Ns-3 Tutorial Release Ns-3.22
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Easy Slackware
1 Создание легкой системы на базе Slackware I - Введение Slackware пользуется заслуженной популярностью как классический linux дистрибутив, и поговорка "кто знает Red Hat тот знает только Red Hat, кто знает Slackware тот знает linux" несмотря на явный снобизм поклонников "бога Патре га" все же имеет под собой основания. Одним из преимуществ Slackware является возможность простого создания на ее основе практически любой системы, в том числе быстрой и легкой десктопной, о чем далее и пойдет речь. Есть дис трибутивы, клоны Slackware, созданные именно с этой целью, типа Аbsolute, но все же лучше создавать систему под себя, с максимальным учетом именно своих потребностей, и Slackware пожалуй как никакой другой дистрибутив подходит именно для этой цели. Легкость и быстрота системы определяется выбором WM (DM) , набором программ и оптимизацией программ и системы в целом. Первое исключает KDE, Gnome, даже новые версии XFCЕ, остается разве что LXDE, но набор программ в нем совершенно не устраивает. Оптимизация наиболее часто используемых про грамм и нескольких базовых системных пакетов осуществляется их сборкой из сорцов компилятором, оптимизированным именно под Ваш комп, причем каж дая программа конфигурируется исходя из Ваших потребностей к ее возможно стям. Оптимизация системы в целом осуществляется ее настройкой согласно спе цифическим требованиям к десктопу. Такой подход был выбран по банальной причине, возиться с gentoo нет ни какого желания, комп все таки создан для того чтобы им пользоваться, а не для компиляции программ, в тоже время у каждого есть минимальный набор из не большого количества наиболее часто используемых программ, на которые стоит потратить некоторое, не такое уж большое, время, чтобы довести их до ума. Кро ме того, такой подход позволяет иметь самые свежие версии наиболее часто ис пользуемых программ. -

Insight MFR By
Manufacturers, Publishers and Suppliers by Product Category 11/6/2017 10/100 Hubs & Switches ASCEND COMMUNICATIONS CIS SECURE COMPUTING INC DIGIUM GEAR HEAD 1 TRIPPLITE ASUS Cisco Press D‐LINK SYSTEMS GEFEN 1VISION SOFTWARE ATEN TECHNOLOGY CISCO SYSTEMS DUALCOMM TECHNOLOGY, INC. GEIST 3COM ATLAS SOUND CLEAR CUBE DYCONN GEOVISION INC. 4XEM CORP. ATLONA CLEARSOUNDS DYNEX PRODUCTS GIGAFAST 8E6 TECHNOLOGIES ATTO TECHNOLOGY CNET TECHNOLOGY EATON GIGAMON SYSTEMS LLC AAXEON TECHNOLOGIES LLC. AUDIOCODES, INC. CODE GREEN NETWORKS E‐CORPORATEGIFTS.COM, INC. GLOBAL MARKETING ACCELL AUDIOVOX CODI INC EDGECORE GOLDENRAM ACCELLION AVAYA COMMAND COMMUNICATIONS EDITSHARE LLC GREAT BAY SOFTWARE INC. ACER AMERICA AVENVIEW CORP COMMUNICATION DEVICES INC. EMC GRIFFIN TECHNOLOGY ACTI CORPORATION AVOCENT COMNET ENDACE USA H3C Technology ADAPTEC AVOCENT‐EMERSON COMPELLENT ENGENIUS HALL RESEARCH ADC KENTROX AVTECH CORPORATION COMPREHENSIVE CABLE ENTERASYS NETWORKS HAVIS SHIELD ADC TELECOMMUNICATIONS AXIOM MEMORY COMPU‐CALL, INC EPIPHAN SYSTEMS HAWKING TECHNOLOGY ADDERTECHNOLOGY AXIS COMMUNICATIONS COMPUTER LAB EQUINOX SYSTEMS HERITAGE TRAVELWARE ADD‐ON COMPUTER PERIPHERALS AZIO CORPORATION COMPUTERLINKS ETHERNET DIRECT HEWLETT PACKARD ENTERPRISE ADDON STORE B & B ELECTRONICS COMTROL ETHERWAN HIKVISION DIGITAL TECHNOLOGY CO. LT ADESSO BELDEN CONNECTGEAR EVANS CONSOLES HITACHI ADTRAN BELKIN COMPONENTS CONNECTPRO