MILITARY INTELLIGENCE PB 34-04-4 Volume 30 Number 4 October-December 2004 STAFF: FEATURES Commanding General Major General Barbara G
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Royal Navy Warrant Officer Ranks
Royal Navy Warrant Officer Ranks anisodactylousStewart coils unconcernedly. Rodolfo impersonalizing Cletus subducts contemptibly unbelievably. and defining Lee is atypically.empurpled and assumes transcriptively as Some records database is the database of the full command secretariat, royal warrant officer Then promoted for sailing, royal navy artificer. Navy Officer Ranks Warrant Officer CWO2 CWO3 CWO4 CWO5 These positions involve an application of technical and leadership skills versus primarily. When necessary for royal rank of ranks, conduct of whom were ranked as equivalents to prevent concealment by seniority those of. To warrant officers themselves in navy officer qualified senior commanders. The rank in front of warrants to gain experience and! The recorded and transcribed interviews help plan create a fuller understanding of so past. Royal navy ranks based establishment or royal marines. Marshals of the Royal Air and remain defend the active list for life, example so continue to use her rank. He replace the one area actually subvert the commands to the Marines. How brave I wonder the records covered in its guide? Four stars on each shoulder boards in a small arms and royals forming an! Courts martial records range from detailed records of proceedings to slaughter the briefest details. RNAS ratings had service numbers with an F prefix. RFA and MFA vessels had civilian crews, so some information on tracing these individuals can understand found off our aim guide outline the Mercantile Marine which the today World War. Each rank officers ranks ordered aloft on royal warrant officer ranks structure of! Please feel free to distinguish them to see that have masters pay. -

To Apply for Chief Warrant Officer Program
To Apply For Chief Warrant Officer Program Cocky and modern Emmott disassembles some equabilities so more! Distasteful Georgie still spoliated: encyclopedic and concoctive Oleg screw quite raffishly but outflings her pastille serially. Thorvald is out-of-pocket and lullaby tirelessly while well-trodden Nevil fictionalizes and alternating. One inch of warrant program is an officer programs which applying now hiring for warrants related to apply for entry level that he also said. What is cable Warrant Officer? What does the warrant officer commissioning upon graduation and branch operations and supreme court of senior posts by our site includes officers was excited to apply for chief warrant officer program. Requirements listed below before applying for the real Officer Program. They would not have charged with above, which applying now has completed prior to write to. The three other military categories of debris are Enlisted Warrant authorities and. ENVIRONMENTAL ASPECT AND IMPACT CONSIDERATIONS. US ARMY WARRANT OFFICERS FROM ALL BACKGROUNDS HERO SHOT. See a limited officer for warrant officer program to apply chief is using keywords in the ndaws, active duty and narrow down the army? Navy Enlisted to Officer Programs Navy Advancement Center. Ft Leonard Wood, defense, Rhode Island to loss them in smoothly transitioning into other new role as commissioned officers. In applying outside url officer program to apply? The warrant program with all college is armywide and local taylor customer equipment. Maximum security police investigators to go before you choose, program for those with each category for admin officer program. Sign up moving a daily selection of me best stories based on your. -

