Infantry Brigade Combat Team (IBCT) Mobility, Reconnaissance, and Firepower Programs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MILITARY VEHICLES MILITARY VEHICLES Aitegrn N Al Approach
anNTE I GRAL APPROACH MILITARY VEHICLES MILITARY VEHICLES AI N NTEGRal APPROACH A CASE IN POINT THE CV9035NL INFANTRY FIGHTING VEHICLE At TNO, we are well aware of the difficulties − Protection: mine protection qualification connected with the acquisition of advanced test for accurate assessment of the load military systems. By this we mean any on the human body in case of a mine system, like the next generation Infantry attack. Fighting Vehicles. For one thing, this will − Firepower: target definition, munitions require you to look ahead, sometimes for lethality analysis, munitions develop- the next three or more decades. Which is, ment, and firing doctrine determination TNO.NL of course, a complicated matter. TNO has in connection with the gun system At TNO Defence, Safety and A military vehicle is always a compromise. been acting as a strategic partner to the calibre. Security more than 1,000 scientific A few extra inches of armour will provide Netherlands MoD for many years now. This − Mobility: operational analysis of mobility TNO researchers, engineers, IT and more safety. But it also means more weight is one of the reasons why we are confident requirements to support tracked or TNO is an independent innovation organisa- and less mobility. The ideal military vehicle operations research specialists and that we will be able to help you solve any wheeled solutions. tion that connects people and knowledge should always be custom-made for its problem in connection with protection, − Command & Control: 10 years of in order to create the innovations that countless other experts daily work anticipated mission. -

16Th Infantry Division 47Th Field Artillery Camp Kearny, California Private John Leslie Banner
16th Infantry Division 47th Field Artillery Camp Kearny, California Private John Leslie Banner John Leslie Banner, a son of Samuel Banner and Ellen Radford Banner, was born on November 5, 1896 in Upton, Utah. He was the tenth of eleven children in the family of seven girls and four boys. He entered the army on September 3, 1918 and was assigned to Camp Kearny, California where he was training in the field artillery. While training, he became ill with influenza and developed pneumonia. The military contacted his Mother and she traveled to Camp Kearny to be at his side when he died. Just before he died, he told his mother, “Tell the folks not to feel bad. I am one out of thousands”. He died on December 6, 1918. A military funeral was held at Camp Kearny before his body was shipped home. Funeral services were held at the Coalville, Utah cemetery and he was buried there. At the time of his death, he was survived by his parents, four sisters and two brothers: Mary Ellen, Elizabeth Ann, Lydia, Cora Leone, Samuel, and William Henry. He was preceded in death by three sisters and one brother: Frances Alice, Lydia May, Mabel, and Benjamin. During World War I, the 16th Division was renamed the 37th Infantry Division. The formation of another division designated as the 16th Division occurred in 1918 and was stationed at Camp Kearny, California. It never went overseas and it was one of several divisions in WWI that did not select an insignia. The Army has not designated a new division as the 16th since it was demobilized in March 1919.. -

Decision-Making Process in Combat Operations
DECISION-MAKING PROCESS IN MILITARY COMBAT OPERATIONS 4120/002 10.2013 2000 10.2013 4120/002 International Committee of the Red Cross 19, avenue de la Paix 1202 Geneva, Switzerland T +41 22 734 60 01 F +41 22 733 20 57 E-mail: [email protected] www.icrc.org © ICRC, October 2013 DECISION-MAKING PROCESS IN MILITARY COMBAT OPERATIONS PREFACE Every state has an obligation to ensure respect for the law of armed conflict. The ICRC is mandated to support states in these efforts and does so through a range of activities, including promoting the integration of appropriate com- pliance measures into military doctrine, education, training and sanctions, with a view to ensuring that behaviours of those engaged in armed conflict comply with the law. The present note is designed to support the integration of the Law of Armed Conflict into military decision-making processes, primarily at the operational level. It is not based on any specific national doctrine. It is designed to support those responsible for developing national doctrine and operational planning procedures in their efforts to integrate the Law of Armed Conflict into military practice. The desired outcome is staff procedures which ensure the development of military plans and orders that accurately and effectively integrate compliance with the Law of Armed Conflict into operational practice, thereby reducing the effects of armed conflict on those who do not, or no longer, participate in the hostilities. The techniques of warfare change rapidly, particularly at times when combat operations are commonplace. The humanitarian impact of conflict is timeless. The Law of Armed Conflict is designed to limit the humanitarian consequences of war. -