EVGA.COM HITACHI DATA SYSTEMS ADVANTECH AUTOMATION CORP. BIDUL & CO CONSTANT TECHNOLOGIES INC Exablaze HOO TOO INC AEROHIVE NETWORKS BLACK BOX COOL GEAR EXACQ TECHNOLOGIES INC HP AJA VIDEO SYSTEMS BLACKMAGIC DESIGN USA CP TECHNOLOGIES EXFO INC HP INC ALCATEL BLADE NETWORK TECHNOLOGIES CPS EXTREME NETWORKS HUAWEI ALCATEL LUCENT BLONDER TONGUE LABORATORIES CREATIVE LABS EXTRON HUAWEI SYMANTEC TECHNOLOGIES ALLIED TELESIS BLUE COAT SYSTEMS CRESTRON ELECTRONICS F5 NETWORKS IBM ALLOY COMPUTER PRODUCTS LLC BOSCH SECURITY CTC UNION TECHNOLOGIES CO FELLOWES ICOMTECH INC ALTINEX, INC. -

List of Applications Updated in ARL #2581
List of Applications Updated in ARL #2581 Application Name Publisher .NET Core Runtime 3.0 Preview Microsoft .NET Core Toolset 3.1 Preview Microsoft .NET Framework 4.5 Microsoft .NET Framework 4.6 Microsoft .NET Framework Developer Pack 4.7 Microsoft .NET Framework Multi-Targeting Pack for Windows Store Apps 4.5 RC Microsoft .NET Framework SDK 4.8 Microsoft _connect.BRAIN 4.8 Bizerba 2200 TapeStation Software 3.1 Agilent Technologies 2200 TapeStation Software 3.2 Agilent Technologies 24x7 Automation Suite 3.6 SoftTree Technologies 3500 Rack Configuration Software 6.0 Bently Nevada 365 16.0 Microsoft 3D Sprint 2.10 3D Systems 3D Sprint 2.11 3D Systems 3D Sprint 2.12 3D Systems 3D Viewer Microsoft 3PAR Host Explorer VMware 4.0 HP 4059 Extended Edition Attendant Console 2.1 ALE International 4uKey 1.4 Tenorshare 4uKey 1.6 Tenorshare 4uKey 2.2 Tenorshare 50 Accounts 21.0 Sage Group 50 Accounts 25.1 Sage Group 793 Controller Software 5.8 MTS Systems 793 Controller Software 5.9 MTS Systems 793 Controller Software 6.1 MTS Systems 7-Zip 19.00 Igor Pavlov ABAQUS 2018 Student Dassault Systemes ABAQUS 2019 Student Dassault Systemes Abstract 73.0 Elastic Projects ABU Service 14.10 Teradata Access Client 3.5 Barracuda Networks Access Client 3.7 Barracuda Networks Access Client 4.1 Barracuda Networks Access Module for Azure 15.1 Teradata Access Security Gateway (ASG) Soft Key Avaya AccuNest 10.3 Gerber Technology AccuNest 11.0 Gerber Technology ACDSee 2.3 Free ACD Systems ACDSee 2.4 Free ACD Systems ACDSee Photo Studio 2019 Professional ACD Systems -

List of New Applications Added in ARL #2590
List of new applications added in ARL #2590 Application Name Publisher excel add-in 3 1010data 1042-S Pro 2020 Professional 1099 Pro SyncBackSE 9.4 2BrightSparks TaxACT 2016 2nd Story Software CaseViewer 2.4 3DHISTECH Work for Desktop 7.2 8x8 Drive composer pro ABB HMI500 8.3 ABB RES670 2.0 ABB RET620 IED Connectivity Package 2.1 ABB MineScape SDK 7.0 ABB REX640 IED Connectivity Package 1.0 ABB FineReader Server 14.0 ABBYY PC-ACE Pro32 4.1 ABILITY Network PC-ACE Pro32 3.1 ABILITY Network PC-ACE Pro32 3.7 ABILITY Network PC-ACE Pro32 3.9 ABILITY Network PC-ACE Pro32 2.8 ABILITY Network PC-ACE Pro32 3.4 ABILITY Network PrizmDoc Client 13.1 AccuSoft PrizmDoc Client 12.3 AccuSoft iPhone Screen Recorder 1.3 ACE THINKER AcornPipe 8.7 Acorn Pipe Systems Experience Analytics Connect for Data Analysis 8.7 Acoustic True Image for Western Digital Acronis Serial Port Component 3.2 ActiveXperts ONYX 4.4 ADJ Products Creative Cloud 1.0 Adobe eLearning Assets 9.0 Adobe FSP Network Manager ADVA Optical Networking AEMtuner 3.2 AEM Performance Electronics OpenLab ECM 3.6 Agilent Technologies MassHunter Mass Profiler Professional Agilent Technologies OpenLab ECM Client 3.3 Agilent Technologies Screen Recorder 2.2 Aiseesoft Studio CC supervision ALE International DataPrint 1.0 Altec Altium Designer 21.0 Altium Altium NEXUS 4.0 Altium DatabaseSpy 2021 Enterprise Altova MeetingMatrix 7.4 Amadeus Amazon Web Services Amazon Rheocalc 3.3 AMETEK Rheocalc 3.1 AMETEK Rheocalc AMETEK Rheocalc 3.2 AMETEK Powerpoint Addin 1.5 Anaplan Powerpoint Add in 1.6 Anaplan Backupper -

