Build a Secure Enterprise Machine Learning Platform on AWS AWS Technical Guide Build a Secure Enterprise Machine Learning Platform on AWS AWS Technical Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Social Media Job Expectations
Social Media Job Expectations Twitter @FHNtoday User 1Push all new content from FHNtoday.com and FHNgameday.com ● Push miscellaneous announcements ● User will focus on tagging people/groups when possible. ● Promote other social accounts weekly ● Push breaking news ● Check on Medium daily. ● Have at least 3 updates per week day ● Maintain look/profile of @FHNtoday ● Research this and brainstorm ways to make medium even stronger. Twitter @FHNtoday User 2 Push all new content from FHNgameday.com ● Push miscellaneous sports announcements ● User will focus on tagging people/groups when possible. ● Promote other social accounts weekly ● Push breaking sports news ● Check on Medium daily. ● Have at least 3 updates per week day ● Research this and brainstorm ways to make medium even stronger. Twitter @FHNtoday User 3: ● Maintain weekly analytics report ● User will focus on tagging people/groups when possible. ● Follow back accounts ● Follow new accounts ● Maintain lists ● Check on Medium daily. ● RT appropriate members of the community. 1 or 2 per day ● Reply to @mentions ● Utilize: https://analytics.twitter.com OK -- Pinterest User 1: Focus on school-related topics like Homecoming, Pep Assembly's, etc. ● Focus on at least one board per week with multiple postings per day ● Work to maintain and update previous related boards when appropriate ● Share information at least once per week with Facebook and Twitter User #1 to promote ● Work to maintain/increase followers/board followed ● Check on Medium daily. ● Maintain overall look/profile of account OK -- Pinterest User 2: ● Focusing on trending topics or things that are going viral. ● Focus on at least one board per week with multiple postings per day ● Work to maintain and update previous related boards when appropriate ● Share information at least once per week with Facebook and Twitter User #1 to promote ● Maintain weekly analytics of Pinterest ● Check on Medium daily. -

Security Analysis of Tumblr
Security Analysis of Tumblr 6.857 Spring 2017 Team Hackerman Remi Mir, Shruti Banda, Stephen Li, José Zúñiga Table of Contents Abstract 2 Introduction 2 What is Tumblr? 2 Motivation 2 Past Security Incidents 2 Principals and Actions 3 Guests 3 Users with Accounts 3 Group Users 4 Third Party Developers 4 Tumblr Corporation 4 Testing Methodology 4 Web Application 5 Burp Suite 6 Overview 6 Tests 6 Results 8 API 9 Overview 9 Tests 10 Invalid Inputs 10 Basic Scripting 11 Script Injection Attacks 12 Results 14 Conclusion 14 Summary 14 Recommendations 15 Further Work 15 Acknowledgements 16 References 16 1 Abstract Our project was to perform the security analysis of a popular microblogging site called Tumblr. The objective was to explore the different ways Tumblr ensures the protection of the information it collects from its users, and identify which areas it fails to secure. We especially focused on how Tumblr handles the security as per its privacy policy, including all relevant account information, e.g. username, password, age, and email address. We constructed a security analysis document summarizing our attempts to detect flaws in both the web application and the API. Our group identified strengths and weaknesses of the web application and the API, and drafted recommendations for solutions that Tumblr can implement to make the platform more secure for its users. Introduction What is Tumblr? Tumblr is a popular microblogging platform with more than 20 million users from the United States [1] and over 300 million blogs in total [2]. It is also among the top ten social networking sites worldwide in 2017 [3]. -

Effectiveness of Dismantling Strategies on Moderated Vs. Unmoderated
www.nature.com/scientificreports OPEN Efectiveness of dismantling strategies on moderated vs. unmoderated online social platforms Oriol Artime1*, Valeria d’Andrea1, Riccardo Gallotti1, Pier Luigi Sacco2,3,4 & Manlio De Domenico 1 Online social networks are the perfect test bed to better understand large-scale human behavior in interacting contexts. Although they are broadly used and studied, little is known about how their terms of service and posting rules afect the way users interact and information spreads. Acknowledging the relation between network connectivity and functionality, we compare the robustness of two diferent online social platforms, Twitter and Gab, with respect to banning, or dismantling, strategies based on the recursive censor of users characterized by social prominence (degree) or intensity of infammatory content (sentiment). We fnd that the moderated (Twitter) vs. unmoderated (Gab) character of the network is not a discriminating factor for intervention efectiveness. We fnd, however, that more complex strategies based upon the combination of topological and content features may be efective for network dismantling. Our results provide useful indications to design better strategies for countervailing the production and dissemination of anti- social content in online social platforms. Online social networks provide a rich laboratory for the analysis of large-scale social interaction and of their social efects1–4. Tey facilitate the inclusive engagement of new actors by removing most barriers to participate in content-sharing platforms characteristic of the pre-digital era5. For this reason, they can be regarded as a social arena for public debate and opinion formation, with potentially positive efects on individual and collective empowerment6. -

