Coverity Static Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Enabling RUST for UEFI Firmware
presented by Enabling RUST for UEFI Firmware UEFI 2020 Virtual Plugfest August 20, 2020 Jiewen Yao & Vincent Zimmer, Intel Corporation www.uefi.org 1 Jiewen Yao • Jiewen Yao is a principal engineer in the Intel Architecture, Graphics, and Software Group. He has been engaged as a firmware developer for over 15 years. He is a member of the UEFI Security sub team, and the TCG PC Client sub working group. www.uefi.org 2 Vincent Zimmer • Vincent Zimmer is a senior principal engineer in the Intel Architecture, Graphics, and Software Group. He has been engaged as a firmware developer for over 25 years and leads the UEFI Security sub team. www.uefi.org 3 Agenda • EDKII Security Summary • RUST Language • Enabling RUST for EDKII • Summary / Call to Action www.uefi.org 4 EDKII Security Summary www.uefi.org 5 BIOS Memory Issue in Hack Conf www.uefi.org 6 BIOS Security Bug Top Issue Open Source Close Source Buffer Overflow/ 50% 38% Integer Overflow SMM 7% 18% Variable 8% 5% Register Lock 3% 10% www.uefi.org 7 Vulnerabilities in C/C++ Source: Trends, challenges, and strategic shifts in the software vulnerability mitigation landscape – Microsoft, Bluehat IL 2019 www.uefi.org 8 Firmware as Software • Many software issues are also firmware issues. – Buffer Overflow – Integer Overflow – Uninitialized Variable • Software mitigation can be used for firmware mitigation. – (See next page) www.uefi.org 9 3 Levels of Prevention Prevention Method EDKII Open Source Example Eliminate Reduce Attack Surface SMI Handler Profile Vulnerability Static Analysis / Dynamic -

Beyond BIOS Developing with the Unified Extensible Firmware Interface
Digital Edition Digital Editions of selected Intel Press books are in addition to and complement the printed books. Click the icon to access information on other essential books for Developers and IT Professionals Visit our website at www.intel.com/intelpress Beyond BIOS Developing with the Unified Extensible Firmware Interface Second Edition Vincent Zimmer Michael Rothman Suresh Marisetty Copyright © 2010 Intel Corporation. All rights reserved. ISBN 13 978-1-934053-29-4 This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold with the understanding that the publisher is not engaged in professional services. If professional advice or other expert assistance is required, the services of a competent professional person should be sought. Intel Corporation may have patents or pending patent applications, trademarks, copyrights, or other intellectual property rights that relate to the presented subject matter. The furnishing of documents and other materials and information does not provide any license, express or implied, by estoppel or otherwise, to any such patents, trademarks, copyrights, or other intellectual property rights. Intel may make changes to specifications, product descriptions, and plans at any time, without notice. Fictitious names of companies, products, people, characters, and/or data mentioned herein are not intended to represent any real individual, company, product, or event. Intel products are not intended for use in medical, life saving, life sustaining, critical control or safety systems, or in nuclear facility applications. Intel, the Intel logo, Celeron, Intel Centrino, Intel NetBurst, Intel Xeon, Itanium, Pentium, MMX, and VTune are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. -

Working with Unreliable Observers Using Reactive Extensions
Master thesis WORKING WITH UNRELIABLE OBSERVERS USING REACTIVE EXTENSIONS November 10, 2016 Dorus Peelen (s4167821) Computing science Radboud University [email protected] — Supervisors: Radboud University: Rinus Plasmeijer Aia Software: Jeroen ter Hofstede Contents 1 Introduction 5 1.1 Overview of thesis . .7 2 Background 8 2.1 Aia Software . .8 2.2 Current situation . .8 2.3 The use case . .9 2.3.1 Technical details . 10 2.3.2 Potential problems . 11 2.4 Problem description . 11 2.5 Desired Properties of the new system . 11 3 Overview of Rx 13 3.1 Basic Ideas of Rx . 13 3.2 Observer and Observable . 15 3.3 Hot vs Cold observables . 15 3.4 Marble diagrams . 16 3.5 Transformations on Event Streams . 16 3.6 Schedulers . 16 3.7 Control process in Rx . 17 3.8 Interactive vs reactive . 18 3.9 Push-back and backpressure . 18 3.10 Operators with unbounded Queue . 19 3.11 Explanation and example of different operators in Rx . 19 3.11.1 Select .................................. 19 3.11.2 SelectMany ............................... 20 3.11.3 Where .................................. 20 3.11.4 Delay .................................. 20 3.11.5 Merge and Concat ........................... 21 3.11.6 Buffer and Window ........................... 21 3.11.7 GroupBy ................................. 21 3.11.8 Amb .................................... 21 3.11.9 Debounce, Sample and Throttle ................... 22 3.11.10 ObserveOn ................................ 22 3.12 Related work . 22 3.12.1 TPL . 23 3.12.2 iTasks . 23 4 The experiment 25 4.1 Important properties . 25 4.2 Test architecture . 26 4.2.1 Design . 26 2 4.2.2 Concepts . -

