The Terrorist Naval Mine/Underwater Improvised Explosive Device Threat
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

United States Navy and World War I: 1914–1922
Cover: During World War I, convoys carried almost two million men to Europe. In this 1920 oil painting “A Fast Convoy” by Burnell Poole, the destroyer USS Allen (DD-66) is shown escorting USS Leviathan (SP-1326). Throughout the course of the war, Leviathan transported more than 98,000 troops. Naval History and Heritage Command 1 United States Navy and World War I: 1914–1922 Frank A. Blazich Jr., PhD Naval History and Heritage Command Introduction This document is intended to provide readers with a chronological progression of the activities of the United States Navy and its involvement with World War I as an outside observer, active participant, and victor engaged in the war’s lingering effects in the postwar period. The document is not a comprehensive timeline of every action, policy decision, or ship movement. What is provided is a glimpse into how the 20th century’s first global conflict influenced the Navy and its evolution throughout the conflict and the immediate aftermath. The source base is predominately composed of the published records of the Navy and the primary materials gathered under the supervision of Captain Dudley Knox in the Historical Section in the Office of Naval Records and Library. A thorough chronology remains to be written on the Navy’s actions in regard to World War I. The nationality of all vessels, unless otherwise listed, is the United States. All errors and omissions are solely those of the author. Table of Contents 1914..................................................................................................................................................1 -

Tordess Oeeupiedi
THE SCOTTISH CAMPAIGN TO RESIST THE ATOMIC MENACE,2 AINSLIE PLACE,E~INBURGH.031-2?5 7752 ISSN 0140- 7340 No 8 October/November 1978 lOp TORDESS OEEUPIEDI ---protesters rebuild cottage---- On 30th September the date on which the tenant farmers on the Torness site gave up their land to the SSEB, the 15 members of the Torness Alliance moved on. Supported by a group of similar size outwith the site; they immediately began to rebuild the derilict 'Half Moon' cottage, which is seen as a base for the occupation. This m·ove, to non-violent direct action and civil disobedience, was not taken without careful thought and planning.Clearly Mr. Millan, the Secretary of State, has decided to turn a deaf ear to any objections to Torness - whether they come from anyi- nuclear groups or the Labour · controlled Lothian Regional Council~ Thus, in the spirit of the Torness declaration, non-violent direct action is the only option availabl e if the power sta!on is to be stopped. DE COMMISSIONING FRIENDLY THE HIDDEN PROBLEMS Those participating (from all over Britain) British nuclear This statement, however, carefully planned this companies have deliberately flies i n the face of action; and of necessit y played down the difficulties evidence , both from t he trained in non-violent involved in scrapping atomic United States and the A. E.A's techniques. This planning pl ant. own sc-ientists. Their has paid off the l ocal report s claim t hat outworn community has rallied round According to a r.ecent plants are highly radioact ive in support and materials for 'Guardian' repor.t the Atomic and should be l eft for the reconstruction of the Ener gy Authority "is certain 100- 150 years for the cottage have been readily · that i t could demolish a r adi at ion t o " cool down" ma.de available; and the· nuclear react or local police have been comprehensivel y enough to b efoo=~=~]J univer sally friendly. -

Shipping and Port Security: Challenges and Legal Aspects
The Business and Management Review, Volume 10 Number 5 December 2019 Shipping and port security: Challenges and legal aspects Zillur Rahman Bhuiyan Managing Director, Marinecare Consultants Bangladesh Ltd. Marine Consultant in Maritime Safety and Security Key Words Globalization, ISPS Code, maritime transport system, security threats, UNCLOS. Abstract The current trend of globalization provides intense impact on access to resources, raw materials and markets, expedited by modern maritime transport system comprising shipping and port operations. Security of ships and port facilities, thus, discernibly an enormous challenge to the globalized world. The international maritime transport system is vulnerable to piracy, terrorism, illegal drug trafficking, gun-running, human smuggling, maritime theft, fraud, damage to ships & port facilities, illegal fishing and pollution, which can all disrupt maritime supply chains to the heavy cost of the global economy. This paper discusses the nature and effect of the security threats to the international shipping and port industry with impact on the international trade & commerce and governmental economy, taking into consideration of the emerging geopolitics, Sea Lines of Communication, chokepoints of maritime trading routes and autonomous ships. The existing legislative measures against maritime security appraised and evolution of automation and digitalization of shipping and port operations taken into consideration. Studying the contemporary maritime transport reviews, existing legislation and the threat scenarios to the shipping and port operations, this paper identifies further advancement to the existing maritime security legislation in respect of piracy and terrorism at sea, and recommends amendment to the International Ship and Port Security (ISPS) Code under the SOLAS Convention. 1 Introduction Globalization is based on the unrestricted movement of commodities, resources, information and people enhancing international trade and commerce through connectivity between the places of production and places of consumption. -

