Aviation Security Management Praeger Security International Advisory Board Board Cochairs Loch K
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IATA CLEARING HOUSE PAGE 1 of 21 2021-09-08 14:22 EST Member List Report
IATA CLEARING HOUSE PAGE 1 OF 21 2021-09-08 14:22 EST Member List Report AGREEMENT : Standard PERIOD: P01 September 2021 MEMBER CODE MEMBER NAME ZONE STATUS CATEGORY XB-B72 "INTERAVIA" LIMITED LIABILITY COMPANY B Live Associate Member FV-195 "ROSSIYA AIRLINES" JSC D Live IATA Airline 2I-681 21 AIR LLC C Live ACH XD-A39 617436 BC LTD DBA FREIGHTLINK EXPRESS C Live ACH 4O-837 ABC AEROLINEAS S.A. DE C.V. B Suspended Non-IATA Airline M3-549 ABSA - AEROLINHAS BRASILEIRAS S.A. C Live ACH XB-B11 ACCELYA AMERICA B Live Associate Member XB-B81 ACCELYA FRANCE S.A.S D Live Associate Member XB-B05 ACCELYA MIDDLE EAST FZE B Live Associate Member XB-B40 ACCELYA SOLUTIONS AMERICAS INC B Live Associate Member XB-B52 ACCELYA SOLUTIONS INDIA LTD. D Live Associate Member XB-B28 ACCELYA SOLUTIONS UK LIMITED A Live Associate Member XB-B70 ACCELYA UK LIMITED A Live Associate Member XB-B86 ACCELYA WORLD, S.L.U D Live Associate Member 9B-450 ACCESRAIL AND PARTNER RAILWAYS D Live Associate Member XB-280 ACCOUNTING CENTRE OF CHINA AVIATION B Live Associate Member XB-M30 ACNA D Live Associate Member XB-B31 ADB SAFEGATE AIRPORT SYSTEMS UK LTD. A Live Associate Member JP-165 ADRIA AIRWAYS D.O.O. D Suspended Non-IATA Airline A3-390 AEGEAN AIRLINES S.A. D Live IATA Airline KH-687 AEKO KULA LLC C Live ACH EI-053 AER LINGUS LIMITED B Live IATA Airline XB-B74 AERCAP HOLDINGS NV B Live Associate Member 7T-144 AERO EXPRESS DEL ECUADOR - TRANS AM B Live Non-IATA Airline XB-B13 AERO INDUSTRIAL SALES COMPANY B Live Associate Member P5-845 AERO REPUBLICA S.A. -

FY2014 Aviation - Deferred Maintenance
FY2014 Aviation - Deferred Maintenance Project Cost Project Description Location House Project Title (1,000's) (City) District Brush cutting at 3 Interior Aviation airports back to original clearing Interior Interior Airport Brush-Cutting 90.0 limits: Stevens Village, Beaver and Fort Yukon – to improve Aviation 39 aviation safety District Southwest District Lighting Southwest 35 - 37 150.0 Various lighting replacement and repair in Southwest District Repairs District Brush Cutting on RSA 2/20 50.0 Brush cutting with excavator & hand brushing Klawock 34 Repair airport fencing (at At Cordova Airport, repair or replace 900 LF of deteriorated Valdez 100.0 6 Cordova) fencing. District Y-K Delta Airports 500.0 Contract for gravel stockpile for surfacing repairs Various 36 - 38 Brush Cutting on RSA 8/26 50.0 Brush Cutting on RSA 8/26 Haines 34 Replace equipment fuel storage tanks at (6) Interior Aviation airports; Ruby, Rampart, Lake Minchumina, Hughes, Chalkyitsik, Interior Fuel Storage Tank Bettles; in order to burn ultra low sulfur diesel, provide for 200.0 Aviation 38 - 39 Repair/Replacement economical bulk fuel delivery, and store enough fuel onsite to operate snow removal equipment for a normal winter season. Dist Enhance security through fencing and lights to prevent loss of expensive fuel due to theft. New Access Gate 35.0 Replace access gate Skagway 32 Valdez Repair airport fencing (at Nome) 50.0 At Nome Airport, repair or replace 250 LF of fencing. 6 District Old Harbor Airport 150.0 Replace deteriorated surface course Old harbor 35 -
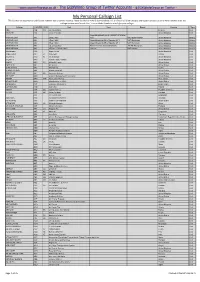
