Proyecto Final De Carrera
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Smart Phone User Manual
Smart Phone User Manual www.htc.com 2 Congratulations on the purchase of your new Windows Mobile® Smartphone! Please Read Before Proceeding. THIS PHONE IS NOT FULLY CHARGED WHEN YOU TAKE IT OUT OF THE BOX. DO NOT REMOVE THE BATTERY PACK WHEN THE PHONE IS CHARGING. YOUR WARRANTY IS INVALIDATED IF YOU OPEN OR TAMPER WITH THE PHONE'S OUTER CASING. PRIVACY RESTRICTIONS Some countries require full disclosure of recorded telephone conversations, and stipulate that you must inform the person with whom you are speaking that the conversation is being recorded. Always obey the relevant laws and regulations of your country when using the recording feature of your phone. COPYRIGHT INFORMATION Copyright © 2007 High Tech Computer Corp. All Rights Reserved. , , , ExtUSB, HTC Home, and HTC Care are trademarks and/or service marks of High Tech Computer Corp. Microsoft, MS-DOS, Windows, Windows Vista, Windows NT, Windows Server, Windows Mobile, ActiveSync, Windows Media, Excel, Internet Explorer, MSN, Outlook, PowerPoint, and Word are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Bluetooth and the Bluetooth logo are trademarks owned by Bluetooth SIG, Inc. Wi-Fi is a registered trademark of the Wireless Fidelity Alliance, Inc. microSD is a trademark of SD Card Association. Java, J2ME and all other Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. Copyright © 2007, Adobe Systems Incorporated. Copyright © 2007, Macromedia Netherlands, B.V. 3 Macromedia, Flash, Macromedia Flash, Macromedia Flash Lite and Reader are trademarks and/or registered trademarks of Macromedia Netherlands, B.V. -

Arrive on Time with Garmin Mobile™ XT
Smartphone Compatibility Guide Garmin Mobile™ XT is compatible with the following phones: Amoi N8 Gigabyte g-Smart i350 Dopod D810 O2 XDA Stealth Amoi N800 HP iPAQ 600 / 610 / 612 / 614 Dopod U1000 Orange SPV M650 Amoi N810 HP iPAQ 900 / 910 / 912 / 914 Hop-On HOP2001 Orange SPV M700 Asus P526 HTC Advantage X7501 HP iPAQ hw6510 Psion Teklogix iKon Asus P527 HTC Omni HP iPAQ hw6515 RoverPC N6 Asus P535 HTC P6500 HP iPAQ hw6910 / hw6920 / hw6940 RoverPC N7 Asus P550 HTC P6550 HP iPAQ hw6915 / hw6925 / hw6945 / hw6965 RoverPC Q6 Asus P750 HTC Polaris HTC Advantage X7500 Samsung SGH-i617 BlackJack II BenQ-Siemens P51 HTC S420 HTC Cruise Samsung SGH-i617 Jack Dopod CHT 9100 HTC Tilt HTC P3300 SFR S300+ Dopod CHT 9110 HTC Touch Cruise HTC P3600 Toshiba Protégé G910 Dopod P800W HTC Vogue HTC P4550 Vodafone v1620 E-TEN glofiish M700 i-mate Ultimate 8502 HTC P5500 Vodafone VPA Compact GPS E-TEN glofiish M800 Intermec CN3 HTC S640 Vodafone VPA Compact V E-TEN glofiish X500 Mitac Mio A501 HTC S730 XPA v1510 E-TEN glofiish X600 Motorola MC35 HTC TyTN II XPA v1520 E-TEN glofiish X800 Okwap K871 Mitac Mio A700 XPA v1615 E-TEN InfoTouch G500 ORSiO g735 Mitac Mio A701 Nokia 6110 Navigator E-TEN InfoTouch G500+ Pharos GPS Phone 600e Mitac Mio A702 Nokia N82 Fujitsu-Siemens Pocket LOOX T810 RoverPC E5 Motorola Q9h Nokia N95 Fujitsu-Siemens Pocket LOOX T830 Samsung SGH-i640v O2 XDA Orbit Gigabyte g-Smart i300 Torq N100 O2 XDA Orbit II Lost? Garmin Mobile XT garmin.co.uk Arrive on time with Garmin Mobile™ XT. -
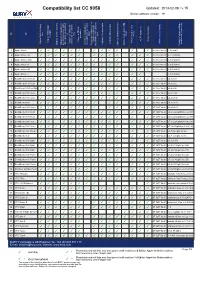
CC9058-Compatibility
