Enterprise Vault™ Compatibility Charts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Comprehensive Protection for Windows®
Solutions for Small and Mid-Sized Businesses October 2007 Product Comprehensive Catalog Protection for Windows® As companies increasingly rely on sophisticated technologies to support their objectives, the risks to business operations grow. The complexity of managing IT systems increases, as do the costs. And, if your company is like most, its IT staff and resources are limited and continually called on to justify their costs. Under these conditions, it’s difficult for companies to keep the Microsoft® Windows® environments they depend on to run their business secure, available, and well-managed. Symantec is uniquely qualified to address the challenge. That’s because Symantec delivers an unparalleled combination of leading technologies and services to help ensure the highest level of protection across your Microsoft Windows environment. Symantec offers comprehensive and affordable, best-in-class solutions that help protect Microsoft Windows environments by keeping data, systems, and applications secure, available, and well-managed at all times. Our world-class support programs and partners offer guidance to help you implement comprehensive solutions that will maximize your investment as they protect your IT environment. As you will see on the following pages, Symantec offers industry-leading solutions delivering enterprise-class performance without unnecessary cost or complexity. With a proven track record spanning several decades, Symantec knows how to help you keep your business up, running, and growing—no matter what happens. Symantec Product Catalog—October 2007 Comprehensive Protection for Windows® Contents Security . 2 Client, Server, and Network Security. 3 Symantec Endpoint Protection . 3 Symantec Network Access Control . 4 Symantec Multi-Tier Protection. 4 Symantec Mail Security for SMTP. -

Symantec Backup Exec™ 2012 Sales Script
Symantec Backup Exec™ 2012 Sales Script Partner Competitive Sales Script Product overview The Symantec Backup Exec™ 2012 product portfolio drives sales with a name customers know and trust plus new technology fit for both simple and complex IT environments. One integrated product protects virtual AND physical environments, simplifies both backup AND disaster recovery, and recovers data or systems at any scale, from an individual item to an entire server. New technologies include integrated disaster recovery, physical to virtual conversions and a renovated interface with default settings for the most common backup options. Available as packaged software, appliances, or cloud-based backup and recovery, Backup Exec is the one data protection choice for growing businesses and the partners that serve them. Why sell it? Selling Symantec Backup Exec 2012 product portfolio provides unlimited sales opportunities for you. • Attach with every new Windows® server, application, and VMware® or Hyper-V® virtual server sale to further build a complete and differentiating solution. • Quickly grow your deal size by adding Backup Exec Agents and Options. • Cross-sell other Symantec solutions, such as Symantec Enterprise Vault™, Symantec™ Endpoint Protection or Symantec™ ApplicationHA, for comprehensive protection. • Provide additional add-on installation service opportunities to further grow your margin. Key features of Backup Exec 2012 • Unite physical and virtual machine backups. Only Symantec Backup Exec™ with V-Ray technology offers flexible backup and recovery capabilities, deduplication, and policy management across VMware, Hyper-V and physical server environments. • New! One Product! Any Recovery! Complete data, application, and disaster recovery for physical and virtual environments from a single console. -