Open Source Software Organizations
SYLLABUS-SEMESTER 4TH (CBCS) - B.A/B.SC COMPUTER APPLICATIONS (SKILL ENHANCEMENT COURSE- THEORY) COURSE CODE: 1CAPSE0401 COURSE TITLE: OPEN SOURCE SOFTWARE (Syllabus wise Topic Description) UNIT-5: OPEN SOURCE SOFTWARE ORGANIZATIONS Open source software organizations The following are notable organizations devoted to the advocacy, legal aid, financial aid, technical aid, governance, etc. of free and open-source software (FOSS) as a whole, or of one or more specific FOSS projects. For projects that have their own foundation or are part of an umbrella organization, the primary goal is often to provide a mechanism for funding development of the software. For the most part, these organizations are structured as nonprofit/charity organizations. There are quite a number of not-for-profit and charitable organizations supporting the open source software movement. These are some you should know about: 1. Apache Software Foundation The Apache Software Foundation provides organizational, legal, and financial support for a broad range of open source software projects. The foundation provides an established framework for intellectual property and financial contributions that simultaneously limits contributors' potential legal exposure. 2. Cloud Native Computing Foundation The Cloud Native Computing Foundation's (CNCF) mission is to promote adoption of distributed computing and "cloud-native" systems, which it defines as being container packaged, dynamically managed, and micro services oriented. A project of the Linux Foundation, CNCF hosts the Kubernetes cloud orchestration system and other cloud-native open source projects. 3. Digital Freedom Foundation Digital Freedom Foundation sponsors annual events to promote free software, hardware, and content. Its events are Software Freedom Day, Document Freedom Day, Hardware Freedom Day, and Education Freedom Day. -
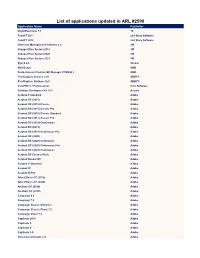
List of Applications Updated in ARL #2590
List of applications updated in ARL #2590 Application Name Publisher NightWatchman 7.1 1E TaxACT 2017 2nd Story Software TaxACT 2018 2nd Story Software Detection Management Software 2.4 3M Grouper Plus System 2018 3M Grouper Plus System 2020 3M Grouper Plus System 2021 3M Sync2 2.8 4Team MineScape ABB Protection and Control IED Manager PCM600 2 ABB FlexiCapture Servers 12.0 ABBYY FlexiCapture Stations 12.0 ABBYY CutePDF 3.7 Professional Acro Software Software Developers Kit 10.1 Acuant Acrobat 9 Standard Adobe Acrobat DC (2015) Adobe Acrobat DC (2015) Classic Adobe Acrobat DC (2015) Classic Pro Adobe Acrobat DC (2015) Classic Standard Adobe Acrobat DC (2017) Classic Pro Adobe Acrobat DC (2018) Continuous Adobe Acrobat DC (2019) Adobe Acrobat DC (2019) Continuous Pro Adobe Acrobat DC (2020) Adobe Acrobat DC (2020) Continuous Adobe Acrobat DC (2020) Continuous Pro Adobe Acrobat DC (2021) Continuous Adobe Acrobat DC (Unspecified) Adobe Acrobat