E - S O U V E N I R
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UNIVERSITY GRANTS COMMISSION State-Wise List of Private
UNIVERSITY GRANTS COMMISSION State-wise List of Private Universities as on 01.02.2020 S.No Name of Private University Date of Notification ARUNACHAL PRADESH 1. Apex Professional University, Pasighat, District East Siang, 10.05.2013 Arunachal Pradesh - 791102. 2. Arunachal University of Studies, NH-52, Namsai, Distt – Namsai 26.05.2012 - 792103, Arunachal Pradesh. 3. Arunodaya University, E-Sector, Nirjuli, Itanagar, Distt. Papum 21.10.2014 Pare, Arunachal Pradesh-791109 4. Himalayan University, 401, Takar Complex, Naharlagun, 03.05.2013 Itanagar, Distt – Papumpare – 791110, Arunachal Pradesh. 5. North East Frontier Technical University, Sibu-Puyi, Aalo 03.09.2014 (PO), West Siang (Distt.), Arunachal Pradesh –791001. 6. The Global University, Hollongi, Itanagar, Arunachal Pradesh. 18.09.2017 7. The Indira Gandhi Technological & Medical Sciences University, 26.05.2012 Ziro, Arunachal Pradesh. 8. Venkateshwara Open University, Itanagar, Arunachal Pradesh. 20.06.2012 S.No Andhra Pradesh 9. Bharatiya Engineering Science and Technology Innovation 17.02.2019 University, Gownivaripalli, Gorantla Mandal, Anantapur, Andhra Pradesh 10. Centurian University of Technology and Management, Gidijala 23.05.2017 Junction, Anandpuram Mandal, Visakhapatnam- 531173, Andhra Pradesh. 11. KREA University, 5655, Central, Expressway, Sri City-517646, 30.04.2018 Andhra Pradesh 12. Saveetha Amaravati University, 3rd Floor, Vaishnavi Complex, 30.04.2018 Opposite Executive Club, Vijayawada- 520008, Andhra Pradesh 13. SRM University, Neerukonda-Kuragallu Village, mangalagiri 23.05.2017 Mandal, Guntur, Dist- 522502, Andhra Pradesh (Private University) 14. VIT-AP University, Amaravati- 522237, Andhra Pradesh (Private 23.05.2017 University) ASSAM 15. Assam Don Bosco University, Azara, Guwahati 12.02.2009 16. Assam Down Town University, Sankar Madhab Path, Gandhi 29.04.2010 Nagar, Panikhaiti, Guwahati – 781 036. -

Era News Letter (10-10-2020).Cdr
JJuullyy,, 22002200 NNEEWWSSLLEETTTTEERR VVoolluummee 22,, NNuummbbeerr 11 EU Era University, Sarfarazganj, Hardoi Road, Lucknow - 226003, U.P., India. EDITORIAL BOARD Message from Sub-Editor: Times today are stressful-many of us are anxiously, Dr. Rupali Mirza almost continously scrolling through news updates, Department of Liberal Education rationing supplies, counting figures of those affected, cured or dead. Simultaneously, whether employed or Dr. Mohini Chaurasia currently unemployed wondering how to utilise time Era College of Pharmacy or how to work from home. A new life- style has thus emerged where carrying sanitizer and donning a Dr. Tabrez Jafar mask is not only the in-thing but normal. Department of Molecular Medicine Not withstanding the pandemic raging the continents and Ms. Godhuli Ghosh the world trying to adjust and live with this new normal, Era College of Nursing it's imperative that the mind is kept occupied through creativity and good readings. This besides diverting us Mr. Bilal Ahmad from the macabre thoughts invading our minds will assist Research Coordinator in keeping negativity at bay, energising our brain and relaxing us in the process. So folks, with this noble thought we present before you our yearly newsletter. Our singular aim is to help our Message from Chief Editor: readers de-stress and venture through an informative, Scarlet, yellow, amethyst, pink, amaranth and mauve sheaves educative and creative compilation. All courses that She carries all colours in her basket count- MBBS, Pharmacy, Sciences, Liberal Education, and Allied & paramedical - are voiced in a delectable, Mellow is her voice multifarious assortment — a binding vine of perennial Over-brimming with dulcet tones growth and development of Era University. -

