V2406/2422/2426 Linux User's Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Solaris 2.5 Software Developer Kit Introduction
Solaris 2.5 Software Developer Kit Introduction 2550 Garcia Avenue Mountain View, CA 94043 U.S.A. A Sun Microsystems, Inc. Business 1995 Sun Microsystems, Inc. 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Portions of this product may be derived from the UNIX® system, licensed from UNIX Systems Laboratories, Inc., a wholly owned subsidiary of Novell, Inc., and from the Berkeley 4.3 BSD system, licensed from the University of California. Third-party software, including font technology in this product, is protected by copyright and licensed from Sun’s Suppliers. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19. The product described in this manual may be protected by one or more U.S. patents, foreign patents, or pending applications. TRADEMARKS Sun, Sun Microsystems, the Sun logo, SunSoft, the SunSoft logo, Solaris, SunOS, OpenWindows, DeskSet, ONC, ONC+, NFS, SunExpress, ProCompiler, XView, ToolTalk, XGL, XIL, Solaris VISUAL, Solaris PEX, and AnswerBook are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. CatalystSM is a service mark of Sun Microsystems, Inc. -

Direct Xlib User's Guide
Direct Xlib User’s Guide 2550 Garcia Avenue Mountain View, CA 94043 U.S.A. A Sun Microsystems, Inc. Business 1995 Sun Microsystems, Inc. 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Portions of this product may be derived from the UNIX® system, licensed from UNIX Systems Laboratories, Inc., a wholly owned subsidiary of Novell, Inc., and from the Berkeley 4.3 BSD system, licensed from the University of California. Third-party software, including font technology in this product, is protected by copyright and licensed from Sun’s Suppliers. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19. The product described in this manual may be protected by one or more U.S. patents, foreign patents, or pending applications. TRADEMARKS Sun, Sun Microsystems, the Sun logo, SunSoft, the SunSoft logo, Solaris, SunOS, OpenWindows, Direct Xlib, DeskSet, ONC, ONC+, and NFS are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. -

A Sense of Time for Node.Js: Timeouts As a Cure for Event Handler Poisoning
A Sense of Time for Node.js: Timeouts as a Cure for Event Handler Poisoning Anonymous Abstract—The software development community has begun to new Denial of Service attack that can be used against EDA- adopt the Event-Driven Architecture (EDA) to provide scalable based services. Our Event Handler Poisoning attack exploits web services. Though the Event-Driven Architecture can offer the most important limited resource in the EDA: the Event better scalability than the One Thread Per Client Architecture, Handlers themselves. its use exposes service providers to a Denial of Service attack that we call Event Handler Poisoning (EHP). The source of the EDA’s scalability is also its Achilles’ heel. Multiplexing unrelated work onto the same thread re- This work is the first to define EHP attacks. After examining EHP vulnerabilities in the popular Node.js EDA framework and duces overhead, but it also moves the burden of time sharing open-source npm modules, we explore various solutions to EHP- out of the thread library or operating system and into the safety. For a practical defense against EHP attacks, we propose application itself. Where OTPCA-based services can rely on Node.cure, which defends a large class of Node.js applications preemptive multitasking to ensure that resources are shared against all known EHP attacks by making timeouts a first-class fairly, using the EDA requires the service to enforce its own member of the JavaScript language and the Node.js framework. cooperative multitasking [89]. An EHP attack identifies a way to defeat the cooperative multitasking used by an EDA-based Our evaluation shows that Node.cure is effective, broadly applicable, and offers strong security guarantees. -

POWERVR 3D Application Development Recommendations
Imagination Technologies Copyright POWERVR 3D Application Development Recommendations Copyright © 2009, Imagination Technologies Ltd. All Rights Reserved. This publication contains proprietary information which is protected by copyright. The information contained in this publication is subject to change without notice and is supplied 'as is' without warranty of any kind. Imagination Technologies and the Imagination Technologies logo are trademarks or registered trademarks of Imagination Technologies Limited. All other logos, products, trademarks and registered trademarks are the property of their respective owners. Filename : POWERVR. 3D Application Development Recommendations.1.7f.External.doc Version : 1.7f External Issue (Package: POWERVR SDK 2.05.25.0804) Issue Date : 07 Jul 2009 Author : POWERVR POWERVR 1 Revision 1.7f Imagination Technologies Copyright Contents 1. Introduction .................................................................................................................................4 1. Golden Rules...............................................................................................................................5 1.1. Batching.........................................................................................................................5 1.1.1. API Overhead ................................................................................................................5 1.2. Opaque objects must be correctly flagged as opaque..................................................6 1.3. Avoid mixing -