Naval Shipbuilding Expansion: the World War II Surface Combatant Experience
Naval Shipbuilding Expansion: The World War II Surface Combatant Experience Dr. Norbert Doerry and Dr. Philip Koenig Naval Sea Systems Command David W. Taylor Lecture Series Naval Surface Warfare Center Carderock Division June 13, 2019 From material originally presented at: SNAME Maritime Convention 2018, Providence, RI, Oct 24-26, 2018 and 16th Annual Acquisition Research Symposium, Monterey, CA, 8-9 May 2019 10/24/2018 Statement A: Approved for Release. Distribution is Unlimited. 1 Introduction • The post-Cold War “Peace Dividend” era is over • “Overt challenges to the free and open international order and the re-emergence of long- term, strategic competition between nations.” (DoD 2018) • Possibility of non-nuclear, industrial-scale war has re-emerged. What can we learn from the last time we engaged in industrial-scale war? 10/24/2018 Statement A: Approved for Release. Distribution is Unlimited. 2 U.S. Destroyer Acquisition Eras World War I Era (up to 1922) • 68 destroyers commissioned prior to U.S. entry into WW I — One would serve in WW II • 273 “Flush-Deckers” acquired in response to U.S. entry into WW I — 41 commissioned prior to end of hostilities — The rest were commissioned after WW I — 105 lost or scrapped prior to WW II, remainder served in WWII Treaty Period (1922-1936) USS Fletcher (DD 445) underway off New York, 18 July 1942 • Limitations placed on displacement, weapons, and number (www.history.navy.mil – 19-N-31245) • Torpedo tubes and 5 inch guns were the primary weapon systems • 61 destroyers in seven classes procured Pre-War (1936-1941) • Designs modified to reflect experiences of foreign navies in combat — Lend-Lease prepared industry for production ramp-up • 182 destroyers in four classes authorized • 39 in commission upon U.S. -

Winning the Salvo Competition Rebalancing America’S Air and Missile Defenses
WINNING THE SALVO COMPETITION REBALANCING AMERICA’S AIR AND MISSILE DEFENSES MARK GUNZINGER BRYAN CLARK WINNING THE SALVO COMPETITION REBALANCING AMERICA’S AIR AND MISSILE DEFENSES MARK GUNZINGER BRYAN CLARK 2016 ABOUT THE CENTER FOR STRATEGIC AND BUDGETARY ASSESSMENTS (CSBA) The Center for Strategic and Budgetary Assessments is an independent, nonpartisan policy research institute established to promote innovative thinking and debate about national security strategy and investment options. CSBA’s analysis focuses on key questions related to existing and emerging threats to U.S. national security, and its goal is to enable policymakers to make informed decisions on matters of strategy, security policy, and resource allocation. ©2016 Center for Strategic and Budgetary Assessments. All rights reserved. ABOUT THE AUTHORS Mark Gunzinger is a Senior Fellow at the Center for Strategic and Budgetary Assessments. Mr. Gunzinger has served as the Deputy Assistant Secretary of Defense for Forces Transformation and Resources. A retired Air Force Colonel and Command Pilot, he joined the Office of the Secretary of Defense in 2004. Mark was appointed to the Senior Executive Service and served as Principal Director of the Department’s central staff for the 2005–2006 Quadrennial Defense Review. Following the QDR, he served as Director for Defense Transformation, Force Planning and Resources on the National Security Council staff. Mr. Gunzinger holds an M.S. in National Security Strategy from the National War College, a Master of Airpower Art and Science degree from the School of Advanced Air and Space Studies, a Master of Public Administration from Central Michigan University, and a B.S. in chemistry from the United States Air Force Academy. -

