A Framework for Multilingual Information Processing by Steven Edward Atkin Bachelor of Science Physics State University of New Y
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cumberland Tech Ref.Book
Forms Printer 258x/259x Technical Reference DRAFT document - Monday, August 11, 2008 1:59 pm Please note that this is a DRAFT document. More information will be added and a final version will be released at a later date. August 2008 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or other countries. © 2008 Lexmark International, Inc. All rights reserved. 740 West New Circle Road Lexington, Kentucky 40550 Draft document Edition: August 2008 The following paragraph does not apply to any country where such provisions are inconsistent with local law: LEXMARK INTERNATIONAL, INC., PROVIDES THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions; therefore, this statement may not apply to you. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in later editions. Improvements or changes in the products or the programs described may be made at any time. Comments about this publication may be addressed to Lexmark International, Inc., Department F95/032-2, 740 West New Circle Road, Lexington, Kentucky 40550, U.S.A. In the United Kingdom and Eire, send to Lexmark International Ltd., Marketing and Services Department, Westhorpe House, Westhorpe, Marlow Bucks SL7 3RQ. Lexmark may use or distribute any of the information you supply in any way it believes appropriate without incurring any obligation to you. -

AMPERSAND an International Journal of General and Applied Linguistics
AMPERSAND An International Journal of General and Applied Linguistics AUTHOR INFORMATION PACK TABLE OF CONTENTS XXX . • Description p.1 • Abstracting and Indexing p.2 • Editorial Board p.2 • Guide for Authors p.4 ISSN: 2215-0390 DESCRIPTION . Serving the breadth of the general and applied linguistics communities, Ampersand offers a highly- visible, open-access home for authors. An international, peer-reviewed journal, Ampersand welcomes submissions in applied and historical linguistics, phonetics, phonology, pragmatics, semantics, sociolinguistics and syntax. Ampersand provides authors with an open-access venue to disseminate a wide range of linguistic research in an equally wide range of formats, prioritizing rapid peer review and publication so that researchers can share their work in its most current and innovative form. In response to the global thrust toward open source, open data and open access in science, Ampersand offers the opportunity for authors to make their research freely available to everyone, opening their work to a wider audience and increased readership. Ampersand caters to a comprehensive audience, ranging from language researchers, linguists, teachers, educationalists, practitioners to those with a general interest in language and linguistics. The journal aims to encourage the free exchange of information between researchers by being a forum for the constructive discussion and debate of issues in both theoretical and applied research. The journal welcomes all types of submission format: traditional 'full' research articles, short communications, opinion pieces, book reviews, case studies and literature reviews. Ampersand also offers the opportunity to publish special issues or sections to reflect current interest and research in topical or developing areas. The journal fully supports authors wanting to present their research in an innovative fashion through the use of modern multimedia in the award-winning 'article of the future' format on ScienceDirect?. -
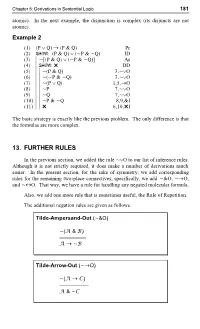
Tilde-Arrow-Out (~→O)
Chapter 5: Derivations in Sentential Logic 181 atomic). In the next example, the disjunction is complex (its disjuncts are not atomic). Example 2 (1) (P ´ Q) → (P & Q) Pr (2) •: (P & Q) ∨ (~P & ~Q) ID (3) |~[(P & Q) ∨ (~P & ~Q)] As (4) |•: ¸ DD (5) ||~(P & Q) 3,~∨O (6) ||~(~P & ~Q) 3,~∨O (7) ||~(P ∨ Q) 1,5,→O (8) ||~P 7,~∨O (9) ||~Q 7,~∨O (10) ||~P & ~Q 8,9,&I (11) ||¸ 6,10,¸I The basic strategy is exactly like the previous problem. The only difference is that the formulas are more complex. 13. FURTHER RULES In the previous section, we added the rule ~∨O to our list of inference rules. Although it is not strictly required, it does make a number of derivations much easier. In the present section, for the sake of symmetry, we add corresponding rules for the remaining two-place connectives; specifically, we add ~&O, ~→O, and ~↔O. That way, we have a rule for handling any negated molecular formula. Also, we add one more rule that is sometimes useful, the Rule of Repetition. The additional negation rules are given as follows. Tilde-Ampersand-Out (~&O) ~(d & e) ––––––––– d → ~e Tilde-Arrow-Out (~→O) ~(d → f) –––––––––– d & ~f 182 Hardegree, Symbolic Logic Tilde-Double-Arrow-Out (~±O) ~(d ± e) –––––––––– ~d ± e The reader is urged to verify that these are all valid argument forms of sentential logic. There are other valid forms that could serve equally well as the rules in question. The choice is to a certain arbitrary. The advantage of the particular choice becomes more apparent in a later chapter on predicate logic. -