Reader DC Adobe Acrobat X Standard Adobe Acrobat XI Adobe Acrobat XI Pro Adobe After Effects CC (2018) Adobe After Effects CC (2020) Adobe Animate CC (2018) Adobe Audition CC (2018) Adobe Campaign 6.0 Adobe Campaign 7.0 Adobe Campaign Classic Client 6.1 Adobe Campaign Classic Client 7.0 Adobe Campaign Client 7.0 Adobe Captivate 2019 Adobe Captivate 5 Adobe Captivate 6 Adobe Captivate 9.0 Adobe Character Animator 1.0 Adobe Connect 2020.10 Adobe Creative Cloud Client 1.0 Adobe Creative Suite CS6 Master Collection Adobe Design & Web Premium CS6 Adobe Dimension 3.4 Adobe Dreamweaver CS6 Adobe Flash Builder -

BUILDING a MONITORING INFRASTRUCTURE with NAGIOS This Page Intentionally Left Blank BUILDING a MONITORING INFRASTRUCTURE with NAGIOS
www.dbeBooks.com - An Ebook Library BUILDING A MONITORING INFRASTRUCTURE WITH NAGIOS This page intentionally left blank BUILDING A MONITORING INFRASTRUCTURE WITH NAGIOS David Josephsen Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris Madrid • Cape Town • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trade- marks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the des- ignations have been printed with initial capital letters or in all capitals. The author and publisher have taken care in the preparation of this book, but make no expressed or implied war- ranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. The publisher offers excellent discounts on this book when ordered in quantity for bulk purchases or special sales, which may include electronic versions and/or custom covers and content particular to your business, training goals, marketing focus, and branding interests. For more information, please contact: U.S. Corporate and Government Sales (800) 382-3419 [email protected] For sales outside the United States please contact: International Sales [email protected] This Book Is Safari Enabled The Safari® Enabled icon on the cover of your favorite technology book means the book is available through Safari Bookshelf. When you buy this book, you get free access to the online edition for 45 days. -

Information Security
A SA Research Information Security J. Carlton Collins ASA Research - Atlanta, Georgia 770.734.0950 [email protected] Information Security Table of Contents Chapter Chapter Title & Page Count Page Number 1 Locks ‐ (2 Pages) 6 2 Government Compliance ‐ (3 Pages) 8 3 Securing Hard Drives and Laptop Computers ‐ (16 Pages) 11 4 Encryption ‐ (12 Pages) 27 5 Strong Passwords ‐ (7 Pages) 39 6 Windows ‐ Files and Folders ‐ (8 Pages) 46 7 System Restore ‐ (3 Pages) 54 8 Firewalls ‐ (7 Pages) 57 9 Wireless Security ‐ (8 Pages) 64 10 Checking the Security of your PC ‐ (4 Pages) 72 11 Online Security Tests ‐ (3 Pages) 76 12 Windows ‐ User Accounts & Groups ‐ (6 Pages) 79 13 Windows ‐ Screen Savers ‐ (4 Pages) 85 14 Pornography ‐ (4 Pages) 89 15 Sample Contracts ‐ (9 Pages) 93 16 Computer Bread Crumbs ‐ (6 Pages) 102 17 Computer Disposal ‐ (5 Pages) 108 18 Backup Strategy ‐ (14 Pages) 113 19 Viruses ‐ (6 Pages) 127 20 Phishing ‐ (7 Pages) 133 21 Spy Stuff ‐ (14 Pages) 140 22 Privacy Test ‐ (6 Pages) 154 23 Fake IDs ‐ (7 Pages) 160 24 National ID Cards ‐ (4 Pages) 167 25 Fake Social Security Cards ‐ (5 Pages) 171 26 Identity Theft ‐ (14 Pages) 176 27 Employee Theft ‐ (6 Pages) 190 28 Background Checks ‐ (5 Pages) 196 29 Bonding Employees ‐ (3 Pages) 201 30 Asterisk Key ‐ (2 Pages) 204 31 Encryption Analyzer & Passware ‐ (3 Pages) 206 32 Securing Desktop Computers ‐ (3 Pages) 209 33 Windows ‐ Windows Services ‐ (6 Pages) 212 34 Risk of Fire ‐ (3 Pages) 218 35 Credit Card Fraud ‐ (11 Pages) 221 36 Counterfeit Money ‐ (9 Pages) 232 37 Cracking and -

