How Unique Is Your Web Browser?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dynamic and Interactive R Graphics for the Web: the Gridsvg Package
JSS Journal of Statistical Software MMMMMM YYYY, Volume VV, Issue II. http://www.jstatsoft.org/ Dynamic and Interactive R Graphics for the Web: The gridSVG Package Paul Murrell Simon Potter The Unversity of Auckland The Unversity of Auckland Abstract This article describes the gridSVG package, which provides functions to convert grid- based R graphics to an SVG format. The package also provides a function to associate hyperlinks with components of a plot, a function to animate components of a plot, a function to associate any SVG attribute with a component of a plot, and a function to add JavaScript code to a plot. The last two of these provides a basis for adding interactivity to the SVG version of the plot. Together these tools provide a way to generate dynamic and interactive R graphics for use in web pages. Keywords: world-wide web, graphics, R, SVG. 1. Introduction Interactive and dynamic plots within web pages are becomingly increasingly popular, as part of a general trend towards making data sets more open and accessible on the web, for example, GapMinder (Rosling 2008) and ManyEyes (Viegas, Wattenberg, van Ham, Kriss, and McKeon 2007). The R language and environment for statistical computing and graphics (R Development Core Team 2011) has many facilities for producing plots, and it can produce graphics formats that are suitable for including in web pages, but the core graphics facilities in R are largely focused on static plots. This article describes an R extension package, gridSVG, that is designed to embellish and transform a standard, static R plot and turn it into a dynamic and interactive plot that can be embedded in a web page. -

CSS Contenu / Mise En Forme 3 Séparer Contenu, Site Mise En Forme, Web Document Object Et Actions
Langages du Web 1 Langages du Web CSS Contenu / Mise en forme 3 Séparer contenu, Site mise en forme, Web Document Object et actions. DOM Model Cascading Style JS JavaScript Sheet CSS HyperText Markup Language HTML francois.piat@univ‐fcomte.fr CSS Cascading Style Sheet 4 Feuille de style en cascade : séparer contenu et forme. Pas d'attributs de mise en forme dans le code HTML CSS ≠ HTML. Un "mécanisme" avec sa propre syntaxe Contrôle précis de la mise en page et de la mise en forme Code HTML plus simple et plus court CCS 1 : décembre 1996 Propriétés de mise en forme et de rendu typographique CSS 2 : mai 1998 70 nouvelles propriétés (ex : positionnement à l'écran) Cascade : plusieurs de feuilles de styles mises en oeuvre CSS 2.1 : septembre 2009 ‐ Recommandation : 7 juin 2011 Supprime des parties de CSS 2 / corrections suivant les implémentations CSS 3 : en développement http://www.w3.org/Style/CSS/current‐work#roadmap francois.piat@univ‐fcomte.fr 2 Langages du Web CSS Contenu / Mise en forme 5 1994 1997 1999 2005 Maintenant JS JS HTML HTML CSS JS CSS HTML HTML JS HTML HTML "The Web technology stack is a complete mess." Ian Hickson – 08/01/2013 - http://html5doctor.com/interview-with-ian-hickson-html-editor/ francois.piat@univ‐fcomte.fr CSS Code CSS 6 h1 { background: url(images/trait.png) no‐repeat; color: #be7e11; font‐size: 28px; font‐weight: bold; width: 590px; } #bcContenu li .avatar { font: 16px/1.8 Arial, Verdana, sans‐serif; height: 50px; margin‐left: ‐60px; width: 50px; } francois.piat@univ‐fcomte.fr 3 Langages du -