INTERSKILL MAINFRAME QUARTERLY December 2011
INTERSKILL MAINFRAME QUARTERLY December 2011 Retaining Data Center Skills Inside This Issue and Knowledge Retaining Data Center Skills and Knowledge 1 Interskill Releases - December 2011 2 By Greg Hamlyn Vendor Briefs 3 This the final chapter of this four part series that briefly Taking Care of Storage 4 explains the data center skills crisis and the pros and cons of Learning Spotlight – Managing Projects 5 implementing a coaching or mentoring program. In this installment we will look at some of the steps to Tech-Head Knowledge Test – Utilizing ISPF 5 implementing a program such as this into your data center. OPINION: The Case for a Fresh Technical If you missed these earlier installments, click the links Opinion 6 below. TECHNICAL: Lost in Translation Part 1 - EBCDIC Code Pages 7 Part 1 – The Data Center Skills Crisis MAINFRAME – Weird and Unusual! 10 Part 2 – How Can I Prevent Skills Loss in My Data Center? Part 3 – Barriers to Implementing a Coaching or Mentoring Program should consider is the GROW model - Determine whether an external consultant should be Part Four – Implementing a Successful Coaching used (include pros and cons) - Create a basic timeline of the project or Mentoring Program - Identify how you will measure the effectiveness of the project The success of any project comes down to its planning. If - Provide some basic steps describing the coaching you already believe that your data center can benefit from and mentoring activities skills and knowledge transfer and that coaching and - Next phase if the pilot program is deemed successful mentoring will assist with this, then outlining a solid (i.e. -

Proposal to Add U+2B95 Rightwards Black Arrow to Unicode Emoji
Proposal to add U+2B95 Rightwards Black Arrow to Unicode Emoji J. S. Choi, 2015‐12‐12 Abstract In the Unicode Standard 7.0 from 2014, ⮕ U+2B95 was added with the intent to complete the family of black arrows encoded by ⬅⬆⬇ U+2B05–U+2B07. However, due to historical timing, ⮕ U+2B95 was not yet encoded when the Unicode Emoji were frst encoded in 2009–2010, and thus the family of four emoji black arrows were mapped not only to ⬅⬆⬇ U+2B05–U+2B07 but also to ➡ U+27A1—a compatibility character for ITC Zapf Dingbats—instead of ⮕ U+2B95. It is thus proposed that ⮕ U+2B95 be added to the set of Unicode emoji characters and be given emoji‐ and text‐style standardized variants, in order to match the properties of its siblings ⬅⬆⬇ U+2B05–U+2B07, with which it is explicitly unifed. 1 Introduction Tis document primarily discusses fve encoded characters, already in Unicode as of 2015: ⮕ U+2B95 Rightwards Black Arrow: Te main encoded character being discussed. Located in the Miscellaneous Symbols and Arrows block. ⬅⬆⬇ U+2B05–U+2B07 Leftwards, Upwards, and Downwards Black Arrow: Te three black arrows that ⮕ U+2B95 completes. Also located in the Miscellaneous Symbols and Arrows block. ➡ U+27A1 Black Rightwards Arrow: A compatibility character for ITC Zapf Dingbats. Located in the Dingbats block. Tis document proposes the addition of ⮕ U+2B95 to the set of emoji characters as defned by Unicode Technical Report (UTR) #51: “Unicode Emoji”. In other words, it proposes: 1. A property change: ⮕ U+2B95 should be given the Emoji property defned in UTR #51. -

Dictation Presentation.Pptx
Dictaon using Apple Devices Presentaon October 10, 2013 Trudy Downs Operang Systems • iOS6 • iOS7 • Mountain Lion (OS X10.8) Devices • iPad 3 or iPad mini • iPod 4 • iPhone 4s, 5 or 5c or 5s • Desktop running Mountain Lion • Laptop running Mountain Lion Dictaon Shortcut Words • Shortcut WordsDictaon includes many voice “shortcuts” that allows you to manipulate the text and insert symbols while you are speaking. Here’s a list of those shortcuts that you can use: - “new line” is like pressing Return on your keyboard - “new paragraph” creates a new paragraph - “cap” capitalizes the next spoken word - “caps on/off” capitalizes the spoken sec&on of text - “all caps” makes the next spoken word all caps - “all caps on/off” makes the spoken sec&on of text all caps - “no caps” makes the next spoken word lower case - “no caps on/off” makes the spoken sec&on of text lower case - “space bar” prevents a hyphen from appearing in a normally hyphenated word - “no space” prevents a space between words - “no space on/off” to prevent a sec&on of text from having spaces between words More Dictaon Shortcuts • - “period” or “full stop” places a period at the end of a sentence - “dot” places a period anywhere, including between words - “point” places a point between numbers, not between words - “ellipsis” or “dot dot dot” places an ellipsis in your wri&ng - “comma” places a comma - “double comma” places a double comma (,,) - “quote” or “quotaon mark” places a quote mark (“) - “quote ... end quote” places quotaon marks around the text spoken between - “apostrophe” -