Consolidated List Private Universities
UNIVERSITY GRANTS COMMISSION State-wise List of Private Universities as on 06.08.2021 S.No Name of Private University Date of Notification ARUNACHAL PRADESH 1. Apex Professional University, Pasighat, District East Siang, 10.05.2013 Arunachal Pradesh - 791102. 2. Arunachal University of Studies, NH-52, Namsai, Distt – Namsai 26.05.2012 - 792103, Arunachal Pradesh. 3. Arunodaya University, E-Sector, Nirjuli, Itanagar, Distt. Papum 21.10.2014 Pare, Arunachal Pradesh-791109 4. Himalayan University, 401, Takar Complex, Naharlagun, 03.05.2013 Itanagar, Distt – Papumpare – 791110, Arunachal Pradesh. 5. North East Frontier Technical University, Sibu-Puyi, Aalo 03.09.2014 (PO), West Siang (Distt.), Arunachal Pradesh –791001. 6. The Global University, Hollongi, Itanagar, Arunachal Pradesh. 18.09.2017 7. The Indira Gandhi Technological & Medical Sciences University, 26.05.2012 Ziro, Arunachal Pradesh. 8. Venkateshwara Open University, Itanagar, Arunachal Pradesh. 20.06.2012 Andhra Pradesh 9. Bharatiya Engineering Science and Technology Innovation 17.02.2019 University, Gownivaripalli, Gorantla Mandal, Anantapur, Andhra Pradesh 10. Centurian University of Technology and Management, Gidijala 23.05.2017 Junction, Anandpuram Mandal, Visakhapatnam- 531173, Andhra Pradesh. 11. KREA University, 5655, Central, Expressway, Sri City-517646, 30.04.2018 Andhra Pradesh 12. Saveetha Amaravati University, 3rd Floor, Vaishnavi Complex, 30.04.2018 Opposite Executive Club, Vijayawada- 520008, Andhra Pradesh 13. SRM University, Neerukonda-Kuragallu Village, mangalagiri 23.05.2017 Mandal, Guntur, Dist- 522502, Andhra Pradesh (Private University) 14. VIT-AP University, Amaravati- 522237, Andhra Pradesh (Private 23.05.2017 University) ASSAM 15. Assam Don Bosco University, Azara, Guwahati 12.02.2009 16. Assam Down Town University, Sankar Madhab Path, Gandhi 29.04.2010 Nagar, Panikhaiti, Guwahati – 781 036. -

Who We Are Campus Automation Solution About Us Complete Student Life Cycle Management Kamtron Systems Pvt
Our New Initiative Who We Are Campus Automation Solution About Us Complete Student Life cycle management Kamtron Systems Pvt. Ltd., as a leading partner in providing latest software Admission, Time table, attendance technology and licensing solutions to Examination & Report card educational institutions. We believe in Teacher and Parents portal creating awareness through education and Fees, Library & Hostel work with consultative approach. Complete Web based system On Cloud / On Campus Solution or We Provide an end to end software solutions both to all client with complete deployment and Developed and hosted on open after sales support for the best utilization of source platform the technology. Our dedicated sales and technical team is our core strength to create and retain our customers for the past 15 years. We thank all our customers for showing their trust in us. KAMTRON SYSTEMS PVT. LTD. Contact Us 402, Eros Apartment, 56 Nehru Place, New Delhi - 110019 Phone: +91-11-26286257, 58, 59 Email: [email protected] Web: www.kamtrononline.com Office365x24.com Sales Enquiries: Licensed Software Solutions Ms. Shamim Fatima – 011 26286460 and Campus Automation Ms. Jyoti Bisht – 011- 26210721 Solutions for Universities, Higher Education Institutions Ms. Kavita Singhal – 09810365559 and K-12 SCHOOLS Our Software Product Range Other Licensing Solutions Corel Graphic Suite Microsoft Solutions Rhino Perpetual Licensing Embracadero . One time procurement Autodesk : AutoCAD, AutoCAD LT OVS-ES (Open Value Subscription for (free for AICTE approved Education Solution) institutions) . Campus Wide Licensing – OS Winzip Our Partial List of Satisfied Clients Upgrade, Office Pro and Core Cal WinRAR Suite Oracle Database: Oracle Std., IIT, Allahabad Edu Cloud Campus: Oracle Enterprise, Oracle Express IIT, Delhi (Okhla) . -