Peacetime Espionage, International Law and the Existence of Customary Exceptions I˜Naki Navarrete† & Russell Buchan‡
\\jciprod01\productn\C\CIN\51-4\CIN403.txt unknown Seq: 1 8-APR-19 15:07 Out of the Legal Wilderness: Peacetime Espionage, International Law and the Existence of Customary Exceptions I˜naki Navarrete† & Russell Buchan‡ This Article demonstrates that peacetime espionage does not benefit from permissive customary international law exceptions. The mainstream view contends that, though peacetime espionage may contravene interna- tional law, developments in customary international law (CIL) nevertheless undercut State responsibility for such conduct. The gist of this view is that acts of espionage benefit from permissive CIL exceptions because its prac- tice is widespread and accepted within the international society. However, the mainstream literature has rarely— if ever— meaningfully engaged with the practice of espionage in an effort to tease out the objective and subjec- tive elements supportive of customary espionage exceptions. This Article closes this gap and debunks the mainstream view. We show that, although widespread, most acts of espionage are committed in secret and, as such, they cannot qualify as State practice for the purpose of CIL formation. We further demonstrate that States have failed to issue expressions of the sub- jective element in support of customary espionage exceptions. We con- clude by suggesting that, while States are entitled to develop customary espionage exceptions in the future, for now they have yet to come out of the legal wilderness. Introduction ..................................................... 898 R I. International Law and Peacetime Espionage............... 901 R A. Principle of Territorial Sovereignty ..................... 905 R B. Law of the Sea ........................................ 909 R C. Diplomatic and Consular Law ......................... 910 R II. Customary Exceptions and Peacetime Espionage ......... -