Ill[S ADJUSTMENTS
B249 DATA TRANSMISSION CONTROL UNIT INTRODUCTION AND OPERATION Burroughs FUNCTIONAL DETAIL FIELD ENGINEERING CIRCUIT DETAIL lJrn~[}{] ~ D~ill[s ADJUSTMENTS MAINTENANCE ~ ill ~ OD ill [S PROCEDURES INST ALLAT ION PROCEDURES RELIABILITY IMPROVEMENT NOTICES OPTIONAL FEATURES MODIFICATIONS (BRANCH LIBRARIES) Printed in U.S. America 9-15-66 Form 1026259 Burroughs - B249 Data Transmission ~echnical Manual I N D E X INTRODUCTION & OPERATION - SECTION I Page No. B249 Data Transmission Control Unit - General Descript ion . 1 Glossary - Data Transmission Terminal Unit and MCU. 5 Glossary - DTCU & System . 3 Physical De$cr1ption . 2 FUNCTIONAL DETAIL - SECTION II B300 Active Interrogate. · . · . · · 57 B300 Data Communications Read. · · . · · · · 62 B300 Data Communications Write · · . 78 B300 Passive Interrogate · · 49 VB300 Passive Interrogate - ITU (B486) Mode · . 92 v13300 Read - ITU (B486) Mode. · · . · · . · . 95 V'B300 Write - ITU (13486) Mode · · . · · 108 B5500 Data Communications Interrogate. · . 1 B5500 Data Communications Read . · 9 B5500 Data Communications Write. · 21 CIRCUIT DETAIL - SECTION III "AU Register Load - (Normal & Reverse) 1 Clock Control. ... 11 Scan . 3 Translator . 4 ADJUSTMENTS - SECTION IV Clock Adjustments ..... 1 Variable Bias Adjustment . 1 MAINTENANCE PROCEDURES - SECTION V Maintenance Panel ... 1 INSTALLATION PROCEDURES - SECTION VI DTCU Installation. 1 Pluggable Options. 2 Power ON . 3 Special Inquiry Terminal Connection .. 2 NOTE: Pages for Sections VII, VIII and IX will be furnished when applicable. Printed in U. S. America Revised 4/1/67 For Form 1026259 Burroughs - B249 Data Transmission Technical Manual Sec, I Page 1 Introduction & Operation B249 DATA TRANSMISSION CONTROL UNIT - GENERAL DESCRIPTION The B249 DTCU is required when: 1. More than one B487 DTTU is used on a single Processing System. -

Relink Eo 3-11-97
CHAPTER 1 COMMUNICATIONS As an Aviation Electronics Technician, you will be communication circuits. These operations are accom- tasked to operate and maintain many different types of plished through the use of compatible and flexible airborne communications equipment. These systems communication systems. may differ in some respects, but they are similar in many Radio is the most important means of com- ways. As an example, there are various models of AM municating in the Navy today. There are many methods radios, yet they all serve the same function and operate of transmitting in use throughout the world. This manual on the same basic principles. It is beyond the scope of will discuss three types. They are radiotelegraph, this manual to discuss each and every model of radiotelephone, and teletypewriter. communication equipment used on naval aircraft; therefore, only representative systems will be discussed. Every effort has been made to use not only systems that Radiotelegraph are common to many of the different platforms, but also have not been used in the other training manuals. It is Radiotelegraph is commonly called CW (con- the intent of this manual to have systems from each and tinuous wave) telegraphy. Telegraphy is accomplished every type of aircraft in use today. by opening and closing a switch to separate a continuously transmitted wave. The resulting “dots” and “dashes” are based on the Morse code. The major RADIO COMMUNICATIONS disadvantage of this type of communication is the relatively slow speed and the need for experienced Learning Objective: Recognize the various operators at both ends. types of radio communications. -

