Veritas Backup Reporter Administrator's Guide Veritas Backup Reporter Administrator's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cluster Server Installation Guide
Veritas™ Cluster Server Installation Guide Solaris 5.0 N18534F Veritas Cluster Server Installation Guide Copyright © 2006 Symantec Corporation. All rights reserved. Veritas Cluster Server 5.0 Symantec, the Symantec logo, Veritas are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THIS DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID, SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be “commercial computer software” and “commercial computer software documentation” as defined in FAR Sections 12.212 and DFARS Section 227.7202. Symantec Corporation 20330 Stevens Creek Blvd. Cupertino, CA 95014 www.symantec.com Third-party legal notices Third-party software may be recommended, distributed, embedded, or bundled with this Symantec product. Such third-party software is licensed separately by its copyright holder. All third-party copyrights associated with this product are listed in the accompanying release notes. -

Comprehensive Protection for Windows®
Solutions for Small and Mid-Sized Businesses October 2007 Product Comprehensive Catalog Protection for Windows® As companies increasingly rely on sophisticated technologies to support their objectives, the risks to business operations grow. The complexity of managing IT systems increases, as do the costs. And, if your company is like most, its IT staff and resources are limited and continually called on to justify their costs. Under these conditions, it’s difficult for companies to keep the Microsoft® Windows® environments they depend on to run their business secure, available, and well-managed. Symantec is uniquely qualified to address the challenge. That’s because Symantec delivers an unparalleled combination of leading technologies and services to help ensure the highest level of protection across your Microsoft Windows environment. Symantec offers comprehensive and affordable, best-in-class solutions that help protect Microsoft Windows environments by keeping data, systems, and applications secure, available, and well-managed at all times. Our world-class support programs and partners offer guidance to help you implement comprehensive solutions that will maximize your investment as they protect your IT environment. As you will see on the following pages, Symantec offers industry-leading solutions delivering enterprise-class performance without unnecessary cost or complexity. With a proven track record spanning several decades, Symantec knows how to help you keep your business up, running, and growing—no matter what happens. Symantec Product Catalog—October 2007 Comprehensive Protection for Windows® Contents Security . 2 Client, Server, and Network Security. 3 Symantec Endpoint Protection . 3 Symantec Network Access Control . 4 Symantec Multi-Tier Protection. 4 Symantec Mail Security for SMTP. -

Veritas Backup Reporter 6.5 Installation Guide Veritas Backup Reporter Installation Guide
Veritas Backup Reporter 6.5 Installation Guide Veritas Backup Reporter Installation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 6.5 PN: : (HRO7210)SKU 11132088 Legal Notice Copyright © 2008 Symantec Corporation. All rights reserved. Federal acquisitions: Commercial Software - Government Users Subject to Standard License Terms and Conditions. Actionable Infrastructure™, Active Extensions™, ActiveAdmin™, Anti-Freeze™, Application Saver™, Backup Exec™, Bare Metal Restore™, BindView™, Bloodhound™, Bootguard™, Brightmail™, bv-Admin™, bv-Control™, CarrierScan™, CleanSweep™, ColorScale™, CommandCentral™, Confidence Online™, CrashGuard™, Day-End Sync™, dbAnywhere™, DeepSight™, Defender™, Digital Immune System™, DiskDoubler™, DiskLock™, Drive Image™, Enterprise Security Manager™, Enterprise Vault™, FlashSnap™, FlowChaser™, Ghost Walker™, Ghost™, GoBack™, Healthy PC™, i3™, iCommand™, I-Gear™, Indepth™, Information Integrity™, Intellicrypt™, Intruder Alert™, LiveUpdate™, LiveState™, Mail-Gear™, ManHunt™, ManTrap™, MicroMeasure™, Mobile Update™, NetBackup™, NetProwler™, NetRecon™, Norton™, Norton 360™, Norton AntiSpam™, Norton AntiVirus™, Norton Commander™, Norton Editor™, Norton Guides™, Norton Internet Security™, Norton Mobile Essentials™, Norton Password Security™, Norton SystemWorks™, Norton Utilities™, Norton WinDoctor™, OmniGuard™, OpForce™, PartitionMagic™, pcAnywhere™, PowerQuest™, PowerVPN™, Procomm™, Procomm Plus™, -

