Download Slides
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

Interaction Between Web Browsers and Script Engines
IT 12 058 Examensarbete 45 hp November 2012 Interaction between web browsers and script engines Xiaoyu Zhuang Institutionen för informationsteknologi Department of Information Technology Abstract Interaction between web browser and the script engine Xiaoyu Zhuang Teknisk- naturvetenskaplig fakultet UTH-enheten Web browser plays an important part of internet experience and JavaScript is the most popular programming language as a client side script to build an active and Besöksadress: advance end user experience. The script engine which executes JavaScript needs to Ångströmlaboratoriet Lägerhyddsvägen 1 interact with web browser to get access to its DOM elements and other host objects. Hus 4, Plan 0 Browser from host side needs to initialize the script engine and dispatch script source code to the engine side. Postadress: This thesis studies the interaction between the script engine and its host browser. Box 536 751 21 Uppsala The shell where the engine address to make calls towards outside is called hosting layer. This report mainly discussed what operations could appear in this layer and Telefon: designed testing cases to validate if the browser is robust and reliable regarding 018 – 471 30 03 hosting operations. Telefax: 018 – 471 30 00 Hemsida: http://www.teknat.uu.se/student Handledare: Elena Boris Ämnesgranskare: Justin Pearson Examinator: Lisa Kaati IT 12 058 Tryckt av: Reprocentralen ITC Contents 1. Introduction................................................................................................................................ -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -

NET Framework
Advanced Windows Programming .NET Framework based on: A. Troelsen, Pro C# 2005 and .NET 2.0 Platform, 3rd Ed., 2005, Apress J. Richter, Applied .NET Frameworks Programming, 2002, MS Press D. Watkins et al., Programming in the .NET Environment, 2002, Addison Wesley T. Thai, H. Lam, .NET Framework Essentials, 2001, O’Reilly D. Beyer, C# COM+ Programming, M&T Books, 2001, chapter 1 Krzysztof Mossakowski Faculty of Mathematics and Information Science http://www.mini.pw.edu.pl/~mossakow Advanced Windows Programming .NET Framework - 2 Contents The most important features of .NET Assemblies Metadata Common Type System Common Intermediate Language Common Language Runtime Deploying .NET Runtime Garbage Collection Serialization Krzysztof Mossakowski Faculty of Mathematics and Information Science http://www.mini.pw.edu.pl/~mossakow Advanced Windows Programming .NET Framework - 3 .NET Benefits In comparison with previous Microsoft’s technologies: Consistent programming model – common OO programming model Simplified programming model – no error codes, GUIDs, IUnknown, etc. Run once, run always – no "DLL hell" Simplified deployment – easy to use installation projects Wide platform reach Programming language integration Simplified code reuse Automatic memory management (garbage collection) Type-safe verification Rich debugging support – CLR debugging, language independent Consistent method failure paradigm – exceptions Security – code access security Interoperability – using existing COM components, calling Win32 functions Krzysztof -
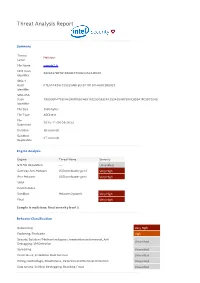
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Automated Malware Analysis Report For
ID: 310931 Sample Name: 44S5D444F55G8222Y55UU44S4S.vbs Cookbook: default.jbs Time: 07:32:12 Date: 07/11/2020 Version: 31.0.0 Red Diamond Table of Contents Table of Contents 2 Analysis Report 44S5D444F55G8222Y55UU44S4S.vbs 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Startup 4 Malware Configuration 4 Yara Overview 4 Sigma Overview 4 Signature Overview 4 AV Detection: 5 Data Obfuscation: 5 Persistence and Installation Behavior: 5 Malware Analysis System Evasion: 5 HIPS / PFW / Operating System Protection Evasion: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 7 URLs 7 Domains and IPs 8 Contacted Domains 8 Contacted URLs 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 9 General Information 9 Simulations 10 Behavior and APIs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 11 General 11 File Icon 12 Network Behavior 12 TCP Packets 12 HTTP Request Dependency Graph 12 HTTP Packets 12 Code Manipulations 13 Statistics 13 Behavior 13 System Behavior 14 Analysis Process: wscript.exe PID: 6124 Parent PID: 3388 14 Copyright null 2020 Page 2 of 15 General 14 File Activities 14 File Created 14 File Written 14 Registry Activities 15 Analysis Process: wscript.exe PID: 5560 Parent PID: 6124 15 General 15 File Activities 15 Disassembly 15 Code Analysis 15 Copyright null 2020 Page 3 of -

