The Use of Pseudonym in Social Media
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FHISO CFPS 21: Proposal for Handling Personal Names
CFPS 21 (Call for Papers Submission number 21) Proposal for Handling Personal Names Submitted by: Proctor, Tony Type: Technical proposal Created: 2013-03-19 Last updated: 2013-04-20 URL: Most recent version: http://fhiso.org/files/cfp/cfps21.pdf This version: http://fhiso.org/files/cfp/cfps21_v1-1.pdf Description: Proposal for Handling Personal Names Keywords: Personal-names, Culture-neutral Family History Information Standards Organisation, Inc. http://fhiso.org/ Contents 1. Abstract ........................................................................................................................................... 3 2. Proposal ........................................................................................................................................... 3 2.1 Name Structure ......................................................................................................................... 3 2.2 Time Dependency ..................................................................................................................... 3 2.3 Name Types .............................................................................................................................. 4 2.4 Name Matching ........................................................................................................................ 4 2.5 Sorting and Collation ................................................................................................................ 4 3. Not Covered or Not Required ....................................................................................................... -

Lapp 1 the Victorian Pseudonym and Female Agency Research Thesis
Lapp 1 The Victorian Pseudonym and Female Agency Research Thesis Presented in partial fulfillment of the requirements for graduation with research distinction in English in the undergraduate colleges of The Ohio State University by Anna Lapp The Ohio State University April 2015 Project Advisor: Professor Robyn Warhol, Department of English Lapp 2 Chapter One: The History of the Pseudonym Anonymity disguises information. For authors, disguised or changed names shrouds their circumstance and background. Pseudonyms, or pen names, have been famously used to disguise one’s identity. The word’s origin—pseudṓnymon—means “false name”. The nom de plume allows authors to conduct themselves without judgment attached to their name. Due to an author’s sex, personal livelihood, privacy, or a combination of the three, the pen name achieves agency through its protection. To consider the overall protection of the pseudonym, I will break down the components of a novel’s voice. A text is written by a flesh-and-blood, or actual, author. Second, an implied author or omnipresent figure of agency is present throughout the text. Finally, the narrator relates the story to the readers. The pseudonym offers freedom for the actual author because the author becomes two-fold—the pseudonym and the real person, the implied author and the actual author. The pseudonym can take the place of the implied author by acting as the dominant force of the text without revealing the personal information of the flesh-and-blood author. Carmela Ciuraru, author of Nom de Plume: A (Secret) History of Pseudonyms, claims, “If the authorial persona is a construct, never wholly authentic (now matter how autobiographical the material), then the pseudonymous writer takes this notion to yet another level, inventing a construct of a construct” (xiii-xiv). -

A RADAR for Information Reconciliation in Question Answering Systems Over Linked Data 1
Undefined 1 (2009) 1–5 1 IOS Press A RADAR for Information Reconciliation in Question Answering Systems over Linked Data 1 Editor(s): Name Surname, University, Country Solicited review(s): Name Surname, University, Country Open review(s): Name Surname, University, Country a, b c Elena Cabrio ⇤, Serena Villata and Alessio Palmero Aprosio a University of Nice Sophia Antipolis, 2000 Route des Lucioles BP93 06902, Sophia Antipolis - France E-mail: [email protected] b CNRS - I3S laboratory, 2000 Route des Lucioles BP93 06902, Sophia Antipolis - France E-mail: [email protected] c Fondazione Bruno Kessler, Via Sommarive, 18, 38123 Povo (TN) - Italy E-mail: [email protected] Abstract. In the latest years, more and more structured data is published on the Web and the need to support typical Web users to access this body of information has become of crucial importance. Question Answering systems over Linked Data try to address this need by allowing users to query Linked Data using natural language. These systems may query at the same time different heterogenous interlinked datasets, that may provide different results for the same query. The obtained results can be related by a wide range of heterogenous relations, e.g., one can be the specification of the other, an acronym of the other, etc. In other cases, such results can contain an inconsistent set of information about the same topic. A well known example of such heterogenous interlinked datasets are language-specific DBpedia chapters, where the same information may be reported in different languages. Given the growing importance of multilingualism in the Semantic Web community, and in Question Answering over Linked Data in particular, we choose to apply information reconciliation to this scenario. -