What Is Gab? a Bastion of Free Speech Or an Alt-Right Echo Chamber?
What is Gab? A Bastion of Free Speech or an Alt-Right Echo Chamber? Savvas Zannettou Barry Bradlyn Emiliano De Cristofaro Cyprus University of Technology Princeton Center for Theoretical Science University College London [email protected] [email protected] [email protected] Haewoon Kwak Michael Sirivianos Gianluca Stringhini Qatar Computing Research Institute Cyprus University of Technology University College London & Hamad Bin Khalifa University [email protected] [email protected] [email protected] Jeremy Blackburn University of Alabama at Birmingham [email protected] ABSTRACT ACM Reference Format: Over the past few years, a number of new “fringe” communities, Savvas Zannettou, Barry Bradlyn, Emiliano De Cristofaro, Haewoon Kwak, like 4chan or certain subreddits, have gained traction on the Web Michael Sirivianos, Gianluca Stringhini, and Jeremy Blackburn. 2018. What is Gab? A Bastion of Free Speech or an Alt-Right Echo Chamber?. In WWW at a rapid pace. However, more often than not, little is known about ’18 Companion: The 2018 Web Conference Companion, April 23–27, 2018, Lyon, how they evolve or what kind of activities they attract, despite France. ACM, New York, NY, USA, 8 pages. https://doi.org/10.1145/3184558. recent research has shown that they influence how false informa- 3191531 tion reaches mainstream communities. This motivates the need to monitor these communities and analyze their impact on the Web’s information ecosystem. 1 INTRODUCTION In August 2016, a new social network called Gab was created The Web’s information ecosystem is composed of multiple com- as an alternative to Twitter. -

Riots: a Comparative Study of Twitter and Parler
111 Capitol (Pat)riots: A comparative study of Twitter and Parler HITKUL, IIIT - Delhi, India AVINASH PRABHU∗, DIPANWITA GUHATHAKURTA∗, JIVITESH JAIN∗, MALLIKA SUBRA- MANIAN∗, MANVITH REDDY∗, SHRADHA SEHGAL∗, and TANVI KARANDIKAR∗, IIIT - Hy- derabad, India AMOGH GULATI∗ and UDIT ARORA∗, IIIT - Delhi, India RAJIV RATN SHAH, IIIT - Delhi, India PONNURANGAM KUMARAGURU, IIIT - Delhi, India On 6 January 2021, a mob of right-wing conservatives stormed the USA Capitol Hill interrupting the session of congress certifying 2020 Presidential election results. Immediately after the start of the event, posts related to the riots started to trend on social media. A social media platform which stood out was a free speech endorsing social media platform Parler; it is being claimed as the platform on which the riots were planned and talked about. Our report presents a contrast between the trending content on Parler and Twitter around the time of riots. We collected data from both platforms based on the trending hashtags and draw comparisons based on what are the topics being talked about, who are the people active on the platforms and how organic is the content generated on the two platforms. While the content trending on Twitter had strong resentments towards the event and called for action against rioters and inciters, Parler content had a strong conservative narrative echoing the ideas of voter fraud similar to the attacking mob. We also find a disproportionately high manipulation of traffic on Parler when compared to Twitter. Additional Key Words and Phrases: Social Computing, Data Mining, Social Media Analysis, Capitol Riots, Parler, Twitter 1 INTRODUCTION Misinformation of the United States of America’s presidential election results being fraudulent has been spreading across the world since the elections in November 2020.1 Public protests and legal cases were taking place across the states against the allegation of voter fraud and manhandling of mail-in ballots.2 This movement took a violent height when a mob attacked the Capitol Hill building to stop certification of Mr. -