Webometric Analysis of Deemed University Websites in India Jeyshankar
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Library Philosophy and Practice (e-journal) Libraries at University of Nebraska-Lincoln Winter 2-2019 Webometric Analysis of Deemed University Websites in India Jeyshankar -. Ramalingam - Dept. of Library and Information Science, Alagappa UNiversity, Tamil Nadu, India, [email protected] Follow this and additional works at: https://digitalcommons.unl.edu/libphilprac Part of the Library and Information Science Commons Ramalingam, Jeyshankar -. -, "Webometric Analysis of Deemed University Websites in India" (2019). Library Philosophy and Practice (e-journal). 2266. https://digitalcommons.unl.edu/libphilprac/2266 Webometric Analysis of Deemed University Websites in India Dr. R. Jeyshankar Assistant Professor, Department of Library & Information Science Alagappa University, Karaikudi-630 003, India, Email: [email protected] 0. Abstract This paper examines Webometric analysis the website of deemed universities in India. This study covered 125 deemed universities in India. The researcher identified and classified the four domains like State Universities, Central Universities, Deemed Universities and Private Universities. The researcher found that, out of 21 states, Tamil Nadu has a maximum of 28 (22.40%) universities, it is followed by Maharashtra 21(16.8%). The study calculated the Internal Link, External Link, back link and Size of the website. The study indicates that the numbers of backlinks are very low comparing to some of internal and external link. The researcher suggested that the websites of deemed universities need to attract more external links and impact factor by introducing novel and creative online sources and services and updates of news and research information. Keyword: Deemed university websites, university websites, website analysis, Link analysis, Internal Link; External Link Back Link, Web Impact Factor and size of websites. -

List of Universities Under Section 2(F) and Section 3 of the UGC Act, 1956
UNIVERSITY GRANTS COMMISSION List of Universities under Section 2(f) and Section 3 of the UGC Act, 1956 S.No ANDHRA PRADESH 1. A.P. University of Law, Palace Layout, Pedawaltair, Visakhapatnam – 530 017 (A. P) (State University). 2. Acharya N.G. Ranga Agricultural University, Hderabad-500 030. (State University) 3. Acharya Nagarjuna University, Nagarjuna Nagar, Guntur-522 510. (State University) 4. Adikavi Nannaya University, Jaya Krishnapuram, Rajahmundry – 533 105, Andhra Pradesh. (State University) 5. Andhra Pradesh University of Health Sciences, Vijayawada-520 008. (State University) 6. Andhra University, Visakhapatnam-530 003. (State University) 7. Dr. B.R. Ambedkar Open University, Jubilee Hills, Hyderabad-500 033. (State University) 8. Dr. B.R. Ambedkar University, Etcherla – 532 410 Srikakulam, Andhra Pradesh (State University) 9. Dravidian University, Kuppam-517 425. (State University) 10. Dr. Y.S.R. Horticultural University, PO Box No. 7, Venkataramannagudem, West Godavari District – 536 101, Andhra Pradesh. (State University) 11. Gandhi Institute of Technology and Management (GITAM), Gandhi Nagar Campus, Rushikonda, Visakhapatman – 530 045.