Panorama-2017-2018-V3.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Princeton University Library September 27, 2013
Checklist of Western Medieval, Byzantine, and Renaissance Manuscripts in the Princeton University Library and the Scheide Library Princeton University Library September 27, 2013 Contents Introduction, p. 3 Manuscripts Division Robert Garrett Medieval and Renaissance Manuscripts, p. 5 Robert Taylor Medieval and Renaissance Manuscripts, p. 44 Grenville Kane Medieval and Renaissance Manuscripts, p. 48 Princeton Medieval and Renaissance Manuscripts, p. 56 Cotsen Children’s Library Cotsen Medieval and Renaissance Manuscripts, p. 87 Rare Books Division Manuscripts bound with early printed books, p. 88 The Scheide Library Scheide Medieval and Renaissance Manuscripts, p. 88 Introduction The present checklist is not a catalogue, but rather is a checklist intended to serve as a guide to sources of up-to-date cataloging, textual and codicological description, and digital images for western medieval, Byzantine, and Renaissance manuscripts in the Princeton University Library and the Scheide Library. Manuscripts are listed by holding unit, collection, and manuscript number or shelfmark. Links are given for more than well over 2,000 digital images of miniatures, illustrations, and selected diagrams and decoration in the manuscripts, about a third of which are illuminated. In addition, links are provided for digitized grayscale microfilm of a large number of Middle English manuscripts at Princeton and for a group of important manuscripts digitized in the Library since the 1990s. For additional information about the holdings of the Manuscripts Division and to make appointments, potential researchers should contact Don C. Skemer, Curator of Manuscripts, at [email protected]. For information about holdings of the Scheide Library, please contact Paul Needham, Librarian, at [email protected] For information concerning photoduplication and permission to publish and/or broadcast, please send an email to [email protected] A brief overview of the manuscripts and their cataloging follows. -

CITY of CRESCENT CITY Mayor Blake Inscore Mayor Pro Tem Heidi Kime Council Member Alex Fallman Council Member Jason Greenough Council Member Isaiah Wright
CITY OF CRESCENT CITY Mayor Blake Inscore Mayor Pro Tem Heidi Kime Council Member Alex Fallman Council Member Jason Greenough Council Member Isaiah Wright AGENDA REGULAR CITY COUNCIL MEETING VIRTUAL VIA ZOOM MONDAY JULY 20, 2020 6:00 P.M. Due to the current public health emergency resulting from COVID-19, the public may access and participate in the public meeting using one or more of the following three methods: (1) participate online via Zoom - details to join the meeting will be on both the City of Crescent City - City Hall Facebook page as well as the City of Crescent City website (www.crescentcity.org): (2 ) watch the meeting via livestream on YouTube (Channel: City of Crescent City, California) and submit comments via [email protected]; or submit a written comment by filing it with the City Clerk at 377 J Street, Crescent City, California 95531 prior to 4:00 pm, July 20, 2020. If you require a special accommodation, please contact City Clerk Robin Patch at 464-7483 ext. 223. Due to lack of items to discuss, there will not be a closed session. OPEN SESSION Call to order Roll call Pledge of Allegiance PUBLIC COMMENT PERIOD Any member of the audience is invited to address the City Council on any matter that is within the jurisdiction of the City of Crescent City. Comments of public interest or on matters appearing on the agenda are accepted. Note, however, that the Council is not able to undertake extended discussion or act on non-agendized items. Such items can be referred to staff for appropriate action, which may include placement on a future agenda. -

Recent Evolution of Poverty
Report No. 19385-AM ImprovingSocial Assistancein Armenia Public Disclosure Authorized June8,1999 Human Development Unit Country Department III Europe and Central Asia Region Public Disclosure Authorized Public Disclosure Authorized Public Disclosure Authorized Document of the World Bank ABBREVIATIONS AND ACRONYMS ACBA Agriculture Credit Bank of Armenia ASIF Armenia Social Investment Fund BBP Basic Benefit Package CAS Country Assistance Strategy CIS Commonwealth of Independent States ECHO European Community Humanitarian Office FAR Fund for Armenian Relief FBS Family Budget Survey FSU Former Soviet Union GDP Gross Domestic Product GOA Government of Armenia HAC Humanitarian Assistance Commission HACC Humanitarian Aid Coordination Commission HBS Household Budget Survey HES Health and Education Survey IDA International Development Association IMF International Monetary Fund JMP Jinishian Memorial Program MA Mission Armenia NGO Non-governmental Organization(s) OECD Organization for Economic Cooperation and Development PAYG Pay-As-You-Go SDS Armenian State Department of Statistics SSC Social Services Center UNHCR United Nations High Commissioner for Refugees UNICEF United Nations Children's Fund USAID United States Agency for International Development VAT Value Added Tax WFP World Food Program YICRD Yerevan Institute of Computer Research and Development YSU Yerevan State University Vice President Johannes Linn, ECAVP Country Director Judy O'Connor, ECCO3 Sector Manager Michal Rutkowski, ]ECSHD Task Team Leader Alexandre Marc, ECSHD ACKNOWLEDGEMENTS The preparation of the report was managed by Alexandre Marc (Sr. Human Resources Specialist). Margaret Grosh (Sr. Economist) was responsible for the research work on targeting which she carried out in collaboration with Elena Glinskaya (Consultant), and was the main author of the chapter on targeting of social assistance. -