Les Paul the Search for the New Sound Biography Written By
Les Paul The Search for the New Sound Biography written by: Becky Marburger Educational Producer Wisconsin Media Lab Glossary abolish (v): . to end or do away with aspiring (adj): . hoping for or working toward a goal Great Depression (n): . a time period from 1929 through the 1930s when it was hard for people around the world to fi nd a job or Table of Contents earn money harmonica (n): . a musical instrument; sound is made when the player inhales or exhales Introduction . 2 into it, vibrating the reeds inside Early Life . 3 immigrant (n): . a person who comes to live in a new country and stays there Instruments and Experiments . 4 legacy (n): . anything handed down from the past to future generations Hitting the Road . .6 multitrack recorder (n): . a machine that enables a musician Growing Career . 8 to record different single tracks and Conclusion . 10 combine them into one recording player piano (n): . a self-playing piano that makes music Glossary . 12 by reading the holes punched in a spinning paper roll rhubarb (n): . a plant with a thick pink or red stem and large green leaves separate (v): . to stop being a couple or husband and wife stage name (n): . a name performers use that is not their legal name 12 Introduction Les Paul’s mother often told him, “It’s your life. It’s up to you.” She wanted her son to go for his dreams. Les was a musician and an inventor. He dreamed of creating a new sound. Musicians today still use Les’s inventions and music. -

Issues in the Linguistics of Onomastics
Journal of Lexicography and Terminology, Volume 1, Issue 2 Issues in the Linguistics of Onomastics By Vincent M. Chanda School of Humanities and Social Science University of Zambia Email: mchanda@@gmail.com Abstract Names, also called proper names or proper nouns, are very important to mankind that there is no human language without names and, for some types of names, there are written or unwritten naming conventions. The social importance of names is also the reason why onomastics, the study of names, is a multidisciplinary field. After briefly discussing the multidisciplinary nature of onomastics, the article proves the following view stated and proved by many a scholar: proper names have a grammar that includes some grammatical features of common nouns. In so doing, the article shows that, like common nouns, proper names show cross linguistic differences. To prove that names do have a grammar which in some aspects differs from the grammar of common nouns, the article often compares proper names and common nouns. Furthermore, the article uses data from several languages in addition to English. After a bief discussion of orthographic differences between proper names and common nouns, the article focuses on the morphology, both inflectional and lexical, and the syntax of proper names. Key words: Name, common noun, onomastics, multidisciplinary, naming convention, typology of names, anthroponym, inflectional morphology, lexical morphology, derivation, compounding, syntac. 67 Journal of Lexicography and Terminology, Volume 1, Issue 2 1. Introduction Onomastics or onomatology, is the study of proper names. Proper names are terms used as a means of identification of particular unique beings. -

Indigenous Music Awards Presented by Casinos of Winnipeg Announce Performers for May 17 Award Show
FOR IMMEDIATE RELEASE May 7, 2019 Indigenous Music Awards presented by Casinos of Winnipeg announce performers for May 17 award show Treaty One Territory _ The Indigenous Music Awards presented by the Casinos of Winnipeg is proud to announce this year’s performers. “This year we have performances from someone who is nominated as Best New Artist to someone who is in his 30th year in the music industry,” said Lisa Meeches, executive director for the Manito Ahbee Festival. “Each of these performers brings something special to the stage and we are excited to share the variety of musical genres with the audience,” said Jacquie Black, manager of the Indigenous Music Awards. Performers for this year’s show at the Club Regent Casino on May 17 include: Don Amero, Laura Grizzlypaws, Angela Amarualik, HellnBack, Celeigh Cardinal, and Midnight Shine. Hometown favourite and all-around nice guy Don Amero is nominated for two awards – Best Music Video for “Church” and Best Country Album for Evolution. “Performing on the IMA stage is a bit of a full circle moment for me. When it was the APCMAs (Aboriginal People’s Choice Music Awards) that’s kind of where I got my start in the business. It’s a true honour to be getting back up there and sharing the stage with some of today’s Indigenous music stars,” said Amero. Laura Grizzlypaws hails from Lillooet, B.C. Her St’át’imc name is Stálhalamcen which means Grizzly Paws. She is nominated for Best Inuit, Indigenous Language, or Francophone Album for We are Children of the Land; and Best Hand Drum Album for Come Home. -