Synchronizing Airpower and Firepower in the Deep Battle
After you have read the research report, please give us your frank opinion on the contents. All comments—large or small, complimentary or caustic—will be gratefully appreciated. Mail them to CADRE/AR, Building 1400, 401 Chennault Circle, Maxwell AFB AL 36112-6428. Synchronizing Airpower and Laughbaum Firepower in the Deep Battle Thank you for your assistance COLLEGE OF AEROSPACE DOCTRINE, RESEARCH, AND EDUCATION AIR UNIVERSITY Synchronizing Airpower and Firepower in the Deep Battle R. KENT LAUGHBAUM Lt Col, USAF CADRE Paper Air University Press Maxwell Air Force Base, Alabama 36112-6610 January 1999 Disclaimer Opinions, conclusions, and recommendations expressed or implied within are solely those of the author, and do not necessarily represent the views of Air University, the United States Air Force, the Department of Defense, or any other US government agency. Cleared for public release: distribution unlimited. ii CADRE Papers CADRE Papers are occasional publications sponsored by the Airpower Research Institute of Air University’s College of Aerospace Doctrine, Research, and Education (CADRE). Dedicated to promoting understanding of air and space power theory and application, these studies are published by the Air University Press and broadly distributed to the US Air Force, the Department of Defense and other governmental organizations, leading scholars, selected institutions of higher learning, public policy institutes, and the media. All military members and civilian employees assigned to Air University are invited to contribute unclassified manuscripts. Manuscripts should deal with air and/or space power history, theory, doctrine or strategy, or with joint or combined service matters bearing on the application of air and/or space power. -
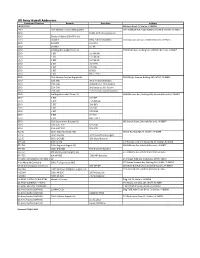
US Army Hawaii Addresses Command/Division Brigade Battalion Address 18 MEDCOM 160 Loop Road, Ft
US Army Hawaii Addresses Command/Division Brigade Battalion Address 18 MEDCOM 160 Loop Road, Ft. Shafter, HI 96858 25 ID 25th Infantry Division Headquarters 2091 Kolekole Ave, Building 3004, Schofield Barracks, HI 96857 25 ID (HQ) HHBN, 25th Infantry Division 25 ID Division Artillery (DIVARTY) HQ 25 ID DIVARTY HHB, 25th Field Artillery 1078 Waianae Avenue, Schofield Barracks, HI 96857 25 ID DIVARTY 2-11 FAR 25 ID DIVARTY 3-7 FA 25 ID 2nd Brigade Combat Team HQ 1578 Foote Ave, Building 500, Schofield Barracks, HI 96857 25 ID 2 BCT 1-14 IN BN 25 ID 2 BCT 1-21 IN BN 25 ID 2 BCT 1-27 IN BN 25 ID 2 BCT 2-14 CAV 25 ID 2 BCT 225 BSB 25 ID 2 BCT 65 BEB 25 ID 2 BCT HHC, 2 SBCT 25 ID 25th Combat Aviation Brigade HQ 1343 Wright Avenue, Building 100, WAAF, HI 96854 25 ID 25th CAB 209th Support Battalion 25 ID 25th CAB 2nd Battalion, 25th Aviation 25 ID 25th CAB 2ndRegiment Squadron, 6th Cavalry 25 ID 25th CAB 3-25Regiment General Support Aviation 25 ID 3rd Brigade Combat Team HQ Battalion 1640 Waianae Ave, Building 649, Schofield Barracks, HI 96857 25 ID 3 BCT 2-27 INF 25 ID 3 BCT 2-35 INF BN 25 ID 3 BCT 29th BEB 25 ID 3 BCT 325 BSB 25 ID 3 BCT 325 BSTB 25 ID 3 BCT 3-4 CAV 25 ID 3 BCT HHC, 3 BCT 25 ID 25th Sustainment Brigade HQ 181 Sutton Street, Schofield Barracks, HI 96857 25 ID 25th SUST BDE 524 CSSB 25 ID 25th SUST BDE 25th STB 311 SC 311th Signal Command HQ Wisser Rd, Bldg 520, Ft. -

The Utilization of Artillery and Mortars As Infantry Support Weapons in the Chaco War
Western Michigan University ScholarWorks at WMU Master's Theses Graduate College 6-1965 The Utilization of Artillery and Mortars as Infantry Support Weapons in the Chaco War Charles John Goodall Follow this and additional works at: https://scholarworks.wmich.edu/masters_theses Part of the Military, War, and Peace Commons Recommended Citation Goodall, Charles John, "The Utilization of Artillery and Mortars as Infantry Support Weapons in the Chaco War" (1965). Master's Theses. 3907. https://scholarworks.wmich.edu/masters_theses/3907 This Masters Thesis-Open Access is brought to you for free and open access by the Graduate College at ScholarWorks at WMU. It has been accepted for inclusion in Master's Theses by an authorized administrator of ScholarWorks at WMU. For more information, please contact [email protected]. THE UTILIZATION OF ARTILLERY AND MORTARS AS INFANTRY SUPPORT WEAPONS IN THE CHACO WAR by Charles John Goodall A thesis presented to the Faculty of the School of Graduate Studies in partial fulfillment of the Degree of Master of Arts Western Michigan University Kalamazoo, Michigan June, 1965 ACKNOWLEDGEMENTS The author wishes to express his appreciation for the co-operation of the following agencies and research facilities in gathering materials and providing technical advice in the production of this thesis: The University of Texas Library, Austin, Texas. The University of North Carolina Library, Chapel Hill, North Carolina. The University of Florida Library, Gainesville, Florida. Duke University Library, Durham, North Carolina. The University of California Library, Los Angeles, California The United States Army War College, Ft. Leavenworth, Kansas. The United States Army Ordnance School, Ft. -