293202846.Pdf
ÚÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄ¿ ³ ## ## ## ## ### ######## ######## ########³ ³ ## ## ## ## ## ## ## ## ## ## ## ³ ³######### ## ## ## ## ## ## ## ## ## ³ ³ ## ## ## ## ## ## ## ######## ###### ## ³ ³######### ## ## ## ######### ## ## ## ## ³ ³ ## ## ## ## ## ## ## ## ## ## ## ³ ³ ## ## ### ### ## ## ## ## ######## ########³ ³ ³ ÃÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÁÄÄÄÄÄÄÄÄÄÁÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄ´ ³ This site list brought to you by all of us in ³ ³ the best warez channel on FDFnet, #Warez. ³ ³ ÚÄÄÄÄÄÄÄÄÄÄÄÄ¿ ³ ÃÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄ´irc.fdfnet.netÃÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄ´ ³ ÀÄÄÄÄÄÄÄÄÄÄÄÄÙ ³ ³ Dont be a leech. Contribute! ³ ³ To add a site /msg Balthor SITE xxx.xxx.xxx.xxx /dirs L: & P: ³ ³ For posting you will be +ved until your site is removed. ³ ³ Please only post VERIFIED sites ³ ÃÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÂÄÄÄÄÂÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄ´ ³ . .. .:ÃNewS´: .. ³ ³ ÀÄÄÄÄÙ ³ ³ 02-15-2002 ³ ³ ³ ³ At long last the OOmpah forums are back! Go ahead, post ³ ³ something at http://oompah.tk/ ³ ³ ³ ³ The list that you are currently viewing is a 6 hour time ³ ³ delayed version of our complete list. Site posters receive ³ ³ access to the complete list which contains ALL of the sites. ³ ³ Upon verifcation of your site post, you will gain access to ³ ³ the current list, access to our !search, and you will also ³ ³ see new sites immediately after they are verified (6 hours ³ ³ before everybody else!). ³ ³ ³ ÃÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÂÄÄÄÄÂÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄÄ´ ³ . .. .: Other Info : .. ³ ³ ³ ³ PSST! -

VERITAS Cluster Server 4.0 Installation Guide for Linux
VERITAS Cluster Server 4.0 Installation Guide Linux N10923H August 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. VERITAS Legal Notice Copyright © 1998-2004 VERITAS Software Corporation. All rights reserved. VERITAS, the VERITAS logo, VERITAS Cluster Server, and all other VERITAS product names and slogans are trademarks or registered trademarks of VERITAS Software Corporation. VERITAS and the VERITAS logo, Reg. U.S. Pat. & Tm. Off. Other product names and/or slogans mentioned herein may be trademarks or registered trademarks of their respective companies. VERITAS Software Corporation 350 Ellis Street Mountain View, CA 94043 USA Phone 650–527–8000 Fax 650–527–2908 www.veritas.com Third-Party Copyrights Apache License Version 2.0, January 2004 http://www.apache.org/licenses/ TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION 1. Definitions. “License” shall mean the terms and conditions for use, reproduction, and distribution as defined by Sections 1 through 9 of this document. “Licensor” shall mean the copyright owner or entity authorized by the copyright owner that is granting the License. “Legal Entity” shall mean the union of the acting entity and all other entities that control, are controlled by, or are under common control with that entity. -

Symantec™ Cluster Server 6.2.1 Installation Guide - Linux
Symantec™ Cluster Server 6.2.1 Installation Guide - Linux Platform Release OL7 UEK R3 April 2015 Symantec™ Cluster Server Installation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Product version: 6.2.1 Document version: 6.2.1 Rev 0 Legal Notice Copyright © 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Veritas, Veritas Storage Foundation, CommandCentral, NetBackup, Enterprise Vault, and LiveUpdate are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in Commercial Computer Software or Commercial Computer Software Documentation", as applicable, and any successor regulations, whether delivered by Symantec as on premises or hosted services. -

