Efficient Formal Verification for the Linux Kernel
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Reconfigurable Embedded Control Systems: Problems and Solutions
RECONFIGURABLE EMBEDDED CONTROL SYSTEMS: PROBLEMS AND SOLUTIONS By Dr.rer.nat.Habil. Mohamed Khalgui ⃝c Copyright by Dr.rer.nat.Habil. Mohamed Khalgui, 2012 v Martin Luther University, Germany Research Manuscript for Habilitation Diploma in Computer Science 1. Reviewer: Prof.Dr. Hans-Michael Hanisch, Martin Luther University, Germany, 2. Reviewer: Prof.Dr. Georg Frey, Saarland University, Germany, 3. Reviewer: Prof.Dr. Wolf Zimmermann, Martin Luther University, Germany, Day of the defense: Monday January 23rd 2012, Table of Contents Table of Contents vi English Abstract x German Abstract xi English Keywords xii German Keywords xiii Acknowledgements xiv Dedicate xv 1 General Introduction 1 2 Embedded Architectures: Overview on Hardware and Operating Systems 3 2.1 Embedded Hardware Components . 3 2.1.1 Microcontrollers . 3 2.1.2 Digital Signal Processors (DSP): . 4 2.1.3 System on Chip (SoC): . 5 2.1.4 Programmable Logic Controllers (PLC): . 6 2.2 Real-Time Embedded Operating Systems (RTOS) . 8 2.2.1 QNX . 9 2.2.2 RTLinux . 9 2.2.3 VxWorks . 9 2.2.4 Windows CE . 10 2.3 Known Embedded Software Solutions . 11 2.3.1 Simple Control Loop . 12 2.3.2 Interrupt Controlled System . 12 2.3.3 Cooperative Multitasking . 12 2.3.4 Preemptive Multitasking or Multi-Threading . 12 2.3.5 Microkernels . 13 2.3.6 Monolithic Kernels . 13 2.3.7 Additional Software Components: . 13 2.4 Conclusion . 14 3 Embedded Systems: Overview on Software Components 15 3.1 Basic Concepts of Components . 15 3.2 Architecture Description Languages . 17 3.2.1 Acme Language . -

The Next Big OS War Is in Your Dashboard
12/4/12 The Next Big OS War Is in Your Dashboard | Autopia | Wired.com Autopia Planes, Trains, Automobiles and the Future of Transportation Infotainment LTikwe ee1t54 297 25 Sharre 39 The Next Big OS War Is in Your Dashboard By Doug Newcomb 12.03.12 6:30 AM Follow @dougnew comb Photo: Jim Merithew/Wired Competition in automotive technology has long been about who’s got the most horsepower, the best towing capacity or the fastest acceleration. These days, though, it’s all about having the slickest infotainment systems and most-connected cars. The shift in focus from what’s under the hood to what’s behind the dashboard has brought a largely covert war to the auto industry over the operating systems that will control these gadgets. As in the smartphone biz, the battle line is between proprietary and open source software. The outcome will determine what these systems look like, how they work and how distinctive they are as automakers embrace walled gardens or open ecosystems. It would be difficult to overstate the importance of getting this right. The amount of software in the average vehicle has grown exponentially — a typical new car has about 100 million lines of code — with the advent of sophisticated, cloud-connected infotainment systems. Software has become a competitive advantage as vital to General Motors or Toyota as it is to Apple or Google. The trouble is, automotive development cycles are measured in years, while the consumer www.wired.com/autopia/2012/12/automotiv e-os-war/all/ 1/11 The Next Big OS War Is in Your Dashboard | Autopia | Wired.com electronics industry works in months. -

