Quality Attributes and Design Tactics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Software Quality Management
Software Quality Management 2004-2005 Marco Scotto ([email protected]) Software Quality Management Contents ¾Definitions ¾Quality of the software product ¾Special features of software ¾ Early software quality models •Boehm model • McCall model ¾ Standard ISO 9126 Software Quality Management 2 Definitions ¾ Software: intellectual product consisting of information stored on a storage device (ISO/DIS 9000: 2000) • Software may occur as concepts, transactions, procedures. One example of software is a computer program • Software is "intellectual creation comprising the programs, procedures, rules and any associated documentation pertaining to the operation of a data processing system" •A software product is the "complete set of computer programs, procedures and associated documentation and data designated for delivery to a user" [ISO 9000-3] • Software is independent of the medium on which it is recorded Software Quality Management 3 Quality of the software product ¾The product should, on the highest level… • Ensure the satisfaction of the user needs • Ensure its proper use ¾ Earlier: 1 developer, 1 user • The program should run and produce results similar to those expected ¾ Later: more developers, more users • Need to economical use of the storage devices • Understandability, portability • User-friendliness, learnability ¾ Nowadays: • Efficiency, reliability, no errors, able to restart without using data Software Quality Management 4 Special features of software (1/6) ¾ Why is software ”different”? • Does not really have “physical” existence -

Quality-Based Software Reuse
Quality-Based Software Reuse Julio Cesar Sampaio do Prado Leite1, Yijun Yu2, Lin Liu3, Eric S. K. Yu2, John Mylopoulos2 1Departmento de Informatica, Pontif´ıcia Universidade Catolica´ do Rio de Janeiro, RJ 22453-900, Brasil 2Department of Computer Science, University of Toronto, M5S 3E4 Canada 3School of Software, Tsinghua University, Beijing, 100084, China Abstract. Work in software reuse focuses on reusing artifacts. In this context, finding a reusable artifact is driven by a desired functionality. This paper proposes a change to this common view. We argue that it is possible and necessary to also look at reuse from a non-functional (quality) perspective. Combining ideas from reuse, from goal-oriented requirements, from aspect-oriented programming and quality management, we obtain a goal-driven process to enable the quality-based reusability. 1 Introduction Software reuse has been a lofty goal for Software Engineering (SE) research and prac- tice, as a means to reduced development costs1 and improved quality. The past decade has seen considerable progress in fulfilling this goal, both with respect to research ideas and industrial practices (e.g., [1–3]). Current reuse techniques focus on the reuse of software artifacts on the basis of de- sired functionality. However, non-functional properties (qualities) of a software system are also crucial. Systems fail because of inadequate performance, security, reliability, usability, or precision, to name a few. Quality concerns, therefore, should also be front and centre in methods for software reuse. For example, in designing for the NASA Mars Spirit spacecraft, one would not adopt a “cosine” function from an arbitrary mathemat- ical library. -

Design Rules
Design rules Chapter 7 adapted by Dr. Kristina Lapin, Vilnius University design rules Designing for maximum usability – the goal of interaction design • Principles of usability – general understanding • Standards and guidelines – direction for design • Design patterns – capture and reuse design knowledge types of design rules • principles – abstract design rules – low authority – high generality Guideline s • standards – specific design rules – high authority – limited application increasinggenerality Standards • guidelines generality increasing – lower authority increasing authority increasing authority – more general application Principles to support usability Learnability the ease with which new users can begin effective interaction and achieve maximal performance Flexibility the multiplicity of ways the user and system exchange information Robustness the level of support provided the user in determining successful achievement and assessment of goal- directed behaviour •Predictability •Synthezability Learnability •Familiarity •Generalizability •Consistency Principles of learnability Predictability – determining effect of future actions based on past interaction history – operation visibility Predictability http://www.webbyawards.com/ 7 Principles of learnability Synthesizability – assessing the effect of past actions – immediate vs. eventual honesty Synthesizability 1. 2. 3. 9 Principles of learnability (ctd) Familiarity – how prior knowledge applies to new system – guessability; affordance Principles of learnability (ctd) Generalizability -