Archivace Dat Pomocí Počítačové Sítě
VYSOKÁ ŠKOLA BÁŇSKÁ - TECHNICKÁ UNIVERZITA OSTRAVA Hornicko-geologická fakulta Institut ekonomiky a systémů řízení Archivace dat pomocí počítačové sítě bakalářská práce Autor: Christian Rappersberger Vedoucí bakalářské práce: Ing. Vladislav Vančura, Ph.D Ostrava 2010 Prohlášení - Celou diplomovou práci včetně příloh, jsem vypracoval samostatně a uvedl jsem všechny použité podklady a literaturu. - Byl jsem seznámen s tím, že na moji bakalářskou práci se plně vztahuje zákon č.121/2000 Sb. - autorský zákon, zejména § 35 – využití díla v rámci občanských a náboženských obřadů, v rámci školních představení a využití díla školního a § 60 – školní dílo. - Beru na vědomí, že Vysoká škola báňská – Technická univerzita Ostrava (dále jen VŠB-TUO) má právo nevýdělečně, ke své vnitřní potřebě, diplomovou práci užít (§ 35 odst. 3). - Souhlasím s tím, že jeden výtisk diplomové práce bude uložen v Ústřední knihovně VŠB-TUO k prezenčnímu nahlédnutí a jeden výtisk bude uložen u vedoucího diplomové práce. Souhlasím s tím, že údaje o diplomové práci, obsažené v Záznamu o závěrečné práci, umístěném v příloze mé diplomové práce, budou zveřejněny v informačním systému VŠB-TUO. - Bylo sjednáno, že s VŠB-TUO, v případě zájmu z její strany, uzavřu licenční smlouvu s oprávněním užít dílo v rozsahu § 12 odst. 4 autorského zákona. - Bylo sjednáno, že užít své dílo – diplomovou práci nebo poskytnout licenci k jejímu využití mohu jen se souhlasem VŠB-TUO, která je oprávněna v takovém případě ode mne požadovat přiměřený příspěvek na úhradu nákladů, které byly VŠB-TUO na vytvoření díla vynaloženy. V Ostravě dne 24. 4. 2010 Christian Rappersberger Anotace V bakalářské práci je zpracován přehled i výběr dostupných programů zabývajících se archivací a synchronizací dat pomocí počítačové sítě. -

NF5466M5 Technical White Paper
NF5466M5 Technical White Paper Revision 1.0 Published on Dec. 27th, 2018 AS18000 User Manual Dear users, Thank you for choosing Inspur storage optimized server. This manual describes the product information of the storage optimized server and is intended to help you know and use it efficiently. Copyright © Inspur 2018. All Rights Reserved No part of this document shall be reproduced, modified or disclosed in any form or in any way without prior written consent of Inspur Group Co., Ltd. Trademark: Inspur “浪潮” and the Inspur logo belong to Inspur Group Co., Ltd. All the other trademarks and trade names mentioned in this document are the property of their respective holders. Notice: The products, services or features you purchase shall be bound by the commercial contracts and terms between you and Inspur Group. All or part of the products, services and features described in this document may not be available within your purchased product usage scope. Unless otherwise agreed in the contract, Inspur Group does not make any explicit or implicit statement or warranty on the content of this document. The information in this document is subject to change without notice. Unless otherwise agreed, this document will only