Overview Guide Release 21B F45060-01
Oracle Utilities Customer Care and Billing Cloud Service Overview Guide Release 21B F45060-01 August 2021 Oracle Utilities Customer Care and Billing Cloud Service Release 21B Overview Guide Copyright © 2012, 2021 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" -

Industrial Ethernet Quick and Simple Explanation of Key Terms
Industrial Ethernet Quick and simple explanation of key terms EN_Bro_Glossar_Netzwerktechnik_A6_Rev02.indd 1 26.05.14 15:26 Industrial Ethernet The use of industrial Ethernet communication offers many advantages and is becoming more common in the automation of production plants and machinery. Many new technical terms from the IT world are also being used in this context among industrial users. In this glossary, we have listed and explained the main techni- cal terms from the field of Industrial Ethernet – we make Ethernet easy. 2 PHOENIX CONTACT EN_Bro_Glossar_Netzwerktechnik_A6_Rev02.indd 2 26.05.14 15:26 Table of contents Glossary Pages 04 – 45 IEEE standards Pages 46 – 47 PHOENIX CONTACT 3 EN_Bro_Glossar_Netzwerktechnik_A6_Rev02.indd 3 26.05.14 15:26 Industrial Ethernet 10Base-T Standard for data transmission of 10 Mbps Ethernet using unshielded twisted pair cables (Category 3, 4 or 5). 100Base-FX Standard for data transmission of 100 Mbps Ethernet using fiber optic cables. 100Base-TX Standard for data transmission of 100 Mbps Ethernet using twisted pair cables (Category 5). Each connection is established via two wire pairs, one wire pair for “transmit data” and the other for “receive data”. 100Base-T Fast Ethernet; 100Base-T has been officially elevated to an IEEE standard as ITU 802.3u. This standard is essentially based on technologies for 10Base-T, the Ethernet version for twisted pair cables. There are several versions of 100Base-T, which differ with respect to the physical layer and therefore the transmission media: 100Base-TX, 100Base-T2, 100Base-T4, and 100Base-FX. With this method, the MAC level and therefore the conventional CSMA/CD access method are retained at a transmission speed of 100 Mbps. -

No Starch Press, Inc
Table of Contents The Book of VMware—The Complete Guide to VMware Workstation.......................................................1 Chapter 1: Introduction.....................................................................................................................................3 Overview..................................................................................................................................................3 1.1 Who Should Read This Book............................................................................................................3 1.2 Terms and Conventions.....................................................................................................................4 1.3 Book Layout......................................................................................................................................4 1.4 VMware Applications........................................................................................................................6 1.4.1 Quality Assurance (QA)....................................................................................................6 1.4.2 Network Programming and Testing...................................................................................6 1.4.3 Operating System Development, Research, and Education..............................................7 1.4.4 Other VMware Products....................................................................................................7 Chapter 2: The VMware Virtual Machine.......................................................................................................8 -