The New Font Project: TEX Gyre
Hans Hagen, Jerzy Ludwichowski, Volker Schaa NAJAAR 2006 47 The New Font Project: TEX Gyre Abstract metric and encoding files for each font. We look for- In this short presentation, we will introduce a new ward to an extended TFM format which will lift this re- project: the “lm-ization” of the free fonts that come striction and, in conjunction with OpenType, simplify with T X distributions. We will discuss the project E delivery and usage of fonts in TEX. objectives, timeline and cross-lug funding aspects. We especially look forward to assistance from pdfTEX users, because the pdfTEX team is working on the implementation on the support for OpenType Introduction fonts. An important consideration from Hans Hagen: “In The New Font Project is a brainchild of Hans Ha- the end, even Ghostscript will benefit, so I can even gen, triggered mainly by the very good reception imagine those fonts ending up in the Ghostscript dis- of the Latin Modern (LM) font project by the TEX tribution.” community. After consulting other LUG leaders, The idea of preparing such font families was sug- Bogusław Jackowski and Janusz M. Nowacki, aka gested by the pdfTEX development team. Their pro- “GUST type.foundry”, were asked to formulate the pro- posal triggered a lively discussion by an informal ject. group of representatives of several TEX user groups — The next section contains its outline, as prepared notably Karl Berry (TUG), Hans Hagen (NTG), Jerzy by Bogusław Jackowski and Janusz M. Nowacki. The Ludwichowski (GUST), Volker RW Schaa (DANTE)— remaining sections were written by us. who suggested that we should approach this project as a research, technical and implementation team, and Project outline promised their help in taking care of promotion, integ- ration, supervising and financing. -
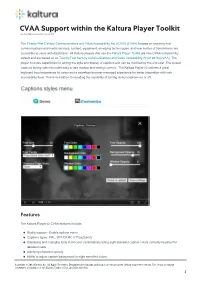
CVAA Support Within the Kaltura Player Toolkit Last Modified on 06/21/2020 4:25 Pm IDT
CVAA Support within the Kaltura Player Toolkit Last Modified on 06/21/2020 4:25 pm IDT The Twenty-First Century Communications and Video Accessibility Act of 2010 (CVAA) focuses on ensuring that communications and media services, content, equipment, emerging technologies, and new modes of transmission are accessible to users with disabilities. All Kaltura players that use the Kaltura Player Toolkit are now CVAA compliant by default and are based on on Twenty-First Century Communications and Video Accessibility Act of 2010 (CVAA). The player includes capabilities for editing the style and display of captions and can be modified by the end user. The closed captions styling editor includes easy to use markup and testing controls. The Kaltura Player v2 delivers a great keyboard input experience for users and a seamless browser-managed experience for better integration with web accessibility tools. This is in addition to including the capability of turning closed captions on or off. Features The Kaltura Player v2 CVAA features include: Studio support - Enable options menu Captions types: XML, SRT/DFXP, VTT(outband) Displaying and changing fonts in 64 color combinations using eight standard caption colors currently required for television sets. Adjusting character opacity Ability to adjust caption background in eight specified colors. Copyright ©️ 2019 Kaltura Inc. All Rights Reserved. Designated trademarks and brands are the property of their respective owners. Use of this document constitutes acceptance of the Kaltura Terms of Use and Privacy Policy. 1 Ability to adjust character edge (i.e., non, raised, depressed, uniform or drop shadow). Ability to adjust caption window color and opacity. -

