Commit Signatures for Centralized Version Control Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pragmatic Version Control Using Subversion
What readers are saying about Pragmatic Version Control using Subversion I expected a lot, but you surprised me with even more. Hav- ing used CVS for years I hesitated to try Subversion until now, although I knew it would solve many of the shortcom- ings of CVS. After reading your book, my excuses to stay with CVS disappeared. Oh, and coming from the Pragmatic Bookshelf this book is fun to read too. Thanks Mike. Steffen Gemkow Managing Director, ObjectFab GmbH I’m a long-time user of CVS and I’ve been skeptical of Sub- version, wondering if it would ever be “ready for prime time.” Until now. Thanks to Mike Mason for writing a clear, con- cise, gentle introduction to this new tool. After reading this book, I’m actually excited about the possibilities for version control that Subversion brings to the table. David Rupp Senior Software Engineer, Great-West Life & Annuity This was exactly the Subversion book I was waiting for. As a long-time Perforce and CVS user and administrator, and in my role as an agile tools coach, I wanted a compact book that told me just what I needed to know. This is it. Within a couple of hours I was up and running against remote Subversion servers, and setting up my own local servers too. Mike uses a lot of command-line examples to guide the reader, and as a Windows user I was worried at first. My fears were unfounded though—Mike’s examples were so clear that I think I’ll stick to using the command line from now on! I thoroughly recommend this book to anyone getting started using or administering Subversion. -

Version Control 101 Exported from Please Visit the Link for the Latest Version and the Best Typesetting
Version Control 101 Exported from http://cepsltb4.curent.utk.edu/wiki/efficiency/vcs, please visit the link for the latest version and the best typesetting. Version Control 101 is created in the hope to minimize the regret from lost files or untracked changes. There are two things I regret. I should have learned Python instead of MATLAB, and I should have learned version control earlier. Version control is like a time machine. It allows you to go back in time and find out history files. You might have heard of GitHub and Git and probably how steep the learning curve is. Version control is not just Git. Dropbox can do version control as well, for a limited time. This tutorial will get you started with some version control concepts from Dropbox to Git for your needs. More importantly, some general rules are suggested to minimize the chance of file losses. Contents Version Control 101 .............................................................................................................................. 1 General Rules ................................................................................................................................... 2 Version Control for Files ................................................................................................................... 2 DropBox or Google Drive ............................................................................................................. 2 Version Control on Confluence ................................................................................................... -

Generating Commit Messages from Git Diffs
Generating Commit Messages from Git Diffs Sven van Hal Mathieu Post Kasper Wendel Delft University of Technology Delft University of Technology Delft University of Technology [email protected] [email protected] [email protected] ABSTRACT be exploited by machine learning. The hypothesis is that methods Commit messages aid developers in their understanding of a con- based on machine learning, given enough training data, are able tinuously evolving codebase. However, developers not always doc- to extract more contextual information and latent factors about ument code changes properly. Automatically generating commit the why of a change. Furthermore, Allamanis et al. [1] state that messages would relieve this burden on developers. source code is “a form of human communication [and] has similar Recently, a number of different works have demonstrated the statistical properties to natural language corpora”. Following the feasibility of using methods from neural machine translation to success of (deep) machine learning in the field of natural language generate commit messages. This work aims to reproduce a promi- processing, neural networks seem promising for automated commit nent research paper in this field, as well as attempt to improve upon message generation as well. their results by proposing a novel preprocessing technique. Jiang et al. [12] have demonstrated that generating commit mes- A reproduction of the reference neural machine translation sages with neural networks is feasible. This work aims to reproduce model was able to achieve slightly better results on the same dataset. the results from [12] on the same and a different dataset. Addition- When applying more rigorous preprocessing, however, the per- ally, efforts are made to improve upon these results by applying a formance dropped significantly. -