Building Alexa Skills Using Amazon Sagemaker and AWS Lambda
Bootcamp: Building Alexa Skills Using Amazon SageMaker and AWS Lambda Description In this full-day, intermediate-level bootcamp, you will learn the essentials of building an Alexa skill, the AWS Lambda function that supports it, and how to enrich it with Amazon SageMaker. This course, which is intended for students with a basic understanding of Alexa, machine learning, and Python, teaches you to develop new tools to improve interactions with your customers. Intended Audience This course is intended for those who: • Are interested in developing Alexa skills • Want to enhance their Alexa skills using machine learning • Work in a customer-focused industry and want to improve their customer interactions Course Objectives In this course, you will learn: • The basics of the Alexa developer console • How utterances and intents work, and how skills interact with AWS Lambda • How to use Amazon SageMaker for the machine learning workflow and for enhancing Alexa skills Prerequisites We recommend that attendees of this course have the following prerequisites: • Basic familiarity with Alexa and Alexa skills • Basic familiarity with machine learning • Basic familiarity with Python • An account on the Amazon Developer Portal Delivery Method This course is delivered through a mix of: • Classroom training • Hands-on Labs Hands-on Activity • This course allows you to test new skills and apply knowledge to your working environment through a variety of practical exercises • This course requires a laptop to complete lab exercises; tablets are not appropriate Duration One Day Course Outline This course covers the following concepts: • Getting started with Alexa • Lab: Building an Alexa skill: Hello Alexa © 2018, Amazon Web Services, Inc. -
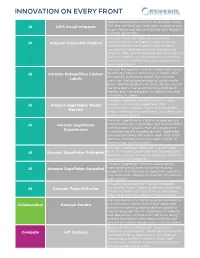
Innovation on Every Front
INNOVATION ON EVERY FRONT AWS DeepComposer uses AI to compose music. AI AWS DeepComposer The new service gives developers a creative way to get started and become familiar with machine learning capabilities. Amazon Transcribe Medical is a machine AI Amazon Transcribe Medical learning service that makes it easy to quickly create accurate transcriptions from medical consultations between patients and physician dictated notes, practitioner/patient consultations, and tele-medicine are automatically converted from speech to text for use in clinical documen- tation applications. Amazon Rekognition Custom Labels helps users AI Amazon Rekognition Custom identify the objects and scenes in images that are specific to business needs. For example, Labels users can find corporate logos in social media posts, identify products on store shelves, classify machine parts in an assembly line, distinguish healthy and infected plants, or detect animated characters in videos. Amazon SageMaker Model Monitor is a new AI Amazon SageMaker Model capability of Amazon SageMaker that automatically monitors machine learning (ML) Monitor models in production, and alerts users when data quality issues appear. Amazon SageMaker is a fully managed service AI Amazon SageMaker that provides every developer and data scientist with the ability to build, train, and deploy ma- Experiments chine learning (ML) models quickly. SageMaker removes the heavy lifting from each step of the machine learning process to make it easier to develop high quality models. Amazon SageMaker Debugger is a new capa- AI Amazon SageMaker Debugger bility of Amazon SageMaker that automatically identifies complex issues developing in machine learning (ML) training jobs. Amazon SageMaker Autopilot automatically AI Amazon SageMaker Autopilot trains and tunes the best machine learning models for classification or regression, based on your data while allowing to maintain full control and visibility. -
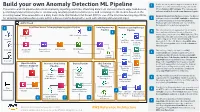
Build Your Own Anomaly Detection ML Pipeline
Device telemetry data is ingested from the field Build your own Anomaly Detection ML Pipeline 1 devices on a near real-time basis by calls to the This end-to-end ML pipeline detects anomalies by ingesting real-time, streaming data from various network edge field devices, API via Amazon API Gateway. The requests get performing transformation jobs to continuously run daily predictions/inferences, and retraining the ML models based on the authenticated/authorized using Amazon Cognito. incoming newer time series data on a daily basis. Note that Random Cut Forest (RCF) is one of the machine learning algorithms Amazon Kinesis Data Firehose ingests the data in for detecting anomalous data points within a data set and is designed to work with arbitrary-dimensional input. 2 real time, and invokes AWS Lambda to transform the data into parquet format. Kinesis Data AWS Cloud Firehose will automatically scale to match the throughput of the data being ingested. 1 Real-Time Device Telemetry Data Ingestion Pipeline 2 Data Engineering Machine Learning Devops Pipeline Pipeline The telemetry data is aggregated on an hourly 3 3 basis and re-partitioned based on the year, month, date, and hour using AWS Glue jobs. The Amazon Cognito AWS Glue Data Catalog additional steps like transformations and feature Device #1 engineering are performed for training the SageMaker AWS CodeBuild Anomaly Detection ML Model using AWS Glue Notebook Create ML jobs. The training data set is stored on Amazon Container S3 Data Lake. Amazon Kinesis AWS Lambda S3 Data Lake AWS Glue Device #2 Amazon API The training code is checked in an AWS Gateway Data Firehose 4 AWS SageMaker CodeCommit repo which triggers a Machine Training CodeCommit Containers Learning DevOps (MLOps) pipeline using AWS Dataset for Anomaly CodePipeline. -

