Getting Started with Windows Speech Recognition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bitlocker Encryption for USB Drives Bitlocker Is a Security Feature. the Purpose of Bitlocker Is to Encrypt Your Data
BitLocker Encryption for USB Drives BitLocker is a security feature. The purpose of BitLocker is to encrypt your data. This is extremely necessary for any data that is not to be shared with other persons. This will prevent anyone from being able to access your files. In order to have access to your files, you will need to provide a secure password. This password should be unique only to you. More information is provided below on how to make a unique password in step 2. During this process, step 3 offers the option to save a recovery key. The recovery key is 48 characters long and consist of numbers and letters. This key will be saved to Active Directory and allow the IS Department to access your USB/External drive should you forget your password. To get started I would recommend encrypting the USB/External drive BEFORE adding any files. Once the drive is encrypted and you enter your password it will function as any other USB/External drive. So you may add, edit, or delete your files as you normally would. If you have any trouble following this guide or have any questions please do not hesitate to contact the IS department. You will need a USB or External drive in order to successfully complete this process. Multiple ways to navigate to BitLocker: 1. Control Panel System & Security BitLocker Drive Encryption 2. Search bar type in “BitLocker” Manage BitLocker Steps to encrypt your USB drive: Step 1: Click “Turn on BitLocker” Step 2: Check the “Use a password to unlock the drive” and enter your password. -

Tips for Receiving Email Yahoo! Mail Hotmail, Windows Live Or
Tips for receiving Email An email has been sent to [email address] containing instructions on how to confirm your registration or how to reset your password. To make sure you receive this email, please: 1. Check your spam filter 2. Add [email protected] to your address book or ‘safe’ list. 3. Read the instructions below for your email provider. Yahoo! Mail There are two options to help ensure you receive our emails. • Bulk or Spam mail folder (does not guarantee delivery, but will help) 1. Check your Yahoo! Bulk mail or Spam folder 2. Click on the email from International Scholarship and Tuition Services and click the button marked ‘not Spam’. 3. The email will move to your inbox. • Create a mail filter (almost guarantees delivery) 1. Click on ‘Options’ in the top right. 2. Choose ‘Mail Options’ 3. Locate and choose ‘Filters’ 4. Click ‘Add’ 5. Name the filter ‘ISTS’ 6. Beside ‘From header’, select ‘contains’ and type International Scholarship and Tuition Services, Inc. 7. Beside ‘Move the message to’, select Inbox Hotmail, Windows Live or MSN There are two options to help ensure you receive our emails. • Junk Folder 1. In the left hand menu, select ‘Junk’ 2. Select the email from International Scholarship and Tuition Services, Inc. 3. Inside the email message, there will be an exclamation mark and a message saying ‘You may not know this sender.’ 4. Beside this, click the link ‘Mark as safe.’ 5. The email will move into your inbox. • Add ISTS to your ‘Safe List’ 1. In the top right corner, Click ‘Options’ 2. -