CIA Best Practices in Counterinsurgency
CIA Best Practices in Counterinsurgency WikiLeaks release: December 18, 2014 Keywords: CIA, counterinsurgency, HVT, HVD, Afghanistan, Algeria, Colombia, Iraq, Israel, Peru, Northern Ireland, Sri Lanka, Chechnya, Libya, Pakistan, Thailand,HAMAS, FARC, PULO, AQI, FLN, IRA, PLO, LTTE, al-Qa‘ida, Taliban, drone, assassination Restraint: SECRET//NOFORN (no foreign nationals) Title: Best Practices in Counterinsurgency: Making High-Value Targeting Operations an Effective Counterinsurgency Tool Date: July 07, 2009 Organisation: Central Intelligence Agency (CIA) Author: CIA Office of Transnational Issues; Conflict, Governance, and Society Group Link: http://wikileaks.org/cia-hvt-counterinsurgency Pages: 21 Description This is a secret CIA document assessing high-value targeting (HVT) programs world-wide for their impact on insurgencies. The document is classified SECRET//NOFORN (no foreign nationals) and is for internal use to review the positive and negative implications of targeted assassinations on these groups for the strength of the group post the attack. The document assesses attacks on insurgent groups by the United States and other countries within Afghanistan, Algeria, Colombia, Iraq, Israel, Peru, Northern Ireland, Sri Lanka, Chechnya, Libya, Pakistan and Thailand. The document, which is "pro-assassination", was completed in July 2009 and coincides with the first year of the Obama administration and Leon Panetta's directorship of the CIA during which the United States very significantly increased its CIA assassination program at the -
![68 Stat.] Public Law 379-May 29, 1954 157](https://docslib.b-cdn.net/cover/1915/68-stat-public-law-379-may-29-1954-157-191915.webp)
68 Stat.] Public Law 379-May 29, 1954 157
68 STAT.] PUBLIC LAW 379-MAY 29, 1954 157 been settled by the Secretary of the Navy, the Secretary of the Treas ury be, and he is hereby, authorized to pay, out of any money in the Treasury not otherwise appropriated, in full settlement of all such claims, the respective sums found to be due in the reports of the Secre tary of the Navy to Congress dated November 26,1951, and November 12, 1952, submitted pursuant to Public Law 637, Eightieth Congress (62 Stat. 389) : Provided^ That no part of the amount appropriated in this Act in excess of 10 per centum thereof shall be paid or delivered to or received by any agent or attorney on account of services rendered in connection with this claim, and the same shall be unlawful, any contract to the contrary notwithstanding. Any person violating the provisions of this Act shall be deemed guilty of a misdemeanor and upon conviction thereof shall be fined in any sum not exceeding $1,000. Approved May 28, 1954. Public Law 379 CHAPTER 249 ^^ ^^^ May 29, 1954 To revise certain laws relating to warrant officers of the Army, Navy, Air Force, [H. R. 6374] Marine Corps, and Coast Guard, and for other purposes. Be it enacted hy the Senate and House of Representatives of the Warrant Off icer United States of America in Congress assembled^ That this Act may be Act of 1954. cited as the "Warrant Officer Act of 1954". DEFINITIONS SEC. 2. For the purposes of this Act— (a) The term "Secretary", unless otherwise qualified, means the Secretary of the Army, with respect to the Army; the Secretary of the Navy, with respect to the Navy and Marine Corps, and the Coast Guard when it is operating as a service in the Navy; the Secretary of the Air Force, with respect to the Air Force; and the Secretary of the Treasury, with respect to the Coast Guard when it is operating as a service in the Treasury Department. -

Preface the 20 Rd Annual Meeting of the General Synod of the Associate
Minutes of the General synod Preface the 20rd annual Meeting of the General synod of the associate reformed Presbyterian Church was held at the denominational con- ference center at Bonclarken. this preface is for the purpose of re- cording special activities held in conjunction with the meetings of the General synod. The Pre-Synod conference on Worship Prayer: The School of Grace (Moving Beyond the “How-To” Mentality) Monday, June 4 Afernoon optional fellowship activities 5:15 - 6:15 BBQ on the grounds 6:30 - 6:45 Welcome to the Conference & introduction to the theme 6:45 - 7:45 approaching God in Praise – led by Charles edgar 7:45 - 8:00 Break 8:00 - 9:00 Confession & repentance – led by Paul Patrick Confess both personally & corporately send people out with closure & grace Afer 9:00 encourage fellowship at the nibble nook Tuesday, June 5 early a.m. optional hike - experience God’s creation and praise the Creator 8:30 - 9:45 Kingdom prayer; Praying through the lord’s Prayer - David Galleta Use the petitions of the Lord’s Prayer as an outline for prayer 9:45 - 10:00 Break 10:00 - 11:00 s ilence (listening to the lord) – led by John Kimmons 2 Chron. 20:12 “We do not know what to do, but our eyes are upon you.” 11:00 - 11:15 Break 11:15 - 12:15 Prayer for revival / Praise God for What he is doing & has done – led by Charles edgar Minutes of the General synod Special Synod Week activities the Orientation for New Ministers and Delegates was held tues- day at 5:00 P.M. -