(Deemed University) 12. ICFAI Foundation for Higher Education, Hyderabad, Andhra Pradesh. (Deemed University) 13. International Institute of Information Technology, Hyderabad-500 019. (Deemed University) 14. Jawaharlal Nehru Architecture and Fine Arts University, Mahaveer Marg, Masab Tank, Hyderabad – 500 028 (State University) 15. Jawaharlal Nehru Technological University, Anantpur-515 002, Andhra Pradesh (State University) 16. Jawaharlal Nehru Technological University, Hyderabad-500 072. (State University) 17. Jawaharlal Nehru Technological University, Kakinada-533003, Andhra Pradesh.(State University) 18. Kakatiya University, Warangal-506 009. (State University) 19. Koneru Lakshmaiah Education Foundation, Greenfields, Kunchanapalli Post, Vaddeswaram, Guntur District, Andhra Pradesh (Deemed University) 20. -

1 Acharya Nagarjuna University 2 Adikavi Nannaya University 3
1 Acharya Nagarjuna University 2 Adikavi Nannaya University 3 Andhra University Centurion University of Technology and Management, Andhra 4 Pradesh 5 Damodaram Sanjivayya National Law University 6 Dr. Abdul Haq Urdu University, Kurnool- 518001, Andhra Pradesh 7 Dr. B.R. Ambedkar University 8 Dravidian University 9 Dr. Y.S.R. Horticultural University Dr. N.T.R. University of Health Sciences (Formerly Andhra Pradesh 10 University of Health Sciences) Gandhi Institute of Technology and Management (GITAM), Gandhi 11 Nagar 12 Jawaharlal Nehru Technological University, Anantpur-515 002 Jawaharlal Nehru Technological University, Pithapuram Road, 13 Kakinada 14 Koneru Lakshmaiah Education Foundation KREA University, 5655, Central, Expressway, Sri City-517646, 15 Andhra 16 Krishna University 17 Rashtriya Sanskrit Vidyapeeth 18 Rayalaseema University 19 Saveetha Amaravati University 20 Sri Krishnadevaraya University 21 Sri Padmavati Mahila Vishwavidyalayam Sri Sathya Sai Institute of Higher Learning, Prasanthinilayam, 22 Anantapur-515 23 Sri Venkateswara University 24 Sri Venkateswara Vedic University 25 Sri Venkateswara Veterinary University 26 Sri Venkateswara Institute of Medical Sciences 27 SRM University, Andhra Pradesh Vignan's Foundation for Science, Technology and Research, 28 Vadlamudi, 29 Vikrama Simhapuri University, Kakutur 30 VIT-AP University, Amravati 31 Yogi Vemana University 32 Apex Professional University 33. Arunachal University of Studies 34 Arunodaya University 35 Himalayan University 36 North East Frontier Technical University -

NAAC 5.3.3 Sports & Cultural Events Organized By
NAAC 5.3.3 Sports & Cultural events organized by the university Athletic Meet 2015 Date: 20 Oct, 2015 STRIDE – The Sports Club organised its first event i.e. Athletic Meet 2015 on 20th Oct, 2015. On this event STRIDE introduced different field and track events. • Field Events: 1. Long Jump 2. Discus Throw 3. Javelin Throw 4. Shot Putt • Track Events: 1. 100 m 2. 200 m 3. 400 m 4. 800 m 5. 4x100 m Relay Race More than 300 participants took part in the various events with full zeal and zest. Winners List: Event : 100m Position Name Course Student ID BOYS: 1st Vikram Singh B.tech (CE) 4th year CI2012045 2nd Mohit Pal Diploma(CE) 3rd year DCE2013036 3rd Nayan Raj Joshi B.tech (CE) 3rd year CI2013081 GIRLS: 1st Mandeep Kaur B.B.A 1st year BB2015091 2nd Yashica Kohli B.sc Maths 2nd year BSM2014001 3rd Anjali Yadav B.Sc Chemistry 3rd year BSC2013007 Event: 200m Position Name Course Student ID BOYS: 1st Inam-ur-rehman B.Com (H) 2nd year BCO2014138 2nd Akash Rathore B.B.A 1st year BB2015068 3rd Somdutt Malasi M.B.A 2nd year MB2014029 GIRLS: 1st Yashica Kholi B.sc Maths 2nd year BSM2014001 2nd Manpreet Kaur B.com(H) 2nd year BCO2014056 3rd Divya B.sc phy 2nd year BSP2014013 Event: 400m Position Name Course Student ID BOYS: 1st Sachin kumar Diploma 1st year DMA2015003 2nd Vishal Bahadur B.Tech (CE) 1st year CI2015010 3rd Mohd. Zahid B.Pharm 4th year BP2012012 GIRLS: 1st Alka Shukla B.Sc Physics 3rd year BSP2013027 2nd Anjali Yadav B.Sc Chemistry 3rd year BSC2013007 3rd Polki Thakur B.B.A 1st year BB2015029 Event: 800m Position Name Course Student -