Chapter 2: Windows 7
Chapter 2: Windows 7 When you delete a file, a. A copy of the file will be sent to the desktop b. You send the file to the Recycle Bin. c. The file will not be affected. d. A copy of the file will be stored in your active folder. Which of the following statements is correct about arrange icon on desktop. a. Icons on desktop can be arranged by name. b. Icons on desktop can be arranged by type. c. Icons on desktop can be arranged by size. d. All of the above. Which of the following statements is correct about opening control panel. a. You can open control panel from windows explorer. b. You can open control panel from start menu. c. You can open control panel from my computer. d. All of the above. The documents that is located in start menu store. a. The last 15 files that you have open. b. The last 15 files that you have delete. c. The last 15 files that you have copy. d. None of the above. The desktop is: a. An example of a hardware device. b. A folder. c. A file d. A window. The Shutdown icon on start menu means: a. Close all windows. b. Close the current windows. c. Close your computer. d. None of the above. To open a minimized window, you can click on the:- a. window’s button on the body of the taskbar. b. maximized button on the title bar. c. restore button on the title bar. d. all of the above. -
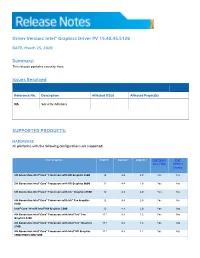
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Getting Started with Exchange Unified Messaging
Getting Started with Exchange Unified Messaging Welcome to Exchange Unified Messaging. This system will replace MCC’s existing Audix voice mail system and provide additional functionality. Microsoft® Exchange Server is the engine that powers Outlook but it also provides new and convenient ways to access voice mail. Now your e‐mail and voice mail messages are placed into one mailbox that can be accessed through many different devices such as a telephone, mobile phone, or computer. 1 Table of Contents INTRODUCING UNIFIED MESSAGING VOICEMAIL ................................................................................................................... 3 TYPES OF VOICEMAIL BOXES ................................................................................................................................................... 4 Individual Voicemail Users ................................................................................................................................................. 4 Shared Departmental Voicemail Users ............................................................................................................................. 4 Departmental Voicemail Users .......................................................................................................................................... 4 HOW TO ACCESS YOUR VOICEMAIL ........................................................................................................................................ 5 First Time Set Up From A Phone ........................................................................................................................................... -

Active@ NTFS Reader for DOS User Guide
Active Data Recovery Software Active@ NTFS Reader for DOS User Guide Version 1.0 Contents PRODUCT OVERVIEW SYSTEM REQUIREMENTS PRODUCT FEATURES OPERATING PROCEDURES 4.1 Bootable Floppy Disk (Startup Disk) Preparation..............................................................................4 4.2 Program Start and Information Display...............................................................................................5 4.3. Scan and Search for Files and Folders..................................................................................................5 4.4. Previewing Files.......................................................................................................................................6 4.5. Copying Files and Folders......................................................................................................................7 4.6. Using Disk Viewer ..................................................................................................................................8 4.7. Localized File Names Display ...............................................................................................................8 4.8. Long File Names Display.......................................................................................................................9 4.9. Command Line Parameters ...................................................................................................................9 1 PRODUCT OVERVIEW Active@ NTFS Reader is a compact and powerful DOS utility that -

How to Join a Skype Meeting Via E-Mail Invitation
HOW TO JOIN A SKYPE MEETING VIA E-MAIL INVITATION Important note before you start! It is best practice to install the Skype app before joining your first meeting. To do so please refer to the TC Toolbox note Install the Skype software for a Computer or Install the Skype app for an Apple or Android Mobile device. 1 Visit your inbox and open the 2 email invitation sent from the meeting host. While viewing the message, look for and click/tap on the hyperlink provided under Join Skype Meeting. [email protected] 3 On a computer, you may be promoted to open the Skype app, click Open Skype or Allow. Note On a mobile device, you may be prompted to select a browser to proceed. Tap on any button that says Open, then Join Conversation, then tap Open again. You’re all set. Time to learn how to use the Skype App! PAGE 1 of 2 Tools to help boost your digital literacy WWW.TECHCOACHES.CA Copyright © 2020 Tech Coaches Inc. 4 On a computer, if prompted, sign in with your existing Microsoft Account, or click Join as guest if you do not have a Microsoft account. 5 Set your microphone and video settings, by clicking the switches on/off. On a mobile device, if prompted tap Let’s go. Then, sign in with your existing Microsoft Account, or tap Join as guest if you do not have a Microsoft account. 6 Note Note: If a Join Meeting button is not Click/tap the green Join Meeting present but a Start Meeting button is button. -