Cloud Computing & Big Data
Cloud Computing & Big Data PARALLEL & SCALABLE MACHINE LEARNING & DEEP LEARNING Ph.D. Student Chadi Barakat School of Engineering and Natural Sciences, University of Iceland, Reykjavik, Iceland Juelich Supercomputing Centre, Forschungszentrum Juelich, Germany @MorrisRiedel LECTURE 11 @Morris Riedel @MorrisRiedel Big Data Analytics & Cloud Data Mining November 10, 2020 Online Lecture Review of Lecture 10 –Software-As-A-Service (SAAS) ▪ SAAS Examples of Customer Relationship Management (CRM) Applications (PAAS) (introducing a growing range of machine (horizontal learning and scalability artificial enabled by (IAAS) intelligence Virtualization capabilities) in Clouds) [5] AWS Sagemaker [4] Freshworks Web page [3] ZOHO CRM Web page modfied from [2] Distributed & Cloud Computing Book [1] Microsoft Azure SAAS Lecture 11 – Big Data Analytics & Cloud Data Mining 2 / 36 Outline of the Course 1. Cloud Computing & Big Data Introduction 11. Big Data Analytics & Cloud Data Mining 2. Machine Learning Models in Clouds 12. Docker & Container Management 13. OpenStack Cloud Operating System 3. Apache Spark for Cloud Applications 14. Online Social Networking & Graph Databases 4. Virtualization & Data Center Design 15. Big Data Streaming Tools & Applications 5. Map-Reduce Computing Paradigm 16. Epilogue 6. Deep Learning driven by Big Data 7. Deep Learning Applications in Clouds + additional practical lectures & Webinars for our hands-on assignments in context 8. Infrastructure-As-A-Service (IAAS) 9. Platform-As-A-Service (PAAS) ▪ Practical Topics 10. Software-As-A-Service -

Google and Yelp Reviews of Early Care and Education in Georgia
Google and Yelp Reviews as a Window into Public Perceptions of Early Care and Education in Georgia Diane M. Early and Weilin Li Introduction In recent years, federal programs and policies such as the 2014 reauthorization of the Child Care Development Block Grant (CCDBG) Act1 and the Race to the Top–Early Learning Challenge2 have brought increased attention to improving families’ access to high-quality early care and education (ECE). In response to this increased focus, Child Trends worked with the Office of Planning, Research, and Evaluation, an office of the Administration for Children and Families in the U.S. Department of Health and Human Services, to create a guidebook defining ECE access for policymakers and researchers. This resource’s definition of ECE access includes four primary dimensions: (1) requiring reasonable effort to locate and enroll a child in a care arrangement that is (2) affordable, (3) supports the child’s development, and (4) meets parents’ needs.3 Despite this progress in defining ECE access, researchers and policymakers know relatively little about how families and the general public view ECE access or the extent to which the public’s values match professional definitions. This Child Trends study, funded by Georgia’s Department of Early Care and Learning (DECAL), is a first step toward filling that gap. Using publicly available Google and Yelp reviews of ECE programs in Georgia, we aimed to better understand how the public views ECE access. Additionally, we analyzed associations between star ratings provided by the public on these rating platforms and star ratings assigned by Georgia’s Quality Rated system. -

Medium Post (15%) You Will Pick One of Your Blog Posts Or Written Assignments and Convert It Into a Medium Post, Or Write a New One on a Completely Different Topic
Social Media 3307 Final Assignment – Medium Post (15%) You will pick one of your blog posts or written assignments and convert it into a Medium post, or write a new one on a completely different topic. You will write and edit this post throughout the last month of class with input from your classmates. Getting Started with Medium.com Medium.com is a website where anyone can publish content. Content can be collected into publications, which are like online magazines. We are going to create a publication for this class about social media, and each of you will be writing an article for it. Create an account on Medium.com using your Facebook, Twitter, or Google account, or create a new account using your email. Decide whether you want to use your “real name,” or a pseudonym. If the latter, don’t use an account or email to sign up that is linked to your real name. Find at least three Medium articles that you think are interesting or that are well-shared (there is a lot of bad content on Medium, just as in any user-generated content site). Get a sense for the writing style on Medium and what types of topics people write about. Click on “Top Stories” on the top navigation bar, or look at what’s bubbled up in an area you’re interested in - Picking a topic Generally, you should be writing about social media, but you can pick any topic that you’d like. Taking an existing paper or blog post to edit or expand upon is one possibility, as is exploring something you’re interested in but haven’t had the opportunity to tackle yet. -

Analytics Lens AWS Well-Architected Framework Analytics Lens AWS Well-Architected Framework
Analytics Lens AWS Well-Architected Framework Analytics Lens AWS Well-Architected Framework Analytics Lens: AWS Well-Architected Framework Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. Analytics Lens AWS Well-Architected Framework Table of Contents Abstract ............................................................................................................................................ 1 Abstract .................................................................................................................................... 1 Introduction ...................................................................................................................................... 2 Definitions ................................................................................................................................. 2 Data Ingestion Layer ........................................................................................................... 2 Data Access and Security Layer ............................................................................................ 3 Catalog and Search Layer ...................................................................................................