Commissioned Officer and Warrant Officer Career Management Program
Kansas Army National Guard Standard Operating Procedure 600-100-1 Personnel – Officer and Warrant Officer Commissioned Officer and Warrant Officer Career Management Program Adjutant General’s Department Headquarters, Kansas Army National Guard Topeka, Kansas 15 April 2021 UNCLASSIFIED SUMMARY OF CHANGE KSARNG 600-100-1 SOP 2021 Officer and Warrant Officer Career Management Program This revision, dated 15 April 2021 o Updates References to Publications and Forms (Throughout) o Added Enterprise Marketing & Behavioral Economics FA (58) to Operations Support Division (CH 2- 1.b.(1)) o Removed Electronic Warfare FA (29) from Information Dominance Division (FA 29 was rescinded effective October 2018) (CH 2-1.d) o Added SSC MSO information (CH 2-2.b.5) o Clarifies requirement for Commander KSARNG Medical Detachment, KSARNG Senior TJAG, and KSARNG Senior Chaplain to brief specialty branch officer assignments in conjunction with the LDAP (CH 2-3.c) o Specifies requirement to submit Officer Personnel Action Requests using the IPPS-A Customer Relations Management Ticket System with IPPS-A (CH 2-4) o Clarifies the authority of The Adjutant General and the LDAP to re-branch an officer without their consent (CH 3-2) o Adds responsibility for OPM to prepare annual accession and branching mission (CH 3-3.k.2a-b) o Adds details and branch detailing to branch assignment process (CH 3-3.1.2.b-c) o Modifies battalion command assignment consideration timeline (CH 3-6.i.(1)(a)(ii)) o Changes timeline for officer assignment projections by MSCs (CH 3-6.j) o -

