Newly Added Applications Catalog Publisher Name Software Title Name Software Title Version Name App Name Version ACD Systems Ltd
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adobe Application Manager Enterprise Edition Deployment Guide
ADOBE® APPLICATION MANAGER ENTERPRISE EDITION GUIDE DE DEPLOIEMENT EN ENTREPRISE Adobe® Application Manager Enterprise Edition version 3.1 Version de document 3.1 Date du document : Septembre 2012 © 2012 Adobe Systems Incorporated and its licensors. All rights reserved. Adobe® Application Manager Enterprise Edition Guide de déploiement en entreprise This guide is licensed for use under the terms of the Creative Commons Attribution Non-Commercial 3.0 License. This License allows users to copy, distribute, and transmit the guide for noncommercial purposes only so long as (1) proper attribution to Adobe is given as the owner of the guide; and (2) any reuse or distribution of the guide contains a notice that use of the guide is governed by these terms. The best way to provide notice is to include the following link. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/3.0/ Adobe, the Adobe logo, Acrobat, Adobe Audition, Adobe Bridge, Adobe Device Central, Adobe OnLocation, Adobe Premiere, Adobe Premiere Pro, Adobe Technical Communication Suite, After Effects, Contribute, Captivate, Creative Suite, CS Live, Dreamweaver, Encore, Fireworks, Flash, Flash Builder, Flash Catalyst, FrameMaker, Illustrator, InDesign, Photoshop, RoboHelp, SiteCatalyst, and Soundbooth are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple, Mac, and Mac OS are trademarks of Apple Inc., registered in the United States and other countries. Microsoft, Windows, and Windows Vista are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. UNIX is a registered trademark of The Open Group in the US and other countries. -

List of TCP and UDP Port Numbers
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia Jump to: navigation, search This is a list of Internet socket port numbers used by protocols of the Transport Layer of the Internet Protocol Suite for the establishment of host-to-host communications. Originally, these port numbers were used by the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), but are used also for the Stream Control Transmission Protocol (SCTP), and the Datagram Congestion Control Protocol (DCCP). SCTP and DCCP services usually use a port number that matches the service of the corresponding TCP or UDP implementation if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] However, many unofficial uses of both well- known and registered port numbers occur in practice. Contents [hide] y 1 Table legend y 2 Well-known ports: 0±1023 y 3 Registered ports: 1024±49151 y 4 Dynamic, private or ephemeral ports: 49152±65535 y 5 See also y 6 References y 7 External links [edit] Table legend Color coding of table entries Official Port/application combination is registered with IANA Unofficial Port/application combination is not registered with IANA Conflict Port is in use for multiple applications [edit] Well-known ports: 0±1023 The port numbers in the range from 0 to 1023 are the well-known ports. They are used by system processes that provide widely-used types of network services. On Unix-like operating systems, a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. -