Pymupdf 1.12.2 Documentation » Next | Index Pymupdf Documentation
PyMuPDF 1.12.2 documentation » next | index PyMuPDF Documentation Introduction Note on the Name fitz License Covered Version Installation Option 1: Install from Sources Step 1: Download PyMuPDF Step 2: Download and Generate MuPDF Step 3: Build / Setup PyMuPDF Option 2: Install from Binaries Step 1: Download Binary Step 2: Install PyMuPDF MD5 Checksums Targeting Parallel Python Installations Using UPX Tutorial Importing the Bindings Opening a Document Some Document Methods and Attributes Accessing Meta Data Working with Outlines Working with Pages Inspecting the Links of a Page Rendering a Page Saving the Page Image in a File Displaying the Image in Dialog Managers Extracting Text Searching Text PDF Maintenance Modifying, Creating, Re-arranging and Deleting Pages Joining and Splitting PDF Documents Saving Closing Example: Dynamically Cleaning up Corrupt PDF Documents Further Reading Classes Annot Example Colorspace Document Remarks on select() select() Examples setMetadata() Example setToC() Example insertPDF() Examples Other Examples Identity IRect Remark IRect Algebra Examples Link linkDest Matrix Remarks 1 Remarks 2 Matrix Algebra Examples Shifting Flipping Shearing Rotating Outline Page Description of getLinks() Entries Notes on Supporting Links Homologous Methods of Document and Page Pixmap Supported Input Image Types Details on Saving Images with writeImage() Pixmap Example Code Snippets Point Remark Point Algebra Examples Shape Usage Examples Common Parameters Rect Remark Rect Algebra Examples Operator Algebra for Geometry Objects -

OSS Disclosure Document OSS Licenses Used in RN AIVI 1
OSS Disclosure Document Date: 08-10-2017 OSS Licenses used in RN_AIVI CM-CI1/PJ-CB Page 1 Project 1 Overview .................................................. 12 2 OSS Licenses used in the project .......................... 13 3 Package details for OSS Licenses usage .................... 14 AES - Advanced Encryption Standard – 1.0 ..................... 14 Alsa Libraries - 1.0.29 ...................................... 14 Alsa Plugins - 1.0.29 ........................................ 14 Alsa Utils - 1.0.29 .......................................... 14 APMD - 3.2.2 ................................................. 15 ATK - 2.8.0 .................................................. 15 Attr - 2.4.47 ................................................ 15 Audio File Library - 0.2.7 ................................... 15 Avahi - 0.6.31 ............................................... 15 Bash - 3.2.48 .............................................. 15 BidiReferenceCpp - 26 ...................................... 15 Bison - 2.5.2., 3.0.2, 3.0.4 ............................... 16 Blktrace - 1.0.5 ........................................... 16 BlueZ - 4.101, 5.33 ........................................ 16 BPSTL ...................................................... 16 Btrfs-progs – 4.1.2 ........................................ 16 Busybox - 1.23.2 ........................................... 16 Bzip2 - 1.0.6 .............................................. 16 Cairo Vector Graphics Library - 1.12.14, 1.12.16, 1.14.2 ... 17 Cairo-Pixman - 0.30.2,0.32.6 .............................. -
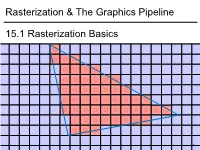
Rasterization & the Graphics Pipeline 15.1 Rasterization Basics
1 1 0.8 0.6 0.4 0.2 0 -0.2 -0.4 -0.6 -0.8 15.1Rasterization Basics Rasterization & TheGraphics Pipeline Rasterization& -1 -1 -0.8 -0.6 -0.4 -0.2 0 0.2 0.4 0.6 0.8 1 In This Video • The Graphics Pipeline and how it processes triangles – Projection, rasterisation, shading, depth testing • DirectX12 and its stages 2 Modern Graphics Pipeline • Input – Geometric model • Triangle vertices, vertex normals, texture coordinates – Lighting/material model (shader) • Light source positions, colors, intensities, etc. • Texture maps, specular/diffuse coefficients, etc. – Viewpoint + projection plane – You know this, you’ve done it! • Output – Color (+depth) per pixel Colbert & Krivanek 3 The Graphics Pipeline • Project vertices to 2D (image) • Rasterize triangle: find which pixels should be lit • Compute per-pixel color • Test visibility (Z-buffer), update frame buffer color 4 The Graphics Pipeline • Project vertices to 2D (image) • Rasterize triangle: find which pixels should be lit – For each pixel, test 3 edge equations • if all pass, draw pixel • Compute per-pixel color • Test visibility (Z-buffer), update frame buffer color 5 The Graphics Pipeline • Perform projection of vertices • Rasterize triangle: find which pixels should be lit • Compute per-pixel color • Test visibility, update frame buffer color – Store minimum distance to camera for each pixel in “Z-buffer” • ~same as tmin in ray casting! – if new_z < zbuffer[x,y] zbuffer[x,y]=new_z framebuffer[x,y]=new_color frame buffer Z buffer 6 The Graphics Pipeline For each triangle transform into eye space (perform projection) setup 3 edge equations for each pixel x,y if passes all edge equations compute z if z<zbuffer[x,y] zbuffer[x,y]=z framebuffer[x,y]=shade() 7 (Simplified version) DirectX 12 Pipeline (Vulkan & Metal are highly similar) Vertex & Textures, index data etc. -