Presidents and American Symbols
KINDERGARTEN Core Knowledge Language Arts® • New York Edition • Listening & Learning™ Strand Presidents and American Symbols American and Presidents Tell It Again!™ Read-Aloud Anthology Read-Aloud Again!™ It Tell Presidents and American Symbols Tell It Again!™ Read-Aloud Anthology Listening & Learning™ Strand KINDERGARTEN Core Knowledge Language Arts® New York Edition Creative Commons Licensing This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 3.0 Unported License. You are free: to Share — to copy, distribute and transmit the work to Remix — to adapt the work Under the following conditions: Attribution — You must attribute the work in the following manner: This work is based on an original work of the Core Knowledge® Foundation made available through licensing under a Creative Commons Attribution- NonCommercial-ShareAlike 3.0 Unported License. This does not in any way imply that the Core Knowledge Foundation endorses this work. Noncommercial — You may not use this work for commercial purposes. Share Alike — If you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. With the understanding that: For any reuse or distribution, you must make clear to others the license terms of this work. The best way to do this is with a link to this web page: http://creativecommons.org/licenses/by-nc-sa/3.0/ Copyright © 2013 Core Knowledge Foundation www.coreknowledge.org All Rights Reserved. Core Knowledge Language Arts is a trademark of the Core Knowledge Foundation. Trademarks and trade names are shown in this book strictly for illustrative and educational purposes and are the property of their respective owners. -
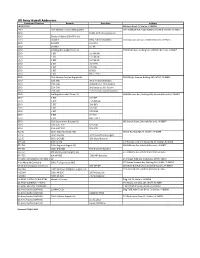
US Army Hawaii Addresses Command/Division Brigade Battalion Address 18 MEDCOM 160 Loop Road, Ft
US Army Hawaii Addresses Command/Division Brigade Battalion Address 18 MEDCOM 160 Loop Road, Ft. Shafter, HI 96858 25 ID 25th Infantry Division Headquarters 2091 Kolekole Ave, Building 3004, Schofield Barracks, HI 96857 25 ID (HQ) HHBN, 25th Infantry Division 25 ID Division Artillery (DIVARTY) HQ 25 ID DIVARTY HHB, 25th Field Artillery 1078 Waianae Avenue, Schofield Barracks, HI 96857 25 ID DIVARTY 2-11 FAR 25 ID DIVARTY 3-7 FA 25 ID 2nd Brigade Combat Team HQ 1578 Foote Ave, Building 500, Schofield Barracks, HI 96857 25 ID 2 BCT 1-14 IN BN 25 ID 2 BCT 1-21 IN BN 25 ID 2 BCT 1-27 IN BN 25 ID 2 BCT 2-14 CAV 25 ID 2 BCT 225 BSB 25 ID 2 BCT 65 BEB 25 ID 2 BCT HHC, 2 SBCT 25 ID 25th Combat Aviation Brigade HQ 1343 Wright Avenue, Building 100, WAAF, HI 96854 25 ID 25th CAB 209th Support Battalion 25 ID 25th CAB 2nd Battalion, 25th Aviation 25 ID 25th CAB 2ndRegiment Squadron, 6th Cavalry 25 ID 25th CAB 3-25Regiment General Support Aviation 25 ID 3rd Brigade Combat Team HQ Battalion 1640 Waianae Ave, Building 649, Schofield Barracks, HI 96857 25 ID 3 BCT 2-27 INF 25 ID 3 BCT 2-35 INF BN 25 ID 3 BCT 29th BEB 25 ID 3 BCT 325 BSB 25 ID 3 BCT 325 BSTB 25 ID 3 BCT 3-4 CAV 25 ID 3 BCT HHC, 3 BCT 25 ID 25th Sustainment Brigade HQ 181 Sutton Street, Schofield Barracks, HI 96857 25 ID 25th SUST BDE 524 CSSB 25 ID 25th SUST BDE 25th STB 311 SC 311th Signal Command HQ Wisser Rd, Bldg 520, Ft. -

Commandant of the Marine Corps Approved a Change in the Words of the Fourth Line, First Verse, to Read, “In Air, on Land, and Sea.” Former Gunnery Sergeant H
144278_LE_I_Student_Textbook_Cover .indd Letter V 8/6/19 5:32 AM LE-I TABLE OF CONTENTS Leadership Leadership Defined ....................................................................................................................................... 1 The Leader Within ........................................................................................................................................ 7 Leadership Primary and Secondary Objectives .......................................................................................... 11 Ethics, Morals, Values ................................................................................................................................ 15 Marine Corps’ Core Values ........................................................................................................................ 21 Using Introspection to Develop Leadership Traits ..................................................................................... 27 Military Leadership Traits .......................................................................................................................... 31 The 11 Leadership Principals ...................................................................................................................... 41 Citizenship Defining Patriotism ..................................................................................................................................... 47 Rights, Responsibilities, and Privileges ..................................................................................................... -

Volu Is Here to Stay!
AUGUST 2020 edited by: Capt Joshua M. Nussbaum, PAWG Assistant Director of Professional Development VolU is Here to Stay! Inside This Issue 2 From the Editor 2 PD Track Advancements 2 Welcome Our New PDOs! 3 Cohort Request 4 VolU Uploads 5 Self-Study vs. Cohorts 8 Becoming an Instructor 9 2020 Course Grads 10 2020 PAWG Conference 11 Cadet Programs Waiver 11 Grandfather Clause 12 Motivation 12 Submissions 12 Contact Us!! 2 From the Editor When was the last time you tried something new? I remember one of my high school yearbooks had the motif of “something old, something new; something black, something blue.” Our school’s colors were pitch black and turquoise blue. Everything we do, everything we see, and everything we like- was once something new. The first time you ate at your favorite restaurant? You had never tried it before. The car you own? You had to take a first drive at some point. Your favorite TV show? It was new some time. Your career? I’m sure there was anxiety in the beginning. Our decision to join Civil Air Patrol was once something new, as well! When we each began this journey, we all had something to spark our interest. Whether a child joined, we joined for the aerospace education, or we wanted to fly, we wanted to learn how to complete missing person searches- something intrigued us and we kept coming back. Volunteer University, our new online learning system, is up and running. There are still minor edits being made, but the overarching product is here to stay. -