Linux Automotive Security “Safer and More Secure”
Linux Automotive Security “Safer and more secure” Authors Fulup Ar Foll [email protected] José Bollo [email protected] Abstract Cars are expensive pieces of equipment, yet they represent a huge mass market. Adding Internet connectivity to previous elements generates perfect conditions for the growth of a viable business model on attacking “Connected Cars”. It is already well understood that cars will be connected and connected cars will be attacked. While it's still too early to predict with certainty how “Connected Cars” will be impacted by security flaws, making the assumption that a car should be at least as secure as a TV, a set-top-box or a smart phone should make sense to everyone. This white paper focuses on how Linux best practices security mechanisms that could be used today and within the next couple of years to make connected cars safer and more secure. Version 1.0 January 2016 Linux Automotive Security Table of contents 1.Introduction...................................................................................................3 2.Make Sure You Run the Right Code...................................................................4 2.1.Before Booting............................................................................................4 2.2.When Booting.............................................................................................5 2.3.After Booting...............................................................................................5 3.Keeping Secrets Secret...................................................................................6 -

Table of Contents
1 Vol. 32, No. 3 April 2019 Table of Contents AGL Will Be Overtaken by Android Automotive 2 SmartDrive Has Massive Data Trove for AV Developers 6 The Company Profile: NVIDIA 8 Ludwigsburg Automotive Electronics Conference: 16 June 25-26, 2019 Momentum Is Building for a Self-Driving Safety Standard 17 Roland Berger Examines the New Mobility World 18 Roundup: 2018 Financial Results for Hyundai Mobis, 19 Lear, ZF The© Hansen2019 Paul Report Hansen onAssociates, Automotive 150 Pinehurst Electronics, Road, July/August Portsmouth, NH 2016 03801 USA www.hansenreport.comTelephone: 603-431-5859; email: [email protected] All rights reserved. Materials may not be reproduced in any form without written permission. ISSN 1046-1105 2 AGL Will Be Overtaken by Android Automotive The Linux Foundation just picked up another new member to work on its Automotive Grade Linux project, the collaborative open source effort to develop a common platform that can serve as a de facto standard for infotainment, telematics and instrument cluster applications. Volkswagen joined earlier this month. Thus far 130 members have signed onto the project; 30 members signed up in 2018. There is much to recommend AGL. The AGL Unified Code Base platform provides 70% of the starting point for a production project, including operating system, middleware and application framework. “If AGL can establish itself as a true automotive platform, suppliers will have a common set of interfaces their suppliers can write to,” said Tim VanGoethem, vice president of Advanced Mobility Solutions at Harman X, the company’s innovation taskforce. “Instead of paying people to write software on your behalf, you can take advantage of what has been done already and just license it to use in your final product.” Toyota and the Linux Foundation launched AGL in 2012 and thus far only Toyota has gone on record to say that it is committed to the platform. -

Software Defined Vertical Industries: Transformation Through Open Source
Software-defined vertical industries: transformation through open source How open collaboration enables user-centered innovation, achieving faster development cycles, time to market, and increased interoperability and cost savings. A Publication of The Linux Foundation | September 2020 www.linuxfoundation.org “When I say that innovation is being democratized, I mean that users of products and services-both firms and individual consumers are increasingly able to innovate for themselves. User-centered innovation processes offer great advantages over the manufacturer-centric innovation development systems that have been the mainstay of commerce for hundreds of years. Users that innovate can develop exactly what they want, rather than relying on manufacturers to act as their (often very imperfect) agents.” — Eric von Hippel, Democratizing Innovation The Linux Foundation 2 Overview What do some of the world’s largest, most regulated, Over the last 20 years, the Linux Foundation has expanded complex, centuries-old industries such as banKing, from a single project, the Linux kernel, to hundreds of telecommunications, and energy have in common with distinct project communities. The “foundation-as-a- rapid development, bleeding-edge innovative, creative service” model developed by Linux Foundation supports industries such as the motion pictures industry? communities collaborating on open source across key horizontal technology domains, such as cloud, security, They’re all dependent on open source software. blocKchain, and the web. That would be both a great answer and correct, but it However, many of these project communities align across doesn’t tell the whole story. A complete answer is these vertical industry groupings, such as automotive, motion industries not only depend on open source, but they’re pictures, finance, telecommunications, energy, and public building open source into the fabric of their R&D and health initiatives. -
Logca: a High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A
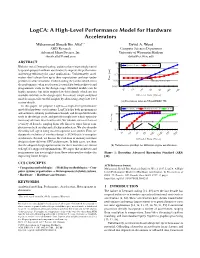
LogCA: A High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A. Wood AMD Research Computer Sciences Department Advanced Micro Devices, Inc. University of Wisconsin-Madison [email protected] [email protected] ABSTRACT 10 With the end of Dennard scaling, architects have increasingly turned Unaccelerated Accelerated 1 to special-purpose hardware accelerators to improve the performance and energy efficiency for some applications. Unfortunately, accel- 0.1 erators don’t always live up to their expectations and may under- perform in some situations. Understanding the factors which effect Time (ms) 0.01 Break-even point the performance of an accelerator is crucial for both architects and 0.001 programmers early in the design stage. Detailed models can be 16 64 highly accurate, but often require low-level details which are not 256 1K 4K 16K 64K available until late in the design cycle. In contrast, simple analytical Offloaded Data (Bytes) models can provide useful insights by abstracting away low-level system details. (a) Execution time on UltraSPARC T2. In this paper, we propose LogCA—a high-level performance 100 model for hardware accelerators. LogCA helps both programmers SPARC T4 UltraSPARC T2 GPU and architects identify performance bounds and design bottlenecks 10 early in the design cycle, and provide insight into which optimiza- tions may alleviate these bottlenecks. We validate our model across Speedup 1 Break-even point a variety of kernels, ranging from sub-linear to super-linear com- plexities on both on-chip and off-chip accelerators. We also describe the utility of LogCA using two retrospective case studies. -