OMEGA CS Fonts
OMEGA CS Fonts A ACADEMY ENGRAVED ACCT AK REV C American Uncial Inl Accolade Bold American Uncial Shadow Accolade Light AMERICANA BOLD ACCT.AK.REV.C Accolade Light Ita Americana URW T Bol Accolade Med Americana URW T Reg Alcuin Caps URW T Bol Americana URW T Reg Ita Alcuin Caps URW T Lig Americana URW T Xtr Bol Alcuin Caps URW T Reg ANN. GROTESQUE ACCT.A.K.REV.C Alcuin Caps URW T Xtr Bol ANTIQUE OLIVE BOLD ACCT AK REV E Alcuin Discaps URW D Bol ANTIQUE OLIVE MED ACCT AK REV C Alcuin URW T Bol Antique Olive Nord Reg Ita Alcuin URW T Lig ARNOLD BOCKLIN ACCT.A.K.REV.D Alcuin URW T Reg Arnold Boecklin D Alcuin URW T Xtr Bol Arnold Boecklin Initials D Alternate Gothic No1 D Arnold Boecklin No2 Alternate Gothic No2 D Arnold Boecklin Outl Alternate Gothic No3 D ATH.SCRIPT CONN.ACCT.A.K.REV.D American Uncial D AVANT EXTRA BOLD ACCT. AK. REV G American Uncial Initials D AVANT GARDE ACCT. A.K. REV.K B BABYTEETH ACCT.AK REV B Baskerville T Bol Balloon Caps D Xtr Bol Baskerville T Med Balloon D Xtr Bol Baskerville T Med Ita Balloon Drop Shadow D Baskerville T Reg Balloon Outl P Xtr Bol Baskerville T Reg Ita Balloon P Xtr Bol Baskerville URW Bol Balloon URW Bold Baskerville URW BolNar Balloon URW Light Baskerville URW BolNarObl BASKERVILLE ACCT AK REV B Baskerville URW BolObl Baskerville AI Ad Weight Baskerville URW BolWid Baskerville AI Heavy Weight Baskerville URW BolWidObl Baskerville AI Over Weight Baskerville URW BolXtrNar BASKERVILLE BOLD ACCT.A.K.REV.F Baskerville URW BolXtrNarObl Baskerville Handcut Bold Baskerville URW BolXtrWid Baskerville -

Issue Table of Contents 2006, Number 1
The PracTeX Journal - TeX Users Group Journal home page General information Submit an item Download style files Copyright Contact us Issue Table of Contents 2006, Number 1 [Published 2006-02-18] Notices From the Editor: In this issue: Fonts Lance Carnes [whole issue page number 3] Feedback From Readers [6] Invitation to PracTeX'06 Robin Laakso [8] PracTeX Journal 2006-1 Whole Issue PDF The Editors Articles Typographic Opportunities Tamye Riggs [11] Font selection in LaTeX The most frequently asked questions Walter Schmidt [17] Mac OS X Fonts in pdfTeX Gerben C. Th. Wierda, Thomas A. Schmitz and Adam T. Lindsay [24] The MathTimeProfessional Fonts Or, How I Wasted the Last Twenty Years of my Life Mike Spivak [42] An exploration of the Latin Modern fonts Will Robertson [45] Chinese TeX: Using the CJK LaTeX Package, Unicode TrueType Fonts and PDFTeX under Windows Helmer Aslaksen [57] http://dw.tug.org/pracjourn/2006-1/wholeissue/toc.html (1 of 2)3/5/2006 7:24:41 AM The PracTeX Journal - TeX Users Group A Survey of Free Math Fonts for TeX and LaTeX Stephen Hartke [62] Columns Travels in TeX Land: Using the Lucida fonts David Walden [89] Ask Nelly: Which fonts can be accessed from the TeX Live distribution just using usepackage? What is the difference between Fonts and Typefaces? Which are the best fonts for typesetting math? The Editors [103] Distractions: Name-that-Font The Editors [106] http://dw.tug.org/pracjourn/2006-1/wholeissue/toc.html (2 of 2)3/5/2006 7:24:41 AM The PracTeX Journal - TeX Users Group Journal home page General information Submit an item Download style files Copyright Contact us From the Editor: In this issue: Fonts Lance Carnes G Comment on this paper G Send submission idea to editor In this issue: Fonts Next Issue Thanks Issue 2006-1 is the first issue of the PracTeX Journal's second year. -

