Subject Index for Volume 42
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Gulf Pine Catholic • March 22, 2019 St
Catholic Volume 36 No. 15 www.biloxidiocese.org March 22, 2019 St. Peter the Apostle Parish in Pascagoula celebrates new church Bishop Louis F. Kihneman III exits the new St. Peter the Apostle Church in Pascagoula, right, after a March 3 dedication Mass. For more, photos, see pages 12-14. Photos/Juliana Skelton and Father Joseph Benjamin, SSJ Sister Clare Bass takes perpetual vows with the Sisters of St. Joseph of Carondelet ST. LOUIS: Sister Clare Bass, Mitchell. science and a master’s in public policy and administra- who entered the Sisters of St. Joseph Sister Clare is grateful for the influence of the tion. She is currently working on a master’s in social of Carondelet in 2010, takes her per- women religious who served in the diocese, especially work at Southern Illinois University-Edwardsville, and petual vows on March 30. the Irish Sisters of Mercy: Sister Rita Murray, Sister hopes to be a child and family therapist. She is passion- Originally from Biloxi, Rose Hennessy, Sister Kathleen Byrne, and Sister Anna ate about social justice and is a member of the prov- Mississippi, Sister Clare attended St. Quinlan, Sister Theresa and Sister Mary Riordan; ince’s Cultural and Racial Justice Committee. James Elementary School in Daughter of Charity Sister Joanne Cozzi, Marianite- “I am humbled by the great love and support of Gulfport and is a graduate of Mercy Sister Mary Ann Peltier and Sister of St. Francis Sister God, my family, the Sisters of St. Joseph, and friends Sister Clare Cross High School, class of 2001. Mary Jo Mike. -

View Details
RAJAGIRI SCHOOL OF ENGINEERING & TECHNOLOGY RAJAGIRI VALLEY P.O. KOCHI - 682039 Notice inviting quotation Sealed quotations are invited for the supply of books, in the list attached (No. of Titles 355, No. of Volumes 1569).The quotation should include the price, discount, availability of titles; time required for procurement and supply for titles which are currently unavailable (if any). We request you to make it sure that the price quoted is current as per the latest catalogue. Quotation has to reach the undersigned on or before 27th August 2016 Principal Applied Electornics & Instrumentation Total Number of Titles 20 Total Number of Volumes 100 No Author Book Title Publisher Copies Price Per Copy Discount % Network Analysis and Synthesis McGrawHill Education 1 Ravish R 2nd Ed. India Pvt.Ltd. 5 Fundamentals of Network Analysis 2 Pandey S K and Synthesis S Chand 5 Introduction to Semiconductor 3 Tyagi M S Materials and Devices 5th Ed. Wiley India 5 Physics of Semiconductor Devices 4 Sze S M 3rd Ed. Wiley India 5 Semiconductor Physics and Devices McGrawHill Education 5 Neamen 4th Ed. India Pvt.Ltd. 5 Semiconductor Devices and 6 Pierret Fundamentals Pearson 5 McGrawHill Education 7 Rita John Solid State Devices India Pvt.Ltd. 5 8 Bhattacharya Sharma Solid State Devices Oxford university press 5 Semiconductor Devices : Modelling 9 Dasgupta and Dasgupta and Technology PHI 5 10 Sedra A S amd K C Smith Microelectronic Circuits 6th Ed. Oxford university press 5 Introduction to Electronic Circuit 11 Spencer R R And M S Ghausi Design Pearson 5 12 Razavi B Fundmamentals of Wiley India 5 McGrawHill Education 13 Donald D Givone Digital Principles and Design India Pvt.Ltd. -