Foreign Library Interface by Daniel Adler Dia Applications That Can Run on a Multitude of Plat- Forms
30 CONTRIBUTED RESEARCH ARTICLES Foreign Library Interface by Daniel Adler dia applications that can run on a multitude of plat- forms. Abstract We present an improved Foreign Function Interface (FFI) for R to call arbitary na- tive functions without the need for C wrapper Foreign function interfaces code. Further we discuss a dynamic linkage framework for binding standard C libraries to FFIs provide the backbone of a language to inter- R across platforms using a universal type infor- face with foreign code. Depending on the design of mation format. The package rdyncall comprises this service, it can largely unburden developers from the framework and an initial repository of cross- writing additional wrapper code. In this section, we platform bindings for standard libraries such as compare the built-in R FFI with that provided by (legacy and modern) OpenGL, the family of SDL rdyncall. We use a simple example that sketches the libraries and Expat. The package enables system- different work flow paths for making an R binding to level programming using the R language; sam- a function from a foreign C library. ple applications are given in the article. We out- line the underlying automation tool-chain that extracts cross-platform bindings from C headers, FFI of base R making the repository extendable and open for Suppose that we wish to invoke the C function sqrt library developers. of the Standard C Math library. The function is de- clared as follows in C: Introduction double sqrt(double x); We present an improved Foreign Function Interface The .C function from the base R FFI offers a call (FFI) for R that significantly reduces the amount of gate to C code with very strict conversion rules, and C wrapper code needed to interface with C. -