Font List for the Cisco Edge 340 Series, Release 1.1
Font List for the Cisco Edge 340 Series, Release 1.1 First Published: August 4, 2014 This document describes the default fonts of the Cisco Edge 340 Series, Release 1.1. Font List The following fonts are supported on the Cisco Edge 340 Series, Release 1.1: • Umpush:style=Oblique • Utopia:style=Bold Italic • Nimbus Sans L:style=Regular Italic • URW Palladio L:style=Roman • Century Schoolbook L:style=Bold Italic • DejaVu Sans,DejaVu Sans Condensed:style=Condensed Oblique,Oblique • Norasi:style=Oblique • TlwgTypewriter:style=Oblique • TlwgMono:style=Medium • Tlwg Typo:style=Medium • Nimbus Sans L:style=Bold • Norasi:style=BoldOblique • Utopia:style=Bold • Tlwg Typo:style=BoldOblique • Purisa:style=BoldOblique • URW Chancery L:style=Medium Italic • Bitstream Charter:style=Bold Italic • DejaVu Sans:style=Bold Oblique Cisco Systems, Inc. www.cisco.com Font List • Nimbus Roman No9 L:style=Regular • Loma:style=Oblique • Century Schoolbook L:style=Bold • Century Schoolbook L:style=Italic • Norasi:style=BoldItalic • Nimbus Sans L:style=Regular • URW Palladio L:style=Italic • Cursor:style=Regular • Garuda:style=Oblique • Nimbus Sans L:style=Bold Condensed • TlwgTypewriter:style=Medium • URW Gothic L:style=Demi • Nimbus Roman No9 L:style=Medium Italic • Bitstream Charter:style=Regular • Purisa:style=Bold • Garuda:style=BoldOblique • Nimbus Mono L:style=Bold Oblique • Kinnari:style=Medium • Norasi:style=Italic • Dingbats:style=Regular • TlwgMono:style=Bold • Loma:style=BoldOblique • Waree:style=Oblique • Nimbus Roman No9 L:style=Medium • Nimbus Sans -

The Matplotlib User's Guide
The Matplotlib User’s Guide John Hunter August 10, 2006 2 Contents 1 Introduction 5 1.1 Migrating from matlab .......................................... 6 1.2 Numerix .................................................. 8 1.2.1 Choosing Numeric, numarray, or NumPy ............................ 8 1.3 Backends ................................................. 9 1.4 Integrated development environments .................................. 9 1.5 Interactive ................................................. 10 1.6 Customization using matplotlibrc ................................... 11 1.6.1 RC file format .......................................... 11 1.6.2 Which rc file is used? ....................................... 12 1.7 Installing ................................................. 12 1.7.1 Compiling matplotlib ....................................... 12 1.7.2 Installing on windows ...................................... 13 1.7.3 Package managers: (rpms, apt, fink) ............................... 13 1.7.4 Getting feedback from matplotlib ................................ 14 2 The pylab interface 15 2.1 Simple plots ................................................ 15 2.2 More on plot ............................................... 16 2.2.1 Multiple lines ........................................... 16 2.2.2 Controlling line properties .................................... 17 2.3 Color arguments .............................................. 20 2.4 Loading and saving data ......................................... 21 2.4.1 Loading and saving ASCII data ................................ -

Data Becker Font Forgery "Christian Becker" 1234567890$&? ABCDEFGHI J KLM NOPQ RSTUVWXYZ Abcdefghi J Klm Nopqr S Tuvwxyz
DATA BECKERs Goldene Serie Das große Schriftenpaket 2.500 Data Becker Golden Series: The Big Font Collection 2500 Fonts In the report "The Funny Font Forging Industry" designed for prosecutors and criminal court judges, I described, how Bruno Steinert forged the "Akzidenz-Grotesk" by the "Linotype Method". This "Linotype Method" was also applied in the case of the Data Becker Font CD containing 2500 fonts which were forged such that the original font names or font trademarks of all the 2500 fonts were entirely erased and replaced by forged font names (e.g. "Peter Becker" as forged name instead of the true name or trademark "Futura". See the file DBPER.TTF on the Data Becker Font CD). The Data Becker CD declares "© 2004 Data Becker GmbH", but the file dates of the fonts are 1999-2000. The following list is sorted by the "sources" contained in the "copyright notices" of the 2500 forged fonts. It is interesting that Data Becker quotes in the CD booklet the "Will Software GmbH" as the font source, although this company is never mentioned in any of the 2500 "copyright notices", so that it is very likely that the "copyright notices" have been forged too. But I have no time to analyse all 2500 forged fonts. This is the job of font forging experts at criminal courts. The Data Becker CD contains a manual as PDF file ("Handbuch.pdf"). But Data Becker was of opinion that none of the 2500 forged fonts was suitable for typesetting the manual, and hence none of the forged fonts was used by Data Becker in the "Handbuch.pdf". -