Navy Shipboard Lasers for Surface, Air, and Missile Defense: Background and Issues for Congress
Navy Shipboard Lasers for Surface, Air, and Missile Defense: Background and Issues for Congress Ronald O'Rourke Specialist in Naval Affairs December 9, 2010 Congressional Research Service 7-5700 www.crs.gov R41526 CRS Report for Congress Prepared for Members and Committees of Congress Navy Shipboard Lasers for Surface, Air, and Missile Defense Summary Department of Defense (DOD) development work on high-energy military lasers, which has been underway for decades, has reached the point where lasers capable of countering certain surface and air targets at ranges of about a mile could be made ready for installation on Navy surface ships over the next few years. More powerful shipboard lasers, which could become ready for installation in subsequent years, could provide Navy surface ships with an ability to counter a wider range of surface and air targets at ranges of up to about 10 miles. These more powerful lasers might, among other things, provide Navy surface ships with a terminal-defense capability against certain ballistic missiles, including the anti-ship ballistic missile (ASBM) that China is believed to be developing. The Navy and DOD are developing three principal types of lasers for potential use on Navy surface ships—fiber solid state lasers (SSLs), slab SSLs, and free electron lasers (FELs). The Navy’s fiber SSL prototype demonstrator is called the Laser Weapon System (LaWS). Among DOD’s multiple efforts to develop slab SSLs for military use is the Maritime Laser Demonstration (MLD), a prototype laser weapon developed as a rapid demonstration project. The Navy has developed a lower-power FEL prototype and is now developing a prototype with scaled-up power. -

2018 Hawaii Football MG.Pdf
Photos credited to: Chicago Bears, Denver Broncos, USA Today, Detroit Lions, Andy Lyons Getty images, Hamilton Tiger-Cats, BC Lions WHAT’S INSIDE TABLE OF CONTENTS 2018 SCHEDULE Date Opponent Time Table of Contents __________________________ 1 Aug. 25 at Colorado State* (CBSSN) 5:30 pm MT Quick Facts ______________________________2-3 97 HISTORY Media Information ________________________4-5 History of UH Football _________________ 97-101 Sept. 1 NAVY (CBSSN) 5:00 pm Bowl Games Media Outlets _____________________________ 6 Sept. 8 RICE (Spectrum) 6:00 pm Aloha Stadium ____________________________ 7 Bowl Game History __________________ 102 Sept. 15 at Army (CBSSN) 12:00 pm ET Bowl Appearances ______________ 103-108 Sept. 22 DUQUESNE (HC) (Spectrum) 6:00 pm RAINBOW WARRIOR FOOTBALL Bowl Game Record Book _____________ 109 8 National Appearances Sept. 29 at San José State* (Spectrum) TBA Head Coach Nick Rolovich _________________8-9 National Television __________________ 110 Oct. 6 WYOMING* (Spectrum) 6:00 pm Assistant Coaches _____________________ 10-14 National Rankings ___________________ 111 Support Staff & Graduate Assistants _________ 15 Coaches & Players Oct. 13 at Brigham Young (ESPN Family) TBA Rosters ______________________________ 16-17 All-Time Head Coaches _______________ 112 Oct. 20 NEVADA* (Spectrum) 6:00 pm Geographical Roster/Pronunciation Chart _____ 18 All-Time Assistant Coaches ___________ 113 Oct. 27 at Fresno State* (ESPN Family) TBA Returning Player Profiles ________________ 20-39 All-Time Letterwinners ___________ 114-121 2018 Recruiting Class Profiles ___________ 40-45 All-Time Homecoming Results _____________ 121 Nov. 3 UTAH STATE* (Spectrum) 6:00 pm 2018 Opponents ______________________ 46-50 Stats & Results Nov. 17 UNLV* (Spectrum) 6:00 pm Rivalry Games ___________________________ 50 Year-by-Year Statistics ___________ 122-123 Nov. -
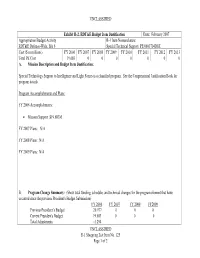
BA-6, Management Support Because It Includes Studies and Analyses in Support of R&D Efforts
UNCLASSIFIED Exhibit R-2, RDT&E Budget Item Justification Date: February 2007 Appropriation/Budget Activity R-1 Item Nomenclature: RDT&E Defense-Wide, BA 6 Special Technical Support PE 0603704D8Z Cost ($ in millions) FY 2006 FY 2007 FY 2008 FY 2009 FY 2010 FY 2011 FY 2012 FY 2013 Total PE Cost 19.683 0 0 0 0 0 0 0 A. Mission Description and Budget Item Justification: Special Technology Support to Intelligence and Light Forces is a classified program. See the Congressional Justification Book for program details. Program Accomplishments and Plans: FY 2006 Accomplishments: • Mission Support $19.683M FY 2007 Plans: N/A FY 2008 Plans: N/A FY 2009 Plans: N/A B. Program Change Summary: (Show total funding, schedule, and technical changes for the program element that have occurred since the previous President's Budget Submission) FY 2006 FY 2007 FY 2008 FY2009 Previous President’s Budget 20.977 0 0 0 Current President's Budget 19.683 0 0 0 Total Adjustments -1.294 UNCLASSIFIED R-1 Shopping List Item No. 125 Page 1 of 2 UNCLASSIFIED Congressional program reductions Congressional rescissions Congressional increases Other Adjustments -1.294 FY 2006: Congressional add transferred to other activity FY 2007: Funding transferred out of USD-I C. Other Program Funding Summary: Not Applicable D. Acquisition Strategy: Not Applicable E. Performance Metrics: Classified UNCLASSIFIED R-1 Shopping List Item No. 125 Page 2 of 2 UNCLASSIFIED FY 2007 RDT&E,D BUDGET ITEM JUSTIFICATION SHEET DATE: FEBRUARY 2007 Exhibit R-2 BUDGET ACTIVITY: 06 PROGRAM ELEMENT: 0603757D8Z PROGRAM ELEMENT TITLE: TRAINING TRANSFORMATION (T2) PROJECT NUMBER: PROJECT TITLE: GENERAL COMMENTS: As directed in the National Defense Authorization Act for FY 2005, all RDT&E funding for U.S. -