Hardware, Firmware, Devices Disks Kernel, Boot, Swap Files, Volumes
hardware, kernel, boot, firmware, disks files, volumes swap devices software, security, patching, networking references backup tracing, logging TTAASSKK\ OOSS AAIIXX AA//UUXX DDGG//UUXX FFrreeeeBBSSDD HHPP--UUXX IIRRIIXX Derived from By IBM, with Apple 1988- 4.4BSD-Lite input from 1995. Based and 386BSD. System V, BSD, etc. on AT&T Data General This table SysV.2.2 with was aquired does not Hewlett- SGI. SVR4- OS notes Runs mainly extensions by EMC in include Packard based on IBM from V.3, 1999. external RS/6000 and V.4, and BSD packages related 4.2 and 4.3 from hardware. /usr/ports. /usr/sysadm ssmmiitt ssaamm /bin/sysmgr (6.3+) ssmmiittttyy ttoooollcchheesstt administrativ /usr/Cadmin/ wwssmm FFiinnddeerr ssyyssaaddmm ssyyssiinnssttaallll ssmmhh (11.31+) e GUI bin/* /usr/sysadm/ useradd (5+) FFiinnddeerr uusseerraadddd aadddduusseerr uusseerraadddd privbin/ addUserAcco userdell (5+) //eettcc//aadddduusseerr uusseerrddeell cchhppaassss uusseerrddeell unt usermod edit rrmmuusseerr uusseerrmmoodd managing (5+) /etc/passwd users llssuusseerr ppww ggeettpprrppww ppaassssmmggmmtt mmkkuusseerr vviippww mmooddpprrppww /usr/Cadmin/ cchhuusseerr ppwwggeett bin/cpeople rmuser usrck TASK \ OS AAIIXX AA//UUXX DDGG//UUXX FFrreeeeBBSSDD HHPP--UUXX IIRRIIXX pprrttccoonnff uunnaammee iioossccaann hhiinnvv dmesg (if (if llssccffgg ssyyssccttll--aa you're lucky) llssaattttrr ddmmeessgg aaddbb ssyyssiinnffoo--vvvv catcat lsdev /var/run/dm model esg.boot stm (from the llssppaatthh ppcciiccoonnff--ll SupportPlus CDROM) list hardware dg_sysreport - bdf (like -

Op E N So U R C E Yea R B O O K 2 0
OPEN SOURCE YEARBOOK 2016 ..... ........ .... ... .. .... .. .. ... .. OPENSOURCE.COM Opensource.com publishes stories about creating, adopting, and sharing open source solutions. Visit Opensource.com to learn more about how the open source way is improving technologies, education, business, government, health, law, entertainment, humanitarian efforts, and more. Submit a story idea: https://opensource.com/story Email us: [email protected] Chat with us in Freenode IRC: #opensource.com . OPEN SOURCE YEARBOOK 2016 . OPENSOURCE.COM 3 ...... ........ .. .. .. ... .... AUTOGRAPHS . ... .. .... .. .. ... .. ........ ...... ........ .. .. .. ... .... AUTOGRAPHS . ... .. .... .. .. ... .. ........ OPENSOURCE.COM...... ........ .. .. .. ... .... ........ WRITE FOR US ..... .. .. .. ... .... 7 big reasons to contribute to Opensource.com: Career benefits: “I probably would not have gotten my most recent job if it had not been for my articles on 1 Opensource.com.” Raise awareness: “The platform and publicity that is available through Opensource.com is extremely 2 valuable.” Grow your network: “I met a lot of interesting people after that, boosted my blog stats immediately, and 3 even got some business offers!” Contribute back to open source communities: “Writing for Opensource.com has allowed me to give 4 back to a community of users and developers from whom I have truly benefited for many years.” Receive free, professional editing services: “The team helps me, through feedback, on improving my 5 writing skills.” We’re loveable: “I love the Opensource.com team. I have known some of them for years and they are 6 good people.” 7 Writing for us is easy: “I couldn't have been more pleased with my writing experience.” Email us to learn more or to share your feedback about writing for us: https://opensource.com/story Visit our Participate page to more about joining in the Opensource.com community: https://opensource.com/participate Find our editorial team, moderators, authors, and readers on Freenode IRC at #opensource.com: https://opensource.com/irc . -