Sistemas De Control De Versiones De Última Generación (DCA)
Tema 10 - Sistemas de Control de Versiones de última generación (DCA) Antonio-M. Corbí Bellot Tema 10 - Sistemas de Control de Versiones de última generación (DCA) II HISTORIAL DE REVISIONES NÚMERO FECHA MODIFICACIONES NOMBRE Tema 10 - Sistemas de Control de Versiones de última generación (DCA) III Índice 1. ¿Qué es un Sistema de Control de Versiones (SCV)?1 2. ¿En qué consiste el control de versiones?1 3. Conceptos generales de los SCV (I) 1 4. Conceptos generales de los SCV (II) 2 5. Tipos de SCV. 2 6. Centralizados vs. Distribuidos en 90sg 2 7. ¿Qué opciones tenemos disponibles? 2 8. ¿Qué podemos hacer con un SCV? 3 9. Tipos de ramas 3 10. Formas de integrar una rama en otra (I)3 11. Formas de integrar una rama en otra (II)4 12. SCV’s con los que trabajaremos 4 13. Git (I) 5 14. Git (II) 5 15. Git (III) 5 16. Git (IV) 6 17. Git (V) 6 18. Git (VI) 7 19. Git (VII) 7 20. Git (VIII) 7 21. Git (IX) 8 22. Git (X) 8 23. Git (XI) 9 Tema 10 - Sistemas de Control de Versiones de última generación (DCA) IV 24. Git (XII) 9 25. Git (XIII) 9 26. Git (XIV) 10 27. Git (XV) 10 28. Git (XVI) 11 29. Git (XVII) 11 30. Git (XVIII) 12 31. Git (XIX) 12 32. Git. Vídeos relacionados 12 33. Mercurial (I) 12 34. Mercurial (II) 12 35. Mercurial (III) 13 36. Mercurial (IV) 13 37. Mercurial (V) 13 38. Mercurial (VI) 14 39. -

Code Review Is an Architectural Necessity
Code review is an architectural necessity Colin Dean @colindean 1 @ColinDean Software Engineer Organizer, Abstractions.io Wearer of many hats 2 My words are my own and not my employer(s), past or present. Please save questions until the end of the presentation. 3 Agenda • Quick anecdote • What is code review? • What problems does code review solve? • Quality attributes code review ensures • Tips for code reviews • Limitations 4 5 Agenda • Quick anecdote • What is code review? • What problems do code review solve? • Quality attributes code review ensures • Tips for code reviews • Limitations 6 What is code review? 7 Code review is the process by which those who maintain a software codebase evaluate a proposed change to that codebase, regardless of the source of the proposed change. 8 Code review is systematic examination of computer source code. Code Review, Wikipedia 9 Peer Review 10 Code Review 11 Code Review Vocabulary • Change - an individual unit of work altering what exists • Submission - a collection of changes • Submitter - the person proposing the submission • Reviewer - the people evaluating the submission • Annotation - remarks or ratings bestowed upon the submission 12 The submitter proposes changes in a submission, which is evaluated by a reviewer, who annotates or accepts it. 13 Most formal Least formal Team Pair Peer Inspection Walkthrough Ad-hoc review review programming deskcheck, passaround Wiegers’ peer review formality spectrum 14 Most formal Least formal Team Pair Peer Inspection Walkthrough Ad-hoc review review programming deskcheck, passaround Wiegers’ peer review formality spectrum 15 16 Agenda • Quick anecdote • What is code review? • What problems does code review solve? • Quality attributes code review ensures • Tips for code reviews • Limitations 17 Aside from the primary goal of reducing defects, Code review solves two major problems. -

