The Ospp.Vbs Script
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tips for Receiving Email Yahoo! Mail Hotmail, Windows Live Or
Tips for receiving Email An email has been sent to [email address] containing instructions on how to confirm your registration or how to reset your password. To make sure you receive this email, please: 1. Check your spam filter 2. Add [email protected] to your address book or ‘safe’ list. 3. Read the instructions below for your email provider. Yahoo! Mail There are two options to help ensure you receive our emails. • Bulk or Spam mail folder (does not guarantee delivery, but will help) 1. Check your Yahoo! Bulk mail or Spam folder 2. Click on the email from International Scholarship and Tuition Services and click the button marked ‘not Spam’. 3. The email will move to your inbox. • Create a mail filter (almost guarantees delivery) 1. Click on ‘Options’ in the top right. 2. Choose ‘Mail Options’ 3. Locate and choose ‘Filters’ 4. Click ‘Add’ 5. Name the filter ‘ISTS’ 6. Beside ‘From header’, select ‘contains’ and type International Scholarship and Tuition Services, Inc. 7. Beside ‘Move the message to’, select Inbox Hotmail, Windows Live or MSN There are two options to help ensure you receive our emails. • Junk Folder 1. In the left hand menu, select ‘Junk’ 2. Select the email from International Scholarship and Tuition Services, Inc. 3. Inside the email message, there will be an exclamation mark and a message saying ‘You may not know this sender.’ 4. Beside this, click the link ‘Mark as safe.’ 5. The email will move into your inbox. • Add ISTS to your ‘Safe List’ 1. In the top right corner, Click ‘Options’ 2. -

Tadiran-Coral-Voicemail-User-Guide-Steadfasttelecom.Com .Pdf
Coral Message Center (CMC) User Guide Version 2.1 for Windows The flexible way to communicate . © 2002-2003 Active Voice LLC To access your mailbox from inside your organization All rights reserved. First edition 2003. 1. Call the voice messaging system. 1 for Yes, 2 for No, PhoneBASIC, Repartee, TeLANophy, 2. When the system greets you, enter: ViewCall, and ViewMail are trademarks of Active Voice, LLC. Personal ID ______________________________________________________ All other brands and product names used in this docu- ment are trademarks of their respective owners. Security code (if required) ___________________________________________ Licensed under one or more of the following patents: U.S. Nos. 4,994,926; 5,291,302; 5,459,584; 4,696,028; To access your mailbox by computer 4,809,321; 4,850,012; 4,922,526; 4,935,958; 4,955,047; 1. Launch Mailbox Manager. 4,972,469; 4,975,941; 5,020,095; 5,027,384; 5,029,196; 5,099,509; 5,109,405; 5,148,478; 5,166,974; 5,168,519; 2. When the system greets you, enter: 5,249,219; 5,303,298; 5,309,504; 5,347,574; 5,666,401; 5,181,243; 5,724,408; and Canadian No. 1329852. Host name_______________________________________________________ Extension _______________________________________________________ Security Code _____________________________________________________ For assistance, call: Name___________________________________________________________ Extension _______________________________________________________ Contents Introduction ii Changing your mailbox setup 21 Using quick message actions and shortcuts 47 Setting up your mailbox .......................................iv Working with the Mailbox Manager ....................22 Changing your security code..............................24 Quick message actions ...................................... 48 Checking and leaving messages 1 Changing your recorded and spelled names......25 Shortcuts........................................................... -