Číslo 1–4/2016
CS G TU Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravoda j Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživat el˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskˇ ého sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpra vodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení u živatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskosloˇ venského sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdruž ení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceˇ skoslovenského sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚u TEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravoda j Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživat el˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskˇ ého sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpra vodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení u živatel˚uTEXu Zpravodaj Ceskoslovenskéhoˇ sdružení uživatel˚uTEXu Zpravodaj Ceskosloˇ venského sdružení -
Die Texnische K Om Ödie
DANTE Deutschsprachige Anwendervereinigung TEX e.V. 18. Jahrgang Heft 4/2006 November 2006 Xnische Komödie E Die T 4/2006 Impressum »Die TEXnische Komödie« ist die Mitgliedszeitschrift von DANTE e.V. Der Bezugs- preis ist im Mitgliedsbeitrag enthalten. Namentlich gekennzeichnete Beiträge geben die Meinung der Schreibenden wieder. Reproduktion oder Nutzung der erschiene- nen Beiträge durch konventionelle, elektronische oder beliebige andere Verfahren ist nur im nicht-kommerziellen Rahmen gestattet. Verwendungen in größerem Umfang bitte zur Information bei DANTE e.V. melden. Beiträge sollten in Standard-LATEX-Quellcode unter Verwendung der Dokumenten- klasse dtk erstellt und per E-Mail oder Datenträger an untenstehende Adresse der Redaktion geschickt werden. Sind spezielle Makros, LATEX-Pakete oder Schriften dafür nötig, so müssen auch diese komplett mitgeliefert werden. Außerdem müssen sie auf Anfrage Interessierten zugänglich gemacht werden. Diese Ausgabe wurde mit Hilfe folgender Programme erstellt: pdfeTeXk, Version 3.141592-1.30.4-2.2 (Web2C 7.5.5). Als Standard-Schriften kamen die Type-1- Fonts Latin-Modern und LuxiMono zum Einsatz. Erscheinungsweise: vierteljährlich Erscheinungsort: Heidelberg Auflage: 2700 Herausgeber: DANTE, Deutschsprachige Anwendervereinigung TEX e.V. Postfach 10 18 40 69008 Heidelberg E-Mail: [email protected] [email protected] (Redaktion) Druck: Konrad Triltsch Print und digitale Medien GmbH Johannes-Gutenberg-Str. 1–3, 97199 Ochsenfurt-Hohe Stadt Redaktion: Herbert Voß (verantwortlicher Redakteur) Rudolf Herrmann Sven Naumann Volker RW Schaa Mitarbeit : Lutz Ihlenburg Rolf Niepraschk Martin Schröder Gert Ingold Bernd Raichle Redaktionsschluss für Heft 1/2007: 15. Januar 2007 ISSN 1434-5897 Die TEXnische Komödie 4/2006 Editorial Liebe Leserinnen und Leser, in dieser Ausgabe finden Sie den Tagungsbericht von der letzten Mitglieder- versammlung in Rosenheim, an der leider nicht sehr viele Mitglieder teilge- nommen haben. -

Font Test. Fe Fi Fo Fum, I Smell the Blood of an English Man. Foddle This Or That
FONT NAME Small Sample Text Actionis Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. AD Mono Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Allegro Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Amelia Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Font Test. fe fi fo fum, I smell the blood of an English man. Andale Mono Foddle this or that. Arial Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Font Test. fe fi fo fum, I smell the blood of an English man. Foddle Arial Black this or that. Asia Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Font Test. fe fi fo fum, I smell the blood of an English man. Bank Gothic Foddle this or that. Font Test. fe fi fo fum, I smell the blood of an English man. Bazaronite Foddle this or that. Bernhard Bold Cond Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Bernhard Fashion Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that. Bernhard Modern Font Test. fe fi fo fum, I smell the blood of an English man. Foddle this or that.