Veritas Backup Reporter Getting Started Guide Veritas Backup Reporter Getting Started Guide
Veritas Backup Reporter Getting Started Guide Veritas Backup Reporter Getting Started Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 6.0 PN: : (HRO7210)SKU 11132088 Legal Notice Copyright © 2006 Symantec Corporation. All rights reserved. Federal acquisitions: Commercial Software - Government Users Subject to Standard License Terms and Conditions. Actionable Infrastructure™, Active Extensions™, ActiveAdmin™, Anti-Freeze™, Application Saver™, Backup Exec™, Bare Metal Restore™, BindView™, Bloodhound™, Bootguard™, Brightmail™, bv-Admin™, bv-Control™, CarrierScan™, CleanSweep™, ColorScale™, CommandCentral™, Confidence Online™, CrashGuard™, Day-End Sync™, dbAnywhere™, DeepSight™, Defender™, Digital Immune System™, DiskDoubler™, DiskLock™, Drive Image™, Enterprise Security Manager™, Enterprise Vault™, FlashSnap™, FlowChaser™, Ghost Walker™, Ghost™, GoBack™, Healthy PC™, i3™, iCommand™, I-Gear™, Indepth™, Information Integrity™, Intellicrypt™, Intruder Alert™, LiveUpdate™, LiveState™, Mail-Gear™, ManHunt™, ManTrap™, MicroMeasure™, Mobile Update™, NetBackup™, NetProwler™, NetRecon™, Norton™, Norton 360™, Norton AntiSpam™, Norton AntiVirus™, Norton Commander™, Norton Editor™, Norton Guides™, Norton Internet Security™, Norton Mobile Essentials™, Norton Password Security™, Norton SystemWorks™, Norton Utilities™, Norton WinDoctor™, OmniGuard™, OpForce™, PartitionMagic™, pcAnywhere™, PowerQuest™, PowerVPN™, Procomm™, Procomm Plus™, -

Veritas Backup Reporter Administrator's Guide Veritas Backup Reporter Administrator's Guide
Veritas Backup Reporter Administrator's Guide Veritas Backup Reporter Administrator's Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 6.0 PN: : (HRO7210)SKU 11132088 Legal Notice Copyright © 2006 Symantec Corporation. All rights reserved. Federal acquisitions: Commercial Software - Government Users Subject to Standard License Terms and Conditions. Actionable Infrastructure™, Active Extensions™, ActiveAdmin™, Anti-Freeze™, Application Saver™, Backup Exec™, Bare Metal Restore™, BindView™, Bloodhound™, Bootguard™, Brightmail™, bv-Admin™, bv-Control™, CarrierScan™, CleanSweep™, ColorScale™, CommandCentral™, Confidence Online™, CrashGuard™, Day-End Sync™, dbAnywhere™, DeepSight™, Defender™, Digital Immune System™, DiskDoubler™, DiskLock™, Drive Image™, Enterprise Security Manager™, Enterprise Vault™, FlashSnap™, FlowChaser™, Ghost Walker™, Ghost™, GoBack™, Healthy PC™, i3™, iCommand™, I-Gear™, Indepth™, Information Integrity™, Intellicrypt™, Intruder Alert™, LiveUpdate™, LiveState™, Mail-Gear™, ManHunt™, ManTrap™, MicroMeasure™, Mobile Update™, NetBackup™, NetProwler™, NetRecon™, Norton™, Norton 360™, Norton AntiSpam™, Norton AntiVirus™, Norton Commander™, Norton Editor™, Norton Guides™, Norton Internet Security™, Norton Mobile Essentials™, Norton Password Security™, Norton SystemWorks™, Norton Utilities™, Norton WinDoctor™, OmniGuard™, OpForce™, PartitionMagic™, pcAnywhere™, PowerQuest™, PowerVPN™, Procomm™, Procomm Plus™, -
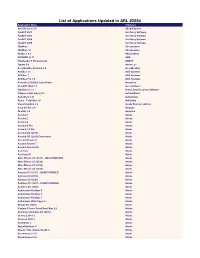
List of Applications Updated in ARL #2554
List of Applications Updated in ARL #2554 Application Name Publisher SyncBackLite 8.6 2BrightSparks TaxACT 2001 2nd Story Software TaxACT 2003 2nd Story Software TaxACT 2004 2nd Story Software TaxACT 2005 2nd Story Software 3DxWare 3Dconnexion 3DxWare 10 3Dconnexion HotDocs 6.3 AbacusNext PROMOD IV 11 ABB FineReader 6 Professional ABBYY Typora 0.9 Abner Lee AccuWeather Desktop 1.8 AccuWeather ACDSee 3.1 ACD Systems ACDSee 7 ACD Systems ACDSee Pro 7.0 ACD Systems Acoustica CD/DVD Label Maker Acoustica CutePDF Writer 3 Acro Software ISO Burner 1.1 Active Data Recovery Software FlySpeed SQL Query 3.3 ActiveDBSoft ActivePerl 5.16 ActiveState Rome - Total War 1.0 Activision