Do You Know Bruce Was Known by Many Names?
Newspapers In Education and the Wing Luke Museum of the Asian Pacific American Experience present ARTICLE 2 DO YOU KNOW BRUCE WAS KNOWN BY MANY NAMES? “The key to immortality is living a life worth remembering.”—Bruce Lee To have one English name and one name in your family’s mother tongue is common Bruce began teaching and started for second and third generation Asian Americans. Bruce Lee had two names as well as his first school here in Seattle, on a number of nicknames he earned throughout his life. His Chinese name was given to Weller Street, and then moved it to him by his parents at birth, while it is said that a nurse at the hospital in San Francisco its more prominent location in the where he was born gave him his English name. While the world knows him primarily University District. From Seattle as Bruce Lee, he was born Lee Jun Fan on November 27, 1940. he went on to open schools in Oakland and Los Angeles, earning Bruce Lee’s mother gave birth to him in the Year of the Dragon during the Hour of the him the respectful title of “Sifu” by Dragon. His Chinese given name reflected her hope that Bruce would return to and be his many students which included Young Bruce Lee successful in the United States one day. The name “Lee Jun Fan” not only embodied the likes of Steve McQueen, James TM & (C) Bruce Lee Enterprises, LLC. All Rights Reserved. his parents’ hopes and dreams for their son, but also for a prosperous China in the Coburn, Kareem Abdul Jabbar, www.brucelee.com modern world. -

Volume VIII, No. 2 28 February 2007
Volume VIII, No. 2 28 February 2007 ISSN 1555-774X. Copyright © 2007, PolishRoots®, Inc. Editor: William F. “Fred” Hoffman, E-mail: <[email protected]> *************************************** CONTENTS Welcome More Than One Surname Letters to the Editor Mazowsze Troupe on PBS Poznań Project Update Nobility vs. Gentry New Book on Ukrainian Genealogy Post-Immigration Name Changes 1852 New Year’s Resolutions Solve Genealogical Mysteries Polish Trivia Questions Upcoming Events More Useful Web Addresses You May Reprint Articles... *************************************** *** WELCOME! *** to the latest issue of Gen Dobry!, the e-zine of PolishRoots®. If you missed previous issues, you can find them here: http://www.polishroots.org/gendobry/gendobry_index.htm If you’d like Gen Dobry! in PDF form, this issue is available for downloading here: Gen Dobry!, Vol. VIII, No. 2, February 2007— 1 http://www.polishroots.org/gendobry/PDF/GenDobry_VIII_2.pdf *************************************** *** MORE THAN ONE SURNAME *** by Fred Hoffman<[email protected]> Recently there has been a very interesting discussion on the Galicia_Poland-Ukraine list, one I thought I might write about because the subject comes up often: why the same person may be listed in records with two different surnames. At practically every genealogical conference where I’ve spoken, a researcher has come up with photocopies of records and asked why the same person shows up under one name in this one, another in that one. So I know the subject interests and baffles people. The discussion started when a member named Erika posted this note: > Wonder if anyone one might be able to shed some light on this... > I recently have access to a transcription of birth and marriage > records from Okno (these are typed out from the films, not photo- > copies), and I have traced back some of my Namakas.. -

