [Document ID] Dell believes the information in this document is accurate as of its publication date. The information is subject to change without notice. 2 : BIOS vs. UEFI | Doc ID 20444677 | June 2018 Table of contents Revisions............................................................................................................................................................................. 2 Executive Summary ............................................................................................................................................................ 4 1 Introduction .................................................................................................................................................................. -

The Backspace
spumante e rosato* (choose 2) per la tavola glera NV lunetta prosecco, veneto straw, baked apple, peach 11 43 farm greens :: giardiniera, red onion, pecorino romano lambrusco NV medici ermete, emilia romagna black currant, violet, graphite 10 39 lamb & pork meatballs :: stewed tomato, bread crumb, asiago, mint NV l’onesta, emilia romagna fresh strawberry, violet, orange zest 11 43 baked ricotta :: lemon, poached tomato, olive oil * lambrusco whipped lardo bruschetta :: herbs, citrus segment * aglianico 2015 feudi di san gregorio ‘ros‘aura’, irpinia, campania fresh strawberry, rose petal 12 47 shishito peppers :: melon, basil roasted corn :: ricotta, pesto bianco bombino bianco 2016 poderi dal nespoli “pagadebit”, romagna gooseberry, apple, hawthorn blossom 11 43 antipasti (choose 3) pinot grigio 2015 ronchi di pietro, friuli hazelnut, white peach, limestone 48 sweet potato :: cippolini onion, mushroom, rosemary friulano 2014 villa chiopris, friuli grave straw, white flowers, almond 10 39 braised greens :: golden raisins, pecan, red pepper falanghina 2014 terredora, campagna lemon, quince, pear 13 51 :: tomato, basil, balsamic house-made mozzarella chardonnay 2014 tenute del cabreo ‘la pietra’, chianti classico peach preserves, salted popcorn, vanilla 85 roasted beets :: celery, lemon zest, pepperoncini moscato 2015 oddera cascina di fiori, asti tangerine, peach, sage 12 47 the backspace marinated olives :: lemon, rosemary, oregano green beans :: pancetta, garlic, lemon family-style menu rosso $20 per guest pizze (choose 2) pergola rosso -

Operator's Guide for IBM 3270 Information Display Systems
GA27-2742-1 Operator's Guide for IBM 3270 Information Systems Display Systems i i Second Edition (July, 1972) This is a major revision of GA27-2742-0 and incorporates Technical Newsletter GN31-3001. Operating instructions for the printer and operator identification card reader have been added. Comments and corrections have been incorporated throughout the manual. Any system changes affecting this publication will be reported in subsequent revisions or Technical Newsletters. Additional copies of this manual can be obtained through IBM branch offices. Text for this publication has been prepared with the IBM SE LECTR IC ® Composer. A form is provided at the back of this publication for reader's comments. If the form has been removed, comments may be addressed to: IBM Systems Development Division, Product Publications, Dept. 520, Neighborhood Road, Kingston, N.V., 12401 © Copyright International Business Machines Corporation, 1971, 1972 Contents iii Table of Contents First Words to the Operator Qu ick Reference . 3 Operating the 3270* . 4 Introduction to Display Station Operation 5 Operator Controls 7,8 The Display Image 8 Indicators . 15-19 Keyboards 20 Typewriter Keyboard* ............... 24 I Data Entry Keyboard* ............... 44 I Operator Console Keyboard* . 62 I ·" Printer Operation * . 76 I,.~' , Operator Identification Card Reader . 88 I A Typical Job . · 90 Correcting Operator Errors . 90 Trouble with Your Machine · 92 Operator Trouble Report 92 Extras for the 3270* . .100 Selector Pen . · 101 Secu rity Key Lock .105 Audible Alarm . .106 Numeric Lock Feature .109 Understanding the 3270* .. 110 Data Processing · 111 Display Stations .. · 114 The IBM 3270 Information Display System · 115 ) Index · 119 *The complete table of contents for each section is on the first page of that section. -

Snagit 11.2 Hotkeys Guide
Snagit® Snagit Hotkeys Guide Release 11.2 March 2013 © 2013 TechSmith Corporation. All rights reserved. This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. The content of this manual is furnished for informational use only, is subject to change without notice and should not be construed as a commitment by TechSmith Corporation. TechSmith Corporation assumes no responsibility or liability for any errors or inaccuracies that may appear in this manual. Trademarks Camtasia, Camtasia Relay, Camtasia Studio, DubIt, EnSharpen, Enterprise Wide, Expressshow, Jing, Morae, Rich Recording Technology (RRT), Screencast.com, Show The World, SmartFocus, Snagit, TechSmith, TSCC and UserVue are either registered marks or marks of TechSmith Corporation in the U.S. and/or other countries. This list is not a comprehensive list of all TechSmith Corporation marks. The absence of a name/mark or logo in this notice does not constitute a waiver of any intellectual property rights that TechSmith Corporation has established in any of its product, feature or service names/marks or logos. All other marks are the property of their respective owners. Snagit on Windows Snagit 11.2 Hotkeys Guide Contents Customize Hotkeys ..............................................................................................................................................4 Hotkeys Reference ...............................................................................................................................................6 www.techsmith.com iii Snagit on Windows Snagit 11.2 Hotkeys Guide Customize Hotkeys Customize the key combinations for Snagit's capture hotkeys. Hotkeys allow you to: Maintain the cursor position on the screen during capture. Quickly access common commands without interacting with the Snagit interface. In Snagit, you can customize any of the following types of hotkeys. -