Honor Roll Stories of Honor
THE FOUNDATION for BARNES-JEWISH HOSPITAL Honor Roll Stories of Honor A Legacy of Giving 3 A Focus on Community Health 5 A Fight of a Lifetime 7 A Symbol of Hope 9 Honor Roll 10 Tribute Gifts 40 2019 2019: AN AMAZING YEAR ROLL HONOR Each year in our Honor Roll, we have the privilege Installed Patrick White, MD, as the inaugural Stokes to recognize the incredible people in our community, Family Endowed Chair in Palliative Medicine and throughout the country and around the world who come Supportive Care, representing a new department at together for one common cause: to enrich lives, save Washington University School of Medicine that is lives and transform health care through charitable gifts working to transform the way we think about end-of- to The Foundation for Barnes-Jewish Hospital. life care and living with chronic and painful diseases. We are honored to take this opportunity to tell the stories Awarded nearly 150 scholarships at Goldfarb School of our donors who were inspired by the exceptional, of Nursing to the future nurses who are so critical to compassionate care they received. These stories are about the health and well-being of patients in our community. the tradition of giving and community service, as well as inspiring courage and eternal optimism in the face Raised more than $4 million at the annual of challenging circumstances. They epitomize what we Illumination Gala to support innovative research know to be true about our donors: that individuals have at Siteman Cancer Center. the power to change the world around them for the better. -

Reflections Volume 68
1 Reflections Volume 68 International Catholic Family Newsletter AprilSept 2021 Are You Living‘ in the Flesh? The New Stigmata Saint of India Who Levitated The Silent Addiction to Technology The Real Easter Hallelujah Message Blessing to All: By: Richard Pickard “For those who live according to the flesh are concerned with the things of the flesh, but those who live according to the spirit with the things of the spirit.” (Romans 8:5) St. Paul was not talking about us acting as people created by God, but to those who have closed themselves to only matters of the flesh. He is talking about people who live only to satisfy their own desires. They care not for others, except for what others can do for them to satisfy their desires. In Philippians 1:21–24 we see a better example from St. Paul on the true meaning of Romans 8:5. “For to me to live is Christ, and to die is gain. If I am to live in the flesh, that means fruitful labor for me. Yet which I shall choose I cannot tell. I am hard pressed between the two. My desire is to depart [that is, to die and leave behind the body] and be with Christ, for that is far better. But to remain in the flesh is more necessary on your account.” Paul wants to help others understand the eternal and joyful salvation that Christ has to offer. Our life on earth is a series of frustrations, pains, sicknesses, hardships, and mental anguish when we live without the Spirit of Christ within us. -

29 ID Dec2015 Carmelasande
I¿sΩektμiw IÀs½ektμiw No.229 Unkw_À 2015 December 2015; No.229 1 I¿sΩektμiw CONTENTS Editorial .................................................................................... 3 P\-dm-f-®s‚ ktμiw ............................................................. 8 hy‡n-Xz-h-f¿®bpw B≤ym-flnI am¿§ Z¿i-\hpw ................ 12 {]m¿∞\maWn-°qdpw \ΩpsS {]m¿∞\mPohn-Xhpw............ 19 Xn∑-Iƒ°p≈ {]Xn-hn[nbpw {]Xn-tcm[hpw ............................ 27 A Provoking Renewal ............................................................. 32 REVISITING THE CMI CHARISM ..................................... 39 hn. Nmhd]nXmhpw \nc-¥-c-{]m¿∞\mPohnXhpw .............. 58 News & Views ....................................................................... 61 A\p-kvarXn: TESTAMENT OF A LOVING FATHER.... 82 Golden Records ................................................................... 101 I¿sΩ-e-bnse kuK-‘n-I-߃...................................................... 105 December 2015; No.229 2 I¿sΩektμiw Editorial Year of Blessings The year almost behind us, 2015, has been a year of blessings for all of us. We celebrated the first anniversary of the canonization of our founder St Kuriakose Elias Chavara, and the Carmelite Saint Sr Euphrasia from the CMC Congretion founded by St Kuriakose Elias Chavara, on November 23, 2015. The spiritual preparations and celebrations, once com- pleted, the Year of Consecrated was de- clared by the Holy Father for us to de- vote ourselves to our religious commit- ment in a special way through the renewal programme organized in various prov- inces and the major missions abroad. It was a great opportunity for us to travel back and revisit the annals of history and to imbibe the charism and spirit of the founding fathers, especially that of St Kuriakose Elias Chavara. The reflections, December 2015; No.229 3 I¿sΩektμiw by so many of our members as part of the renewal, were contextualized and had the feel and smell of their lived experience in religious life and evangelization. -