Visual Lighting 2.4 Acuity Brands Lighting Easy-CD Pro 2.0 Adaptec OneSite 5.6 Adaptiva Acrobat 1 Adobe Acrobat 2 Adobe Acrobat 4 Adobe Acrobat 6 Pro Adobe Acrobat 7.0 Pro Adobe Acrobat DC (2019) Adobe Acrobat DC (2020) Continuous Adobe Acrobat Reader 6 Adobe Acrobat Reader 7 Adobe Acrobat Reader DC Adobe AcroTray Adobe AcroTray XI Adobe After Effects CC (2015) - UNAUTHORIZED Adobe After Effects CC (2018) Adobe After Effects CC (2019) Adobe After Effects CC (2020) Adobe Animate CC (2017) - UNAUTHORIZED Adobe Animate CC (2019) Adobe Animate CC (2020) Adobe Audition CC (2015) - UNAUTHORIZED Adobe Audition CC (2020) Adobe Authorware Runtime 4 Adobe Authorware Runtime 5 Adobe Authorware Runtime 7 Adobe Authorware Web Player 6 Adobe Bridge CC (2020) Adobe Capture Classic FormFlow Filler 2.2 Adobe Character Animator CC (2020) Adobe Connect 2019.3 Adobe Connect 2020.1 Adobe Contribute -

Veritas Backup Reporter Installation Guide Veritas Backup Reporter Installation Guide
Veritas Backup Reporter Installation Guide Veritas Backup Reporter Installation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 6.2 PN: : (HRO7210)SKU 11132088 Legal Notice Copyright © 2007 Symantec Corporation. All rights reserved. Federal acquisitions: Commercial Software - Government Users Subject to Standard License Terms and Conditions. Actionable Infrastructure™, Active Extensions™, ActiveAdmin™, Anti-Freeze™, Application Saver™, Backup Exec™, Bare Metal Restore™, BindView™, Bloodhound™, Bootguard™, Brightmail™, bv-Admin™, bv-Control™, CarrierScan™, CleanSweep™, ColorScale™, CommandCentral™, Confidence Online™, CrashGuard™, Day-End Sync™, dbAnywhere™, DeepSight™, Defender™, Digital Immune System™, DiskDoubler™, DiskLock™, Drive Image™, Enterprise Security Manager™, Enterprise Vault™, FlashSnap™, FlowChaser™, Ghost Walker™, Ghost™, GoBack™, Healthy PC™, i3™, iCommand™, I-Gear™, Indepth™, Information Integrity™, Intellicrypt™, Intruder Alert™, LiveUpdate™, LiveState™, Mail-Gear™, ManHunt™, ManTrap™, MicroMeasure™, Mobile Update™, NetBackup™, NetProwler™, NetRecon™, Norton™, Norton 360™, Norton AntiSpam™, Norton AntiVirus™, Norton Commander™, Norton Editor™, Norton Guides™, Norton Internet Security™, Norton Mobile Essentials™, Norton Password Security™, Norton SystemWorks™, Norton Utilities™, Norton WinDoctor™, OmniGuard™, OpForce™, PartitionMagic™, pcAnywhere™, PowerQuest™, PowerVPN™, Procomm™, Procomm Plus™, PureDisk™, -
Symantec Enterprise Vault with Netapp Storage Systems
Deployment Guide: Symantec Enterprise Vault with NetApp Storage Systems Gangoor Sridhara, NetApp TR-3500 Abstract As the volume of e-mail and other unstructured data skyrockets, it has become increasingly clear that today’s enterprises need a structured approach to archival. The combination of Symantec Enterprise Vault with NetApp storage systems provides enterprises the capability to archive and protect both business-critical e-mail and unstructured file system data in a simple to manage unified storage environment. This technical report discusses in detail the procedures required to complete the installation of Symantec Enterprise Vault in a NetApp unified storage environment. Table of Contents 1. Introduction .............................................................................................................................. 4 1.1. Background on Technical Issues................................................................................................................. 4 1.2. Purpose and Scope ..................................................................................................................................... 5 2. Infrastructure................................................................................................................................................... 5 2.1. Infrastructure-Related Tasks ....................................................................................................................... 6 2.1.1. SnapDrive Software Installation .............................................................................................................. -