Onenote Collaboration
getCISSPcertfied.com XXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXX OneNote Your digital notebook Your World, organized Get organized in notebooks you can divide into sections and pages. With easy navigation and search, you’ll always find your notes right where you left them. Gather your thoughts… Quickly capture important information and ideas through images, videos, audio recordings, as well as ink and voice. …then make them even better Revise your notes with typed or handwritten text, and highlight and annotate what’s important. With OneNote on all your devices, you’ll never miss a flash of inspiration. Share and collaborate Great minds don’t always think alike, but they can share ideas and create together in OneNote. For more information, visit www.microsoft.com/onenote Conversational OneNote for Team Collaboration by Heather Severino © 2020 Conversational Geek Conversational OneNote for Team Collaboration Published by Conversational Geek® Inc. www.conversationalgeek.com All rights reserved. No part of this book shall be reproduced, stored in a retrieval system, or transmitted by any means, electronic, mechanical, photocopying, recording, or otherwise, without written permission from the publisher. No patent liability is assumed with respect to the use of the information contained herein. Although every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions. Nor is any liability assumed for damages resulting from the use of the information contained herein. Trademarks Conversational Geek, the Conversational Geek logo and J. the Geek are trademarks of Conversational Geek®. All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. -
Sharepoint Online
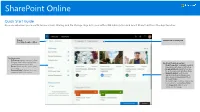
SharePoint Online Quick Start Guide Do more wherever you are with secure access, sharing, and file storage. Sign in to your Office 365 subscription and select SharePoint from the App launcher. Search Create a site or news post Find Sites, People, or Files. Find your sites • Following displays sites you follow, like your team's site or a site from Check out featured content another group you work with. • News from sites highlights updates • Recent shows any site you've gone from sites you follow or visit often. to recently. • Frequent sites shows sites you like • Featured links* displays sites your to go to and recent activity in them. company wants to showcase. • Suggested sites* (not shown) appear based on searches you've done and recommendations from Microsoft Graph. • Microsoft Graph must be enabled by your admin to see Featured links and Suggested sites on your SharePoint homepage. SharePoint Online Work with files Select a site from the SharePoint homepage or enter its URL into your browser. Then select Documents in the left navigation pane. Open Share Copy link Move to/Copy to Open and edit a file online Share files directly from Get a link to the selected file Move or copy to another or in a desktop app. SharePoint. Files are private to insert in an IM, email, or destination in your OneDrive until shared. site. or any SharePoint site. Details Pane Document See file information, recent View and work with the files activity, manage access stored on a SharePoint site. permissions, and edit file Download properties. Download a copy of a file to work offline that takes local device space. -

Consuming Office 365 REST API Paolo Pialorsi – [email protected] – Piasys.Com About Me
Consuming Office 365 REST API Paolo Pialorsi – [email protected] – PiaSys.com About me • Project Manager, Consultant, Trainer • About 50 Microsoft certification exams passed, including MC(S)M • MVP Office 365 • Focused on SharePoint since 2002 • Author of 10 books about XML, SOAP, .NET, LINQ, and SharePoint • Speaker at main IT conferences @PaoloPia - [email protected] - http://www.pialorsi.com/blog.aspx Introducing Office 365 REST API What are the Office 365 REST API? • Set of services with REST (REpresentational State Transfer) endpoints • Available services • Microsoft Exchange Online • Mail, Contacts, Calendars • Microsoft OneDrive for Business • My Files • Microsoft SharePoint Online • Sites • Microsoft Azure Active Directory • Authentication, Directory Graph The SharePoint client APIs _api Office 365 REST APIs How to consume the APIs? • Directly via REST endpoints • Indirectly via high-level client libraries • .NET client libraries • JavaScript client libraries • Open Source SDKs for iOS and Android • Supported platforms for .NET client libraries • .NET Windows Store Apps • Windows Forms Application • WPF Application • ASP.NET Web Forms/MVC • Xamarin Android and iOS Applications • Multi-device hybrid apps DEMO Playing with the APIs using Fiddler .NET Environment Configuration • Microsoft Visual Studio 2013 • Microsoft Office Developer Tools for Visual Studio 2013 • A Microsoft Office 365 tenant (can be a developer tenant) • Some NuGet packages • OWIN OpenId Connect • For ASP.NET only DEMO Preparing a development environment Understanding -

Operational and Administrative Guidance Microsoft Windows 10
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1803 General Purpose Operating System Protection Profile © 2018 Microsoft Confidential. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Getting Started with Exchange Unified Messaging
Getting Started with Exchange Unified Messaging Welcome to Exchange Unified Messaging. This system will replace MCC’s existing Audix voice mail system and provide additional functionality. Microsoft® Exchange Server is the engine that powers Outlook but it also provides new and convenient ways to access voice mail. Now your e‐mail and voice mail messages are placed into one mailbox that can be accessed through many different devices such as a telephone, mobile phone, or computer. 1 Table of Contents INTRODUCING UNIFIED MESSAGING VOICEMAIL ................................................................................................................... 3 TYPES OF VOICEMAIL BOXES ................................................................................................................................................... 4 Individual Voicemail Users ................................................................................................................................................. 4 Shared Departmental Voicemail Users ............................................................................................................................. 4 Departmental Voicemail Users .......................................................................................................................................... 4 HOW TO ACCESS YOUR VOICEMAIL ........................................................................................................................................ 5 First Time Set Up From A Phone ........................................................................................................................................... -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Getting Started with Windows Speech Recognition
Getting Started with Windows™ Speech Recognition (WSR) A. OVERVIEW After reading Part One, the first time user will dictate an E-mail or document quickly with high accuracy. The instructions allow you to create, dictate, and send an E-mail without touching the keyboard. The second part discusses steps to attain highest accuracy. The final part has suggestions for increasing productivity when using Windows™ Speech Recognition. II. PART ONE A. WHY USE SPEECH RECOGNITION? Most people will be able to dictate faster and more accurately than they type. My experience with Windows™ Speech Recognition is the ability to dictate over 80 words a minute with accuracy of about 99%. If you truly can type at 80 words a minute with accuracy approaching 99%, you do not need speech recognition. However, even a good keyboarder will benefit from reduced strain on the hands and arms by using Windows™ Speech Recognition. It takes time to become comfortable with dictation into a computer. There will be moments of frustration as you go through the learning curve. If you are impatient or are a perfectionist, DO NOT read on and do not use Windows™ Speech Recognition. If you have reasonable patience, you will learn to dictate accurately and comfortably. The best strategy is to keep things simple for first several days of using Windows™ Speech Recognition. When you are comfortable with the basics, move to part two of this document. B. THE MICROPHONE A good microphone makes dictation into a computer a pleasure instead of a battle. Good microphones reproduce your voice accurately and block out background noise that distorts the audio signal. -