World Conference 2018
18th Global Information Technology Management Association (GITMA) World Conference 2018 July 8-10, 2018 Mexico City, Mexico p. 1 Conference Schedule Sunday – July 8, 2018 Registration 8:00am - 5:00pm Salón de Congresos Auditorio Profesional Aula Magna 2 (2008) Room 2005 (A1N1) GITMA Leadership 8:30 am to 9:30 am Meeting 9:30 am – 10:00 am Coffee Break 10 am to 11 am World IT Project Forum 11:15 am to 12 pm JGITM Board Meeting 12 noon to 1 pm Lunch on your own Global Information Artificial Intelligence 1pm to 2:30 pm Technology Applications Management 2:30 pm to 3 pm Coffee Break Panel: Privacy and Security IT Management and 3 pm to 4:30 pm Data Analytics I Issues in the Digital Education Economy 5:30 pm to 9:30 pm Social Event – Bus tour to Coyocan – buy $30 ticket at registration Monday, July 9, 2018 Registration 8:00am - 5:00pm Aula Magna 2 (2008) Auditorio Profesional Room 2004 Room 2005 (A1N1) Breakfast Plenary Session - ACADEMIC KEYNOTE SPEAKER 8:30 am to 10 am Dr. Suprateek Sarker, Rolls-Royce Commonwealth Commerce Professor, University of Virginia Salón de Congresos 10 am to 10:30 am Coffee Break Kirk Laughlin - Digital Societal and Cultural Panel: Bridging the Gap between 10:30 am to 12 pm Next Coast Media Academic and Professional Transformation I Issues I Gustavo Parés - NDS Worlds on Data Center Topics 12 noon to 1:30 pm Lunch on your own Prabhu Workshop: Data Chandrasekhar & 1:30 pm to 3:00 pm Social Media Emerging Issues Visualization in Cross- Prasad Vaddadi Humberto Balleza Cultural & Global Context 3:00 pm to 3:30 pm Coffee -

2020 Directory
1 ..................................................................................... PRAYER FOR THE EPARCHY OF MISSISSAUGA God our loving Father, we praise and thank you for the establishment of the Eparchy of Mississauga. Pour out your Spirit, endue with the choicest heavenly blessings and all the necessary graces and gifts of the Holy Spirit on all of us to build up the Syro-Malabar Church in Canada, for the Glory of God. In the name of Jesus we ask you to send your Spirit on our Bishop, Priests, Religious and all Men and Women, Young and Old to respond to your call for renewing the families and building up the community. Holy Mary, Mother of God, Pray for us. St. Joseph, patron of Canada, Pray for us St Thomas, Patron of our Eparchy, Pray for us. 2 3 ST. THOMAS PATRON OF THE EPARCHY 4 His Holiness Pope Francis.......................................................................... 5 The Catholic Church ................................................................................... 8 State of Vatican City ................................................................................... 10 The Roman Curia ........................................................................................ 11 His Excellency the Most Reverend Luigi Bonazzi ................................. 15 Canadian Conference of Catholic Bishops (CCCB)............................. 16 Episcopal Commissions and Standing Committees ............................. 18 Ecclesiastical Jurisdictions .......................................................................... -

APJAKTU M.Tech
RAJAGIRI SCHOOL OF ENGINEERING AND TECHNOLOGY DEPARTMENT OF ELECTRICAL AND ELECTRONICS M.Tech - INDUSTRIAL DRIVES AND CONTROL CURRICULUM BOOK (KTU) Vision of the Institution: To evolve into a premier technological and research institution, moulding eminent professionals with creative minds, innovative ideas and sound practical skill, and to shape a future where technology works for the enrichment of mankind. Mission of the Institution: To impart state-of-the-art knowledge to individuals in various technological disciplines and to inculcate in them a high degree of social consciousness and human values, thereby enabling them to face the challenges of life with courage and conviction. Vision of the Department: To excel in Electrical and Electronics Engineering education with focus on research to make professionals with creative minds, innovative ideas and practical skills for the betterment of mankind. Mission of the Department: To develop and disseminate among the individuals, the theoretical foundation, practical aspects in the field of Electrical and Electronics Engineering and inculcate a high degree of professional and social ethics for creating successful engineers. KERALA TECHNOLOGICAL UNIVERSITY CET Campus, Thiruvananthapuram, Kerala -695 016 ORDINANCE For Master of Technology - M.Tech. In exercise of the Powers conferred under Clause 44 of the Ordinance, the Executive Committee of the University hereby promulgate the Ordinance for the University for the Academic Year 2015-2016. The Academic ordinance will come into effect from -