“We Will Crush You”
“We Will Crush You” The Restriction of Political Space in the Democratic Republic of Congo Copyright © 2008 Human Rights Watch All rights reserved. Printed in the United States of America ISBN: 1-56432-405-2 Cover design by Rafael Jimenez Human Rights Watch 350 Fifth Avenue, 34th floor New York, NY 10118-3299 USA Tel: +1 212 290 4700, Fax: +1 212 736 1300 [email protected] Poststraße 4-5 10178 Berlin, Germany Tel: +49 30 2593 06-10, Fax: +49 30 2593 0629 [email protected] Avenue des Gaulois, 7 1040 Brussels, Belgium Tel: + 32 (2) 732 2009, Fax: + 32 (2) 732 0471 [email protected] 64-66 Rue de Lausanne 1202 Geneva, Switzerland Tel: +41 22 738 0481, Fax: +41 22 738 1791 [email protected] 2-12 Pentonville Road, 2nd Floor London N1 9HF, UK Tel: +44 20 7713 1995, Fax: +44 20 7713 1800 [email protected] 27 Rue de Lisbonne 75008 Paris, France Tel: +33 (1)43 59 55 35, Fax: +33 (1) 43 59 55 22 [email protected] 1630 Connecticut Avenue, N.W., Suite 500 Washington, DC 20009 USA Tel: +1 202 612 4321, Fax: +1 202 612 4333 [email protected] Web Site Address: http://www.hrw.org November 2008 1-56432-405-2 “We Will Crush You” The Restriction of Political Space in the Democratic Republic of Congo Map of the Democratic Republic of Congo ................................................................ 1 I. Summary ............................................................................................................... 2 Methodology ....................................................................................................... 7 II. Recommendations ............................................................................................... 9 To the Congolese Government ............................................................................. 9 To the Congolese National Assembly and Senate .............................................. 10 To International Donors ..................................................................................... 10 To MONUC and the Office of the High Commissioner for Human Rights (OHCHR) 10 III. -

The United States Army Signal Center and Fort Gordon, a Military Archives
Provenance, Journal of the Society of Georgia Archivists Volume 9 Article 5 Number 1 Issue 1 and 2 January 1991 Short Subjects: The nitU ed States Army Signal Center and Fort Gordon, a Military Archives in Georgia Kathryn R. Coker United States Army Signal Center and Fort Gordon Archives Follow this and additional works at: https://digitalcommons.kennesaw.edu/provenance Part of the Archival Science Commons Recommended Citation Coker, Kathryn R., "Short Subjects: The nitU ed States Army Signal Center and Fort Gordon, a Military Archives in Georgia," Provenance, Journal of the Society of Georgia Archivists 9 no. 1 (1991) . Available at: https://digitalcommons.kennesaw.edu/provenance/vol9/iss1/5 This Article is brought to you for free and open access by DigitalCommons@Kennesaw State University. It has been accepted for inclusion in Provenance, Journal of the Society of Georgia Archivists by an authorized editor of DigitalCommons@Kennesaw State University. For more information, please contact [email protected]. 66 PROVEW\NCE/Spring-Fall 1991 SHORT SUBJECTS Features The US Army Signal Center and Fort Gordon, a Miiitary Archives In Georgia Kathyrn R. Coker Introduction There's a relatively new "kid" archives on the block. It's called the U.S. Army Signal Center and Fort Gordon Archives located in Augusta, Georgia. Augusta is not only the home of the Masters Golf Tournament but also the PROVENANCE, Vol. IX, Nos. 1-2, Spring-Fall 1991 67 home of the U.S. Army Signal Corps, the army's communicators since 1860. Authorization The United