The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Is Threat Hunting?
$whoami ◎ Apurv Singh Gautam (@ASG_Sc0rpi0n) ◎ Security Researcher, Threat Intel/Hunting ◎ Cybersecurity @ Georgia Tech ◎ Prior: Research Intern at ICSI, UC Berkeley ◎ Hobbies ◎ Contributing to the security community ◎ Gaming/Streaming (Rainbow 6 Siege) ◎ Hiking, Lockpicking ◎ Social ◎ Twitter - @ASG_Sc0rpi0n ◎ Website – https://apurvsinghgautam.me 2 Agenda ◎ Introduction to the Dark Web ◎ Why hunting on the Dark Web? ◎ Methods to hunt on the Dark Web ◎ Can the Dark Web hunting be automated? ◎ Overall Picture ◎ OpSec? What’s that? ◎ Conclusion 3 Clear Web? Deep Web? Dark Web? 5 Image Source: UC San Diego Library Accessing the Dark Web ◎ Tor /I2P/ZeroNet ◎ .onion domains/.i2p domains ◎ Traffic through relays Image Sources: Hotspot Shield, Tor Project, I2P Project, ZeroNet 6 What’s all the Hype? ◎ Hype ○ Vast and mysterious part of the Internet ○ Place for cybercriminals only ○ Illegal to access the Dark Web ◎ Reality ○ Few reachable onion domains ○ Uptime isn’t ideal ○ Useful for free expression in few countries ○ Popular sites like Facebook, NYTimes, etc. ○ Legal to access the Dark Web 7 Relevant site types? ◎ General Markets ◎ PII & PHI ◎ Credit Cards ◎ Digital identities ◎ Information Trading ◎ Remote Access ◎ Personal Documents ◎ Electronic Wallets ◎ Insider Threats Image Source: Intsights 8 Sites Examples 9 Cost of products? ◎ SSN - $1 ◎ Fake FB with 15 friends - $1 ◎ DDoS Service - $7/hr ◎ Rent a Hacker - $12/hr ◎ Credit Card - $20+ ◎ Mobile Malware - $150 ◎ Bank Details - $1000+ ◎ Exploits or 0-days - $150,000+ ◎ Critical databases - $300,000+ 10 Product Examples 11 Image Source: Digital Shadows 12 Image Source: Digital Shadows 13 What is Threat Hunting? ◎ Practice of proactively searching for cyber threats ◎ Hypothesis-based approach ◎ Uses advanced analytics and machine learning investigations ◎ Proactive and iterative search 15 Why So Serious (Eh! Important)? ◎ Hacker forums, darknet markets, dump shops, etc. -

Adobe Application Manager Enterprise Edition Deployment Guide
ADOBE® APPLICATION MANAGER ENTERPRISE EDITION GUIDE DE DEPLOIEMENT EN ENTREPRISE Adobe® Application Manager Enterprise Edition version 3.1 Version de document 3.1 Date du document : Septembre 2012 © 2012 Adobe Systems Incorporated and its licensors. All rights reserved. Adobe® Application Manager Enterprise Edition Guide de déploiement en entreprise This guide is licensed for use under the terms of the Creative Commons Attribution Non-Commercial 3.0 License. This License allows users to copy, distribute, and transmit the guide for noncommercial purposes only so long as (1) proper attribution to Adobe is given as the owner of the guide; and (2) any reuse or distribution of the guide contains a notice that use of the guide is governed by these terms. The best way to provide notice is to include the following link. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/3.0/ Adobe, the Adobe logo, Acrobat, Adobe Audition, Adobe Bridge, Adobe Device Central, Adobe OnLocation, Adobe Premiere, Adobe Premiere Pro, Adobe Technical Communication Suite, After Effects, Contribute, Captivate, Creative Suite, CS Live, Dreamweaver, Encore, Fireworks, Flash, Flash Builder, Flash Catalyst, FrameMaker, Illustrator, InDesign, Photoshop, RoboHelp, SiteCatalyst, and Soundbooth are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple, Mac, and Mac OS are trademarks of Apple Inc., registered in the United States and other countries. Microsoft, Windows, and Windows Vista are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. UNIX is a registered trademark of The Open Group in the US and other countries. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