Symantec Backup Exec™ 2012 Sales Script
Symantec Backup Exec™ 2012 Sales Script Partner Competitive Sales Script Product overview The Symantec Backup Exec™ 2012 product portfolio drives sales with a name customers know and trust plus new technology fit for both simple and complex IT environments. One integrated product protects virtual AND physical environments, simplifies both backup AND disaster recovery, and recovers data or systems at any scale, from an individual item to an entire server. New technologies include integrated disaster recovery, physical to virtual conversions and a renovated interface with default settings for the most common backup options. Available as packaged software, appliances, or cloud-based backup and recovery, Backup Exec is the one data protection choice for growing businesses and the partners that serve them. Why sell it? Selling Symantec Backup Exec 2012 product portfolio provides unlimited sales opportunities for you. • Attach with every new Windows® server, application, and VMware® or Hyper-V® virtual server sale to further build a complete and differentiating solution. • Quickly grow your deal size by adding Backup Exec Agents and Options. • Cross-sell other Symantec solutions, such as Symantec Enterprise Vault™, Symantec™ Endpoint Protection or Symantec™ ApplicationHA, for comprehensive protection. • Provide additional add-on installation service opportunities to further grow your margin. Key features of Backup Exec 2012 • Unite physical and virtual machine backups. Only Symantec Backup Exec™ with V-Ray technology offers flexible backup and recovery capabilities, deduplication, and policy management across VMware, Hyper-V and physical server environments. • New! One Product! Any Recovery! Complete data, application, and disaster recovery for physical and virtual environments from a single console. -

Publisher's Version/PDF (3.676Mb)
III Public Access Com puter Software · Management · BV RICHARD \NAVNE 24 JUNE 2004 ' COMPUTERS IN LIBRARIES feature: PAC management tools ost libraries now recog nize that public access computers are essential M to providing excellent service to patrons. Managing these computers has become a major re sponsibility for library staffs. Patrons expect to find secure and well-main tained computers that have simple, stable, and predictable interfaces. In my capacity as assistant director for Information Systems at The Uni versity of Texas Southwestern Medical Center at Dallas (UT Southwestern) Library, I have grappled with public access computer issues for years. Ten years ago there were few software tools available; however, today there are many easy-to-use and cost-effective al ternatives to help manage public ac cess computers. Tools to Help Manage PACs I'm about to describe a representa tive sample of software tools in several important categories. This article does or not attempt to address all programs in Tools all software management categories • because there are too many products to do that. I'll discuss specific products LI rarl from specific vendors, but won't rec ommend any. You should do further re search and make a purchase decision appropriate to your environment. Most of the software discussed in this arti cle is available for testing prior to pur chase. Some of the programs are free. The categories of management soft ware that I will address are setup soft ware, security programs, integrity main Today, there are many tenance software, browser control tools, antivirus software, anti-spyware soft easy-to-use and cost-effective ware, patch management tools, session managers, print management systems, system utilities, and some Microsoft tools to help manage software options. -
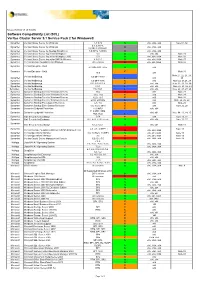
Wxrt VCS for Windows 5.1 SCL Based GA Version
Release Revision 1.6 25 Oct 2012 Software Compatibility List (SCL) Veritas Cluster Server 5.1 Service Pack 2 for Windows® Symantec Veritas Cluster Server for Windows 5.1 SP2 S x86, IA64, x64 Note 01, 02 5.1, 5.1AP1, Symantec Veritas Cluster Server for Windows U x86, IA64, x64 5.1SP1,5.1SP1AP1 Symantec Veritas Cluster Server for NetApp SnapMirror 5.0 RP1a, 5.0RP2 U x86, IA64, x64 Symantec Veritas Cluster Server Agent for Websphere 5.1 S x86, x64 Note 05 Symantec Veritas Cluster Server Agent for Websphere MQ 5.0 S x86, x64, IA64 Note 06 Symantec Veritas Cluster Server Agent for SAP NetWeaver 4.3.01.0 S x86, x64, IA64 Note 07 Symantec Veritas Storage Foundation for Windows All versions X x86, x64, IA64 Note 02 Symantec Veritas Enterprise Vault 8.0 SP1-SP5, 9.0.x S x86 Symantec Veritas Enterprise Vault C Note 31 10.0 x86 Note 21, 22, 23, 28, Veritas NetBackup 6.0 MP1-MP3 Symantec L x86 29 Symantec Veritas NetBackup 6.0 MP4-MP6 C x86 Note 22, 23,28, 29 Symantec Veritas NetBackup 6.5, 6.5.2-6.5.4 C x86, x64 Note 22, 23, 28, 29 Symantec Veritas NetBackup 6.5.1 L x86, x64 Note 22, 23, 28, 29 Symantec Veritas NetBackup 7.0, 7.0.1 L x86, x64 Note 22, 23, 27, 28 Symantec Symantec Backup Exec for Windows Servers 10.x X x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 11.0, 11d C x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 12.0, 12.5 C x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 2010, 2010 R2 L x86 Note 24, 25, 28 Symantec Symantec Backup Exec System Recovery 6.5, 7.0 C x86 Note 28 Symantec Symantec -