Rapid Prototyping for Virtual Environments
Old Dominion University ODU Digital Commons Electrical & Computer Engineering Theses & Dissertations Electrical & Computer Engineering Winter 2008 Rapid Prototyping for Virtual Environments Emre Baydogan Old Dominion University Follow this and additional works at: https://digitalcommons.odu.edu/ece_etds Part of the Computer Sciences Commons, and the Electrical and Computer Engineering Commons Recommended Citation Baydogan, Emre. "Rapid Prototyping for Virtual Environments" (2008). Doctor of Philosophy (PhD), Dissertation, Electrical & Computer Engineering, Old Dominion University, DOI: 10.25777/pb9g-mv96 https://digitalcommons.odu.edu/ece_etds/45 This Dissertation is brought to you for free and open access by the Electrical & Computer Engineering at ODU Digital Commons. It has been accepted for inclusion in Electrical & Computer Engineering Theses & Dissertations by an authorized administrator of ODU Digital Commons. For more information, please contact [email protected]. RAPID PROTOTYPING FOR VIRTUAL ENVIRONMENTS by Emre Baydogan B.S. June 1999, Marmara University, Turkey M.S. June 2001, Marmara University, Turkey A Dissertation Submitted to the Faculty of Old Dominion University in Partial Fulfillment of the Requirement for the Degree of DOCTOR OF PHILOSOPHY ELECTRICAL AND COMPUTER ENGINEERING OLD DOMINION UNIVERSITY December 2008 Lee A. Belfore, H (Director) K. Vijayan Asari Jesmca R. Crouch ABSTRACT RAPID PROTOTYPING FOR VIRTUAL ENVIRONMENTS Emre Baydogan Old Dominion University, 2008 Director: Dr. Lee A. Belfore, II Development of Virtual Environment (VE) applications is challenging where appli cation developers are required to have expertise in the target VE technologies along with the problem domain expertise. New VE technologies impose a significant learn ing curve to even the most experienced VE developer. The proposed solution relies on synthesis to automate the migration of a VE application to a new unfamiliar VE platform/technology. -

Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor Matt Graeber
Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor Matt Graeber Black Hat 2015 Introduction As technology is introduced and subsequently deprecated over time in the Windows operating system, one powerful technology that has remained consistent since Windows NT 4.01 and Windows 952 is Windows Management Instrumentation (WMI). Present on all Windows operating systems, WMI is comprised of a powerful set of tools used to manage Windows systems both locally and remotely. While it has been well known and utilized heavily by system administrators since its inception, WMI was likely introduced to the mainstream security community when it was discovered that it was used maliciously as one component in the suite of exploits and implants used by Stuxnet3. Since then, WMI has been gaining popularity amongst attackers for its ability to perform system reconnaissance, AV and VM detection, code execution, lateral movement, persistence, and data theft. As attackers increasingly utilize WMI, it is important for defenders, incident responders, and forensic analysts to have knowledge of WMI and to know how they can wield it to their advantage. This whitepaper will introduce the reader to WMI, actual and proof-of-concept attacks using WMI, how WMI can be used as a rudimentary intrusion detection system (IDS), and how to perform forensics on the WMI repository file format. WMI Architecture 1 https://web.archive.org/web/20050115045451/http://www.microsoft.com/downloads/details.aspx?FamilyID=c17 4cfb1-ef67-471d-9277-4c2b1014a31e&displaylang=en 2 https://web.archive.org/web/20051106010729/http://www.microsoft.com/downloads/details.aspx?FamilyId=98A 4C5BA-337B-4E92-8C18-A63847760EA5&displaylang=en 3 http://poppopret.blogspot.com/2011/09/playing-with-mof-files-on-windows-for.html WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM)4 and Common Information Model (CIM)5 standards published by the Distributed Management Task Force (DMTF)6. -