My Personal Callsign List This List Was Not Designed for Publication However Due to Several Requests I Have Decided to Make It Downloadable
- www.egxwinfogroup.co.uk - The EGXWinfo Group of Twitter Accounts - @EGXWinfoGroup on Twitter - My Personal Callsign List This list was not designed for publication however due to several requests I have decided to make it downloadable. It is a mixture of listed callsigns and logged callsigns so some have numbers after the callsign as they were heard. Use CTL+F in Adobe Reader to search for your callsign Callsign ICAO/PRI IATA Unit Type Based Country Type ABG AAB W9 Abelag Aviation Belgium Civil ARMYAIR AAC Army Air Corps United Kingdom Civil AgustaWestland Lynx AH.9A/AW159 Wildcat ARMYAIR 200# AAC 2Regt | AAC AH.1 AAC Middle Wallop United Kingdom Military ARMYAIR 300# AAC 3Regt | AAC AgustaWestland AH-64 Apache AH.1 RAF Wattisham United Kingdom Military ARMYAIR 400# AAC 4Regt | AAC AgustaWestland AH-64 Apache AH.1 RAF Wattisham United Kingdom Military ARMYAIR 500# AAC 5Regt AAC/RAF Britten-Norman Islander/Defender JHCFS Aldergrove United Kingdom Military ARMYAIR 600# AAC 657Sqn | JSFAW | AAC Various RAF Odiham United Kingdom Military Ambassador AAD Mann Air Ltd United Kingdom Civil AIGLE AZUR AAF ZI Aigle Azur France Civil ATLANTIC AAG KI Air Atlantique United Kingdom Civil ATLANTIC AAG Atlantic Flight Training United Kingdom Civil ALOHA AAH KH Aloha Air Cargo United States Civil BOREALIS AAI Air Aurora United States Civil ALFA SUDAN AAJ Alfa Airlines Sudan Civil ALASKA ISLAND AAK Alaska Island Air United States Civil AMERICAN AAL AA American Airlines United States Civil AM CORP AAM Aviation Management Corporation United States Civil -

AVIATION Disaster Litigation and Investigations
AVIATION Disaster Litigation and Investigations Attorney Advertising Our attorneys litigate diverse and complex cases for plane crash victims and their families throughout the world and injured crash survivors, as well as people who have suffered as a result of aviation security, safety, or passenger rights violations. At Motley Rice, our goal is not only to seek justice and compensation for our clients, but we also seek accountability from defendants and improvements in aviation safety and security standards. We give our clients a voice when they feel the most vulnerable. MARY F. SCHIAVO Licensed in DC, FL, MD, MO, SC JAMES R. BRAUCHLE Licensed in SC Our Approach At Motley Rice, our goal is not only to seek improvements in aviation safety and security standards through our civil justice system but also to give our clients a voice at a time in their lives when they feel the most vulnerable and to win for them the compensation they are owed and the changes they deserve. At Motley Rice, we work to help aviation disaster COMPASSION, GUIDANCE AND SUPPORT survivors and victims’ families, as well as victims We understand the pain, confusion and questions that of passenger rights violations and other safety and often follow tragic events and know that many clients security violations. feel overwhelmed by the emotional circumstances Our aviation attorneys have experience handling a which brought them to us. While coping with the loss wide variety of aviation cases. We recognize that of a loved one or the devastation of a permanent injury, survivors and family members of victims have many survivors and family members face numerous other concerns following an aviation disaster and may face obstacles such as medical expenses, loss of income considerations of complex legal rights and actions. -