Northland Tourism Product Directory 2017 Paddle Boarding at the Poor Knights Islands Northland Welcome 1
Northland Tourism Product Directory 2017 Paddle boarding at the Poor Knights Islands Northland Welcome 1 Cape Reinga - Te Rerenga Wairua Welcome The Northland Tourism Product Directory is attractions. Our marine activities deserve a special mention. Dive an essential tool for sellers and distributors of expert Jacques Cousteau rated The Poor Knights, a marine reserve Northland holidays and conferences. off the Tutukaka Coast, as one of the top-ten dive sites in the world. For marine lovers and water sport enthusiasts the Bay of Islands is Subtropical Northland begins only one hour’s drive north of an aquatic playground. There is a range of professional Northland Auckland. Renowned for spectacular coastlines, marine reserves tourism operators that offer water-based tours including dolphin and kauri forests - the natural landscape is our speciality. viewing and swimming, charters and lessons. Accommodation options range from luxury lodges and upmarket retreats, to hotels, In addition to our scenic offerings, Northland is home to world-class motels, farmstays, B&Bs and holiday parks. You can opt for a bit luxury resorts, golf courses, and has an abundance of walking tracks of luxury perched high on a cliff top overlooking the sea, a bush and a new cycle trail which links the east and west coasts. We are hideaway set in subtropical gardens, or the ultimate glamping a land of firsts. Not only did the first Mäori canoe land on Northland experience. Northland has it all. shores; it was also where the first European settlers arrived, New Zealand's favourite domestic holiday destination, Northland's accommodation options range from luxury lodges and upmarket retreats, to hotels, motels, farmstays, B&Bs and holiday parks. -

Navy Irregular Warfare and Counterterrorism Operations: Background and Issues for Congress
Navy Irregular Warfare and Counterterrorism Operations: Background and Issues for Congress Ronald O'Rourke Specialist in Naval Affairs November 8, 2011 Congressional Research Service 7-5700 www.crs.gov RS22373 CRS Report for Congress Prepared for Members and Committees of Congress Navy Role in Irregular Warfare and Counterterrorism Summary The Navy for several years has carried out a variety of irregular warfare (IW) and counterterrorism (CT) activities. Among the most readily visible of the Navy’s recent IW operations have been those carried out by Navy sailors serving ashore in Afghanistan and Iraq. Many of the Navy’s contributions to IW operations around the world are made by Navy individual augmentees (IAs)—individual Navy sailors assigned to various DOD operations. The May 1-2, 2011, U.S. military operation in Abbottabad, Pakistan, that killed Osama bin Laden reportedly was carried out by a team of 23 Navy special operations forces, known as SEALs (an acronym standing for Sea, Air, and Land). The SEALs reportedly belonged to an elite unit known unofficially as Seal Team 6 and officially as the Naval Special Warfare Development Group (DEVGRU). The Navy established the Navy Expeditionary Combat Command (NECC) informally in October 2005 and formally in January 2006. NECC consolidated and facilitated the expansion of a number of Navy organizations that have a role in IW operations. The Navy established the Navy Irregular Warfare Office in July 2008, published a vision statement for irregular warfare in January 2010, and established “a community of interest” to develop and advance ideas, collaboration, and advocacy related to IW in December 2010. -