LIST of DEEMED UNIVERSITIES S.No. Name & Address
LIST OF DEEMED UNIVERSITIES S.No. Name & Address Contact 1. Rashtriya Sanskrit Vidyapeeth, E-mail: [email protected] Tirupati-517507 Andhra Pradesh Tel: 0877- 2287680 www.sansknet.org Fax: 0877- 2287680; 2287826 2. Sri Sathya Sai Institute of Higher Learning E-mail: [email protected] Prasanthinilayam, Tel: 08555- 286191 Anantapur Dist.- 515134 Andhra Pradesh Fax: 08555- 287239 www.sssu.edu.in 3. International Institute of Information Technology, E-mail: [email protected] Gachibowli, Tel: 040- 23001967 Hyderabad 500 019 Andhra Pradesh Fax: 040- 23001413 www.iiit.ac.in 4. Gandhi Institute of Technology and Management E-mail: [email protected] ; [email protected] (GITAM), Gandhi Nagar Campus, Rushikonda, Tel: 0891-2790101; 2790202; 2790404; 2790505 Visakhapatnam-530045 Andhra Pradesh Fax: 2790399; 2790037; 2790036 www.gitam.edu 5. North Eastern Regional Institute of Science and E-mail: [email protected] Technology, Nirjuli Tel:0360-2245094; 2257584; 2245095 Itanagar – 791109 Arunachal Pradesh Fax: 0360-2244307 www.nerist.ac.in 6. Bihar Yoga Bharati, E-mail: None Ganga Darshan Fort, Munger, Tel: 06344-222480 Bihar -811201 Fax: 06344-220169 7. Nava Nalanda Mahavihara, E-mail: [email protected] Nalanda- 803111 Bihar Tel: 06112-281672; 281697; 281820 www.navanalanda.org Fax: 06112-281907 8. Punjab Engineering College E-mail: [email protected] Sector -12, Chandigarh 160012 Tel: 0172-2753700 www.pec.ac.in Fax: 0172-2745175 9. Gujarat Vidyapith, PO Navjivan, Near Income E-mail: [email protected] Tax Office Ashram Road, Ahmedabad-38-014 Tel: 079-27541392 Gujarat Fax: 079- 27542547 www.gujaratvidyapith.org 10. Sumandeep Vidyapeeth, E-mail: [email protected] P.O. -
Recognition/ Equivalence List
C RECOGNITION/ EQUIVALENCE LIST April, 2011 MAHARSHI DAYANAND UNIVERSITY, ROHTAK-124001 (HARYANA) Available from Deputy Registrar (Publications Cell) Price : Rs. 50/- M.D. University, Rohtak C 1 IMPORTANT NOTES 1. The eligibility for admission to a particular course may be determined on the basis of equivalence shown in this list and the detailed conditions given in the Admission Brochure(s)/ Handbooks of Information/Prospectuses and the relevant Ordinances. 2. B.A./B.Sc./B.Com/B.Sc. (Home Science) pass/honours and shastri (with English) etc. courses under 10+2+3 pattern of examinations and M.A./M.Sc./M.Com Acharya and LL.M. etc. after three years graduation degree or five years after +2 level examination of all the statutory Universities in India, including open/private Universities, deemed to be universities established by an Act of the State Govt./ Centre govt. which are approved by the University Grants Commission (UGC) have been recognized as equivalent to respective course of this University without following the normal procedure of comparing the syllabi and scheme of examination etc. (list of Universities approved by UGC is appended at appendix-A). However, updated list of such Universities may be seen on UGC Website. Three-year programme of BBA/BCA run by Universities, including open/private Universities/deemed to be Universities, established by an Act of the Central/State Legislature and recognized by UGC approved Universities are recognized as equivalent to BBA/BCA of this University. The part examination of the said degree courses are also recognized provided that candidates must have passed the examination with those subjects in which this University imparts instructions and also fulfils the condition of requisite percentage of marks. -