Nato Warsaw Summit Time
SPRING/SUMMER 2016 SPRING/SUMMER NATO WARSAW SUMMIT TIME TO ACT Anders Fogh Antoni Macierewicz Peter Brookes Rasmussen SECURITY IN A NEW NATO FOR A NATO FIT EUROPE - HOW A NEW AMERICAN FOR PURPOSE TO CHANGE THE ADMINISTRATION NEGATIVE TREND EDITORIAL Tomasz Poręba Tomasz Poręba is a Member of the European Parliament and President of New Direction – The Foundation for European Reform. NATO THE FOUNDATION OF EUROPEAN SECURITY ontrary to popular belief wave of migrants and refugees prevailing since the end towards Europe. Almost all of our of the Cold War, the end neighbourhood is touched by open of the military stand- or frozen conflict, unrest and civil Coff between NATO and Soviet war, whilst exposed to the threat of Union did not mark a new era terrorism. of peace and safety. Under the rule of Vladimir Putin, Russia is Both Europe and NATO face trying to once again assert itself unprecedented threats on many as a world power and regain lost different fronts. These range from influence and prestige by pursuing conventional warfare through an increasingly aggressive and the expansion of terrorist groups, revanchist policy. This coincides radicalisation of our own citizens with the fact that while doing so, to information warfare and the Kremlin is seeking to distract propaganda fuelled mainly by Russian citizens from the country’s the Russia regime. Therefore, the growing internal problems. Warsaw Summit is timely and Turmoil in the Middle East and should be used as an opportunity North Africa, civil war in Syria, to decisively respond to these new and conflicts in Yemen and Libya, forms of threats, which include has brought an unprecedented hybrid warfare and cyber attacks. -

Heroes, Hooligans, and Knights-Errant: Masculinities and Popular Media in the Early People’S Republic of China
_full_journalsubtitle: Men, Women and Gender in China _full_abbrevjournaltitle: NANU _full_ppubnumber: ISSN 1387-6805 (print version) _full_epubnumber: ISSN 1568-5268 (online version) _full_issue: 2 _full_issuetitle: 0 _full_alt_author_running_head (change var. to _alt_author_rh): 0 _full_alt_articletitle_running_head (change var. to _alt_arttitle_rh): Heroes, Hooligans, and Knights-Errant _full_alt_articletitle_toc: 0 _full_is_advance_article: 0 NAN N Ü 316 Nan Nü 19 (2017) 316-356 Wang brill.com/nanu Heroes, Hooligans, and Knights-Errant: Masculinities and Popular Media in the Early People’s Republic of China Y. Yvon Wang University of Toronto [email protected] Abstract This article is an exploration of media and gender in urban and peri-urban China dur- ing the 1950s and early 1960s – specifically, the persistent trope of the “hooligan,” or liumang. Since at least the late imperial period, Chinese authorities had feared unmar- ried, impoverished, rootless men as the main source of crime, disorder, and outright rebellion. Yet such figures were simultaneously celebrated as knights-errant for their violent heroism in cultural works of enormous popularity across regions and classes. As the ruling Chinese Communist Party attempted to reshape society and culture after 1949, it condemned knight-errant tales and made hooliganism a crime. At the same time, the state tried to promote a new pantheon of vigilante-like men in the guise of revolutionary heroes. But the state’s control over deeply rooted cultural markets and their products was incomplete. Moreover, the same potent tools that had empowered the Party, in particular its rhetoric of revolutionary subjectivity and its harnessing of modern media technologies, were open as never before to being adopted by the very targets of its efforts at control and censure. -