Usability Basics for Software Developers Usability Engineering
focususability engineering Usability Basics for Software Developers Xavier Ferré and Natalia Juristo, Universidad Politécnica de Madrid Helmut Windl, Siemens AG, Germany Larry Constantine, Constantine & Lockwood n recent years, software system usability has made some interesting ad- vances, with more and more organizations starting to take usability seri- ously.1 Unfortunately, the average developer has not adopted these new I concepts, so the usability level of software products has not improved. Contrary to what some might think, us- Usability engineering defines the target us- This tutorial ability is not just the appearance of the user ability level in advance and ensures that the examines the interface (UI). Usability relates to how the software developed reaches that level. The system interacts with the user, and it includes term was coined to reflect the engineering ap- relationship five basic attributes: learnability, efficiency, proach some usability specialists take.3 It is between usability user retention over time, error rate, and sat- “a process through which usability character- and the user isfaction. Here, we present the general us- istics are specified, quantitatively and early in interface and ability process for building a system with the the development process, and measured desired level of usability. This process, which throughout the process.”4 Usability is an is- discusses how most usability practitioners apply with slight sue we can approach from multiple view- the usability variation, is structured around a design- points, which is why many different disci- process follows a evaluate-redesign cycle. Practitioners initiate plines, such as psychology, computer science, design-evaluate- the process by analyzing the targeted users and sociology, are trying to tackle it. -

USABILITY of PROCESSES in ENGINEERING DESIGN Becerril, Lucia; Stahlmann, Jan-Timo; Beck, Jesco; Lindemann, Udo Technical University of Munich, Germany
21ST INTERNATIONAL CONFERENCE ON ENGINEERING DESIGN, ICED17 21-25 AUGUST 2017, THE UNIVERSITY OF BRITISH COLUMBIA, VANCOUVER, CANADA USABILITY OF PROCESSES IN ENGINEERING DESIGN Becerril, Lucia; Stahlmann, Jan-Timo; Beck, Jesco; Lindemann, Udo Technical University of Munich, Germany Abstract Processes in Engineering Design are generally optimized towards efficiency, quality, costs, risks, etc., however an analysis that includes requirements from the process users' view is missing. Within the last years, the concept of usability has being introduced to examine business processes. This is a promising approach for Engineering Design, by involving process "users" (designers, engineers, software developers, project managers, etc.) in the process planning phase, several issues such as consistency flaws or counter-intuitive information flow can be identified beforehand. This paper aims to explore the transferability of usability concepts and evaluation methods to processes in the field of Engineering Design. The goal of this paper is to set a basis for further studies with regard on how to plan and design processes that interact efficiently, effectively and satisfactorily with the people involved. For this purpose ten process usability attributes are consolidated from the overlap between usability attributes (of products and systems) and process system properties. Moreover, five usability evaluation methods are examined on their applicability for evaluating design processes. Keywords: Design management, Design process, User centred design Contact: Lucia Becerril Technical University of Munich Chair of Product Development Germany [email protected] Please cite this paper as: Surnames, Initials: Title of paper. In: Proceedings of the 21st International Conference on Engineering Design (ICED17), Vol. 2: Design Processes | Design Organisation and Management, Vancouver, Canada, 21.-25.08.2017. -