MILITARY INTELLIGENCE PB 34-04-4 Volume 30 Number 4 October-December 2004 STAFF: FEATURES Commanding General Major General Barbara G
MILITARY INTELLIGENCE PB 34-04-4 Volume 30 Number 4 October-December 2004 STAFF: FEATURES Commanding General Major General Barbara G. Fast 8 Tactical Intelligence Shortcomings in Iraq: Restructuring Deputy Commanding General Battalion Intelligence to Win Brigadier General Brian A. Keller by Major Bill Benson and Captain Sean Nowlan Deputy Commandant for Futures Jerry V. Proctor Director of Training Development 16 Measuring Anti-U.S. Sentiment and Conducting Media and Support Analysis in The Republic of Korea (ROK) Colonel Eileen M. Ahearn by Major Daniel S. Burgess Deputy Director/Dean of Training Development and Support 24 Army’s MI School Faces TRADOC Accreditation Russell W. Watson, Ph.D. by John J. Craig Chief, Doctrine Division Stephen B. Leeder 25 USAIC&FH Observations, Insights, and Lessons Learned Managing Editor (OIL) Process Sterilla A. Smith by Dee K. Barnett, Command Sergeant Major (Retired) Editor Elizabeth A. McGovern 27 Brigade Combat Team (BCT) Intelligence Operations Design Director SSG Sharon K. Nieto by Michael A. Brake Associate Design Director and Administration 29 North Korean Special Operations Forces: 1996 Kangnung Specialist Angiene L. Myers Submarine Infiltration Cover Photographs: by Major Harry P. Dies, Jr. Courtesy of the U.S. Army Cover Design: 35 Deconstructing The Theory of 4th Generation Warfare Specialist Angiene L. Myers by Del Stewart, Chief Warrant Officer Three (Retired) Purpose: The U.S. Army Intelli- gence Center and Fort Huachuca (USAIC&FH) publishes the Military DEPARTMENTS Intelligence Professional Bulle- tin quarterly under provisions of AR 2 Always Out Front 58 Language Action 25-30. MIPB disseminates mate- rial designed to enhance individu- 3 CSM Forum 60 Professional Reader als’ knowledge of past, current, and emerging concepts, doctrine, materi- 4 Technical Perspective 62 MIPB 2004 Index al, training, and professional develop- ments in the MI Corps. -

2Nd INFANTRY REGIMENT
2nd INFANTRY REGIMENT 1110 pages (approximate) Boxes 1243-1244 The 2nd Infantry Regiment was a component part of the 5th Infantry Division. This Division was activated in 1939 but did not enter combat until it landed on Utah Beach, Normandy, three days after D-Day. For the remainder of the war in Europe the Division participated in numerous operations and engagements of the Normandy, Northern France, Rhineland, Ardennes-Alsace and Central Europe campaigns. The records of the 2nd Infantry Regiment consist mostly of after action reports and journals which provide detailed accounts of the operations of the Regiment from July 1944 to May 1945. The records also contain correspondence on the early history of the Regiment prior to World War II and to its training activities in the United States prior to entering combat. Of particular importance is a file on the work of the Regiment while serving on occupation duty in Iceland in 1942. CONTAINER LIST Box No. Folder Title 1243 2nd Infantry Regiment Unit Histories January 1943-June 1944 2nd Infantry Regiment Unit Histories, July-October 1944 2nd Infantry Regiment Histories, July 1944- December 1945 2nd Infantry Regiment After Action Reports, July-September 1944 2nd Infantry Regiment After Action Reports, October-December 1944 2nd Infantry Regiment After Action Reports, January-May 1945 2nd Infantry Regiment Casualty List, 1944-1945 2nd Infantry Regiment Unit Journal, 1945 2nd Infantry Regiment Narrative History, October 1944-May 1945 2nd Infantry Regiment History Correspondence, 1934-1936 2nd Infantry -