India, Ceylon and Burma 1927
CATHOLIC DIRECTORY OF INDIA, CEYLON AND BURMA 1927. PUBLISHED BY THE CATHOLIC SUPPLY SOCIETY, MADRAS. PRINTED AT THE “ GOOD PASTOR ” PRESS, BROADWAY, MADRAS. Yale Divinity tibn fj New Haven. Conn M T ^ h t € ¿ 2 ( 6 vA 7 7 Nihil obstat. C. RUYGROCK, Censor Deputatus. Imprimatur: * J. AELEN, Aichbishop of Madras. Madras, Slst January 1927. PREFACE. In introducing the Catholic Directory, it is our pleasing duty to reiterate our grateful thanks for the valuable assistance and in formation received from the Prelates and the Superiors of the Missions mentioned in this book. The compilation of the Catholic Direct ory involves no small amount of labour, which, however, we believe is not spent in vain, for the Directory seems to be of great use to many working in the same field. But We would like to see the Directory develop into a still more useful publication and rendered acceptable to a wider circle. This can only come about with the practical "sympathy and active co-operation of all ^ friends and well-wishers. We again give the Catholic Directory to ¿the public, knowing that it is still incom plete, but trusting that all and everyone will ¿help us to ensure its final success. ^ MADRAS, THE COMPILER* Feast of St. Agnes, 1 9 2 7 . CONTENTS. PAGE Agra ... ... ... ... 86 iljiner ... ... ... • •• ... 92 Allahabad ... ••• ••• ••• ••• 97 Apostolic Delegation (The) ... .. ... 26 Archbishops, Bishops and Apostolic Prefects ... 449 Assam ... ... ... ... ... 177 Bombay ... ... ... ... ... 104 Éurma (Eastern) ... ... ... ... 387 Burma (Northern) ... ... ... ... 392 Burma" (Southern) ... ... ... ... 396 Calcutta ... ... ... ... ... 158 Calicut' ... ... ... ... ... 114 Catholic Indian Association of S. India ... ... 426 CHanganacberry ... ... ... ... 201 Ódchin ... ... ... ... ... 51 Coimbatore ... ... ... ... 286 Colombo .. -