COPYRIGHT in PSEUDONYMOUS and ANONYMOUS WORKS Ronan Deazley and Kerry Patterson
COPYRIGHT IN PSEUDONYMOUS AND ANONYMOUS WORKS Ronan Deazley and Kerry Patterson 1. Introduction The use of pseudonyms has a long-standing tradition in newspaper and magazine publishing. The Economist, for example, operates a well-established practice of editorial anonymity in that all of their columnists publish under pseudonyms such as Bagehot, Lexington and Schumpeter.1 This Guidance explains what is stated in the law about the authorship of works made under a pseudonym, and about the ownership of copyright in works created both anonymously and under a pseudonym, and considers the implications these presumptions have for rights clearance projects. 2. In Practice If the name of the publisher appears How is the work credited? on the work, the publisher is It is anonymous presumed to be the owner of the copyright until there is evidence to the contrary. A pseudonym is used No The author is presumed to be the owner of the copyright – ownership Is the author commonly of copyright depends on relationship Yes known by this pseudonym? between author and publisher Ask the publisher for information on Don’t Know the author, but if they cannot provide this information, the publisher is presumed to be the copyright owner. Within the pages of the Edwin Morgan Scrapbooks examined as part of this research project, there is one letter, cut from a newspaper letters page, which has been published under a pseudonym: Navigator. In it, the writer relates the experience of seeing a mysterious ‘aircraft’/UFO over Glasgow. So, what do the legal presumptions -
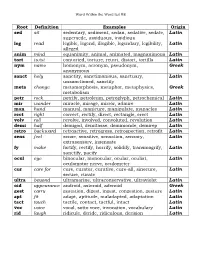
Root Definition Examples Origin Sed Sit Sedentary, Sediment, Sedan
Word Within the Word List #8 Root Definition Examples Origin sed sit sedentary, sediment, sedan, sedative, sedate, Latin supersede, assiduous, insidious leg read legible, legend, illegible, legendary, legibility, Latin alleged anim mind equanimity, animal, animated, magnanimous Latin tort twist contorted, torture, retort, distort, tortilla Latin nym name homonym, acronym, pseudonym, Greek anonymous sanct holy sanctity, sanctimonious, sanctuary, Latin unsanctioned, sanctify meta change metamorphosis, metaphor, metaphysics, Greek metabolism petr rock petrify, petroleum, petroglyph, petrochemical Latin mir wonder miracle, mirage, mirror, admire Latin man hand manual, manicure, manipulate, manacles Latin rect right correct, rectify, direct, rectangle, erect Latin volv roll revolve, involved, convoluted, revolution Latin demi half demigod, demitasse, demimonde, demirep Latin retro backward retroactive, retrogress, retrospection, retrofit Latin sens feel sense, sensitive, sensation, sensory, Latin extrasensory, insensate fy make fortify, rectify, horrify, solidify, transmogrify, Latin sanctify, pacify ocul eye binocular, monocular, ocular, oculist, Latin oculomotor nerve, oculometer cur care for cure, curator, curative, cure-all, sinecure, Latin secure, curate ultra beyond ultramarine, ultraconservative, ultraviolet Latin oid appearance android, asteroid, adenoid Greek gest carry gestation, digest, ingest, congestion, gesture Latin apt fit adapt, aptitude, maladapted, adaptation Latin tact touch tactile, contact, tactful, intact Latin voc voice vocal, sotto voce, invocation, vocabulary Latin rid laugh ridicule, deride, ridiculous, derision Latin Word Within the Word List #8 Using the context clues from the sentence and your understanding of the root, define the underlined words in the following sentences. 1. His sedentary job left him weak and out of shape. 2. The college student’s handwriting was illegible. 3. The bitter animosity made him lose his equanimity. -
Party Name Side Note
ISB Publication Doc Ref: ISB-000075 Party Name Side Note Version: 2.0 Issue Date: 26/04/2016 Document Version History Modified Version Status Issue Date by Description 1.0 Approved: 06/05/2014 ISB Guidance note for Party Recommended Name documentation 2.0 Approved: 26/04/2016 TSS Updated to align with model Recommended changes © Crown copyright 2016 Party Name Side Note Contents 1 Introduction ________________________________________________ 4 1.1 Purpose ______________________________________________________ 4 1.2 Scope ________________________________________________________ 5 1.3 Business Data Architecture (BDA) Model Version ______________________ 5 2 Design Concept _____________________________________________ 6 2.1 Business Requirements __________________________________________ 6 2.1.1 (Party of type) Person ________________________________________________ 6 2.1.2 (Party of type) Organisation ___________________________________________ 7 2.1.3 Common (to both person and organisation types of Party) ___________________ 7 2.2 Entity Definition Models __________________________________________ 8 2.3 Attribute Models ________________________________________________ 9 3 How the Structure resolves the Business Requirements __________ 10 3.1 Multiple names ________________________________________________ 10 3.2 Re-usable name bank __________________________________________ 11 3.3 Parsing a name _______________________________________________ 12 3.4 Name components ordering ______________________________________ 13 3.5 Single design for -

Classifying Inconsistencies in Dbpedia Language Specific Chapters
Classifying Inconsistencies in DBpedia Language Specific Chapters Elena Cabrio, Serena Villata, Fabien Gandon INRIA 2004 Route des Lucioles BP93, 06902 Sophia Antipolis, France fi[email protected] Abstract This paper proposes a methodology to identify and classify the semantic relations holding among the possible different answers obtained for a certain query on DBpedia language specific chapters. The goal is to reconcile information provided by language specific DBpedia chapters to obtain a consistent results set. Starting from the identified semantic relations between two pieces of information, we further classify them as positive or negative, and we exploit bipolar abstract argumentation to represent the result set as a unique graph, where using argumentation semantics we are able to detect the (possible multiple) consistent sets of elements of the query result. We experimented with the proposed methodology over a sample of triples extracted from 10 DBpedia ontology properties. We define the LingRel ontology to represent how the extracted information from different chapters is related to each other, and we map the properties of the LingRel ontology to the properties of the SIOC-Argumentation ontology to built argumentation graphs. The result is a pilot resource that can be profitably used both to train and to evaluate NLP applications querying linked data in detecting the semantic relations among the extracted values, in order to output consistent information sets. Keywords: DBpedia language specific chapters, inconsistencies detection, bipolar argumentation 1. Introduction France), and ii) the combination of these query results may The Web is an information space which is evolving from lead to inconsistent information sets about the same topic.