Function Keys One of the Biggest Differences Between a Typewriter
Function Keys One of the biggest differences between a typewriter keyboard and the computer keyboard is the row of keys at the top of the keyboard that are labeled F1 through F12. Commonly referred to as Function Keys, these keys were frequently used in the good old days of DOS programs. In today’s Windows world of computers, you can probably use your computer without ever using one of these keys. Yet, these function keys provide some interesting shortcuts for common computer functions that can be useful tools in everyday computing . The function keys are frequently used in combination with other keys such as the CTRL key, the ALT key, and the Shift key. This results in a plethora of possible keyboard shortcuts . Here is a brief rundown of the function key and what they can do for you. F1 As a throwback to DOS days, you will find that the F1 key will often bring up a help menu. If you press F1 while working in a program, help for that program will usually appear. If you press F1 while at the Windows desktop or when the Windows Explorer is open, a Windows help screen will pop up . If you happen to be working in a program and would like to see the Windows help screen, simply press the Windows key (the key with the Windows logo on the bottom row of keys) on your keyboard and press F1 at the same time. F2 You can use the F2 key to rename an item when working in Windows. Highlight any folder or file, and press F2. -

Introduction to Mainframe Networking TCP/IP Problem Determination
z/OS Basic Skills Information Center Networking on z/OS z/OS Basic Skills Information Center Networking on z/OS Note Before using this information and the product it supports, read the information in “Notices” on page 251. This edition applies to z/OS (product number 5694-A01). We appreciate your comments about this publication. Comment on specific errors or omissions, accuracy, organization, subject matter, or completeness of this book. The comments you send should pertain to only the information in this manual or product and the way in which the information is presented. For technical questions and information about products and prices, please contact your IBM branch office, your IBM business partner, or your authorized remarketer. When you send comments to IBM, you grant IBM a nonexclusive right to use or distribute your comments in any way it believes appropriate without incurring any obligation to you. IBM or any other organizations will only use the personal information that you supply to contact you about the issues that you state on this form. Send your comments through this web site: http://publib.boulder.ibm.com/infocenter/zoslnctr/v1r7/index.jsp?topic=/com.ibm.zcontact.doc/webqs.html © Copyright IBM Corporation 2006, 2010. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Before you begin the topic about Coupling channels ...........40 networking on z/OS .........vii Open Systems Adapter (OSA) .......40 HiperSockets ..............46 The I/O cage ..............48 Part 1. Introduction to networking on the mainframe...........1 Chapter 4. Sample network configuration ............49 Chapter 1. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

DEC Text Processing Utility Reference Manual
DEC Text Processing Utility Reference Manual Order Number: AA–PWCCD–TE April 2001 This manual describes the elements of the DEC Text Processing Utility (DECTPU). It is intended as a reference manual for experienced programmers. Revision/Update Information: This manual supersedes the DEC Text Processing Utility Reference Manual, Version 3.1 for OpenVMS Version 7.2. Software Version: DEC Text Processing Utility Version 3.1 for OpenVMS Alpha Version 7.3 and OpenVMS VAX Version 7.3 The content of this document has not changed since OpenVMS Version 7.1. Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation COMPAQ, VAX, VMS, and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS is a trademark of Compaq Information Technologies Group, L.P. Motif is a trademark of The Open Group. PostScript is a registered trademark of Adobe Systems Incorporated. All other product names mentioned herein may be the trademarks or registered trademarks of their respective companies. Confidential computer software. Valid license from Compaq or authorized sublicensor required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. The information in this document is provided "as is" without warranty of any kind and is subject to change without notice. The warranties for Compaq products are set forth in the express limited warranty statements accompanying such products. -
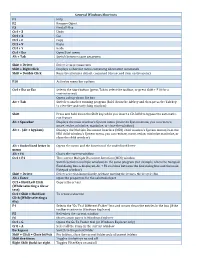
General Windows Shortcuts
General Windows Shortcuts F1 Help F2 Rename Object F3 Find all files Ctrl + Z Undo Ctrl + X Cut Ctrl + C Copy Ctrl + V Paste Ctrl + Y Redo Ctrl + Esc Open Start menu Alt + Tab Switch between open programs Alt + F4 Quit program Shift + Delete Delete item permanently Shift + Right Click Displays a shortcut menu containing alternative commands Shift + Double Click Runs the alternate default command ( the second item on the menu) Alt + Double Click Displays properties F10 Activates menu bar options Shift + F10 Opens a contex t menu ( same as righ t click) Ctrl + Esc or Esc Selects the Start button (press Tab to select the taskbar, or press Shift + F10 for a context menu) Alt + Down Arrow Opens a drop‐down list box Alt + Tab Switch to another running program (hold down the Alt key and then press the Tab key to view the task‐switching window) Alt + Shift + Tab Swit ch b ackward s b etween open appli cati ons Shift Press and hold down the Shift key while you insert a CD‐ROM to bypass the automatic‐ run feature Alt + Spacebar Displays the main window's System menu (from the System menu, you can restore, move, resize, minimize, maximize, or close the window) Alt + (Alt + hyphen) Displays the Multiple Document Interface (MDI) child window's System menu (from the MDI child window's System menu, you can restore, move, resize, minimize maximize, or close the child window) Ctrl + Tab Switch to t h e next child window o f a Multi ple D ocument Interf ace (MDI) pr ogram Alt + Underlined letter in Opens the menu and the function of the underlined letter -