Appendix 25 Box 31/3 Airline Codes
March 2021 APPENDIX 25 BOX 31/3 AIRLINE CODES The information in this document is provided as a guide only and is not professional advice, including legal advice. It should not be assumed that the guidance is comprehensive or that it provides a definitive answer in every case. Appendix 25 - SAD Box 31/3 Airline Codes March 2021 Airline code Code description 000 ANTONOV DESIGN BUREAU 001 AMERICAN AIRLINES 005 CONTINENTAL AIRLINES 006 DELTA AIR LINES 012 NORTHWEST AIRLINES 014 AIR CANADA 015 TRANS WORLD AIRLINES 016 UNITED AIRLINES 018 CANADIAN AIRLINES INT 020 LUFTHANSA 023 FEDERAL EXPRESS CORP. (CARGO) 027 ALASKA AIRLINES 029 LINEAS AER DEL CARIBE (CARGO) 034 MILLON AIR (CARGO) 037 USAIR 042 VARIG BRAZILIAN AIRLINES 043 DRAGONAIR 044 AEROLINEAS ARGENTINAS 045 LAN-CHILE 046 LAV LINEA AERO VENEZOLANA 047 TAP AIR PORTUGAL 048 CYPRUS AIRWAYS 049 CRUZEIRO DO SUL 050 OLYMPIC AIRWAYS 051 LLOYD AEREO BOLIVIANO 053 AER LINGUS 055 ALITALIA 056 CYPRUS TURKISH AIRLINES 057 AIR FRANCE 058 INDIAN AIRLINES 060 FLIGHT WEST AIRLINES 061 AIR SEYCHELLES 062 DAN-AIR SERVICES 063 AIR CALEDONIE INTERNATIONAL 064 CSA CZECHOSLOVAK AIRLINES 065 SAUDI ARABIAN 066 NORONTAIR 067 AIR MOOREA 068 LAM-LINHAS AEREAS MOCAMBIQUE Page 2 of 19 Appendix 25 - SAD Box 31/3 Airline Codes March 2021 Airline code Code description 069 LAPA 070 SYRIAN ARAB AIRLINES 071 ETHIOPIAN AIRLINES 072 GULF AIR 073 IRAQI AIRWAYS 074 KLM ROYAL DUTCH AIRLINES 075 IBERIA 076 MIDDLE EAST AIRLINES 077 EGYPTAIR 078 AERO CALIFORNIA 079 PHILIPPINE AIRLINES 080 LOT POLISH AIRLINES 081 QANTAS AIRWAYS -

Travel Information Örnsköldsvik Airport
w v TRAVEL INFORMATION TO AND FROM OER ÖRNSKÖLDSVIK AIRPORT // OVERVIEW Two airlines fly to Örnsköldsvik AirLeap fly from Stockholm Arlanda and BRA-Braathens fly from 1 Stockholm Bromma. 32 flights a week on average Many connections possible via 2 Stockholm’s airports. Örnsköldsvik is located 25 km from the airport, only 20 minutes 3 with Airport taxi or rental car. Book your travel via Air Leap (LPA) www.airleap.se BRA-Braathens Regional 4 Airlines (TF) www.flygbra.se CONNECTIONS WITH 2 AIRLINES GOOD CONNECTIONS good flight connections is essential for good business relationships and Örnsköldsvik Airport fulfills that requirement. As of 2 February, two airlines operate the airport, Air Leap and BRA – Braathens Regional Airlines. Air Leap (IATA code LPA) operates between Örnsköldsvik and Stockholm Arlanda Airport (ARN) and BRA (IATA code TF) between Örnsköldsvik och Stockholm Bromma Airport (BMA). Together the airlines offer on average 32 flights per week, in each direction. air leap operate Saab2000 with 50 Finnair is also a member of ”One minutes flight time to Örnsköldsvik. World Alliance” which gives bene- At Arlanda you find Air Leap at Termi- fits for its members and One World nal 3, with walking distance to Termi- members when travelling on flights nal 2 (SkyTeam, One World airlines) connected to the Finnair Network. and to Terminal 5 (Star Alliance air- Enclosed is a list of some of the lines). Tickets for connecting flights more common connections that are need to be purchased separately and currently possible with one ticket checked luggage brought through and checked in baggade to your customs at Arlanda and checked-in final destination. -