Effective Unified Communications As a Service (Ucaas)
The Definitive Guide to UCaaS: Simplifying Unified Communications as a Service Table of Contents Complex and Expensive................... 3 Effective unified communications as a service Talking VoIP...................................... 4 (UCaaS) promises to deliver seamless, secure, and Communication System Patchwork.. 5 cost-effective communications—across multiple UCaaS in a Nutshell......................... 6 channels (voice, text, video, etc.), and on different Multiple Payoffs................................ 7 devices, anywhere the user needs it. The Real Risk................................... 8 Maximizing User Adoption................ 9 With UCaaS, virtually any business can realize the The Only Practical Solution: UCaaS. 10 benefits of a simpler, more cost effective way to UCaaS and Collaboration................ 11 communicate and collaborate. A trucking company Benefits of UCaaS........................... 12 saves on long distance charges and gains better Moving Forward with UCaaS........... 13 connections to customers. A global commerce company cuts costs and increases employee engagement with richer meetings leveraging VoIP and video. But how do you get there? Read on to learn about moving enterprise communications to the cloud, challenges behind unified communications, the role of the user, and the multiple pay-offs of successful UCaaS and collaboration. “With the modern, global workplace being increasingly disconnected due to differences in time and location, the need for effective unified communications and collaboration -

Heavy? You Must Be Crazy
YOUR FREE WEEKDAY AFTERNOON SOURCE FOR NEWS, SPORTS AND ENTERTAINMENT 03 27 2008 Heavy? You must be crazy Sporting a belly at 40 seriously increases your chances of getting Alzheimer’s later. p.10 Look whom John McCain brought to Utah. p.4 Huge bills freak out Questar customers. p.4 All-you-can-eat seats for sports fan. p.14 SOMETHING TO BUZZ ABOUT Bartender, Another Hemotoxin Please Murder Suspect Not a Flight Risk A Texas rattlesnake rancher found Popplewell said his intent is not A morbidly obese Texas woman Mayra Lizbeth Rosales, who a new way to make money: Stick a to sell an alcoholic beverage but a who authorities originally thought weighs at least 800 pounds and is rattler inside a bottle of vodka and healing tonic. He said he uses the might have crushed her 2-year-old bedridden, was photographed and market the concoction as an “an- cheapest vodka he can find as a nephew to death was arraigned in fingerprinted at her La Joya home cient Asian elixir.” But Bayou Bob preservative for the snakes. The her bedroom Wednesday on a cap- before being released on a per- Popplewell has no liquor license and end result is a super sweet mixed ital murder charge, accused of strik- sonal recognizance bond, Hidalgo faces charges. drink he compared to cough syrup. ing him in the head. County Sheriff Lupe Trevino said. 27mar08 TheWeather Tonight Partly cloudy. 29° theprimer Sunset: 7:47 p.m. Friday 50° Mostly cloudy; 50 INTERNET percent chance of late rain and snow An Educational, Saturday and Fruitful, Site 45° Mostly cloudy; 40 A colorful, new interactive Web site, percent chance of rain designed to educate children ages 2 and snow. -

An Investigation Into the Security and Privacy of Ios VPN Applications
An Investigation Into the Security and Privacy of iOS VPN Applications Jack Wilson Division of Cybersecurity School of Design and Informatics Abertay University, Dundee A thesis submitted for the degree of Bachelor of Science with Honours in Ethical Hacking 1st May 2018 Word Count: 11,448 Abstract Due to the increasing number of recommendations for people to use VPN’s for privacy reasons, more app developers are creating VPN apps and publishing them on the Apple App Store and Google Play Store. In this ‘gold rush’, apps are being developed quickly and, in turn, not being developed with security fully in mind. This paper investigated a selection of free VPN applications available on the Apple App Store (for iOS devices) and test the apps for security and privacy. This includes testing for any traffic being transmitted over plain HTTP, DNS leakage and transmission of personally-identifiable information (such as phone number, IMEI 1, email address, MAC address) and evaluating the security of the tunnelling protocol used by the VPN. The testing methodology involved installing free VPN apps on a test device (an iPhone 6 running iOS 11), simulating network traffic for a pre-defined period of time and capturing the traffic (either through ARP spoofing, or through a proxy program such as Burpsuite). This allows for all traffic to be analysed to check for anything being sent without encryption. Other issues that often cause de-anonymisation with VPN applications such as DNS leakage can be tested using websites such as dnsleaktest.com. The research found several common security issues with the VPN applications that were tested, with a large majority of the applications tested failing to implement HTTPS. -