El Statu Quo De Perejil», Peace & Security – Paix Et Sécurité Internationales, No 9, 2021
PEACE & SECURITY – PAIX ET SÉCURITÉ INTERNATIONALES EuroMediterranean Journal of International Law and International Relations Issue 9, January-December 2021 | ISSN 2341-0868 DOI http://dx.doi.org/10.25267/Paix_secur_int.2021.i9.1503 Citation: PÉREZ-PRAT DURBAN, L: «España y Marruecos en el Estrecho de Gibraltar, el statu quo de Perejil», Peace & Security – Paix et Sécurité Internationales, No 9, 2021. Received: 13 July 2021. Accepted: 27 July 2021. ESPAÑA Y MARRUECOS EN EL ESTRECHO DE GIBRALTAR: EL STATU QUO DE PEREJIL Luis PÉREZ-PRAT DURBÁN1* I. PLANTEAMIENTO – II. SITUACIÓN GEOGRÁFICA, SITUACIÓN EN EL CONTENCIOSO – III. PORTUGAL Y PEREJIL – IV. ESPAÑA Y PEREJIL – V. MARRUECOS, ESPAÑA Y PEREJIL – VI. CONCLUSIONES RESUMEN: El incierto estatuto jurídico de la isla de Perejil, disputada por España y Marruecos, trae causa de una confusa historia que se retrotrae a los tiempos en que Ceuta pertenecía a Portugal. Por ello, para analizar los títulos españoles hay que examinar tanto los que se derivan de los actos portugueses en el islote como los desarrollados por España a lo largo de los siglos, desde el siglo XV. Y, posteriormente, es ineludible analizar la posición de Marruecos en el contencioso. Todo ello confluye en un statu quo indeterminado que se afianzó tras el incidente militar desencadenado entre España y Marruecos en 2002. PALABRAS CLAVE: Estrecho de Gibraltar; conflicto de la isla de Perejil; islote; adquisición de soberanía territorial; conquista; ocupación; prescripción adquisitiva. SPAIN AND MOROCCO IN THE STRAITS OF GIBRALTAR: THE STATU QUO OF PEREJIL ISLET ABSTRACT: The uncertain legal status of the island of Perejil, disputed by Spain and Morocco, brings about a confusing history that goes back to the times when Ceuta belonged to Portugal. -

International Response to Infectious Salmon Anemia: Prevention, Control, and Eradication: Proceedings of a Symposium; 3Ð4 September 2002; New Orleans, LA
United States Department of Agriculture International Response Animal and Plant Health to Infectious Salmon Inspection Service Anemia: Prevention, United States Department of the Interior Control, and Eradication U.S. Geological Survey United States Department of Commerce National Marine Fisheries Service Technical Bulletin No. 1902 The U.S. Departments of Agriculture (USDA), the Interior (USDI), and Commerce prohibit discrimination in all their programs and activities on the basis of race, color, national origin, sex, religion, age, disability, political beliefs, sexual orientation, or marital or family status. (Not all prohibited bases apply to all programs.) Persons with disabilities who require alternative means for communication of program information (Braille, large print, audiotape, etc.) should contact USDA’s TARGET Center at (202) 720–2600 (voice and TDD). To file a complaint of discrimination, write USDA, Director, Office of Civil Rights, Room 326–W, Whitten Building, 1400 Independence Avenue, SW, Washington, DC 20250–9410 or call (202) 720–5964 (voice and TDD). USDA, USDI, and Commerce are equal opportunity providers and employers. The opinions expressed by individuals in this report do not necessarily represent the policies of USDA, USDI, or Commerce. Mention of companies or commercial products does not imply recommendation or endorsement by USDA, USDI, or Commerce over others not mentioned. The Federal Government neither guarantees nor warrants the standard of any product mentioned. Product names are mentioned solely to report factually on available data and to provide specific information. Photo credits: The background illustration on the front cover was supplied as a photo micrograph by Michael Opitz, of the University of Maine, and is reproduced by permission. -

Agriculture and Food Processing in Armenia
SAMVEL AVETISYAN AGRICULTURE AND FOOD PROCESSING IN ARMENIA YEREVAN 2010 Dedicated to the memory of the author’s son, Sergey Avetisyan Approved for publication by the Scientifi c and Technical Council of the RA Ministry of Agriculture Peer Reviewers: Doctor of Economics, Prof. Ashot Bayadyan Candidate Doctor of Economics, Docent Sergey Meloyan Technical Editor: Doctor of Economics Hrachya Tspnetsyan Samvel S. Avetisyan Agriculture and Food Processing in Armenia – Limush Publishing House, Yerevan 2010 - 138 pages Photos courtesy CARD, Zaven Khachikyan, Hambardzum Hovhannisyan This book presents the current state and development opportunities of the Armenian agriculture. Special importance has been attached to the potential of agriculture, the agricultural reform process, accomplishments and problems. The author brings up particular facts in combination with historic data. Brief information is offered on leading agricultural and processing enterprises. The book can be a useful source for people interested in the agrarian sector of Armenia, specialists, and students. Publication of this book is made possible by the generous fi nancial support of the United States Department of Agriculture (USDA) and assistance of the “Center for Agribusiness and Rural Development” Foundation. The contents do not necessarily represent the views of USDA, the U.S. Government or “Center for Agribusiness and Rural Development” Foundation. INTRODUCTION Food and Agriculture sector is one of the most important industries in Armenia’s economy. The role of the agrarian sector has been critical from the perspectives of the country’s economic development, food safety, and overcoming rural poverty. It is remarkable that still prior to the collapse of the Soviet Union, Armenia made unprecedented steps towards agrarian reforms. -