Cluster Server 5.0 MP2 Release Notes
Veritas™ Cluster Server Release Notes HP-UX 5.0 Maintenance Pack 2 Veritas Cluster Server Release Notes The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Product version: 5.0 MP2 Document version: 5.0MP2.0 Legal Notice Copyright © 2009 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, Storage Foundation and Veritas are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This Symantec product may contain third party software for which Symantec is required to provide attribution to the third party (“Third Party Programs”). Some of the Third Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Please see the Third Party Legal Notice Appendix to this Documentation or TPIP ReadMe File accompanying this Symantec product for more information on the Third Party Programs. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. -
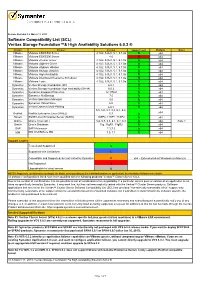
Wxrt VCS for Windows 5.1 SCL Based GA Version
Release Revision 1.6 March 11, 2013 Software Compatibility List (SCL) Veritas Storage Foundation™& High Availability Solutions 6.0.2 ® Vendor Product Version Support Level Platform Notes VMware VMware ESX/ESXi Server 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware ESX/ESXi Server 4.0 X x64 VMware VMware vCenter server 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware vSphere Client 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware vSphere vMotion 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware Storage vMotion 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware High Availability 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware Distributed Resource Scheduler 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 VMware VMware Tools 4.1U2, 5.0U1, 5.1, 5.1.0a S x64 Symantec Veritas Storage Foundation (SF) 6.0.1 S x64 Symantec Veritas Storage Foundation High Availability (SFHA) 6.0.2 S x64 Symantec Symantec Endpoint Protection 12.1 RU2 S x64 Symantec Symantec NetBackup 7.5 S x64 Symantec Veritas Operations Manager 5.0 S x64 Symantec Symantec Virtual Store 6.0 S x64 Symantec Veritas Dynamic Multi-Pathing 6.0.1 S x64 5.5, 5.6, 5.7, 5,8, 6,1, 6.2, x64 RedHat RedHat Enterprise Linux (RHEL) 6.3 S Novell SUSE Linux Enterprise Server (SLES) 10SP4, 11SP1, 11SP2 S x64 Oracle Oracle Linux (OL) 5.6, 5.7, 5.8, 6.1, 6.2, 6.3 S x64 Note 1 Oracle Oracle Database 11g, 11gR1, 11gR2 S x64 SAP SAP Netweaver 7.1,7.3 S x64 IBM IBM WebSphere MQ 7.0, 7.1 S x64 Support Legend Tested and Supported S Supported with Limitations L Compatible and Supported, but not tested by Symantec C x64 = Extended 64-bit Windows architecture Not Supported X Upgradeable to latest version U NOTES: Support is conditional according to the Notes corresponding to the individual platform or application. -
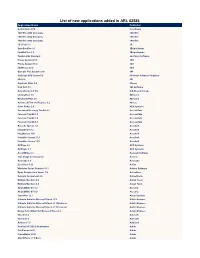
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express