Version Control Systems, Build Automation and Continuous Integration Integration and Verification Techniques
Version Control Systems, Build Automation and Continuous Integration Integration and Verification Techniques Systematic methods and automation can highly enhance the teamwork on software projects. During this laboratory we will learn the basics of the following techniques: • Version control systems to support efficient teamwork. • Build automation to ensure stable and consistent builds. • Continuous Integration to provide automatic and systematic build, test execution and also deployments. 1 Version Control Systems Version control systems allow to keep all the historical versions of your software for easy tracking. Using version control also benefits team collaboration and improves the efficiency of the development team. In addition, it can be used as a central repository for the data, making build automation and continuous integration possible. There are historically two different approaches for managing the repositories: • Centralized model (CVS and Subversion/SVN): there is one server that contains “the repository” and everyone else checks code into and out of that repository. An important feature of these systems is that only the repository has the full history of all changes made. A checkout from this central repository will place a “working copy” on the user’s machine. This is a snapshot from a certain version of the project on his/her disk. • Distributed model (Git): In a distributed version control system, instead of a checkout, a user will clone a repository from a remote server. In return, he/she receives a full-fledged repository, not just a working copy. The user then has his/her own repository on the local machine – including all of the project’s history. -
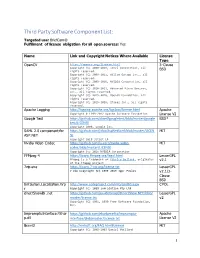
Third Party Software Component List: Targeted Use: Briefcam® Fulfillment of License Obligation for All Open Sources: Yes
Third Party Software Component List: Targeted use: BriefCam® Fulfillment of license obligation for all open sources: Yes Name Link and Copyright Notices Where Available License Type OpenCV https://opencv.org/license.html 3-Clause Copyright (C) 2000-2019, Intel Corporation, all BSD rights reserved. Copyright (C) 2009-2011, Willow Garage Inc., all rights reserved. Copyright (C) 2009-2016, NVIDIA Corporation, all rights reserved. Copyright (C) 2010-2013, Advanced Micro Devices, Inc., all rights reserved. Copyright (C) 2015-2016, OpenCV Foundation, all rights reserved. Copyright (C) 2015-2016, Itseez Inc., all rights reserved. Apache Logging http://logging.apache.org/log4cxx/license.html Apache Copyright © 1999-2012 Apache Software Foundation License V2 Google Test https://github.com/abseil/googletest/blob/master/google BSD* test/LICENSE Copyright 2008, Google Inc. SAML 2.0 component for https://github.com/jitbit/AspNetSaml/blob/master/LICEN MIT ASP.NET SE Copyright 2018 Jitbit LP Nvidia Video Codec https://github.com/lu-zero/nvidia-video- MIT codec/blob/master/LICENSE Copyright (c) 2016 NVIDIA Corporation FFMpeg 4 https://www.ffmpeg.org/legal.html LesserGPL FFmpeg is a trademark of Fabrice Bellard, originator v2.1 of the FFmpeg project 7zip.exe https://www.7-zip.org/license.txt LesserGPL 7-Zip Copyright (C) 1999-2019 Igor Pavlov v2.1/3- Clause BSD Infralution.Localization.Wp http://www.codeproject.com/info/cpol10.aspx CPOL f Copyright (C) 2018 Infralution Pty Ltd directShowlib .net https://github.com/pauldotknopf/DirectShow.NET/blob/ LesserGPL -

Nys Fair Events Mobile Application with Client-Side Caching
NYS FAIR EVENTS MOBILE APPLICATION WITH CLIENT-SIDE CACHING A Master’s Project Presented to Department of Computer and Information Sciences SUNY Polytechnic Institute Utica, New York In Partial Fulfilment of the requirements for the Master of Science Degree By Sumant Kanala (U00287895) December 2017 © SUMANT KANALA 2017 NYS Fair Events Mobile application with client-side caching Declaration I declare that this project is my own work and has not been submitted in any form for another degree or diploma at any university or other institute of tertiary education. Information derived from the published and unpublished work of others has been acknowledged in the text and a list of references is given. _________________ Sumant Kanala Abstract NYS Fair Events collects data about fair events which happen in New York state throughout the year, bundles them, displays the upcoming events and useful information about the event itself, the weather and forecast prediction, and a Google Maps to show the route to the event from the user’s location. The motivation for creating this project arose with understanding the growing market for mobile applications and by working for a startup for several months now in the field of web development. A trend has been established in which more users are switching towards mobile apps as their preferred information exchange tool than their traditional PCs and hence the development of better apps should be geared towards mobile phones and tablet PCs. The development of the app is mainly divided into two steps, the client and server side. For the client side I developed a Cordova-based mobile app which is cross-platform and can be compiled to work on Android and IOS based mobile devices. -