Symantec Enterprise Vault™: Administrator's Guide
Symantec Enterprise Vault™ Administrator's Guide 10.0 Symantec Enterprise Vault: Administrator's Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Last updated: 2013-06-14. Legal Notice Copyright © 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Enterprise Vault, Compliance Accelerator, and Discovery Accelerator are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This Symantec product may contain third party software for which Symantec is required to provide attribution to the third party (“Third Party Programs”). Some of the Third Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Please see the Third Party Software file accompanying this Symantec product for more information on the Third Party Programs. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. -

Deployment Guide for VERITAS Enterprise Vault from Symantec: Netapp Storage Solution Tech Marketing | TR-3382
TECHNICAL REPORT Deployment Guide for VERITAS Enterprise Vault from Symantec: NetApp Storage Solution Tech Marketing | TR-3382 TECHNICAL REPORT strategies. management advanced storage solutions andglobal data complextechnical challenges with organizations understand and meet leader indata storage technology,helps industry and a pioneer Appliance, Network Abstract In the age of information, e-mail has become the mode of communication in the business community. Attachments to e-mail have served a business solution in the communication process, and it is now a norm in the day-to-day business process. The increased acceptance of communication systems has led to documents and messages being stored electronically. Once the information is stored electronically, need for an efficient method of storing, archiving, and managing it is a challenge. In addition to e-mail archival, file system archival offers a new feature to archive needed files and save storage space. Symantec has a compelling product to meet these challenges and increase the customer experience. This paper describes the method to integrate VERITAS Enterprise Vault, from Symantec with Network Appliance™ storage configuration to take advantage of file system archival as well as the backup, recovery, and compliance solutions from Network Appliance. 1 TECHNICAL REPORT Table of Contents 1 Executive Summary 3 2 Background 3 3 Introduction 3 3.1 VERITAS E-mail Archival 4 3.2 VERITAS File System Archival 6 3.2.1 Network Appliance Solution 7 3.2.2 Network Connectivity 8 3.2.3 Microsoft System -

Symantec Enterprise Product Catalog October 2005
Symantec Enterprise Product Catalog October 2005 Symantec has developed a new approach to IT management that simultaneously provides for the security and the availability of network resources. Known as I n formation Integ r i ty™, this balanced approach ke e ps information safe, yet accessible wherever, whenever, and to whomever business needs dictate. It’s an approach designed to help keep businesses up, running, and growing, no matter what happens. On the following pages, you will find a complete range of world-class enterprise security and ava i l a b i l i t y solutions, including products for p reventing intrusions, detecting and removing malicious code, managing enterprise-wide security systems, p r e s e rving business continuity, and much more. In short, just about everything you need to ensure the integrity of information assets in your enterprise environment. Symantec Enterprise Solutions—October 2005 Symantec Enterprise Product Catalog Contents Appliances . .5 