Programmer's Manual SP2000 Series
Dot Matrix Printer SP2000 Series Programmer’s Manual TABLE OF CONTENTS 1. Control Codes (Star Mode) ......................................................................... 1 1-1. Control Codes List .............................................................................. 1 1-1-1. Character Selection .................................................................. 1 1-1-2. Print Position Control ............................................................... 3 1-1-3. Dot Graphics Control ............................................................... 4 1-1-4. Download Graphics Printing .................................................... 4 1-1-5. Peripheral Device Control ........................................................ 4 1-1-6. Auto Cutter Control (SP2500 type printers only) .................... 5 1-1-7. Commands to Set the Page Format .......................................... 5 1-1-8. Other Commands...................................................................... 6 1-2. Control Code Details ........................................................................... 7 1-2-1. Character Selection .................................................................. 7 1-2-2. Print Position Control ............................................................. 17 1-2-3. Dot Graphics Control ............................................................. 25 1-2-4. Download Graphics Printing .................................................. 28 1-2-5. Peripheral Device Control ..................................................... -

IGP® / VGL Emulation Code V™ Graphics Language Programmer's Reference Manual Line Matrix Series Printers
IGP® / VGL Emulation Code V™ Graphics Language Programmer’s Reference Manual Line Matrix Series Printers Trademark Acknowledgements IBM and IBM PC are registered trademarks of the International Business Machines Corp. HP and PCL are registered trademarks of Hewlett-Packard Company. IGP, LinePrinter Plus, PSA, and Printronix are registered trademarks of Printronix, LLC. QMS is a registered trademark and Code V is a trademark of Quality Micro Systems, Inc. CSA is a registered certification mark of the Canadian Standards Association. TUV is a registered certification mark of TUV Rheinland of North America, Inc. UL is a registered certification mark of Underwriters Laboratories, Inc. This product uses Intellifont Scalable typefaces and Intellifont technology. Intellifont is a registered trademark of Agfa Division, Miles Incorporated (Agfa). CG Triumvirate are trademarks of Agfa Division, Miles Incorporated (Agfa). CG Times, based on Times New Roman under license from The Monotype Corporation Plc is a product of Agfa. Printronix, LLC. makes no representations or warranties of any kind regarding this material, including, but not limited to, implied warranties of merchantability and fitness for a particular purpose. Printronix, LLC. shall not be held responsible for errors contained herein or any omissions from this material or for any damages, whether direct, indirect, incidental or consequential, in connection with the furnishing, distribution, performance or use of this material. The information in this manual is subject to change without notice. This document contains proprietary information protected by copyright. No part of this document may be reproduced, copied, translated or incorporated in any other material in any form or by any means, whether manual, graphic, electronic, mechanical or otherwise, without the prior written consent of Printronix, LLC. -

Ascii, Baudot, and the Radio Amateur
ASCII, BAUDOT AND THE RADIO AMATEUR George W. Henry, Jr. K9GWT Copyright © 1980by Hal Communications Corp., Urbana, Illinois HAL COMMUNICATIONS CORP. BOX365 ASCII, BAUDOT, AND THE RADIO AMATEUR The 1970's have brought a revolution to amateur radio RTTY equipment separate wire to and from the terminal device. Such codes are found in com and techniques, the latest being the addition of the ASCII computer code. mon use with computer and line printer devices. Radio amateurs in the Effective March 17, 1980, radio amateurs in the United States have been United States are currently authorized to use either the Baudot or ASCII authorized by the FCC to use the American Standard Code for Information serial asynchronous TTY codes. Interchange(ASCII) as well as the older "Baudot" code for RTTY com munications. This paper discusses the differences between the two codes, The Baudot TTY Code provides some definitions for RTTY terms, and examines the various inter facing standards used with ASCII and Baudot terminals. One of the first data codes used with mechanical printing machines uses a total of five data pulses to represent the alphabet, numerals, and symbols. Constructio11 of RTTY Codes This code is commonly called the Baudot or Murray telegraph code after the work done by these two pioneers. Although commonly called the Baudot Mark Ull s,.ce: code in the United States, a similar code is usually called the Murray code in other parts of the world and is formally defined as the International Newcomers to amateur radio RTTY soon discover a whole new set of terms, Telegraphic Alphabet No. -

JFP Reference Manual 5 : Standards, Environments, and Macros
JFP Reference Manual 5 : Standards, Environments, and Macros Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 817–0648–10 December 2002 Copyright 2002 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. Sun holds a non-exclusive license from Xerox to the Xerox Graphical User Interface, which license also covers Sun’s licensees who implement OPEN LOOK GUIs and otherwise comply with Sun’s written license agreements.