Newline Characters Should Map to a Completely Ignorable Collation Element in the DUCET Marc Lodewijck (Brussels, Belgium) October 28, 2016
Proposal for consideration by UTC Newline characters should map to a completely ignorable collation element in the DUCET Marc Lodewijck (Brussels, Belgium) October 28, 2016 Assume the following records, which compare tertiary-equal: "xy#", "xy", "x#y" With the UCA “Shifted” option for handling variable collation elements, the sorting result is as follows: [3] x#y [1EFF 1F0B | 0020 0020 | 0002 0002 | FFFF 038F FFFF |] [2] xy [1EFF 1F0B | 0020 0020 | 0002 0002 | FFFF FFFF |] [1] xy# [1EFF 1F0B | 0020 0020 | 0002 0002 | FFFF FFFF 038F |] Inserting a variable character makes a string sort before the string without it; and appending a variable character makes a string sort after the string without it. With the “Shift-trimmed” option, this is the outcome: [2] xy [1EFF 1F0B | 0020 0020 | 0002 0002 | |] [3] x#y [1EFF 1F0B | 0020 0020 | 0002 0002 | FFFF 038F |] [1] xy# [1EFF 1F0B | 0020 0020 | 0002 0002 | FFFF FFFF 038F |] Inserting a variable character anywhere makes a string sort after the string without it; and the string having a variable character in the lowest position makes it sort before the other string. The “Shift-trimmed” option is the same as “Shifted”, except that trailing high-quaternary weights (from regular characters) are removed from the sort key. This means that, compared with “Shifted”, the “Shift-trimmed” option sorts strings without variable characters before ones with variable characters added—the string without variable characters has an empty fourth level. Now suppose we wish to sort the following text strings stored in a file: 1/6 It is obvious that we won’t strip off the newline character(s) at the end of each line, before it is processed further. -

Fuzzy Mouse Cursor Control System for Computer Users with Spinal Cord Injuries
Georgia State University ScholarWorks @ Georgia State University Computer Science Theses Department of Computer Science 8-8-2006 Fuzzy Mouse Cursor Control System for Computer Users with Spinal Cord Injuries Tihomir Surdilovic Follow this and additional works at: https://scholarworks.gsu.edu/cs_theses Part of the Computer Sciences Commons Recommended Citation Surdilovic, Tihomir, "Fuzzy Mouse Cursor Control System for Computer Users with Spinal Cord Injuries." Thesis, Georgia State University, 2006. https://scholarworks.gsu.edu/cs_theses/49 This Thesis is brought to you for free and open access by the Department of Computer Science at ScholarWorks @ Georgia State University. It has been accepted for inclusion in Computer Science Theses by an authorized administrator of ScholarWorks @ Georgia State University. For more information, please contact [email protected]. i Fuzzy Mouse Cursor Control System For Computer Users with Spinal Cord Injuries A Thesis Presented in Partial Fulfillment of Requirements for the Degree of Master of Science in the College of Arts and Sciences Georgia State University 2005 by Tihomir Surdilovic Committee: ____________________________________ Dr. Yan-Qing Zhang, Chair ____________________________________ Dr. Rajshekhar Sunderraman, Member ____________________________________ Dr. Michael Weeks, Member ____________________________________ Dr. Yi Pan, Department Chair Date July 21st 2005 ii Abstract People with severe motor-impairments due to Spinal Cord Injury (SCI) or Spinal Cord Dysfunction (SCD), often experience difficulty with accurate and efficient control of pointing devices (Keates et al., 02). Usually this leads to their limited integration to society as well as limited unassisted control over the environment. The questions “How can someone with severe motor-impairments perform mouse pointer control as accurately and efficiently as an able-bodied person?” and “How can these interactions be advanced through use of Computational Intelligence (CI)?” are the driving forces behind the research described in this paper.