Application of User-Centered Design for a Student Case Management System
IT 11 057 Examensarbete 15 hp August 2011 Application of User-Centered Design for a Student Case Management System Vincent Kahl Institutionen för informationsteknologi Department of Information Technology ! Abstract Application of User-Centered Design for a Student Case Management System Vincent Kahl Teknisk- naturvetenskaplig fakultet UTH-enheten The student office and student counselors of Uppsala University’s IT Department need a new application for organizing and coordinating Besöksadress: student cases. The aim of this thesis is to define a specification for a Ångströmlaboratoriet Lägerhyddsvägen 1 new system. A user-centered design (UCD) approach is taken to Hus 4, Plan 0 ensure that the new application will increase productivity, is usable, and is accepted by the people that will work with it. The employed Postadress: UCD process is a custom adaption of the ISO 9241-210 standard’s Box 536 751 21 Uppsala UCD process proposal. Following the activity cycle of the ISO standard for user-centered design, this specification will understand and Telefon: specify the context of use, specify the user and organizational 018 – 471 30 03 requirements, and produce design solutions that are evaluated against Telefax: the requirements. 018 – 471 30 00 Hemsida: http://www.teknat.uu.se/student Handledare: Lars Oestreicher Ämnesgranskare: Lars Oestreicher Examinator: Anders Jansson IT 11 057 Tryckt av: Reprocentralen ITC ! Table of Contents 1! Introduction ........................................................................................................ -

An Analytics Platform for Everyone: Flexibility, Scalability, Usability
An Analytics Platform for Everyone: Flexibility, Scalability, Usability ALLIANCE Comprehensive analytics and reporting capabilities of WebFOCUS from Information Builders, running on the robust and scalable Teradata® Database redefines self- Information Builders and Teradata service analytics by helping organizations use BI more The Need strategically across the enterprise. BI and analytics are needed more than ever to help The value of BI is best measured by how widely it can organizations succeed and thrive in ever more competi- impact decision making across the enterprise and beyond. tive landscapes. This means extending access to BI and WebFOCUS on Teradata Database answers this need, analytics throughout the enterprise. delivering rich, consumable, interactive information to the widest range of employees, managers, analysts, The Solution partners, and customers. All of this can be done in real- WebFOCUS by Information Builders, running on time, while importing data from a spectrum of disparate Teradata ® Database, provides the industry-leading sources—structured and unstructured data, and present- BI and analytics platform. WebFOCUS dashboards, ing results in award-winning user-friendly dashboards and scorecards, and other features provide self-service, other rich formats. real-time solutions to maximize the benefits of BI and analytics across the organization. The Challenge of Pulling Insights The Benefits from Data • Comprehensive solution serves as a complete BI and analytics platform. Business intelligence has long been mission critical, yet many organizations, bursting with data, are frustrated by • Real-time analytics. the challenges of integrating disparate data sources to • Ease of use and award-winning UI answer the need harness the information generated by every customer, for self-serve BI and analytics. -

Software Quality Assurance Process-Based (Conformance to Requirements) Product-Based (You Get What You Pay For) Transcendent (Excellence)
Five Views of Quality Value-based (Engineer to price) User-based (Fitness for purpose) Software Quality Assurance Process-based (Conformance to requirements) Product-based (You get what you pay for) Transcendent (Excellence) M8034 @ Peter Lo 2006 1 M8034 @ Peter Lo 2006 2 Software Quality Definition The Definition Emphasize Conformance to explicitly stated functional and Software requirements are the foundation from which performance requirements, explicitly documented quality is measured. Lack of conformance to development standards, and implicit requirements is lack of quality. characteristics that are expected of all Specified standards define a set of development criteria that guide the manner in which software is engineered. If professionally developed software. the criteria are not followed, lack of quality will almost surely result. There is a set of implicit requirements that often goes unmentioned. If software conforms to its explicit requirements, but fails to meet implicit requirements, software quality is suspect. M8034 @ Peter Lo 2006 3 M8034 @ Peter Lo 2006 4 How Important Software Quality? Software Quality Factors It is important to have the understanding that the It can be categorized in two groups: software quality work begins before the testing Factors that can be Directly Measured (e.g. phase and continues after the software is delivered. errors; KLOC; unit-time) Factors that can be Measured only Indirectly (e.g. usability or maintainability) Or, it can be categorized into: Internal – Attributes which can be measured or observed in isolation. External – Attributes which can only be observed in relation to external environment. M8034 @ Peter Lo 2006 5 M8034 @ Peter Lo 2006 6 McCall’s Triangle of Quality McCall’s Triangle of Quality McCall’s quality factors were proposed in the PRODUCT REVISION PRODUCT TRANSITION early 1970s. -