Symantec Clientless VPN Gateway 4400 Series . .5 Symantec Gateway Security 300 Series . .5 Symantec Gateway Security 400 Series . .6 Symantec Gateway Security 5400 Series . .6 Symantec Gateway Security 5600 Series . .7 Symantec Mail Security 8100 Series . .7 Symantec Mail Security 8200 Series . .8 Symantec Network Security 7100 Series . .8 Application Performance Management . .9 VERITAS Application Saver . .9 VERITAS i3 for ClarifyCRM . .9 VERITAS i3 for J2EE . .10 VERITAS i3 for .Net . .10 VERITAS i3 for Oracle . .10 VERITAS i3 for Oracle Applications . .11 VERITAS i3 for PeopleSoft . .11 VERITAS i3 for SAP . .11 VERITAS i3 for Siebel . .12 VERITAS i3 for SQL Server . .12 VERITAS i3 for Web Servers . -

List of Versions Added in ARL #2586
List of versions added in ARL #2586 Publisher Product Version /n software NetCmdlets 2016 1099 Pro 1099 Pro 2008 1099 Pro 1099 Pro 2009 1099 Pro 1099 Pro 2020 1E 1E Client 5.1 2BrightSparks SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2nd Story Software TaxACT 2002 3CX Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3M Grouper Plus System 2021 3S-Smart Software Solutions CoDeSys OPC Server 3.1 4D 4D 15.0 4Team Duplicate Killer 3.4 508 Software Disk Drill 4.1 A!K Research Labs NotesHolder 2.3 AB Sciex MetabolitePilot 2.0 AB Sciex LibraryView 1.0 Abacre Advanced Find and Replace 5.2 ACA Systems Color Picker 2.0 AccessData Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 6.3 AccessData Forensic Toolkit 7.0 AccuSoft Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft PrizmDoc Server 12.3 AccuSoft PrizmDoc Server 13.1 AccuSoft ImagXpress 13.6 ACD Systems ACDSee 2.2 ACD Systems ACDSync 1.1 Acelogix Software Ace Utilities 6.3 Acronis True Image for Crucial 23. Acrosync Acrosync 1.6 Actian Zen Client 5.10 Actipro Software Windows Forms Controls 16.1 ActiveDocs Opus Composition Server 7.0 ActiveXperts Network Component 4.6 Actual Tools Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Acucorp ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acute Systems TransMac 12.1 Add-in Express Merge Cells Wizard for Microsoft Excel 2.2 Add-in Express Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Adersoft -
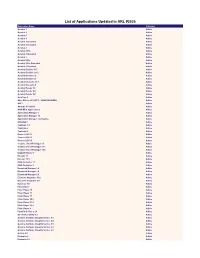
List of Applications Updated in ARL #2535
List of Applications Updated in ARL #2535 Application Name Publisher Acrobat 1 Adobe Acrobat 2 Adobe Acrobat 3 Adobe Acrobat 4 Adobe Acrobat 4 Standard Adobe Acrobat 5 Standard Adobe Acrobat 8 Adobe Acrobat 8 Pro Adobe Acrobat 8 Standard Adobe Acrobat 9 Adobe Acrobat 9 Pro Adobe Acrobat 9 Pro Extended Adobe Acrobat 9 Standard Adobe Acrobat Distiller 15.7 Adobe Acrobat Distiller 19.12 Adobe Acrobat Distiller 6.0 Adobe Acrobat Distiller 9.5 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 9 Adobe Acrobat Reader 19 Adobe Acrobat Reader 5.0 Adobe Acrobat Reader DC Adobe AcroTray 9 Adobe After Effects CC (2017) - UNAUTHORIZED Adobe AIR 3 Adobe Animate CC (2019) Adobe AOM MFC Application 2 Adobe Application Manager 1 Adobe Application Manager 10 Adobe Application Manager 2 Enterprise Adobe Autoplay 6 Adobe Captivate 1.0 Adobe Captivate 2 Adobe Captivate 5 Adobe Connect 2019.1 Adobe Connect 2019.3 Adobe Connect 2019.5 Adobe Creative Cloud Packager 1.1 Adobe Creative Cloud Packager 1.12 Adobe Creative Cloud Packager 1.15 Adobe Digital Editions 9 Adobe Director 11 Adobe Director 11.5 Adobe DNG Converter 11 Adobe DNG Converter 9 Adobe Download Manager 1.0 Adobe Download Manager 1.5 Adobe Download Manager 2.0 Adobe Elements Organizer 15.0 Adobe Elements Organizer 8.0 Adobe Extractor 1.0 Adobe Fireworks 8 Adobe Flash Player 10 Adobe Flash Player 11 Adobe Flash Player 17 Adobe Flash Player 30.0 Adobe Flash Player 31.0 Adobe Flash Player 32.0 Adobe Flash Player 9 Adobe FormFlow Filler 2.24 Adobe GC Invoker Utility 6.3 Adobe Genuine Software Integrity