Albanian Passport Photo Requirements
Call 813-685-4343 For Your Photo Appointment Albanian Passport Photo Requirements Please Read Below For Details Prior To Visiting Our Studio: • Avoid white clothing because the portrait background for Albanian Passport Picture is white. • It is best to remove your glasses to eliminate any chances of rejection because of reflections. • Your expression must be neutral with no frowning or smiling. • You should be looking directly at the camera. Pictures even slightly in profile have been known to be rejected. • Your face should fill between at least 70% of the photo area. • Albanian Passport photographs must be taken by a professional studio. • Passport and Visa photo sizes and quantities of photos required change frequently. Please verify the photo specs with your embassy prior to visiting our studio. Feldman's Photography will create five identical Passport photos for Albania that will be exactly 40mm x 50mm. As required by the government in Albania there will be no hard shadows photographed on a solid white background. More Information about Albanian Passports: • The Albanian passport is a travel and identity document that is issued to citizens who are nationals of Albania, and allows them to travel abroad. The authority responsible for issuing Albanian Passports is the Ministry of Interior. • Starting in May 2009, the Albanian Government started issuing biometric passport and biometric ID card for its citizens. • From January 1, 2011 the biometric will be the only Albanian passport in circulation. To get this passport go to the Registry office of the municipality where the person is photographed, and all the fingerprints digitized. -

G the Aircraft Accident Investigation Board I
GTHE AIRCRAFT ACCIDENT INVESTIGATION BOARD I NORWAY HAV 02/93 REPORT ON THE CONVAIR 340/580 IN-PAA AIRCRAFT ACCIDENT NORTH OF HIRTSHALS, DENMARK, ON SEPTEMBER 8, 1989 SUBMITTED FEBRUARY 1993 THE AIRCRAFT ACCIDENT INVESTIGATION BOARD/ NORWAY HAV 02/93 REPORT ON THE CONVAIR 340/580 LN-PAA AIRCRAFT ACCIDENT NORTH OF HIRTSHALS, DENMARK, ON SEPTEMBER 8, 1989 Note: This is an extract in English of the official Norwegian report dated February 12, 1993. Any formal references required should be made to the original Norwegian report. It should be noted that the numbering of the paragraphs in this extract corresponds to the numbering in the original document. SUBMITTED FEBRUARY 1993 The Aircraft Accident Investigation Board has compiled this report for the purpose of improving flight safety. The object of any investigation is to identify faults or discrepancies which gay endanger flight safety. whether or not these are causal factors In the accident, and to recommend preventive action. It is not the Board's task to apportion blame or liability. Use of this report for any other purpose than for flight safety should be avoided. TABLE OF CONTENTS Page SYNOPSIS ... III • • • • • • • • • • • • • • • • • • • • • • • 2 SUMMARY .. 4 1 FACTUAL INFORMATION . ............... 5 1.1 History of the flight .••.••••.••..•..•.. 5 1.2 Injuries to persons 6 1.3 Damage to aircraft ...........•...•..•.... 6 1.4 other damage ............................ 7 1.5 Personnel information .•..••..•.•..•.••... 7 1.6 Aircraft information ..••..•.•...........• 7 1.7 Meteorological information .•............ 28 1.8 Aids to navigation ........•............. 29 1.9 Communications ...........•............... 29 1.10 Aerodrome information .......••..•......• 29 1.11 Flight recorders .......•..•....••........ 29 1.12 Wreckage and impact information .•..•....• 41 1.13 Medical and pathological information .•. -