Download “The Spy Who Encrypted Me” Case Study
April, 2020 APT41 The Spy Who Encrypted Me Contents APT41 – A spy who steals or a thief who spies ......................................................... 3 The investigation .................................................................................................. 3 The base .......................................................................................................... 4 The toolkit ........................................................................................................ 5 The point of entry .............................................................................................. 6 The initial vector of compromise .......................................................................... 8 Indicators of Compromise .................................................................................... 10 References ......................................................................................................... 11 244 Fifth Avenue, Suite 2035, New York, NY 10001 LIFARS.com (212) 222-7061 [email protected] APT41 – A SPY WHO STEALS OR A THIEF WHO SPIES An advanced persistent threat (“APT”) is, typically, either a nation-state actor and aims at benefiting its state through sabotage, espionage, or industrial espionage; or a cybercriminal and its aims are to steal money through theft, fraud, ransom or blackmail. The Chinese-based threat actor APT41 blurs the lines: known to have run financially- motivated operations against the videogame industry as early as 2012, it got its notoriety in 2013 when -

Document Object Model †DOM‡ Level 1 Specification
Document Object Model (DOM) Level 1 Specification REC-DOM-Level-1-19981001 Document Object Model (DOM) Level 1 Specification Version 1.0 W3C Recommendation 1 October, 1998 This version http://www.w3.org/TR/1998/REC-DOM-Level-1-19981001 http://www.w3.org/TR/1998/REC-DOM-Level-1-19981001/DOM.ps http://www.w3.org/TR/1998/REC-DOM-Level-1-19981001/DOM.pdf http://www.w3.org/TR/1998/REC-DOM-Level-1-19981001/DOM.tgz http://www.w3.org/TR/1998/REC-DOM-Level-1-19981001/DOM.zip http://www.w3.org/TR/1998/REC-DOM-Level-1-19981001/DOM.txt Latest version http://www.w3.org/TR/REC-DOM-Level-1 Previous versions http://www.w3.org/TR/1998/PR-DOM-Level-1-19980818 http://www.w3.org/TR/1998/WD-DOM-19980720 http://www.w3.org/TR/1998/WD-DOM-19980416 http://www.w3.org/TR/WD-DOM-19980318 http://www.w3.org/TR/WD-DOM-971209 http://www.w3.org/TR/WD-DOM-971009 WG Chair Lauren Wood, SoftQuad, Inc. Editors Vidur Apparao, Netscape Steve Byrne, Sun Mike Champion, ArborText Scott Isaacs, Microsoft Ian Jacobs, W3C Arnaud Le Hors, W3C Gavin Nicol, Inso EPS Jonathan Robie, Texcel Research Robert Sutor, IBM Chris Wilson, Microsoft Lauren Wood, SoftQuad, Inc. Principal Contributors Vidur Apparao, Netscape Steve Byrne, Sun (until November 1997) Mike Champion, ArborText, Inc. 1 Status of this document Scott Isaacs, Microsoft (until January, 1998) Arnaud Le Hors, W3C Gavin Nicol, Inso EPS Jonathan Robie, Texcel Research Peter Sharpe, SoftQuad, Inc. Bill Smith, Sun (after November 1997) Jared Sorensen, Novell Robert Sutor, IBM Ray Whitmer, iMall Chris Wilson, Microsoft (after January, 1998) Status of this document This document has been reviewed by W3C Members and other interested parties and has been endorsed by the Director as a W3C Recommendation. -

Co-Development, Delivery and Structural Analysis of a Computer Game Course
Otto-von-Guericke-University Magdeburg University of Otago, Dunedin Department of Computer Science Research Report Co-Development, Delivery and Structural Analysis of a Computer Game Course Lennart Nacke Supervisors: Professor Dr Maic Masuch (Otto-von-Guericke-University Magdeburg), Mr Simon McCallum (University of Otago) Nacke, Lennart: Co-Development, Delivery and Structural Analysis of a Computer Game Course Research Report, Otto-von-Guericke-University Magdeburg, June 2004. i Internship Task Computer game design is still a young, growing subject in computer science education. Due to the industry’s need for qualified personnel, who appreciate the complexities of computer game design, many new academic courses are being created. As computer game design is a new topic there is still much research required into ped- agogy and delivery. The focus of this internship is to assist in the development and delivery of an undergraduate course on computer game design. There are three phases to this internship: 1. Development This includes the research on suitable game engines, taking into account the limited budget available for the course. It also includes • the analysis of proposed lecture topics corresponding to the IGDA Curriculum Framework [IGD03] • research and study on software engineering topics, such as version control A systems like CVS and documentation with LTEX 2. Delivery Including assistance in lectures for the course as well as tutoring. To further help the students we also include: • an introduction to interactive fiction using the Inform environment and con- struction of the first assignment • the creation and maintenance of an interactive website accompanying the course, which includes a student feedback system, a forum and a maintenance system for lecture topics and textbook errata 3.