Usability Issues in Software Development Lifecycle
Volume 3, Issue 8, August 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Usability Issues in Software Development Lifecycle R.Madhavan* Dr.K.Alagarsamy Department Of CSE, Computer Centre Joesuresh Engineering College, Tamilnadu, India Maduraikamaraj University, Tamilnadu, India Abstract: Usability is one of the key quality attributes in software development. It is a factor present in almost all software quality assurance models. There is a close analogy between the terms usability and quality. Usability is an important quality factor for interactive software systems. The usability attributes which contribute to quality of use will include the style and properties of the user interface, the dialogue structure, and the nature of the functionality. The aim of this paper is to improve software quality by finding ways to integrate usability with software quality measurements throughout the life cycle. Keywords: User requirements, design, software architecture, SDLC, software quality. I. Introduction Usability is the extent to which specific users can use a product to their satisfaction in order to effectively and efficiently achieve specific goals in a specific context of use. A number of studies have pointed out a wide range of benefits stemming from usability: it improves productivity and raises team morale, reduces training and documentation costs, improves user productivity, increases e-commerce potential, etc. Additionally, and contrary to what one might think, the cost/benefit ratio of usability is highly worthwhile. Some authors have state that every dollar spent on usability offers a return of $30.25. There are also studies for e-commerce sites that show that a 5% improvement in usability could increase revenues by 10% to 35%. -
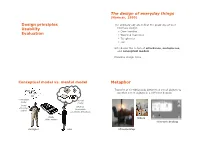
Design Principles Usability Evaluation the Design of Everyday Things
The design of everyday things (Norman, 1990) Design principles The ordinary objects reflect the problems of user Usability interface design ! Door handles Evaluation ! Washing machines ! Telephones ! etc. Introduces the notion of affordance, metaphores, and conceptual models Provides design rules Conceptual model vs. mental model Metaphor Transfer of a relationship between a set of objects to another set of objects in a different domain conceptual mental model model formal informal structured incomplete logical sometimes erroneous image folders of the system electronic desktop designer user office/desktop Affordances Affordances Quality of an object, which allows a user to perform an action The form, the size, the view of the object suggest what we can do with it « Much of everyday knowledge resides in the world, not in the head » (Norman, 1988) Affordances Affordances Button for pressing Dials for turning but action unknown Sliders for These sliding buttons? Affordances Perceived Affordances in this UI? The concept of affordance was first introduced by psychologist James J. Gibson in 1977. Gibson’s affordances are independent of the individual’s ability to recognize them. They depend on their physical capabilities. Norman’s affordances also depend on the individual’s perception. Norman explained that he would rather replace his term by the term « perceived affordances ». Constraints Constraints Our mental models of the mechanics and physics Are these user interfaces effective? help us predict and simulate the operation of an object Mappings Mappings Example: Find the correspondance between the stove Example: Find the correspondance between the stove burners and the controls burners and the controls ...and now? Example: designing a watch Example: designing a watch Conceptual model? Conceptual model? Affordances? Affordances? Mappings? Mappings? ...and user feedback? Norman’s principles (1990) Usability 1. -