SCHOLARSHIP STATUS of STUDENTS FOUND ELIGIBLE in the AY 2012-13 (As on 31.12.2016)
SCHOLARSHIP STATUS OF STUDENTS FOUND ELIGIBLE IN THE AY 2012-13 (as on 31.12.2016) Note: 1. For any query sent mail to [email protected] 2. Scholarships shown as released in AY 2015-16 are subject to verification and confirmation of account details of students for DBT Fresh 2nd Renewal Course 1st Renewal Status 3rd Renewal Status S.No. Student Name College Name State List Scholarship Status Category (2013-14) (2015-16) 2012-13 (2014-15) 1 Aafaq Ahmed Dar Aligarh Muslim University Uttar Pradesh General 2858 Released Released Released Course Complete Engineeri Released (In 2 Aasif Hussain Bhat Career Point Technical Campus Punjab 2858 Released Released No Claim Received ng Cambridge) 3 Amira Sharief Sharief Aligarh Muslim University Uttar Pradesh General 2858 Released Released Released Course Complete 4 Anzar Nabi Lone Aligarh Muslim University Uttar Pradesh General 2858 Released Released Released Course Complete 5 Davood Bashir Dar Aligarh Muslim University Uttar Pradesh General 2858 Released Released Released Course Complete 6 Fazil Fayaz Dar Aligarh Muslim University Uttar Pradesh General 2858 Released Released Released Course Complete Engineeri Released (In 7 Jai . Raj Career Point Technical Campus Punjab 2858 Released Released No Claim Received ng Cambridge) Engineeri Course Completed as 8 Lateef Ahmad Lone Career Point Technical Campus Punjab 493 Released Released Released ng admitted in AY 2011-12 9 Mansoor Ahmad Bhat Aligarh Muslim University Uttar Pradesh General 2858 Released Released Released Course Complete 10 Mir -
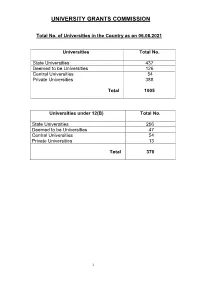
Consolidated List of All Universities
UNIVERSITY GRANTS COMMISSION Total No. of Universities in the Country as on 06.08.2021 Universities Total No. State Universities 437 Deemed to be Universities 126 Central Universities 54 Private Universities 388 Total 1005 Universities under 12(B) Total No. State Universities 256 Deemed to be Universities 47 Central Universities 54 Private Universities 13 Total 370 1 S.No ANDHRA PRADESH Date/Year of Notification/ Establishment 1. Acharya N.G. Ranga Agricultural University, Lam, 1964 Guntur – 522 034,Andhra Pradesh (State University) 2. Acharya Nagarjuna University, Nagarjuna Nagar-522510, Dt. Guntur, 1976 Andhra Pradesh. (State University) 3. Adikavi Nannaya University, 25-7-9/1, Jayakrishnapuram, 2006 Rajahmundry – 533 105, East Godavari District, Andhra Pradesh. (State University) 4. Andhra University, Waltair, Visakhapatnam-530 003, Andhra Pradesh. 1926 (State University) 5. Bharatiya Engineering Science and Technology Innovation University, 17.02.2019 Gownivaripalli, Gorantla Mandal, Anantapur, Andhra Pradesh (Private University) 6. Central University of Andhra Pradesh, IT Incubation Centre Building, 05.08.2019 JNTU Campus, Chinmaynagar, Anantapuramu, Andhra Pradesh- 515002 (Central University) 7. Central Tribal University of Andhra Pradesh, Kondakarakam, 05.08.2019 Vizianagaram, Andhra Pradesh 535008 (Central University) 8. Centurion University of Technology and Management, Gidijala Junction, 23.05.2017 Anandapuram Mandal, Visakhapatnam – 531173, Andhra Pradesh. (Private University) 9. Damodaram Sanjivayya National Law University, Plot No. 116, Sector 2008 11 MVP Colony, Visakhapatnam – 530 017, Andhra Pradesh. (State University) 10. Dr. Abdul Haq Urdu University, Kurnool- 518001, Andhra Pradesh 14.12.2018 (State University) 11. Dr. B.R. Ambedkar University, Etcherla, Dt. Srikakulam-532410, 2008 Andhra Pradesh. (State University) 12. Dravidian University, Srinivasanam, -517 425, Chittoor District, 1997 Andhra Pradesh.