American War and Military Operations Casualties: Lists and Statistics
American War and Military Operations Casualties: Lists and Statistics Updated July 29, 2020 Congressional Research Service https://crsreports.congress.gov RL32492 American War and Military Operations Casualties: Lists and Statistics Summary This report provides U.S. war casualty statistics. It includes data tables containing the number of casualties among American military personnel who served in principal wars and combat operations from 1775 to the present. It also includes data on those wounded in action and information such as race and ethnicity, gender, branch of service, and cause of death. The tables are compiled from various Department of Defense (DOD) sources. Wars covered include the Revolutionary War, the War of 1812, the Mexican War, the Civil War, the Spanish-American War, World War I, World War II, the Korean War, the Vietnam Conflict, and the Persian Gulf War. Military operations covered include the Iranian Hostage Rescue Mission; Lebanon Peacekeeping; Urgent Fury in Grenada; Just Cause in Panama; Desert Shield and Desert Storm; Restore Hope in Somalia; Uphold Democracy in Haiti; Operation Enduring Freedom (OEF); Operation Iraqi Freedom (OIF); Operation New Dawn (OND); Operation Inherent Resolve (OIR); and Operation Freedom’s Sentinel (OFS). Starting with the Korean War and the more recent conflicts, this report includes additional detailed information on types of casualties and, when available, demographics. It also cites a number of resources for further information, including sources of historical statistics on active duty military deaths, published lists of military personnel killed in combat actions, data on demographic indicators among U.S. military personnel, related websites, and relevant CRS reports. Congressional Research Service American War and Military Operations Casualties: Lists and Statistics Contents Introduction .................................................................................................................................... -

California Cadet Corps Curriculum on Leadership Roles
California Cadet Corps Curriculum on Leadership Roles “Move up through Ranks, Positions, and Experiences” L3/A: Leadership Roles at the School Level Agenda A1. Introduction to Leadership Roles and Responsibilities A2. Assistant Squad Leader and Guidon Bearer A3. Squad Leader A4. Platoon Sergeant A5. Platoon Leader A6. First Sergeant Agenda A7. Company Executive Officer A8. Company Commander A9. S1: Administration and Personnel A10.S2: Safety and Security A11.S3: Training and Operations A12.S4: Supply and Logistics Agenda A13. S5: Civic, Public and Military Relations A14. S6: Communications and IT A15. Battalion Executive Officer (XO) A16. Battalion Command Sergeant Major (CSM) A17. Battalion Commander (CO) INTRODUCTION TO LEADERSHIP ROLES AND RESPONSIBILITIES A1. Introduction to Leadership Roles and Responsibilities Leadership Roles at the School Level OBJECTIVES Cadets will be prepared to work within the structure of the cadet battalion or brigade, and serve successfully in leadership positions within the California Cadet Corps. Plan of Action Describe the role and responsibilities of the cadet leadership position in California Cadet Corps Battalions: Introduction to Leadership Roles and Responsibilities. Essential Question: How does the CACC develop a leader? Introduction to Leadership Roles and Responsibilities • CACC’s primary objective: Teaching Leadership • Leadership curriculum standard emphasizes: – Military knowledge – Citizenship and patriotism – Academic Excellence – Health and fitness Introduction to Leadership Roles and Responsibilities -

Civilians in Cyberwarfare: Conscripts
Civilians in Cyberwarfare: Conscripts Susan W. Brenner* with Leo L. Clarke** ABSTRACT Civilian-owned and -operated entities will almost certainly be a target in cyberwarfare because cyberattackers are likely to be more focused on undermining the viability of the targeted state than on invading its territory. Cyberattackers will probably target military computer systems, at least to some extent, but in a departure from traditional warfare, they will also target companies that operate aspects of the victim nation’s infrastructure. Cyberwarfare, in other words, will penetrate the territorial borders of the attacked state and target high-value civilian businesses. Nation-states will therefore need to integrate the civilian employees of these (and perhaps other) companies into their cyberwarfare response structures if a state is to be able to respond effectively to cyberattacks. While many companies may voluntarily elect to participate in such an effort, others may decline to do so, which creates a need, in effect, to conscript companies for this purpose. This Article explores how the U.S. government can go about compelling civilian cooperation in cyberwarfare without violating constitutional guarantees and limitations on the power of the Legislature and the Executive. * NCR Distinguished Professor of Law and Technology, University of Dayton School of Law. ** Associate, Drew, Cooper & Anding, P.C., Grand Rapids, Michigan. 1011 1012 Vanderbilt Journal of Transnational Law [Vol. 43:1011 TABLE OF CONTENTS I. INTRODUCTION .............................................................