Usability Testing Report
Usability Testing Report Kate Meizner Kristen Droesch Alex Hagenah Jo Polanco Pratt Institute EXECUTIVE(SUMMARY( 2! INTRODUCTION( 4! METHODOLOGY( 5! USER(TEST(PARTICIPANTS( 7! PARTICIPANT(DATA(SUMMARY( 8! FINDINGS(&(RECOMMENDATIONS( 11! FINDING(1:(USERS(HAD(DIFFICULTY(LOCATING(THE(SEARCH(BAR,(AND(DIDN’T(HAVE(CONFIDENCE(USING(IT.( 11! RECOMMENDATION(1:(INCORPORATE(A(SEARCH(BAR(PROMINENTLY(ON(THE(HOMEPAGE.( 11! FINDING(2:(USERS(WERE(OVERWHELMED(BY(THE(MAGNITUDE(OF(THE(SUBJECT(HEADINGS.( 12! RECOMMENDATION(2:(CONDENSE(SUBJECT(HEADINGS(TO(PROVIDE(USERS(WITH(A(MORE(APPROACHABLE(PLATFORM.( 13! FINDING(3:(NO(STATUS(FEEDBACK(FOR(KEYWORD(SEARCHES( 14! RECOMMENDATION(3A:(ADD(A(STATUS(INDICATOR(TO(THE(SEARCH(BOX.( 14! RECOMMENDATION(3B:(PROVIDE(MULTIPLE(SIGNIFIERS(THAT(SEARCH(RETURNS(ARE(RELEVANT.( 15! FINDING(4:(APPLYING(AND(CLEARING(FILTERS(CONFUSED(USERS.( 16! RECOMMENDATION(4:(PROVIDE(STRONGER(FILTRATION(FEEDBACK(BY(MAKING(SELECTIONS(MORE(PROMINENT(ON(THE( PAGE.(CONSOLIDATE(SIGNIFIERS(THAT(CLEAR(FILTER(SELECTIONS.( 16! FINDING(5:(SPECIFIC(EDITS(TO(THE(CURATED(“FEATURED(COLLECTION”(TEMPLATE(WOULD(BUILD(UPON(POSITIVE( FEEDBACK( 18! RECOMMENDATION(5:(MAKE(FEATURED(COLLECTION(MORE(PROMINENT(AND(HIGHLIGHT(ITS(FEATURES.( 18! CONCLUSION( 20! APPENDICES( 21! APPENDIX(1(–(RECRUITMENT(QUESTIONNAIRE( 21! APPENDIX(2(–(PRELTEST(QUESTIONNAIRE( 23! APPENDIX(3(–(MODERATOR’S(SCRIPT( 25! APPENDIX(4(–(TASK(RESULT(SUMMARY( 28! APPENDIX(5(–(SYSTEM(USABILITY(SCALE((SUS)( 29( APPENDIX(6(–(PRIORITY(VISUALIZATION(SCALE( 30! REFERENCES( 32! 1 Executive Summary This report details a usability study conducted by four Pratt Institute evaluators of the PEN America Archive prototype. Launching in Spring 2017, the site features a dynamic search function allowing users to browse several hundred pieces of archived PEN America audio and video content. -

Methods and Qualities of a Good User Interface Design
2008:PR002 User Interface Design – Methods and Qualities of a Good User Interface Design Ravi Chandra Chaitanya Guntupalli MASTER’S THESIS Software Engineering, 2008 Department of Technology, Mathematics and Computer Science MASTER’S THESIS User Interface Design – Methods and Qualities of a Good User Interface Design Summary User interface (UI) plays a vital role in software. In terms of visibility, its design and precision holds the primary importance for depicting the exact amount of information for the intended user. Every minor decision taken for the designing of UI can contribute to the software both positively and negatively. Therefore, our study is intended to highlight the strategies that are currently being used for successfully designing UIs, and make appropriate suggestions for betterment of UI designs based on case studies and research findings. Author: Ravi Chandra Chaitanya. Guntupalli Examiner: Dr. Samantha Jenkins Advisor: Dr. Samantha Jenkins Programme: Software Engineering, 2008 Subject: Software Engineering Level: Master Date: June, 2008 Report Number: 2008:PR002 Keywords User interface design, Software Quality, Reliability, Efficiency, Conciseness, Portability, Consistency, Maintainability, Understandability, System status visibility, System consistency, Error handling, Feedback systems, Memory loading, Efficiency, Appropriate outlook, UI design principles, Usability design, Interface design, Information design, Stake holder, End user. Publisher: University West, Department of Technology, Mathematics and Computer Science,