Reimagining Riben Guizi: Japanese Tactical Media Performance After the 2010 Senkaku/Diaoyu Boat Collision Incident
International Journal of Communication 11(2017), 344–362 1932–8036/20170005 Reimagining Riben Guizi: Japanese Tactical Media Performance After the 2010 Senkaku/Diaoyu Boat Collision Incident YASUHITO ABE1 Doshisha University, Japan This article investigates a Japanese online participatory community, the Hinomoto Oniko project, that emerged after the Senkaku/Diaoyu boat collision incident of 2010 in the East China Sea. Drawing on tactical media as a conceptual framework, this study analyzes how the project challenged the prevailing meaning of a Chinese slur against the Japanese via tactical use of visual media and examines how its cultural and aesthetic performances were reproduced in the Japanese media landscape. This facilitates analysis of the implications of its cultural and aesthetic performances in a networked era. Keywords: tactical media, moe, history, Japan, China This study examines a Japanese online participatory community that emerged in Japan after the Senkaku/Diaoyu boat collision incident of 2010 in the East China Sea: the Hinomoto Oniko project. The project remade a Chinese term into various images of that term though visual media; specifically, the Hinomoto Oniko project transformed the pronunciation of the Chinese term into a Japanese reading and substituted cartoon-like characters for the term. In doing so, the project sought to create an alternative space for communication between Japanese and Chinese people, albeit briefly. The project did not necessarily succeed in making the most of an opportunity for promoting communication between Japanese and Chinese people, but the project highlights the characteristic of tactical media performance in East Asia. The Chinese term temporarily disrupted by the Hinomoto Oniko project is 日本鬼子 (Riben Guizi), which originally meant “Japanese are devils” in Chinese. -

Volkskalendev
Freiburger und Walliser Volkskalendev Î98Î teftftj \ 'M^ » •v' •""^j »s< ^k " • I VXXKSKALÊND6R FÜR FRÊIBURQV/NDWALLIS Vor 500 Jahren Eintritt Freiburgs und Solothurns in die Eidgenossenschaft Dank dem Bruder Klaus Geleitwort des altgewordenen Kalendermannes Liebe Freiburger und Walliser in aller Welt! Der Kalender erscheint nur einmal im Jahr. Ihr erwartet daher vom Kalendermann etwas ande res als vom Reporter einer Tageszeitung. Unser Kalender ist noch weltanschaulich einheitlich, d. h. in unserem Falle katholisch, während die Tageszeitungen nicht mehr eine, sondern ver schiedene religiöse und politische Anschauungen bedienen wollen. Unser Kalender kann auch nicht für alle Probleme des kommenden Jahres und darüber hinaus Lösungen anbieten. Er kann auch nicht über die tausend Geschehnisse der jüngsten Vergangenheit berichten. Der Kalender mann wird auf einige grundsätzliche Fragen hinweisen, die in christlichem Geist gelöst werden sollen. Ich nehme mir da ein Beispiel an einem berühmten Kalendermann, nämlich Alban Stolz; der war auch Priester wie ich, lebte auch in Freiburg, aber nicht im Üchtland, sondern im Breisgau. In einem ganz vergilbten Kalender fand ich sein Geleitwort für den Jahrgang 1881. Ich drucke es ab und schreibe daneben mein Geleitwort für 1981. Der Kalendermann F. N. Kalender für Zeit Kalender für Freiburg und Ewigkeit 1881 und Wallis 1981 Alban Stolz F. Neuwirth »Ich habe mich im Frühjahr 1880 besonnen: Auch ich habe mich im Frühjahr 1980 beson Erstens, ob ich wieder einen Kalender schrei nen: ben soll. Erstens, ob ich wieder den Kalender machen soll. Der Umstand, dass ich den Kalender seit 1951 Der Umstand, dass eben der Kalender in vie mache und dass ich selber mehr Jahrgänge auf len Häusern einkehrt und ein ganzes Jahr Her dem Buckel habe als der Kalender mit seinen berge bekommt, dass man also mit einem 72 Jahren, hat mich schon seit Jahren bewo einzigen Kalender in vielen Dörfern und Städ gen, einen jüngeren Kalendermann als Nach ten . -