Compatibility list CC 9058 Updated: 2013-02-08 / v.15 Device software version: 19 on No key level keys Card Type tags) Phone strength activation A2DP supported Phone s REDIAL Charger available / private mode with Activation Bluetooth Phone book entries: Display: GSM-signal Call lists: Missed calls Article code (Charger) connection with device Display: Battery charge Bluetooth connection to used to test/ Comments after ignition is switched Access to mobile phone Call lists: Received calls voice-dial function (voice Phone book entries: SIM Display: Service provider the last connected phone Call lists: Dialled numbers Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 3.0(7a341) 2 Apple iPhone 3G ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 4.2.1 (8a306) 3 Apple iPhone 3GS ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 4 Apple iPhone 4 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 5 Apple iPhone 4S ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 6 Apple iPhone 5 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 6.1 (10b143) 7 BlackBerry 8100 Pearl ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.69 8 BlackBerry 8110 Pearl ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.55 9 BlackBerry 8220 Pearl Flip ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.0.94 10 BlackBerry 8300 Curve ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 os 5.1.342 11 BlackBerry 8310 Curve ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.180 12 BlackBerry 8800 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 -

BURY Compatibility List Generator
Compatibility list CC 9068 Updated: Device software version: Box SW: 106Display SW: 140 on No call key level keys Card SMS Type Phone strength activation conference phone name SMS / Popup between calls A2DP supported Phone s REDIAL reject waiting call Charger available / private mode with Activation Bluetooth Phone book entries: Display: GSM-signal Multiparty call: Swap E-mail read Function Messages: Download Call lists: Missed calls Article code (Charger) connection with device Multiparty call: accept / Display: Battery charge Bluetooth connection to used to test/ Comments after ignition is switched Multiparty call: merge to Required default/factory Call lists: Received calls Multiparty call: hold on 1 Messages: Receive new Phone book entries: SIM Display: Service provider the last connected phone OPP: Synch. phone book Call lists: Dialled numbers Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 3.0 (7a341) 2 Apple iPhone 3G ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 4.2.1 (8c148) 3 Apple iPhone 3GS ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 4 Apple iPhone 4 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 5 Apple iPhone 4S ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 6 BlackBerry 8110 Pearl ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.55 7 BlackBerry 8220 Pearl Flip ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.0.94 8 BlackBerry 8300 Curve ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ -

Cell Phones and Pdas