Propuesta De Mejora De Los Servicios Logísticos En Tierra Del Aeropuerto El Alcaraván De Yopal – Casanare
Propuesta de Mejora de los Servicios Logísticos en Tierra del Aeropuerto El Alcaraván de Yopal – Casanare. Presentado por Leidy Paola Niño Rodríguez Fundaci´on Universitaria Los Libertadores Facultad de Ingenier´ıa y Ciencias B´asicas Programa de Ingenier´ıa Aeron´autica Bogot´a D.C, Colombia 2018 2018 Presentado por Leidy Paola Niño Rodríguez en cumplimiento parcial de los requerimientos para optar por el título de Ingeniero Aeron´autico Dirigida por David Leonardo Silva Coronado Presentada a Programa de Ingenier´ıa Aeron´autica Fundaci´on Universitaria Los Libertadores Bogot´a D.C, Colombia. 2018 2018 Notas de aceptaci´on Firma del presidente del jurado Firma del jurado Firma del jurado Bogota´ DC, agosto de 2018. Las directivas de la Fundaci´on Uni- versitaria Los Libertadores, los ju- rados calificadores y el cuerpo do- cente no son responsables por los criterios e ideas expuestas en el presente documento. Estos corres- ponden u´nicamente a los autores y a los resultados de su trabajo. Dedicatoria El presente trabajo lo dedico al buen Dios Todopoderoso, quien en su infinito amor y misericordia orientó mi vida al propósito divino de culminar una carrera preciosa a la que amo y cada día bendigo. A mi familia, por el ánimo y fe constante en la realización de éste sueño, a ti Mamá por tus oraciones y el aliento de vida que cada día sostiene con firmeza las bases y el desarrollo de mi vida profesional, a cada una de las personas que hacen parte de mi familia en Cristo, mis Pastores, hermanos y amigos que confiaron siempre en la excelencia del buen hacer de las cosas y en coinonía abrazaron junto a mi ésta meta. -

9/11 Report”), July 2, 2004, Pp
Final FM.1pp 7/17/04 5:25 PM Page i THE 9/11 COMMISSION REPORT Final FM.1pp 7/17/04 5:25 PM Page v CONTENTS List of Illustrations and Tables ix Member List xi Staff List xiii–xiv Preface xv 1. “WE HAVE SOME PLANES” 1 1.1 Inside the Four Flights 1 1.2 Improvising a Homeland Defense 14 1.3 National Crisis Management 35 2. THE FOUNDATION OF THE NEW TERRORISM 47 2.1 A Declaration of War 47 2.2 Bin Ladin’s Appeal in the Islamic World 48 2.3 The Rise of Bin Ladin and al Qaeda (1988–1992) 55 2.4 Building an Organization, Declaring War on the United States (1992–1996) 59 2.5 Al Qaeda’s Renewal in Afghanistan (1996–1998) 63 3. COUNTERTERRORISM EVOLVES 71 3.1 From the Old Terrorism to the New: The First World Trade Center Bombing 71 3.2 Adaptation—and Nonadaptation— ...in the Law Enforcement Community 73 3.3 . and in the Federal Aviation Administration 82 3.4 . and in the Intelligence Community 86 v Final FM.1pp 7/17/04 5:25 PM Page vi 3.5 . and in the State Department and the Defense Department 93 3.6 . and in the White House 98 3.7 . and in the Congress 102 4. RESPONSES TO AL QAEDA’S INITIAL ASSAULTS 108 4.1 Before the Bombings in Kenya and Tanzania 108 4.2 Crisis:August 1998 115 4.3 Diplomacy 121 4.4 Covert Action 126 4.5 Searching for Fresh Options 134 5. -

Annual Report 2007