Notice Inviting Quotation
RAJAGIRI SCHOOL OF ENGINEERING & TECHNOLOGY RAJAGIRI VALLEY P.O. KOCHI - 682039 Notice inviting quotation Sealed quotations are invited for the supply of books, in the list attached (No.of Titles 1171 , No.of Volumes 3797 ).The quotation should include the price, discount, availability of titles; time required for procurement and supply for titles which are currently unavailable (if any). We request you to make it sure that the price quoted is current as per the latest catalogue. Quotation has to reach the undersigned on or before 15h November 2013 Principal B.Tech. in Applied Electronics and Instrumentation Total No. of Titles 47 Total No.of Volumes 119 Sl. No.of. Price per No. Author Title Publisher Copies Copy Discount % Symbolic methods in control 1 Neil Munro system analysis and design IEE Press 1 2 R K Mittal and I J Nagrath Robotics and control TMH 1 Robotics : Modeling, Planning and 3 Bruno Siciliano control Springer 1 Cellular Robotics and micro 4 Toshio Fukuda robotics systems World Scientific 1 Electrical instruments and 5 Cidwell W measurements TMH 5 6 Woolvert G. A Transducers in digital systems peter peregrinvs Ltd. 1 Data Acquisition and control: micro computer applications for Tab professional and 7 Joseph J. Carr scientists and engineers reference books 1 Data Acquisition for sensor 8 H. RoseMary Taylor systems Springer 1 Data Acquisition for Instrumentation and Control 9 John Park, Steve Mackay Systems Newness 1 10 R.P Blake Industrial Safty PHI 1 Sytem Analysis and design for 11 Brown D. B safty PHI 1 Industrial Safty and Risk 12 Laird Wilson Management University of Alberto 1 13 L. -
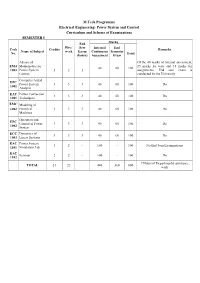
M-Tech Power System & Control Sche & Syllabus
M.Tech Programme Electrical Engineering- Power System and Control Curriculum and Scheme of Examinations SEMESTER I End Marks Hrs / Sem Internal End Code Credits Remarks Name of Subject week Exam Continuous Semester No. Total (hours) Assessment Exam Advanced Of the 40 marks of internal assessment, EMA Mathematics for 25 marks for tests and 15 marks for 40 60 100 1003 Power System 3 3 3 assignments. End sem exam is Control conducted by the University Computer Aided EPC Power System 3 3 3 40 60 100 Do 1001 Analysis EAC Power Conversion 3 3 3 40 60 100 Do 1001 Techniques EMC Modeling of 1002 Electrical 3 3 3 40 60 100 Do Machines Operation and EPC Control of Power 3 3 3 40 60 100 Do 1002 System ECC Dynamics of 3 3 3 40 60 100 Do 1003 Linear Systems EAC Power System 1 2 - 100 - 100 No End Sem Examinations 1101 Simulation Lab EAC Seminar 2 2 - 100 - 100 Do 1102 7 Hours of Departmental assistance TOTAL 21 22 440 360 800 work SEMESTER II End Marks Hrs / Sem Internal End Code Credits Name of Subject week Exam Continuous Semester Remarks No. Total (hours) Assessment Exam Of the 40 marks of internal assessment, 25 marks for tests and EAC Advanced Power 3 3 3 40 60 100 15 marks for assignments. End sem Electronic Sytems 2001 exam is conducted by the University EPC Power System 2002 Dynamics and 3 3 3 40 60 100 Do Control ** Stream Elective I 3 3 3 40 60 100 Do ** Stream Elective 3 3 3 40 60 100 Do II ** Department 3 3 3 40 60 100 Do Elective ECC Research End Sem Exam is conducted by the 2 2 3 40 60 100 2000 Methodology Individual Institutions EAC -

FAMILY BOND (VINCENTIAN BULLETIN) Have Charity the Bond of Perfection (Col
FAMILY BOND (VINCENTIAN BULLETIN) Have charity the bond of perfection (Col. 3: 14 (For private circulation only) Vol.50/ No.4 Dec. 2015 I. Editorial - CHRISTMAS DUTY 04 II. News From the Generalate 06 III. Mary Matha Province 10 IV. St. Joseph Province 18 V. St. Thomas Province 21 VI. Formation Houses 26 VII. Education and Media 35 VIII. Social Service 39 IX. History 1) Bilari: De Paul School 42 2) Thottakam 47 X. New Priests 2015 – 16 52 XI. Popular Missions and Retreats 67 Life is a circle of Happiness, Sadness, Hard times, and Good times. If you are going through hard times, have faith that good times are on the way. Family Bond -December 2015 I CHRISTMAS DUTY - EDUCATION FOR PEACE AND HARMONY During the liturgical period of Annunciation we pray in the Holy Mass: “Jesus, Lord of the nations and King of peace come to establish peace and harmony in the whole world and especially in our country”. It is our duty to translate this prayer into action even after Christmas. The right means are various steps in the apostolate of education for enlightening the younger folk. Indeed peace was the message given at the birth of Jesus, “…Peace on earth” (Lk.2.14). A grown- up Jesus understood that his mission was to bring the kingdom in all its fullness to us. His message, - ‘the reign of God is imminent’ - calls for a heart full of love, ears open to the cry of the poor, and hands willing to help. Bringing peace, well-being and joy were the marks of His Kingdom announced through the first Twelve and then with the help of the Seventy two disciples.