An Opinionated Guide to Technology Frontiers
TECHNOLOGY RADAR An opinionated guide to technology frontiers Volume 24 #TWTechRadar thoughtworks.com/radar The Technology Advisory Board (TAB) is a group of 20 senior technologists at Thoughtworks. The TAB meets twice a year face-to-face and biweekly by phone. Its primary role is to be an advisory group for Thoughtworks CTO, Contributors Rebecca Parsons. The Technology Radar is prepared by the The TAB acts as a broad body that can look at topics that affect technology and technologists at Thoughtworks. With the ongoing global pandemic, we Thoughtworks Technology Advisory Board once again created this volume of the Technology Radar via a virtual event. Rebecca Martin Fowler Bharani Birgitta Brandon Camilla Cassie Parsons (CTO) (Chief Scientist) Subramaniam Böckeler Byars Crispim Shum Erik Evan Fausto Hao Ian James Lakshminarasimhan Dörnenburg Bottcher de la Torre Xu Cartwright Lewis Sudarshan Mike Neal Perla Rachel Scott Shangqi Zhamak Mason Ford Villarreal Laycock Shaw Liu Dehghani TECHNOLOGY RADAR | 2 © Thoughtworks, Inc. All Rights Reserved. About the Radar Thoughtworkers are passionate about technology. We build it, research it, test it, open source it, write about it and constantly aim to improve it — for everyone. Our mission is to champion software excellence and revolutionize IT. We create and share the Thoughtworks Technology Radar in support of that mission. The Thoughtworks Technology Advisory Board, a group of senior technology leaders at Thoughtworks, creates the Radar. They meet regularly to discuss the global technology strategy for Thoughtworks and the technology trends that significantly impact our industry. The Radar captures the output of the Technology Advisory Board’s discussions in a format that provides value to a wide range of stakeholders, from developers to CTOs. -

Command Line Interface
Command Line Interface Squore 21.0.2 Last updated 2021-08-19 Table of Contents Preface. 1 Foreword. 1 Licence. 1 Warranty . 1 Responsabilities . 2 Contacting Vector Informatik GmbH Product Support. 2 Getting the Latest Version of this Manual . 2 1. Introduction . 3 2. Installing Squore Agent . 4 Prerequisites . 4 Download . 4 Upgrade . 4 Uninstall . 5 3. Using Squore Agent . 6 Command Line Structure . 6 Command Line Reference . 6 Squore Agent Options. 6 Project Build Parameters . 7 Exit Codes. 13 4. Managing Credentials . 14 Saving Credentials . 14 Encrypting Credentials . 15 Migrating Old Credentials Format . 16 5. Advanced Configuration . 17 Defining Server Dependencies . 17 Adding config.xml File . 17 Using Java System Properties. 18 Setting up HTTPS . 18 Appendix A: Repository Connectors . 19 ClearCase . 19 CVS . 19 Folder Path . 20 Folder (use GNATHub). 21 Git. 21 Perforce . 23 PTC Integrity . 25 SVN . 26 Synergy. 28 TFS . 30 Zip Upload . 32 Using Multiple Nodes . 32 Appendix B: Data Providers . 34 AntiC . 34 Automotive Coverage Import . 34 Automotive Tag Import. 35 Axivion. 35 BullseyeCoverage Code Coverage Analyzer. 36 CANoe. 36 Cantata . 38 CheckStyle. .. -

Preview Grav Tutorial (PDF Version)
Grav About the Tutorial Grav is a flat-file based content management system which doesn't use database to store the content instead it uses text file (.txt) or markdown (.md) file to store the content. The flat-file part specifically refers to the readable text and it handles the content in an easy way which can be simple for a developer. Audience This tutorial has been prepared for anyone who has a basic knowledge of Markdown and has an urge to develop websites. After completing this tutorial, you will find yourself at a moderate level of expertise in developing websites using Grav. Prerequisites Before you start proceeding with this tutorial, we assume that you are already aware about the basics of Markdown. If you are not well aware of these concepts, then we will suggest you to go through our short tutorials on Markdown. Copyright & Disclaimer Copyright 2017 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at [email protected] i Grav Table of Contents About the Tutorial ................................................................................................................................... -