EU_ENTWURF_08:00_ENTWURF_01 01.04.2026 13:07 Uhr Seite 1 Analyses of the European air transport market Annual Report 2007 EUROPEAN COMMISSION EU_ENTWURF_08:00_ENTWURF_01 01.04.2026 13:07 Uhr Seite 2 Air Transport and Airport Research Annual analyses of the European air transport market Annual Report 2007 German Aerospace Center Deutsches Zentrum German Aerospace für Luft- und Raumfahrt e.V. Center in the Helmholtz-Association Air Transport and Airport Research December 2008 Linder Hoehe 51147 Cologne Germany Head: Prof. Dr. Johannes Reichmuth Authors: Erik Grunewald, Amir Ayazkhani, Dr. Peter Berster, Gregor Bischoff, Prof. Dr. Hansjochen Ehmer, Dr. Marc Gelhausen, Wolfgang Grimme, Michael Hepting, Hermann Keimel, Petra Kokus, Dr. Peter Meincke, Holger Pabst, Dr. Janina Scheelhaase web: http://www.dlr.de/fw Annual Report 2007 2008-12-02 Release: 2.2 Page 1 Annual analyses of the European air transport market Annual Report 2007 Document Control Information Responsible project manager: DG Energy and Transport Project task: Annual analyses of the European air transport market 2007 EC contract number: TREN/05/MD/S07.74176 Release: 2.2 Save date: 2008-12-02 Total pages: 222 Change Log Release Date Changed Pages or Chapters Comments 1.2 2008-06-20 Final Report 2.0 2008-10-10 chapters 1,2,3 Final Report - full year 2007 draft 2.1 2008-11-20 chapters 1,2,3,5 Final updated Report 2.2 2008-12-02 all Layout items Disclaimer and copyright: This report has been carried out for the Directorate-General for Energy and Transport in the European Commission and expresses the opinion of the organisation undertaking the contract TREN/05/MD/S07.74176. -

El Efecto De La Apertura Económica En El Transporte Aereo Colombiano
EL EFECTO DE LA APERTURA ECONOMICA EN EL TRANSPORTE AEREO COLOMBIANO BEATRIZ EUGENIA PALACIOS ROLDAN MARIA DEL PILAR CAICEDO MEJIA Urivrrsld¿d tuttt$om¿ rlr O'.ia¡*f sEcctcrN EtBLtorEcA 025528 CORPORACION UNIVERSITARIA AUTONOMA DE OCCIDENTE \D DIVISION DE CIENCIAS ECONOMICAS Y EMPRESARIALES ro í'\. PRoGRAMA DE EcoNoM,o l$f .. .,::"¿Yó+3"1.. b sANr AGo DE cAL' llil|l|u|ü|üll|lll|ulullillil e \) 1997 ,\) tr- EL EFECTO DE LA APERTURA ECONOMICA EN EL TRANSPORTE AEREO COLOMBIANO BEATRIZ EUGENIA PALACIOS ROLDAN MARIA DEL PILAR CAICEDO MEJIA Trabajo de grado presentado como requisito para optar el titulo de Economista Director HUGO ORTIZ VASQUEZ Economista CORPORACI ON UN IVERSITARIA AUTONOMA DE OCCI DENTE DIVISION DE CIENCIAS ECONOMICAS Y EMPRESARIALES PROGRAMA DE ECONOMIA SANTIAGO DE CALI 1997 T 3r). 76 C !, ?tsza_ a_. _! NOTA DE APROBACION \ IN ñ, \ Aprobado por el cómite de grado en 'S,,. cumplimiento de los requisitos exigidos por la Corporación .¡,\ \\) Universitaria Autónoma de Occidente, .\ \ \ para optar el título de Economista {\ t4 \ ü \ \ nu \ \ t\ Jurado s'\q [\)\ \ \ \ N N *v * N Santigo de Cali, junio 3 de 1997 Nt (\* AGRADECIMIENTOS Muy especialmente a nuestro director HUGO ORTIZ VASQUEZ por su continuo apoyo, por su valiosa sabiduria que hizo posible que llegaramos a la culminación de nuestra investigación. A todos nuestros profesores que en el transcurso de nuestra carrera nos brindaron sus conocimientos permitiendo nuestra formación. A todas aquellas personas y entidades, que de una u otra manera colaboraron con información para la realización de éste proyecto. ill DEDICATORIA presente El trabajo de grado se lo dedico de todo corazón a mis padres Silvestre Palacios y colombia Roldán, por su constante apoyo, amor y paciencia, que permitieron e hicieron de mí una profesional.