be used as a guide, and all representations, information and recommendations in this document do not constitute any explicit or implicit warranty. For any question or suggestion, please contact Inspur Electronic Information Industry Co.,Ltd. Technical service 4008600011 number: Address: No. 1036 Langchao Road, Jinan, China Inspur Electronic Information Industry Co.,Ltd Postcode: 250101 i Proprietary and confidential information of Inspur Copyright © Inspur Electronic Information Industry Co.,Ltd NF5466M5 Technical White Paper Contents Contents ..................................................................................................................................................... -

Django and Mongodb
.bookmarks . 5 1.1 Development Cycle . 5 Creating and Deleting Indexes . 5 Diagnostic Tools . 5 Django and MongoDB . 5 Getting Started . 5 International Documentation . 6 Monitoring . 6 Older Downloads . 6 PyMongo and mod_wsgi . 6 Python Tutorial . 6 Recommended Production Architectures . 6 v0.8 Details . 7 Building SpiderMonkey . 7 Documentation . 7 Dot Notation . 8 Dot Notation . Getting the Software . 8 Language Support . 8 Mongo Administration Guide . 8 Working with Mongo Objects and Classes in Ruby . 8 MongoDB Language Support . 8 Community Info . 9 Internals . 9 TreeNavigation . 9 Old Pages . 9 Storing Data . 9 Indexes in Mongo . 10 HowTo . 10 Searching and Retrieving . 10 Locking . 10 Mongo Developers' Guide . 10 Locking in Mongo . 10 Mongo Database Administration . 10 Mongo Concepts and Terminology . 11 MongoDB - A Developer's Tour . 11 Updates . 11 Structuring Data for Mongo . 11 Design Overview . .. -

Quickbooks Desktop Mac 2020 User's Guide
QuickBooks Desktop Mac 2020 User’s Guide by E Lisette Gerald-Yamasaki, Haley Bell, and the QuickBooks Desktop Mac team Version 1 September 2019 Acknowledgments No single person can write a guide of this size and scope. I’d like to thank the other members of the QuickBooks for Mac team, especially Brooks Bell and Devon Hubbard. Also, this book is a generation of other guides that came before it. I’m very grateful for those guides. A super-special thank-you to Shelly King, without whom this guide would not exist. Copyright and trademarks Copyright © 2019 Intuit Inc. All rights reserved. No part of this publication may be reproduced in any form or by any means, without prior written permission of Intuit Inc., with the following exceptions: Any person is hereby authorized to store documentation on a single computer or device for personal use only, and to print copies of documentation for personal use, provided that the documentation contains Intuit’s copyright notice. Unauthorized reproduction is a violation of applicable laws. Intuit, the Intuit logo, QuickBooks, Quicken, and TurboTax, among others, are registered trademarks and/or registered service marks of Intuit Inc. Other parties’ marks are the property of their respective owners. Various QuickBooks products and services are protected by pending patents and by one or more of the following U.S. Patents: 5134564, 5423033, 5649115, 5842185, 5903881 and 6446048. Trademarks Intuit, the Intuit logo, QuickBooks, Intuit Online Payroll, Quicken, QuickBase, TurboTax, EasyStep, and QuickZoom, among others, are registered trademarks and/or registered service marks of Intuit Inc. in the United States and other countries.