Brno University of Technology Bulk Operation
BRNO UNIVERSITY OF TECHNOLOGY VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ FACULTY OF INFORMATION TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ DEPARTMENT OF INFORMATION SYSTEMS ÚSTAV INFORMAČNÍCH SYSTÉMŮ BULK OPERATION ORCHESTRATION IN MULTIREPO CI/CD ENVIRONMENTS HROMADNÁ ORCHESTRÁCIA V MULTIREPO CI/CD PROSTREDIACH MASTER’S THESIS DIPLOMOVÁ PRÁCE AUTHOR Bc. JAKUB VÍŠEK AUTOR PRÁCE SUPERVISOR Ing. MICHAL KOUTENSKÝ VEDOUCÍ PRÁCE BRNO 2021 Brno University of Technology Faculty of Information Technology Department of Information Systems (DIFS) Academic year 2020/2021 Master's Thesis Specification Student: Víšek Jakub, Bc. Programme: Information Technology and Artificial Intelligence Specializatio Computer Networks n: Title: Bulk Operation Orchestration in Multirepo CI/CD Environments Category: Networking Assignment: 1. Familiarize yourself with the principle of CI/CD and existing solutions. 2. Familiarize yourself with the multirepo approach to software development. 3. Analyze the shortcomings of existing CI/CD solutions in the context of multirepo development with regard to user comfort. Focus on scheduling and deploying bulk operations on multiple interdependent repositories as part of a single logical branching pipeline. 4. Propose and design a solution to these shortcomings. 5. Implement said solution. 6. Test and evaluate the solution's functionality in a production environment. Recommended literature: Humble, Jez, and David Farley. Continuous delivery. Upper Saddle River, NJ: Addison- Wesley, 2011. Forsgren, Nicole, Jez Humble, and Gene Kim. Accelerate : building and scaling high performing technology organizations. Portland, OR: IT Revolution Press, 2018. Nicolas Brousse. 2019. The issue of monorepo and polyrepo in large enterprises. In Proceedings of the Conference Companion of the 3rd International Conference on Art, Science, and Engineering of Programming (Programming '19). Association for Computing Machinery, New York, NY, USA, Article 2, 1-4. -

Making the Most of Git and Github
Contributing to Erlang Making the Most of Git and GitHub Tom Preston-Werner Cofounder/CTO GitHub @mojombo Quick Git Overview Git is distributed Tom PJ Chris Git is snapshot-based The Codebase 1 Snapshots have zero or more parents 1 2 Branching in Git is easy 1 2 3 4 Merging in Git is easy too 1 2 3 5 4 A branch is just a pointer to a snapshot master 1 2 3 5 4 Branches move as new snapshots are taken master 1 2 3 5 6 4 Tags are like branches that never move master 1 2 3 5 6 4 v1.0.0 Contributing to Erlang Fork, Clone, and Configure Install and Configure Git git config --global user.name "Tom Preston-Werner" git config --global user.email [email protected] Sign up on GitHub Fork github.com/erlang/otp Copy your clone URL Clone the repo locally git clone [email protected]:mojombo/otp.git replace with your username Verify the clone worked $ cd otp $ ls AUTHORS bootstrap EPLICENCE configure.in INSTALL-CROSS.md erl-build-tool-vars.sh INSTALL-WIN32.md erts INSTALL.md lib Makefile.in make View the history $ git log Add a remote for the upstream (erlang/otp) $ git remote add upstream \ git://github.com/erlang/otp.git Repositories GitHub GitHub erlang/otp mojombo/otp upstream origin Local otp Create a branch List all branches $ git branch * dev Create a branch off of “dev” and switch to it $ git checkout -b mybranch Both branches now point to the same commit dev mybranch Make Changes Each commit should: Contain a single logical change Compile cleanly Not contain any cruft Have a good commit message Review your changes $ git status $ git diff Commit your -
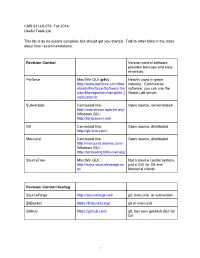
Useful Tools for Game Making
CMS.611J/6.073 Fall 2014 Useful Tools List This list is by no means complete, but should get you started. Talk to other folks in the class about their recommendations. Revision Control Version control software, provides backups and easy reversion. Perforce Mac/Win GUI (p4v): Heavily used in game http://www.perforce.com/dow industry. Commercial nloads/Perforce-Software-Ver software; you can use the sion-Management/complete_l Game Lab server. ist/Customer Subversion Command line: Open source, server-based http://subversion.apache.org/ Windows GUI: http://tortoisesvn.net/ Git Command line: Open source, distributed http://git-scm.com/ Mercurial Command line: Open source, distributed http://mercurial.selenic.com/ Windows GUI: http://tortoisehg.bitbucket.org/ SourceTree Mac/Win GUI: Not a source control system, http://www.sourcetreeapp.co just a GUI for Git and m/ Mercurial clients Revision Control Hosting SourceForge http://sourceforge.net/ git, mercurial, or subversion BitBucket https://bitbucket.org/ git or mercurial GitHub https://github.com/ git, has own (painful) GUI for Git 1 Image Editing MSPaint Windows, pre-installed Surprisingly useful quick pixel art editor (esp for prototypes) Paint.NET Windows, About as easy as MSPaint, but http://www.getpaint.net/download much more powerful .html Photoshop Mac, Windows New Media Center, 26-139 GIMP Many platforms, Easier than photoshop, at http://www.gimp.org/downloads/ least. Sound GarageBand Mac New Media Center, 26-139 Audacity Many platforms, Free, open source. http://audacity.sourceforge.ne -