Comprehensive Protection for Windows®
Solutions for Small and Mid-Sized Businesses October 2007 Product Comprehensive Catalog Protection for Windows® As companies increasingly rely on sophisticated technologies to support their objectives, the risks to business operations grow. The complexity of managing IT systems increases, as do the costs. And, if your company is like most, its IT staff and resources are limited and continually called on to justify their costs. Under these conditions, it’s difficult for companies to keep the Microsoft® Windows® environments they depend on to run their business secure, available, and well-managed. Symantec is uniquely qualified to address the challenge. That’s because Symantec delivers an unparalleled combination of leading technologies and services to help ensure the highest level of protection across your Microsoft Windows environment. Symantec offers comprehensive and affordable, best-in-class solutions that help protect Microsoft Windows environments by keeping data, systems, and applications secure, available, and well-managed at all times. Our world-class support programs and partners offer guidance to help you implement comprehensive solutions that will maximize your investment as they protect your IT environment. As you will see on the following pages, Symantec offers industry-leading solutions delivering enterprise-class performance without unnecessary cost or complexity. With a proven track record spanning several decades, Symantec knows how to help you keep your business up, running, and growing—no matter what happens. Symantec Product Catalog—October 2007 Comprehensive Protection for Windows® Contents Security . 2 Client, Server, and Network Security. 3 Symantec Endpoint Protection . 3 Symantec Network Access Control . 4 Symantec Multi-Tier Protection. 4 Symantec Mail Security for SMTP. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Symantec Backup Exec™ 2012 Sales Script
Symantec Backup Exec™ 2012 Sales Script Partner Competitive Sales Script Product overview The Symantec Backup Exec™ 2012 product portfolio drives sales with a name customers know and trust plus new technology fit for both simple and complex IT environments. One integrated product protects virtual AND physical environments, simplifies both backup AND disaster recovery, and recovers data or systems at any scale, from an individual item to an entire server. New technologies include integrated disaster recovery, physical to virtual conversions and a renovated interface with default settings for the most common backup options. Available as packaged software, appliances, or cloud-based backup and recovery, Backup Exec is the one data protection choice for growing businesses and the partners that serve them. Why sell it? Selling Symantec Backup Exec 2012 product portfolio provides unlimited sales opportunities for you. • Attach with every new Windows® server, application, and VMware® or Hyper-V® virtual server sale to further build a complete and differentiating solution. • Quickly grow your deal size by adding Backup Exec Agents and Options. • Cross-sell other Symantec solutions, such as Symantec Enterprise Vault™, Symantec™ Endpoint Protection or Symantec™ ApplicationHA, for comprehensive protection. • Provide additional add-on installation service opportunities to further grow your margin. Key features of Backup Exec 2012 • Unite physical and virtual machine backups. Only Symantec Backup Exec™ with V-Ray technology offers flexible backup and recovery capabilities, deduplication, and policy management across VMware, Hyper-V and physical server environments. • New! One Product! Any Recovery! Complete data, application, and disaster recovery for physical and virtual environments from a single console. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Listener Feedback #127
Security Now! Transcript of Episode #320 Page 1 of 30 Transcript of Episode #320 Listener Feedback #127 Description: Steve and Leo discuss the week's major security events and discuss questions and comments from listeners of previous episodes. They tie up loose ends, explore a wide range of topics that are too small to fill their own episode, clarify any confusion from previous installments, and present real world 'application notes' for any of the security technologies and issues we have previously discussed. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-320.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-320-lq.mp3 Leo Laporte: This is Security Now! with Steve Gibson, Episode 320, recorded September 28, 2011: Your questions, Steve's answers, #127. It's time for Security Now!. The Kindle Edition, I have a feeling, this week. Steve Gibson is here. He is the man in charge at GRC.com, a security guru and expert. He's done 320 of these shows talking about protecting yourself online. And a good day to you, Steve. Steve Gibson: Well, it would be 320 had we had the foresight of numbering from zero. As it is, we've done 319, and this one is #320. Leo: I'm including this one. This is an extra one. Steve: I'll tell you, it's those little details that trip up programmers an unbelievable number of times, like how many numbers are there between numbers 7 and 10? It's like, okay, wait a minute. -

Peer Institution Research: Recommendations and Trends 2016
Peer Institution Research: Recommendations and Trends 2016 New Mexico State University Abstract This report evaluates the common technology services from New Mexico State University’s 15 peer institutions. Based on the findings, a summary of recommendations and trends are explained within each of the general areas researched: peer institution enrollment, technology fees, student computing, software, help desk services, classroom technology, equipment checkout and loan programs, committees and governing bodies on technology, student and faculty support, printing, emerging technologies and trends, homepage look & feel and ease of navigation, UNM and UTEP my.nmsu.edu comparison, top IT issues, and IT organization charts. Peer Institution Research 1 Table of Contents Peer Institution Enrollment ................................................................................. 3 Technology Fees ................................................................................................. 3 Student Computing ............................................................................................. 6 Software ............................................................................................................. 8 Help Desk Services .............................................................................................. 9 Classroom Technology ...................................................................................... 11 Equipment Checkout and Loan Programs ......................................................... -

Sonosite® Workflow Solutions
SonoSite® Workflow Solutions SWS Software FAQs for IT 1. Why does SWS require a server? The SonoSite Workflow Solutions (SWS™ software) server provides a single, secure location for storage of all images and data that are collected from multiple ultrasound systems. 2. What are the SWS server requirements? The minimum requirements for a SWS server are: Microsoft Windows Operating Systems (Server or Client) • Windows XP with SP3 • Windows Vista Business • Windows Server 2008 MacIntosh Operating System (Server or Client) • Mac® OS 10.5.6 or later System Requirments • CD-ROM drive • USB drive • Ethernet connectivity (wired or wireless) Minimum Server System Hardware Requirements • 2 GHz processor • 4 GB system memory • 250 GB hard disk space Additional requirements for Client • A browser: FireFox 3.5 or later, Internet Explorer 7.0 or later, or Safari 4.0 or later • Adobe Reader 8.1 or later (See www.adobe.com) • Adobe Media Player (See www.adobe.com) 3. How much disk storage space is really used? A sample system with approximately 13,000 complete ultrasound exams uses about 75 GB of storage space. 4. How is SWS installed? SWS server software is installed on both Mac and PC systems using a “Wizard” type installation tool. The software is distributed on a DVD. SWS Client software is installed on PCs and Macs using a web interface on the server PC (or Mac). 5. Who maintains the SWS server? The IT or BioMed group that supports the Emed department would normally maintain the server. 6. How is SWS data backed up? SonoSite provides data backup and restore software with SWS. -