Xinxinli Green Polygons
Automotive Grade Linux on Raspberry Pi: How Does It Work? Leon Anavi Konsulko Group [email protected] [email protected] Embedded Linux Conference North America 2020 Konsulko Group Services company specializing in Embedded Linux and Open Source Software Hardware/software build, design, development, and training services Based in San Jose, CA with an engineering presence worldwide http://konsulko.com/ ELC NA 2020, Leon Anavi, Automotive Grade Linux on Raspberry Pi: How Does It Work? Agenda Automotive Grade Linux Raspberry Pi Building an AGL image for Raspberry Pi Understanding how AGL works on Raspberry Pi Conclusions Q&A ELC NA 2020, Leon Anavi, Automotive Grade Linux on Raspberry Pi: How Does It Work? Automotive Grade Linux (AGL) Project of the Linux Foundation Open source GNU/Linux automotive distribution with In-Vehicle-Infotainment (IVI) Based on the Yocto Project and OpenEmbedded Founded in 2014 ELC NA 2020, Leon Anavi, Automotive Grade Linux on Raspberry Pi: How Does It Work? AGL Members ELC NA 2020, Leon Anavi, Automotive Grade Linux on Raspberry Pi: How Does It Work? AGL Core Technologies Qt/QML HMI HTML5 GStreamer Weston with agl-shell-dekstop Wayland SOTA Updates: OSTree & Aktualizr PipeWire Security systemd AppFW, Cynagora, Linux kernel SMACK ELC NA 2020, Leon Anavi, Automotive Grade Linux on Raspberry Pi: How Does It Work? Yocto/OpenEmbedded Layers in AGL poky meta-security meta-agl meta-virtualization meta-agl-cluster-demo meta-qt5 meta-agl-demo meta-updater meta-agl-devel neta-spdxscanner Meta-agl-extra meta-clang meta-agl-telematics-demo BSP layers: meta-raspberrypi, meta-intel, meta-ti, meta-openembedded meta-renesas-rcar-gen3, meta-sancloud, etc. -

Digitalization of Kernel Diversion from the Upstream to Minimize Local Code Modifications
Did you care for purity of your Linux BSP Computer aided BSP kernel sanity check Yaminabe2 execution and trial result conclusion Digitalization of Kernel Diversion from the Upstream To minimize local code modifications Hisao Munakata Linux Foundation Consumer Electronics working group April 4th 2016 1 / 52 Hisao Munakata Digitalization of Kernel Diversion from the Upstream Did you care for purity of your Linux BSP Computer aided BSP kernel sanity check Yaminabe2 execution and trial result conclusion Who am I ? From an embedded SoC provider company Renesas Linux Foundation CE1 working Gr. Steering committee and AG member LF/CEWG LTSI2 project initiator member An Advisory Board and major contributor of AGL3 Leads dedicated upstream development team at Renesas And, supports customers who develop automotive IVI products 1CE = Consumer Electronics 2LTSI =Long Term Support Initiative 3AGL =Automotive Grade Linux 2 / 52 Hisao Munakata Digitalization of Kernel Diversion from the Upstream Did you care for purity of your Linux BSP Computer aided BSP kernel sanity check Yaminabe2 execution and trial result conclusion Renesas contributes for kernel upstream development http://lwn.net/Articles/679289/ 3 / 52 Hisao Munakata Digitalization of Kernel Diversion from the Upstream Did you care for purity of your Linux BSP Computer aided BSP kernel sanity check common embedded Linux issues caused by in-house kernel Yaminabe2 execution and trial result Sanity assessment for the vendor kernel conclusion Did you care for purity of your Linux BSP 4 / 52 Hisao -

Basics of UNIX
Basics of UNIX August 23, 2012 By UNIX, I mean any UNIX-like operating system, including Linux and Mac OS X. On the Mac you can access a UNIX terminal window with the Terminal application (under Applica- tions/Utilities). Most modern scientific computing is done on UNIX-based machines, often by remotely logging in to a UNIX-based server. 1 Connecting to a UNIX machine from {UNIX, Mac, Windows} See the file on bspace on connecting remotely to SCF. In addition, this SCF help page has infor- mation on logging in to remote machines via ssh without having to type your password every time. This can save a lot of time. 2 Getting help from SCF More generally, the department computing FAQs is the place to go for answers to questions about SCF. For questions not answered there, the SCF requests: “please report any problems regarding equipment or system software to the SCF staff by sending mail to ’trouble’ or by reporting the prob- lem directly to room 498/499. For information/questions on the use of application packages (e.g., R, SAS, Matlab), programming languages and libraries send mail to ’consult’. Questions/problems regarding accounts should be sent to ’manager’.” Note that for the purpose of this class, questions about application packages, languages, li- braries, etc. can be directed to me. 1 3 Files and directories 1. Files are stored in directories (aka folders) that are in a (inverted) directory tree, with “/” as the root of the tree 2. Where am I? > pwd 3. What’s in a directory? > ls > ls -a > ls -al 4.