The Missionary As Devil: Anti-Missionary Demonology in China, 1860–1930
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Loughborough University Institutional Repository Chapter 6 Thoralf Klein Anti-missionary Demonology in China 1 The Missionary as Devil: Anti-Missionary Demonology in China, 1860–1930 Thoralf Klein As a foreign student in China in the early 1990s, I once visited the historical site of Zazhidong camp in Chongqing together with a German friend. This is a place where the Chinese Nationalists, with the help of American advisers provided by the Sino-American Cooperation Organization (SACO), interned and tortured Communists and their sympathizers in the 1940s.1 It was a cold, grey, January day, and visitors were few. Apart from ourselves, I only recall a middle-aged Chinese couple walking in our direction. As they were passing us, I overheard the man say something to his wife. He was not speaking loudly, yet, perhaps because he mistook us for Americans and counted on our not understanding Chinese, what he said was clearly audible. It was just the two words yang guizi 洋鬼子 – ‘foreign devils’.2 This expression will be the focus of my subsequent examination of how European and North American missionaries in China became the object of processes of Othering. I am not suggesting in this article that the Chinese discourse on Europe can be reduced to the demonology implied in the term (yang) guizi; there existed other terms to denote missionaries and other foreigners, some of which – as we shall see – were more neutral. However, I think that the demonizing discourse on missionaries is important for two reasons: firstly, it was the strongest way in which the Christian presence in China, which was connected with imperialism from the mid-nineteenth century well into the twentieth, was construed as an alien and harmful force; secondly, over the same period, this discourse developed in a way that reflected the profound cultural change taking place in China at the time. -
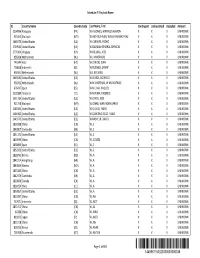
Schedule F-2 by Last Name
Schedule F-2 by Last Name ID Country Name Country Code Last Name, First Contingent Unliquidated Disputed Amount 1204096 Paraguay (PY) W A GOMES, MATHEUS RAMON X X X UNKNOWN 921652 Malaysia (MY) W ABD MUHAIMI, W MUHAMMAD FAIZ X X X UNKNOWN 1649270 United States (US) W CABRERA, PEDRO X X X UNKNOWN 1719541 United States (US) W DALMAN GENERAL SERVICES X X X UNKNOWN 1776164 Uruguay (UY) W DE LIMA, JOSE X X X UNKNOWN 956360 Netherlands (NL) W J M HOFHUIS X X X UNKNOWN 745344 Haiti (HT) W JUNIOR, JEAN X X X UNKNOWN 758668 Indonesia (ID) W KUENGO, SYARIF X X X UNKNOWN 956361 Netherlands (NL) W L BEUVING X X X UNKNOWN 1669241 United States (US) W LEMOS, RODRIGO X X X UNKNOWN 956362 Netherlands (NL) W M J HOFHUIS, W M J HOFHUIS X X X UNKNOWN 676497 Spain (ES) W M LIMA, RAQUEL X X X UNKNOWN 1301880 Tanzania (TZ) W MREMA, FREDRICK X X X UNKNOWN 1551784 United States (US) W O REIS, JOSE X X X UNKNOWN 921760 Malaysia (MY) W OMAR, WAN NORRIZAROS X X X UNKNOWN 1480191 United States (US) W Q GUSS, FABIO X X X UNKNOWN 1480192 United States (US) W QUINTINO GUSS, FABIO X X X UNKNOWN 1445973 United States (US) W RABKE JR, DAVID X X X UNKNOWN 1830388 China (CN) W, 1 X X X UNKNOWN 1842807 Cambodia (KH) W, 1 X X X UNKNOWN 1851171 United States (US) W, 1 X X X UNKNOWN 1830593 China (CN) W, 123456 X X X UNKNOWN 1838893 Spain (ES) W, 2 X X X UNKNOWN 1852261 United States (US) W, 3 X X X UNKNOWN 1828995 Bolivia (BO) W, A X X X UNKNOWN 1841014 Hong Kong (HK) W, A X X X UNKNOWN 1843854 Mexico (MX) W, A X X X UNKNOWN 1831883 China (CN) W, A X X X UNKNOWN 1842929 Cambodia