List of TCP and UDP Port Numbers
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia Jump to: navigation, search In computer networking, the protocols of the Transport Layer of the Internet Protocol Suite, most notably the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), but also other protocols, use a numerical identifier for the data structures of the endpoints for host-to- host communications. Such an endpoint is known as a port and the identifier is the port number. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] Contents [hide] y 1 Table legend y 2 Well-known ports: 0±1023 y 3 Registered ports: 1024±49151 y 4 Dynamic, private or ephemeral ports: 49152±65535 y 5 See also y 6 References y 7 External links [edit] Table legend Color coding of table entries Official Port/application combination is registered with IANA Unofficial Port/application combination is not registered with IANA Conflict Port is in use for multiple applications [edit] Well-known ports: 0±1023 According to IANA "The Well Known Ports are assigned by the IANA and on most systems can only be used by system (or root) processes or by programs executed by privileged users. Ports are used in the TCP [RFC793] to name the ends of logical connections which carry long term conversations. For the purpose of providing services to unknown callers, a service contact port is defined. This list specifies the port used by the server process as its contact port. The contact port is sometimes called the well-known port."[1] Port TCP UDP Description Status 0 UDP Reserved Official When running a server on port 0, the system will run it on a random 0 TCP UDP port from 1-65535 or 1024-65535 depending on the privileges of Official the user. -
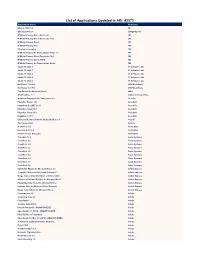
List of Applications Updated in ARL #2573
List of Applications Updated in ARL #2573 Application Name Publisher BIOS to UEFI 1.4 1E SyncBackPro 9.3 2BrightSparks M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct Connector 7.85 3M M*Modal Fluency Direct 3M M*Modal Fluency Flex 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.5 3T Software Labs Studio 3T 2020.7 3T Software Labs Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software Text Toolkit for Microsoft Excel 4Bits ASAP Utilities 7.7 A Must in Every Office Graphical Development Environment 3.2 Ab Initio PrizmDoc Server 13.8 AccuSoft ImageGear for .NET 24.11 AccuSoft PrizmDoc Client 13.8 AccuSoft PrizmDoc Client 13.9 AccuSoft ImagXpress 13.5 AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis True Image 2020 Acronis ActivePerl 5.12 ActiveState Komodo Edit 12.0 ActiveState ActivePerl 5.26 Enterprise ActiveState TransMac 12.6 Acute Systems CrossFont 6.5 Acute Systems CrossFont 6.6 Acute Systems CrossFont 6.2 Acute Systems CrossFont 5.5 Acute Systems CrossFont 5.6 Acute Systems CrossFont 6.3 Acute Systems CrossFont 5.7 Acute Systems CrossFont 6.0 Acute Systems Split Table Wizard for Microsoft Excel 2.3 Add-in Express Template Phrases for Microsoft Outlook 4.7 Add-in Express Merge Tables Wizard for Microsoft Excel 2018 Add-in Express Advanced -

Evaluation, Local Calibration, and Validation of Performance Prediction Models in Aashtowaretm Pavement ME Design Software Using NCAT Test Track Data
Evaluation, Local Calibration, and Validation of Performance Prediction Models in AASHTOWareTM Pavement ME Design Software Using NCAT Test Track Data by Xiaolong Guo A dissertation submitted to the Graduate Faculty of Auburn University in partial fulfillment of the requirements for the Degree of Doctor of Philosophy Auburn, Alabama May 6, 2017 Keywords: Pavement ME Design, Local Calibration, Input Level 1 Copyright 2017 by Xiaolong Guo Approved by David H. Timm, Chair, Brasfield & Gorrie Professor Randy West, Director of National Center for Asphalt Technology Nam Tran, Associate Research Professor Rod E. Turochy, Associate Professor of Civil Engineering Abstract The AASHTOWareTM Pavement ME Design software was adopted by the American Association of State Highway and Transportation Officials (AASHTO) for structural pavement designs. The performance prediction models in the software were only calibrated based on a national database of pavement sections in the U.S. and Canada. These models may not apply to local pavement designs due to insufficient adequacy. The National Center for Asphalt Technology (NCAT), equipped with a full-scale accelerated pavement Test Track and asphalt materials laboratory, supported this study on evaluation, local calibration, and validation of the rutting, bottom-up fatigue cracking, and IRI models. The NCAT database was developed with research-grade detail and accuracy and was locally-based regarding the information of materials, traffic, and climate, and field performance. In the process of local calibration, automation was used during software runs and data compiling to minimize human interaction with the computer. Considerable labor savings (100% reduction) and time savings (nearly 35% reduction) were gained. As for evaluation results, over-predictions by the nationally-calibrated rutting and bottom-up fatigue cracking model were seen for a majority of experimental sections, and local calibration reduced bias and standard error of the estimate.