eCycle Group - Check Prices Page 1 of 19 Track Your Shipment *** Introductory Print Cartridge Version Not Accepted February 4, 2010, 2:18 pm Print Check List *** We pay .10 cents for all cell phones NOT on the list *** To receive the most for your phones, they must include the battery and back cover. Model Price Apple Apple iPhone (16GB) $50.00 Apple iPhone (16GB) 3G $75.00 Apple iPhone (32GB) 3G $75.00 Apple iPhone (4GB) $20.00 Apple iPhone (8GB) $40.00 Apple iPhone (8GB) 3G $75.00 Audiovox Audiovox CDM-8930 $2.00 Audiovox PPC-6600KIT $1.00 Audiovox PPC-6601 $1.00 Audiovox PPC-6601KIT $1.00 Audiovox PPC-6700 $2.00 Audiovox PPC-XV6700 $5.00 Audiovox SMT-5500 $1.00 Audiovox SMT-5600 $1.00 Audiovox XV-6600WOC $2.00 Audiovox XV-6700 $3.00 Blackberry Blackberry 5790 $1.00 Blackberry 7100G $1.00 Blackberry 7100T $1.00 Blackberry 7105T $1.00 Blackberry 7130C $2.00 http://www.ecyclegroup.com/checkprices.php?content=cell 2/4/2010 eCycle Group - Check Prices Page 2 of 19 Search for Pricing Blackberry 7130G $2.50 Blackberry 7290 $3.00 Blackberry 8100 $19.00 Blackberry 8110 $18.00 Blackberry 8120 $19.00 Blackberry 8130 $2.50 Blackberry 8130C $6.00 Blackberry 8220 $22.00 Blackberry 8230 $15.00 Blackberry 8300 $23.00 Blackberry 8310 $23.00 Blackberry 8320 $28.00 Blackberry 8330 $5.00 Blackberry 8350 $20.00 Blackberry 8350i $45.00 Blackberry 8520 $35.00 Blackberry 8700C $6.50 Blackberry 8700G $8.50 Blackberry 8700R $7.50 Blackberry 8700V $6.00 Blackberry 8703 $1.00 Blackberry 8703E $1.50 Blackberry 8705G $1.00 Blackberry 8707G $5.00 Blackberry 8707V -

Acer Acer S200 F1 Neotouch Acer Acer E101 Asus Asus 1210 VDA
Acer Acer S200 F1 neoTouch Acer Acer E101 Asus Asus 1210 VDA Audiovox/UTStarcom/PCD SMT-5800 Audiovox/UTStarcom/PCD PPC-6700 Audiovox/UTStarcom/PCD XV-6700 Audiovox/UTStarcom/PCD XV-6850 Audiovox/UTStarcom/PCD XV-6875 Touch Pro 2 Audiovox/UTStarcom/PCD XV-6900 Dopod Dopod S1 Dopod Dopod D600 Dopod Dopod P800 Dopod Dopod P860 Dopod Dopod T2222 Dopod Dopod T3238 Dopod Dopod T8288 Dopod Dopod T8388 Garmin Nuvi 200 Garmin Oregon 200 Garmin Nuvi 200W Garmin Nuvi 205 Garmin Nuvi 205W Garmin Nuvi 250 Garmin Nuvi 250W Garmin Nuvi 255 Garmin Nuvi 255W Garmin Nuvi 260W Garmin Nuvi 265 Garmin Nuvi 265W Garmin Nuvi 275 Garmin Nuvi 285W Garmin Nuvi 350 Garmin Nuvi 360 Garmin Oregon 450 Garmin Oregon 450T Garmin Zumo 450 Garmin Nuvi 465 Garmin Nuvi 500 Garmin Nuvi 550 Garmin Oregon 550 Garmin Oregon 550T Garmin Zumo 550 Garmin GPSmap 620 Garmin GPSmap 640 Garmin Nuvi 660 Garmin Zumo 660 Garmin Zumo 665 Garmin Nuvi 680 NA Garmin Nuvi 710 Garmin Nuvi 750 Garmin Nuvi 760 Garmin Nuvi 765 Garmin Nuvi 780 Garmin Nuvi 855 Garmin Nuvi 1200 Garmin Nuvi 1210T Garmin Nuvi 1240 Garmin Nuvi 1250 Garmin Nuvi 1300 Garmin Nuvi 1310 Garmin Nuvi 1350 Garmin Nuvi 1390 Garmin Nuvi 1450 Garmin Nuvi 1490 Garmin Nuvi 1690 Garmin Nuvi 1690 BMW edition Garmin Street Pilot 2730 Garmin Nuvi 3760 Garmin Nuvi 3790 Garmin Nuvi 5000 HTC HTC T8585 Touch HD2 HTC HTC S52x Dash 3G HTC HTC S710 HTC HTC S730 HTC HTC S740 HTC HTC T3333 Mega HTC HTC Touch2 HTC HTC P3450 Touch HTC HTC P3470 HTC HTC P3650 Touch Cruise HTC HTC P3700 Touch Diamond HTC HTC T4242 Touch Cruise HTC HTC XV6175 HTC -
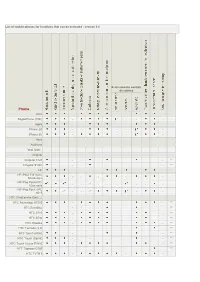
List of Mobile Phones for Functions That Can Be Activated - Version 5.4