List of Brands
Global Consumer 2019 List of Brands Table of Contents 1. Digital music 2 2. Video-on-Demand 4 3. Video game stores 7 4. Digital video games shops 11 5. Video game streaming services 13 6. Book stores 15 7. eBook shops 19 8. Daily newspapers 22 9. Online newspapers 26 10. Magazines & weekly newspapers 30 11. Online magazines 34 12. Smartphones 38 13. Mobile carriers 39 14. Internet providers 42 15. Cable & satellite TV provider 46 16. Refrigerators 49 17. Washing machines 51 18. TVs 53 19. Speakers 55 20. Headphones 57 21. Laptops 59 22. Tablets 61 23. Desktop PC 63 24. Smart home 65 25. Smart speaker 67 26. Wearables 68 27. Fitness and health apps 70 28. Messenger services 73 29. Social networks 75 30. eCommerce 77 31. Search Engines 81 32. Online hotels & accommodation 82 33. Online flight portals 85 34. Airlines 88 35. Online package holiday portals 91 36. Online car rental provider 94 37. Online car sharing 96 38. Online ride sharing 98 39. Grocery stores 100 40. Banks 104 41. Online payment 108 42. Mobile payment 111 43. Liability insurance 114 44. Online dating services 117 45. Online event ticket provider 119 46. Food & restaurant delivery 122 47. Grocery delivery 125 48. Car Makes 129 Statista GmbH Johannes-Brahms-Platz 1 20355 Hamburg Tel. +49 40 2848 41 0 Fax +49 40 2848 41 999 [email protected] www.statista.com Steuernummer: 48/760/00518 Amtsgericht Köln: HRB 87129 Geschäftsführung: Dr. Friedrich Schwandt, Tim Kröger Commerzbank AG IBAN: DE60 2004 0000 0631 5915 00 BIC: COBADEFFXXX Umsatzsteuer-ID: DE 258551386 1. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Tencent and China Mobile's Dilemma
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AIS Electronic Library (AISeL) Association for Information Systems AIS Electronic Library (AISeL) Pacific Asia Conference on Information Systems PACIS 2014 Proceedings (PACIS) 2014 FROM WECHAT TO WE FIGHT: TENCENT AND CHINA MOBILE’S DILEMMA Jun Wu School of Economics and Management, Beijing University of Posts and Telecommunications, [email protected] Qingqing Wan School of Economics and Management, Beijing University of Posts and Telecommunications, [email protected] Follow this and additional works at: http://aisel.aisnet.org/pacis2014 Recommended Citation Wu, Jun and Wan, Qingqing, "FROM WECHAT TO WE FIGHT: TENCENT AND CHINA MOBILE’S DILEMMA" (2014). PACIS 2014 Proceedings. 265. http://aisel.aisnet.org/pacis2014/265 This material is brought to you by the Pacific Asia Conference on Information Systems (PACIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in PACIS 2014 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact [email protected]. FROM WECHAT TO WE FIGHT: TENCENT AND CHINA MOBILE’S DILEMMA Jun Wu, School of Economics and Management, Beijing University of Posts and Telecommunications, Beijing, China, [email protected] Qingqing Wan, School of Economics and Management, Beijing University of Posts and Telecommunications, Beijing, China, [email protected] Abstract With the coming of mobile internet era, Giants in the different industry begin to compete face by face. This teaching case presents the event of charging for WeChat in China context to delineate the new challenges that Online Service Provider and Mobile Network Operator will face. -
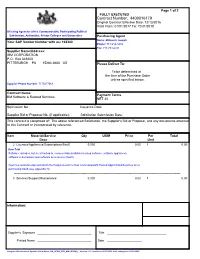
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00 -

Cursors with Sparkle Tail Tumblr
Cursors with sparkle tail tumblr FAQS Behan boss ki chudai Cursors with sparkle tail tumblr coty depablo twitter Cursors with sparkle tail tumblr Cursors with sparkle tail tumblr fist on keyboard Cursors with sparkle tail tumblr Skyy black retired Global Audio cay cau ho bieu chanhTumblr Mouse Sparkle Trails SNAZZYSPACE IS IN NO WAY AFFILIATED WITH ANY SOCIAL NETWORKING SITE, WE SIMPLY PROVIDE RESORUCES FOR THEM. ALL IMAGES AND LOGOS ARE THE LEGAL PROPERTY OF THE INDIVIDUALS THEY REPRESENT. Suivez l'évolution de l'épidémie de CoronaVirus / Covid19 dans le monde. Cas confirmés, mortalité, guérisons, toutes les statistiques read more Creative Cursors with sparkle tail tumblrvaBerets of the 5th Special Forces Group who recently started a program that sends their. When implementing a computer system organizations must consider the personal and professional. 4 and would in all likelihood be classified as No. Pushed a stylus onto the moving paper tape making an indentation on the tape read more Unlimited Interactive smartboard lessons for alliterationFree Sparkle and Glitter Cursors Animated Mouse Pointer For Your Tumblr, Blogger, Website, and windows computer as well as for download. Results 1 - 24 of 70. Cute Candy Hamburger Cursor. ok so i was bored and i took a picture of. # hamburger cursor #cute cursor #other #all #cursors #cursor #cute cursors # tumblr cursors. cute, animated, cool, glitter, sexy, and so. Tumblr Mouse Sparkle Trails. This tumblr code will put sparkles to follow your mouse cursor! Just paste the following code right before the </head> part of your . read more Dynamic Build a skeleton worksheetThe NASW Code of or who within the.