How to Set up HP Lefthand Email Alerts Using Third Party Email
How to Set Up Email Relaying to Offsite Email Provider The approach found most effective for customers is to relay SMTP messages from the HP LeftHand nodes off of the management server which has a NIC on the SAN VLAN. Microsoft’s ISS is used to handle the SMTP relay. An email account is set up on a third party email server (Gmail, etc.) to prevent loss of alert communication if the internal server is part of the outage. This management server can be running the Centralized Management Console as well as the HealthCheck and Failover Manager utilities. Critical messages are sent to an externally controlled email account (Gmail, etc.) that can be monitored at all times by the system administrator. This is done via an email distribution list. Non-critical messages are sent to internal mailboxes. A diagram is included below. SMTP Server Setup (IIS 6.0) The Simple Mail Transfer Protocol (SMTP) service provided by IIS is a simple component for delivering outgoing e-mail messages. Delivery of a message is initiated by transferring the message to a designated SMTP server. Based on the domain name of the recipient e-mail address, the SMTP server initiates communications with a Domain Name System (DNS) server, which looks up and then returns the host name of the destination SMTP server for that domain. Next, the originating SMTP server communicates with the destination SMTP server directly through Transmission Control Protocol/Internet Protocol (TCP/IP) on port 25. If the user name of the recipient e-mail address matches one of the authorized user accounts on the destination server, the original e-mail message is transferred to that server, waiting for the recipient to pick up the message through a client program. -

E-Mailing a Large Amount of Recipients
E-mailing a large amount of recipients DO NOT use the “TO” or “CC” field! If you have a large list of recipients you need to send an email you, you should never try sending one large email with all of the recipients listed in the “TO” and/or “CC” field. First of all, the message will likely not be delivered to everyone. Even if the message makes it past our local header size limit, every mail server you are attempting to send it to has it’s own header size limit and can reject your message for exceeding this limit. There are other reasons you would not want to send it that way as well. For instance, by including everyone you are sending the message to, you are displaying that publicly to everyone on the list. Anyone who received the message can easy perform a reply-all and send an unwanted message to everyone. This usually begins when someone replies-all and says “Remove me from your list”. It won’t be long before you get someone emailing the entire list saying “You didn’t have to email that request to all of us”, etc... Basically, it could create a large amont of unwanted email for everyone involved. So what are your options? DO use the “BCC” field! The first option is to include your list of recipients in the BCC field. This prevents the header size from getting too large and also prevents people from purposely or accidentally replying-to-all. The problem with this method is the recipient does not see their email address in the TO header. -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users. -

CYBONET's Product Pineapp Mail Secure Is Fully Available For
CYBONET’s product PineApp Mail Secure is fully available for installation on Hyper-V platform. The following manual provides assistance in installing PineApp Mail Secure Virtual Machine on the Microsoft Hyper-V platform. Hyper V Quick Installation Guide Step 1: Installing PineApp Mail Secure over virtual machine. 1. Please choose New Virtual Hard Wizard and click on Next > button. 2. Under Choose Disk Format menu, please select VHDX option as mentioned below and click Next. 3. Under Choose Disk Type, please select Fixed Size and continue wizard. 4. Under Specify Name and Location, assign name for virtual disk and specify location. 5. Under Configure Disk, please specify disk size. For standalone unit is 300GB, for scanner unit in cluster enough – 120GB and click on Next > button. 6. Under Summary window, please verify your virtual machine description and click on Finish. 7. Continue with wizard, by clicking Next button. 8. Under Specify Name and Location menu, assign name for PineApp Mail Secure installation (for example – PineApp) and click on Next button. 9. Under Generation menu, please specify Generation 1 as mentioned on a screenshot below and click Next >. 10. Under Memory menu, assign RAM size. Minimum recommended value is – 4GB RAM (4096MB) 11. Under Networking menu, please choose network connection. 12. Under Virtual Hard Disk menu, please connect previously created virtual disk from instruction number 4 and click on Next. 13. Under Summary menu, please verify that virtual machine settings are to your expectations and click on Finish button. 14. Enter Settings of newly created machine, choose SCSI Controller and select DVD Drive and click on Add button.