List of mobile phones for functions that can be activated - version 5.4 Scaricamento contatti da rubrica Phone Amoi SkypePhone (TRE) - - - - Apple iPhone 2G - - - - - iPhone 3G - - - - Asus Audiovox Vedi Qtek... Cingular Cingular 8125 - - - ** Cingular SYNC - - - ** HP HP iPAQ 514 Voice - - - - - Messenger HP iPaq Pocket PC - - -* - - - - - - 63xx serie HP iPaq Pocket PC -* - - -* - - 6515 HTC (Vedi anche Qtek....) HTC Advantage X7500 - - ** HTC Excalibur - - - ** HTC S710 - - ** HTC S730 - - ** HTC Shadow - - ** HTC Tornado (2.0) ** HTC Touch (Alltel) - - - ** HTC Touch (Sprint) - - - - ** HTC Touch Cruise P3650 - - ** HTC Typhoon C500 ** HTC TyTN II - - - HTC Wizard ** Qteck/HTC P3300 - - - - - - - Qteck/HTC Touch Diamond - - - i-Mate Vedi Qtek LG LG CU500 - - ** LG KE850 - - - - - - - - LG KE850 Prada - - - ** LG KG800 (Chocolate) - - - - - - - - ** LG KS20 - - ** LG KU990 - - - ** LG KU800 - - - - - - - - - ** LG Shine (CU720) N N N ** LG Trax (CU575) N N N N N N ** LG U8550 - - - - -* LG U880 - - - - - - - - LG U900 - - - - - - - - Motorola Motorola A830/ - - - - A835 Motorola A1000 - - - - -* - Motorola A1200 Ming N ** Motorola E1000 - Motorola E398 - - - Motorola i615 N ** Motorola i880 N ** Motorola KRZR K1 - Motorola MPX220 - - - - - - Motorola RAZR2V9/ KRZR K3/ RAZR V3xx/ RAZR - MaxxV6 Motorola RAZR V3i/V3r ** Motorola RAZR V3t ** Motorola RAZR V6 Maxx ** Motorola RIZR Z3 - Motorola ROKR E6 N N ** Motorola Sidekick Slide N N N N ** Motorola SLVR L6 - Motorola SLVR L7 - Motorola U9 N N ** Motorola RAZR V3 - - Motorola V8 - - Motorola -

Pointsec Mobile Smartphone (Windows Mobile) 3.2.4 Release Notes
Pointsec Mobile Smartphone (Windows Mobile) 3.2.4 Release Notes Revised: March 23, 2009 This Release Notes document provides essential operating requirements and describes known issues for Pointsec Mobile Smartphone (Windows Mobile) 3.2.4. Review this information before installing this product. Note - There may be an updated version of this document and of the other documents you received with your copy of Pointsec Mobile Smartphone (Windows Mobile). You can access the latest version at: http://supportcontent.checkpoint.com/documentation_download?id=8966 In This Document About This Document page 1 About Pointsec Mobile Smartphone (Windows Mobile) page 2 New in This Release page 2 Supported Smartphones page 2 3rd-party Software page 3 System Requirements page 4 General Recommendations page 4 Compatibility between Releases page 5 Compatibility with Other Programs page 5 Known Issues in this Release page 6 FYI page 7 Documentation Feedback page 7 About This Document This document contains information about Pointsec Mobile Smartphone (Windows Mobile) version 3.2.4, such as new features and functions in this release, what problems have been fixed since the previous release and system requirements. In this document, the abbreviation N/A is used. N/A means Not Applicable. Pointsec Mobile Smartphone (Windows Mobile) is also referred to as Pointsec Mobile or Pointsec. Releases prior to version 3.1.0 are referred to by the previous name, that is, Pointsec for Smartphone (Windows Mobile 5). Copyright © 2009 Pointsec Mobile Technologies AB, a Check Point Software Technologies company. All rights reserved 1 About Pointsec Mobile Smartphone (Windows Mobile) About Pointsec Mobile Smartphone (Windows Mobile) Pointsec Mobile provides users of Windows Mobile 5.0 and Windows Mobile 6-based devices with automatic, real-time encryption of information including Microsoft Outlook e-mail and notes - providing convenient and enforceable handheld security for enterprises on the move. -