Powervr Graphics - Latest Developments and Future Plans
PowerVR Graphics - Latest Developments and Future Plans Latest Developments and Future Plans A brief introduction • Joe Davis • Lead Developer Support Engineer, PowerVR Graphics • With Imagination’s PowerVR Developer Technology team for ~6 years • PowerVR Developer Technology • SDK, tools, documentation and developer support/relations (e.g. this session ) facebook.com/imgtec @PowerVRInsider │ #idc15 2 Company overview About Imagination Multimedia, processors, communications and cloud IP Driving IP innovation with unrivalled portfolio . Recognised leader in graphics, GPU compute and video IP . #3 design IP company world-wide* Ensigma Communications PowerVR Processors Graphics & GPU Compute Processors SoC fabric PowerVR Video MIPS Processors General Processors PowerVR Vision Processors * source: Gartner facebook.com/imgtec @PowerVRInsider │ #idc15 4 About Imagination Our IP plus our partners’ know-how combine to drive and disrupt Smart WearablesGaming Security & VR/AR Advanced Automotive Wearables Retail eHealth Smart homes facebook.com/imgtec @PowerVRInsider │ #idc15 5 About Imagination Business model Licensees OEMs and ODMs Consumers facebook.com/imgtec @PowerVRInsider │ #idc15 6 About Imagination Our licensees and partners drive our business facebook.com/imgtec @PowerVRInsider │ #idc15 7 PowerVR Rogue Hardware PowerVR Rogue Recap . Tile-based deferred renderer . Building on technology proven over 5 previous generations . Formally announced at CES 2012 . USC - Universal Shading Cluster . New scalar SIMD shader core . General purpose compute is a first class citizen in the core … . … while not forgetting what makes a shader core great for graphics facebook.com/imgtec @PowerVRInsider │ #idc15 9 TBDR Tile-based . Tile-based . Split each render up into small tiles (32x32 for the most part) . Bin geometry after vertex shading into those tiles . Tile-based rasterisation and pixel shading . -

Open Windows Version 3 Installation and Start-Up Guide E 1991 by Sun Microsystems, Inc.-Printed in USA
Open Windows Version 3 Installation and Start-Up Guide e 1991 by Sun Microsystems, Inc.-Printed in USA. 2550 Garcia Avenue, Mountain View, California 94043-1100 All rights reserved. No part of this work covered by copyright may be reproduced in any form or by any means-graphic, electronic or mechanical, including photocopying, recording, taping, or storage in an information retrieval system- without prior written permission of the copyright owner. The OPEN LOOK and the Sun Graphical User Interfaces were developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the com puter industry. Sun holds a non-exclusive license from Xerox to the Xerox Graphical User Interface, which license also covers Sun's licensees. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 (October 1988) and FAR 52.227-19 Oune 1987). The product described in this manual may be protected by one or more U.s. patents, foreign patents, and/or pending applications. TRADEMARKS Sun Logo, Sun Microsystems, NeWS, and NFS are registered trademarks, and SunSoft, SunSoft logo, SunOS, SunView, Sun-2, Sun-3, Sun-4, XGL, SunPHIGS, SunGKS, and OpenWindows are trademarks of SunMicrosystems, Inc. licensed to SunSoft, Inc. UNIX and OPEN LOOK are registered trademarks of UNIX System Laboratories, Inc. PostScript is a registered trademark of Adobe Systems Incorporated.