CNA's Integrated Ship Database
CNA’s Integrated Ship Database Second Quarter 2012 Update Gregory N. Suess • Lynette A. McClain CNA Interactive Software DIS-2012-U-003585-Final January 2013 Photo credit “Description: (Cropped Version) An aerial view of the aircraft carriers USS INDEPENDENCE (CV 62), left, and USS KITTY HAWK (CV 63), right, tied up at the same dock in preparation for the change of charge during the exercise RIMPAC '98. Location: PEARL HARBOR, HAWAII (HI) UNITED STATES OF AMERICA (USA) The USS INDEPENDENCE was on its way to be decommissioned, it was previously home ported in Yokosuka, Japan. The crew from the USS INDEPENDENCE cross decked onto the USS KITTY HAWK and brought it back to Atsugi, Japan. The USS INDEPENDENCE was destined for a ship yard in Washington. Source: ID"DN-SD- 00-01114 / Service Depicted: Navy / 980717-N-3612M-001 / Operation / Series: RIMPAC `98. Author: Camera Operator: PH1(NAC) JAMES G. MCCARTER,” Jul. 17, 1998, WIKIMEDIA COMMONS, last accessed Dec. 20, 2012, at http://commons.wikimedia.org/wiki/File:USS_Independence_(CV- 62)_and_USS_Kitty_Hawk_(CV-63)_at_Pearl_Harbor_crop.jpg Approved for distribution: January 2013 Dr. Barry Howell Director, Warfare Capabilities and Employment Team Operations and Tactics Analysis This document represents the best opinion of CNA at the time of issue. It does not necessarily represent the opinion of the Department of the Navy. APPROVED FOR PUBLIC RELEASE. DISTRIBUTION UNLIMITED. Copies of this document can be obtained through the Defense Technical Information Center at www.dtic.mil or contact CNA Document Control and Distribution Section at 703-824-2123. Copyright 2013 CNA This work was created in the performance of Federal Government Contract Number N00014-11-D-0323. -

And Financial Implications of Unmanned
Disruptive Innovation and Naval Power: Strategic and Financial Implications of Unmanned Underwater Vehicles (UUVs) and Long-term Underwater Power Sources MASSACHUsf TTT IMef0hrE OF TECHNOLOGY by Richard Winston Larson MAY 0 8 201 S.B. Engineering LIBRARIES Massachusetts Institute of Technology, 2012 Submitted to the Department of Mechanical Engineering in partial fulfillment of the requirements for the degree of Master of Science in Mechanical Engineering at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY February 2014 © Massachusetts Institute of Technology 2014. All rights reserved. 2) Author Dep.atment of Mechanical Engineering nuaryL5.,3014 Certified by.... Y Douglas P. Hart Professor of Mechanical Engineering Tbesis Supervisor A ccepted by ....................... ........ David E. Hardt Ralph E. and Eloise F. Cross Professor of Mechanical Engineering 2 Disruptive Innovation and Naval Power: Strategic and Financial Implications of Unmanned Underwater Vehicles (UUVs) and Long-term Underwater Power Sources by Richard Winston Larson Submitted to the Department of Mechanical Engineering on January 15, 2014, in partial fulfillment of the requirements for the degree of Master of Science in Mechanical Engineering Abstract The naval warfare environment is rapidly changing. The U.S. Navy is adapting by continuing its blue-water dominance while simultaneously building brown-water ca- pabilities. Unmanned systems, such as unmanned airborne drones, are proving piv- otal in facing new battlefield challenges. Unmanned underwater vehicles (UUVs) are emerging as the Navy's seaborne equivalent of the Air Force's drones. Representing a low-end disruptive technology relative to traditional shipborne operations, UUVs are becoming capable of taking on increasingly complex roles, tipping the scales of battlefield entropy. They improve mission outcomes and operate for a fraction of the cost of traditional operations.