IBM Connect:Direct for Microsoft Windows: Documentation Fixpack 1 (V6.1.0.1)
IBM Connect:Direct for Microsoft Windows 6.1 Documentation IBM This edition applies to Version 5 Release 3 of IBM® Connect:Direct and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 1993, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. Release Notes.......................................................................................1 Requirements...............................................................................................................................................1 Features and Enhancements....................................................................................................................... 2 Special Considerations................................................................................................................................ 3 Known Restrictions...................................................................................................................................... 4 Restrictions for Connect:Direct for Microsoft Windows........................................................................ 4 Restrictions for Related Software.......................................................................................................... 6 Installation Notes.........................................................................................................................................6 -

Resolving Issues with Forms
C1261587x.fm Page 265 Thursday, November 15, 2001 3:51 PM Resolving Issues with Forms In 1988, Alan Cooper demonstrated a prototype called Ruby to Bill Gates. Ruby provided a form designer that allowed you to drag and drop controls, then known as gizmos, to quickly and easily create composite forms—such as dialog boxes, entry forms, and report forms. Microsoft took Cooper’s Ruby product and combined it with Basic to create Microsoft Visual Basic 1. Microsoft has since shipped a version of Ruby with every version of Visual Basic, versions 1 through 6. With every version, that is, until Visual Basic .NET. Visual Basic .NET provides a new forms package called Windows Forms. Although the Windows Forms package was designed using the same basic prin- ciple as Ruby—it is a form designer that allows you to drag and drop controls and set properties—it was never meant to be an extension of, nor to be com- patible with, Ruby. Therefore, there are fundamental differences between the two forms packages that affect the way you create Visual Basic applications. This chapter focuses on some of the fundamental differences between the Ruby and Windows Forms packages. Specifically, it discusses issues that the Upgrade Wizard does not handle for you. Before we get into the differences, however, let’s look at what Windows Forms and Ruby have in common. Similarities in Form Structure When you create a new project in Visual Basic .NET, you will find yourself at home in the environment. The way you create and design forms is the same in Visual Basic .NET as it is in Visual Basic 6. -

ATTACKING RDP How to Eavesdrop on Poorly Secured RDP Connections
IT SECURITY KNOW-HOW Adrian Vollmer ATTACKING RDP How to Eavesdrop on Poorly Secured RDP Connections March 2017 © SySS GmbH, March 2017 Wohlboldstraße 8, 72072 Tübingen, Germany +49 (0)7071 - 40 78 56-0 [email protected] www.syss.de Vollmer | Attacking RDP 1 Introduction The Remote Desktop Protocol (RDP) is used by system administrators everyday to log onto remote Windows machines. Perhaps most commonly, it is used to perform administrative tasks on critical servers such as the domain controller with highly privileged accounts, whose credentials are transmitted via RDP. It is thus vital to use a secure RDP configuration. We at SySS regularly observe that due to misconfigurations, system administrators in an Active Directory environment are routinely presented with (and ignore) certificate warnings like this: Figure 1: An SSL certificate warning If warnings like these are a common occurrence in your environment, you will not be able to recognize a real man-in-the-middle (MitM) attack. This article was written to raise awareness of how important it is to take certificate warnings seriously and how to securely configure your Windows landscape. The intended audience is system administrators, penetration testers and security enthusiasts. While not necessary, it is recommended that you have a firm understanding of the following subjects: – Public key cryptography as well as symmetric cryptography (RSA and RC4) – SSL – x509 certificates – TCP 2 Vollmer | Attacking RDP – Python – Hexadecimal numbers and binary code We will demonstrate how a MitM can sniff your credentials if you aren’t careful. None of this is particularly new – it even has been done before, for example by Cain [2].