Seapine ALM Reporting Platform Database Reference Guide V2016.1
Seapine ALM Data Warehouse Database Reference Guide Version 2016.1 Contents Key entities ................................................................................................................................................................... 1 Repository ................................................................................................................................................................. 1 License Server .......................................................................................................................................................... 1 QA Wizard Pro .......................................................................................................................................................... 1 Surround SCM ........................................................................................................................................................... 1 TestTrack ................................................................................................................................................................... 2 Data dictionary ............................................................................................................................................................. 5 Table: LS_AUTHENTICATION_METHOD ................................................................................................................ 5 Table: LS_EMAIL ..................................................................................................................................................... -

Jenkins Job Builder Documentation Release 3.10.0
Jenkins Job Builder Documentation Release 3.10.0 Jenkins Job Builder Maintainers Aug 23, 2021 Contents 1 README 1 1.1 Developers................................................1 1.2 Writing a patch..............................................2 1.3 Unit Tests.................................................2 1.4 Installing without setup.py........................................2 2 Contents 5 2.1 Quick Start Guide............................................5 2.1.1 Use Case 1: Test a job definition................................5 2.1.2 Use Case 2: Updating Jenkins Jobs...............................5 2.1.3 Use Case 3: Working with JSON job definitions........................6 2.1.4 Use Case 4: Deleting a job...................................6 2.1.5 Use Case 5: Providing plugins info...............................6 2.2 Installation................................................6 2.2.1 Documentation.........................................7 2.2.2 Unit Tests............................................7 2.2.3 Test Coverage..........................................7 2.3 Configuration File............................................7 2.3.1 job_builder section.......................................8 2.3.2 jenkins section.........................................9 2.3.3 hipchat section.........................................9 2.3.4 stash section...........................................9 2.3.5 __future__ section.......................................9 2.4 Running.................................................9 2.4.1 Test Mode........................................... -

Visual Build Help
Visual Build Professional User's Manual Copyright © 1999-2021 Kinook Software, Inc. Contents I Table of Contents Part I Introduction 1 1 Overview ................................................................................................................................... 1 2 Why Visual................................................................................................................................... Build? 1 3 New Features................................................................................................................................... 2 Version 4 .......................................................................................................................................................... 2 Version 5 .......................................................................................................................................................... 3 Version 6 .......................................................................................................................................................... 4 Version 7 .......................................................................................................................................................... 7 Version 8 .......................................................................................................................................................... 9 Version 9 ......................................................................................................................................................... -

DVCS Or a New Way to Use Version Control Systems for Freebsd
Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions DVCS or a new way to use Version Control Systems for FreeBSD Ollivier ROBERT <[email protected]> BSDCan 2006 Ottawa, Canada May, 12-13th, 2006 Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions Agenda 1 Brief history of VCS 2 FreeBSD context & gures 3 Is Arch/baz suited for FreeBSD? 4 Mercurial to the rescue 5 New processes & policies needed 6 Conclusions Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions The ancestors: SCCS, RCS File-oriented Use a subdirectory to store deltas and metadata Use lock-based architecture Support shared developments through NFS (fragile) SCCS is proprietary (System V), RCS is Open Source a SCCS clone exists: CSSC You can have a central repository with symlinks (RCS) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS, the de facto VCS for the free world Initially written as shell wrappers over RCS then rewritten in C Centralised server Easy UI Use sandboxes to avoid locking Simple 3-way merges Can be replicated through CVSup or even rsync Extensive documentation (papers, websites, books) Free software and used everywhere (SourceForge for example) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS annoyances and aws BUT..