Precise Null Pointer Analysis Through Global Value Numbering
Precise Null Pointer Analysis Through Global Value Numbering Ankush Das1 and Akash Lal2 1 Carnegie Mellon University, Pittsburgh, PA, USA 2 Microsoft Research, Bangalore, India Abstract. Precise analysis of pointer information plays an important role in many static analysis tools. The precision, however, must be bal- anced against the scalability of the analysis. This paper focusses on improving the precision of standard context and flow insensitive alias analysis algorithms at a low scalability cost. In particular, we present a semantics-preserving program transformation that drastically improves the precision of existing analyses when deciding if a pointer can alias Null. Our program transformation is based on Global Value Number- ing, a scheme inspired from compiler optimization literature. It allows even a flow-insensitive analysis to make use of branch conditions such as checking if a pointer is Null and gain precision. We perform experiments on real-world code and show that the transformation improves precision (in terms of the number of dereferences proved safe) from 86.56% to 98.05%, while incurring a small overhead in the running time. Keywords: Alias Analysis, Global Value Numbering, Static Single As- signment, Null Pointer Analysis 1 Introduction Detecting and eliminating null-pointer exceptions is an important step towards developing reliable systems. Static analysis tools that look for null-pointer ex- ceptions typically employ techniques based on alias analysis to detect possible aliasing between pointers. Two pointer-valued variables are said to alias if they hold the same memory location during runtime. Statically, aliasing can be de- cided in two ways: (a) may-alias [1], where two pointers are said to may-alias if they can point to the same memory location under some possible execution, and (b) must-alias [27], where two pointers are said to must-alias if they always point to the same memory location under all possible executions. -
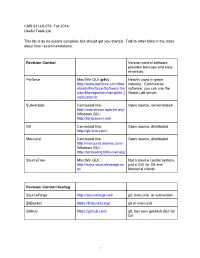
Useful Tools for Game Making
CMS.611J/6.073 Fall 2014 Useful Tools List This list is by no means complete, but should get you started. Talk to other folks in the class about their recommendations. Revision Control Version control software, provides backups and easy reversion. Perforce Mac/Win GUI (p4v): Heavily used in game http://www.perforce.com/dow industry. Commercial nloads/Perforce-Software-Ver software; you can use the sion-Management/complete_l Game Lab server. ist/Customer Subversion Command line: Open source, server-based http://subversion.apache.org/ Windows GUI: http://tortoisesvn.net/ Git Command line: Open source, distributed http://git-scm.com/ Mercurial Command line: Open source, distributed http://mercurial.selenic.com/ Windows GUI: http://tortoisehg.bitbucket.org/ SourceTree Mac/Win GUI: Not a source control system, http://www.sourcetreeapp.co just a GUI for Git and m/ Mercurial clients Revision Control Hosting SourceForge http://sourceforge.net/ git, mercurial, or subversion BitBucket https://bitbucket.org/ git or mercurial GitHub https://github.com/ git, has own (painful) GUI for Git 1 Image Editing MSPaint Windows, pre-installed Surprisingly useful quick pixel art editor (esp for prototypes) Paint.NET Windows, About as easy as MSPaint, but http://www.getpaint.net/download much more powerful .html Photoshop Mac, Windows New Media Center, 26-139 GIMP Many platforms, Easier than photoshop, at http://www.gimp.org/downloads/ least. Sound GarageBand Mac New Media Center, 26-139 Audacity Many platforms, Free, open source. http://audacity.sourceforge.ne -

Return of Organization Exempt from Income
OMB No. 1545-0047 Return of Organization Exempt From Income Tax Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) Open to Public Department of the Treasury Internal Revenue Service The organization may have to use a copy of this return to satisfy state reporting requirements. Inspection A For the 2011 calendar year, or tax year beginning 5/1/2011 , and ending 4/30/2012 B Check if applicable: C Name of organization The Apache Software Foundation D Employer identification number Address change Doing Business As 47-0825376 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 1901 Munsey Drive (909) 374-9776 Terminated City or town, state or country, and ZIP + 4 Amended return Forest Hill MD 21050-2747 G Gross receipts $ 554,439 Application pending F Name and address of principal officer: H(a) Is this a group return for affiliates? Yes X No Jim Jagielski 1901 Munsey Drive, Forest Hill, MD 21050-2747 H(b) Are all affiliates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( ) (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: http://www.apache.org/ H(c) Group exemption number K Form of organization: X Corporation Trust Association Other L Year of formation: 1999 M State of legal domicile: MD Part I Summary 1 Briefly describe the organization's mission or most significant activities: to provide open source software to the public that we sponsor free of charge 2 Check this box if the organization discontinued its operations or disposed of more than 25% of its net assets.