Acer Airis Alcatel Alltel Amoi Amoisonic Anextek Apple Arima
Acer 1 n10 1 1 n311 1 1 S100 Liquid 1 1 X960 1 Airis 1 T480 1 Alcatel 1 ELLE No 1 1 1 ELLE No 3 1 1 One Touch 355 1 1 One Touch 556 1 1 One Touch 557 1 1 One Touch 565 1 1 One Touch 708 1 1 One Touch 735i 1 1 One Touch 756 1 1 One Touch 757 1 1 One Touch 800 1 1 One Touch C551 1 1 One Touch C552 1 1 One Touch C635 1 1 One Touch C651 1 1 One Touch C652 1 1 One Touch C750 1 1 One Touch S853 1 1 One Touch V670 1 Alltel 1 PPC-6800 1 Amoi 1 A310 1 1 D85 1 1 D89 1 1 E72 1 1 F8 1 1 F90 1 1 H9 1 1 M636 1 1 N810 1 1 WP-S1 Skypephone 1 Amoisonic 1 9201 1 AnexTek 1 SP230 1 Apple 1 iPad 1 1 iPhone 1 1 iPod Touch 1 Arima 1 2850 1 Asus 1 1210 1 1 Galaxy II 1 1 Galaxy Mini 1 1 J100 1 1 J101 1 1 J102 1 1 M303 1 1 M530w 1 1 M930 1 1 P320 1 1 P505 1 1 P525 1 1 P526 1 1 P527 1 1 P550 1 1 P552 1 1 P735 1 1 P750 1 1 V80 1 AT&T 1 8900 Tilt 1 1 8925 Tilt 1 Audiovox 1 CDM-8450 1 1 CDM-8450SP 1 1 CDM-8455 1 1 CDM-8615 1 1 CDM-8900 1 1 CDM-8910 1 1 CDM-8912 1 1 CDM-8915 1 1 CDM-8920 1 1 CDM-8930 1 1 PM-8912 1 1 PM-8920 1 1 PPC-6600 / PPC-6601 1 1 PPC-6700 1 1 SMT-5600 1 1 VI600 1 BenQ 1 A500 1 1 A5001 1 1 A520 1 1 CL71 1 1 E72 1 1 E81 1 1 M315 1 1 M350 1 1 M580A 1 1 Morpheus 1 1 P30 1 1 P50 1 1 S660C 1 1 S668C 1 1 S670C 1 1 S680C 1 1 S700 1 1 S7001 1 1 S82 1 1 S830C 1 1 U700 1 1 Z2 1 BenQ-Siemens 1 C81 1 1 C81F 1 1 E71 1 1 EF51 1 1 EF81 1 1 EF91 1 1 EL71 1 1 M81 1 1 P51 1 1 S68 1 1 S80 1 1 S81 1 Bird 1 D660 1 1 E810 1 1 S689 1 1 SC01 1 1 SC24 1 1 V007 1 BlackBerry 1 7100g 1 1 7100i 1 1 7100r 1 1 7100t 1 1 7100v 1 1 7100x 1 1 7105t 1 1 7130c 1 1 7130e 1 1 7130g -

Arrive on Time with Garmin Mobile™ XT
Smartphone Compatibility Guide Garmin Mobile™ XT is compatible with the following phones: Amoi N8 Gigabyte g-Smart i350 Dopod D810 O2 XDA Stealth Amoi N800 HP iPAQ 600 / 610 / 612 / 614 Dopod U1000 Orange SPV M650 Amoi N810 HP iPAQ 900 / 910 / 912 / 914 Hop-On HOP2001 Orange SPV M700 Asus P526 HTC Advantage X7501 HP iPAQ hw6510 Psion Teklogix iKon Asus P527 HTC Omni HP iPAQ hw6515 RoverPC N6 Asus P535 HTC P6500 HP iPAQ hw6910 / hw6920 / hw6940 RoverPC N7 Asus P550 HTC P6550 HP iPAQ hw6915 / hw6925 / hw6945 / hw6965 RoverPC Q6 Asus P750 HTC Polaris HTC Advantage X7500 Samsung SGH-i617 BlackJack II BenQ-Siemens P51 HTC S420 HTC Cruise Samsung SGH-i617 Jack Dopod CHT 9100 HTC Tilt HTC P3300 SFR S300+ Dopod CHT 9110 HTC Touch Cruise HTC P3600 Toshiba Protégé G910 Dopod P800W HTC Vogue HTC P4550 Vodafone v1620 E-TEN glofiish M700 i-mate Ultimate 8502 HTC P5500 Vodafone VPA Compact GPS E-TEN glofiish M800 Intermec CN3 HTC S640 Vodafone VPA Compact V E-TEN glofiish X500 Mitac Mio A501 HTC S730 XPA v1510 E-TEN glofiish X600 Motorola MC35 HTC TyTN II XPA v1520 E-TEN glofiish X800 Okwap K871 Mitac Mio A700 XPA v1615 E-TEN InfoTouch G500 ORSiO g735 Mitac Mio A701 Nokia 6110 Navigator E-TEN InfoTouch G500+ Pharos GPS Phone 600e Mitac Mio A702 Nokia N82 Fujitsu-Siemens Pocket LOOX T810 RoverPC E5 Motorola Q9h Nokia N95 Fujitsu-Siemens Pocket LOOX T830 Samsung SGH-i640v O2 XDA Orbit Gigabyte g-Smart i300 Torq N100 O2 XDA Orbit II Lost? Garmin Mobile XT garmin.co.uk Arrive on time with Garmin Mobile™ XT. -
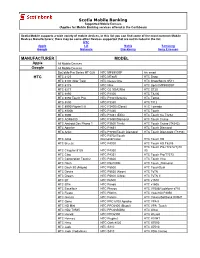
Supported Devices
Scotia Mobile Banking Supported Mobile Devices (Applies for Mobile Banking services offered in the Caribbean) Scotia Mobile supports a wide variety of mobile devices, in this list you can find some of the most common Mobile Devices Manufacturers; there may be some other Devices supported that are not included in the list. HTC Apple LG Nokia Samsung Google Motorola Blackberry Sony Ericsson MANUFACTURER MODEL Apple All Mobile Devices Google All Mobile Devices DoCoMo Pro Series HT-02A HTC MP6950SP htc smart HTC HTC 2125 HTC MTeoR HTC Snap HTC 3100 (Star Trek) HTC Nexus One HTC Snap/Sprint S511 HTC 6175 HTC Nike HTC Sprint MP6900SP HTC 6277 HTC O2 XDA2Mini HTC ST20 HTC 6850 HTC P3300 HTC T8290 HTC 6850 Touch Pro HTC P3301/Artemis HTC Tattoo HTC 8500 HTC P3350 HTC Tilt 2 HTC 8900/Pilgrim/Tilt HTC P3400i (Gene) HTC Tornado HTC 8900b HTC P3450 HTC Touch HTC 9090 HTC P3451 (Elfin) HTC Touch 3G T3232 HTC ADR6300 HTC P3490/Diamond HTC Touch Cruise HTC Android Dev Phone 1 HTC P3600 Trinity HTC Touch Cruise (T4242) HTC Apache HTC P3651 HTC Touch Diamond HTC Artist HTC P3700/Touch Diamond HTC Touch Diamond2 (T5353) HTC P3702/Touch HTC Atlas Diamond/Victor HTC Touch HD HTC Breeze HTC P4000 HTC Touch HD T8285 HTC Touch Pro (T7272/TyTn HTC Cingular 8125 HTC P4350 III) HTC Cleo HTC P4351 HTC Touch Pro/T7373 HTC Corporation Touch2 HTC P4600 HTC Touch Viva HTC Dash HTC P5310BM HTC Touch_Diamond HTC Dash 3G (Maple) HTC P5500 HTC TouchDual HTC Desire HTC P5530 (Neon) HTC TyTN HTC Dream HTC P5800 (Libra) HTC TyTN II HTC Elf HTC P6500 HTC v1510 HTC Elfin HTC -

On Consumer Decision Strategies: New Approaches for Studying And
Universit´ede Lausanne Facult´edes sciences sociales et politiques On Consumer Decision Strategies: New Approaches for Studying and Aiding Preferential Choices Th`esepr´esent´ee`ala Facult´edes sciences sociales et politiques de l'Universit´ede Lausanne pour obtenir le grade de docteur en psychologie par Nils Reisen Lausanne 2009 iii In psychology, invoking \strategies" to explain funny data is the last refuge of the clueless. Steven Pinker iv Acknowledgements First of all, I want to thank my two main supervisors Ulrich Hoffrage and Fred Mast for their support and guidance. Special thanks go to Ulrich Hoffrage for his constant and always immediate assistance. His door is always open, both literally and figuratively. I extend my appreciation to my three colleagues Chris White, Jan K. Woike, and Sebastian Hafenbr¨adl. They were always open for questions and we had many enriching discussions. I also want to thank all the other colleagues who provided help with the planning, execution, and analysis of my experiments. Moreover, I would like to thank the following people for their help with the experiments. For Experiment 1, my thanks go to Giovanni Rivera Diaz, Ada Lezama Lugo, Huseyin Cumhur Tekin, and Eren Vardarli for their help with preparing the material, writing the program, and collecting the data, and Chris M. White for help with the simulations. For Experiment 2, I thank Lucas Sinclair for programming MouseWorkshop, Dario Bombari for his help with the eye tracking equipment, Gregory Affolter, Richard Ciapala, Julien Finci, Gabriella Sinicco, and Vasko Vitanov for their help with the data collection and Felix Reisen for his help with the programming of the data analyses.