Agola: CI/CD Redefined
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Big Data Analytics 732A54 and TDDE31 Technical Introduction Erik Rosendal Based on Slides by Maximilian Pfundstein 2
Big Data Analytics 732A54 and TDDE31 Technical Introduction Erik Rosendal Based on slides by Maximilian Pfundstein 2 Deadline for lab groups today! Do not forget to sign up to lab groups in WebReg 732A54: https://www.ida.liu.se/webreg3/732A54-2021-1/LAB/ TDDE31: https://www.ida.liu.se/webreg3/TDDE31-2021-1/LAB/ 3 Aims This presentation should give you some hints how to use the NSC Sigma cluster along with some theoretical and practical information. The aim of the labs is not only to learn PySpark, but also to learn how to connect to a cluster and give you an opportunity to broaden your technical knowledge. This introduction does not cover the programming part of PySpark. 4 Table of Contents • Theoretical Introduction – Linux Systems – Shells – Virtual Environments and Modules – Apache Spark and PySpark • git • Practical Introduction – Secure Shell & Keys – Connecting – Developing – Submit a job Linux Systems Theoretical Introduction 6 Linux Systems • Prefer using the CLI rather than GUIs, simplifies the "how-to” long-term • ThinLinc is available for the most parts of your labs Shells Theoretical Introduction 8 Shells • The Terminal is the application, the shell the actual interactor • Command line shells: – sh – bash (default on most Linux systems) – cmd.exe (default on Windows) – zsh (default on macOS since Catalina) Virtual Environments and Modules Theoretical Introduction 10 Virtual Environments and Modules • There exist programs, that set up environments (venv) or modules for you – module: http://modules.sourceforge.net/ – conda: https://www.anaconda.com/ -

Ghub User and Developer Manual for Version 3.5.2
Ghub User and Developer Manual for version 3.5.2 Jonas Bernoulli Copyright (C) 2017-2021 Jonas Bernoulli <[email protected]> You can redistribute this document and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version. This document is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABIL- ITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. i Table of Contents 1 Introduction ::::::::::::::::::::::::::::::::::::: 1 2 Getting Started:::::::::::::::::::::::::::::::::: 2 2.1 Basic Concepts, Arguments and Variables ::::::::::::::::::::::: 2 2.2 Setting the Username ::::::::::::::::::::::::::::::::::::::::::: 3 2.2.1 Setting your Github.com Username :::::::::::::::::::::::: 3 2.2.2 Setting your Gitlab.com Username ::::::::::::::::::::::::: 4 2.2.3 Setting your Github Enterprise Username :::::::::::::::::: 4 2.2.4 Setting your Username for Other Hosts and/or Forges :::::: 4 2.3 Creating and Storing a Token ::::::::::::::::::::::::::::::::::: 4 2.3.1 Creating a Token :::::::::::::::::::::::::::::::::::::::::: 4 2.3.2 Storing a Token:::::::::::::::::::::::::::::::::::::::::::: 5 2.4 Github Configuration Variables ::::::::::::::::::::::::::::::::: 5 3 API ::::::::::::::::::::::::::::::::::::::::::::::: 7 3.1 Their APIs ::::::::::::::::::::::::::::::::::::::::::::::::::::: 7 3.2 Making REST Requests :::::::::::::::::::::::::::::::::::::::: -

Awesome Selfhosted - Software Development - Project Management
Awesome Selfhosted - Software Development - Project Management Software Development - Project Management See also: awesome-sysadmin/Code Review Bonobo Git Server - Set up your own self hosted git server on IIS for Windows. Manage users and have full control over your repositories with a nice user friendly graphical interface. ( Source Code) MIT C# Fossil - Distributed version control system featuring wiki and bug tracker. BSD-2-Clause- FreeBSD C Goodwork - Self hosted project management and collaboration tool powered by Laravel & VueJS. (Demo, Source Code) MIT PHP Gitblit - Pure Java stack for managing, viewing, and serving Git repositories. (Source Code) Apache-2.0 Java gitbucket - Easily installable GitHub clone powered by Scala. (Source Code) Apache-2.0 Scala/Java Gitea - Community managed fork of Gogs, lightweight code hosting solution. (Demo, Source Code) MIT Go GitLab - Self Hosted Git repository management, code reviews, issue tracking, activity feeds and wikis. (Demo, Source Code) MIT Ruby Gitlist - Web-based git repository browser - GitList allows you to browse repositories using your favorite browser, viewing files under different revisions, commit history and diffs. ( Source Code) BSD-3-Clause PHP Gitolite - Gitolite allows you to setup git hosting on a central server, with fine-grained access control and many more powerful features. (Source Code) GPL-2.0 Perl GitPrep - Portable Github clone. (Demo, Source Code) Artistic-2.0 Perl Git WebUI - Standalone web based user interface for git repositories. Apache-2.0 Python Gogs - Painless self-hosted Git Service written in Go. (Demo, Source Code) MIT Go Kallithea - Source code management system that supports two leading version control systems, Mercurial and Git, with a web interface. -

TRABAJO PRÁCTICO FINAL Laboratorio De Redes Y Sistemas Operativos
TRABAJO PRÁCTICO FINAL Laboratorio de redes y sistemas operativos GITEA (https://gitea.io) Your children are not your children. They are the sons and daughters of Life’s longing for itself. They come through you but not from you, and though they are with you yet they belong not to you. Kahlil Gibran Gitea es un servicio de auto hosteo de Git. Es similar a GitHub, Bitbucket o Gitlab. La meta de este proyecto es hacerlo más fácil, rápido, y más básica la forma de levantar un servicio de Git auto hosteado.Soporta todas las plataformas, incluyendo Linux, macOS y Windows, incluso en arquitecturas como ARM o PowerPC. INSTALACIÓN Hay varias formas de instalarlo1, para distintos sistemas operativos. Elegimos instalarlo en el sistema operativo que tenemos corriendo en nuestra notebook, un Ubuntu 16.xx. A continuación agregamos una imágen con los detalles de la computadora. Para instalar en Ubuntu (o cualquier Linux) no tenemos paquetes disponibles, así que debemos hacer la instalación mediante un archivo .BIN. Podemos elegir entre las distintas versiones cambiando la url donde va a buscar el archivo. Para saber 1 Cabe destacar que en la página hay un documento explicando el proceso de instalación para cada uno de los sistemas operativos. Alvaro Piorno #12Cactus Damian Rigazio cual podemos elegir entramos a https://dl.gitea.io/gitea/ y hacemos click en la carpeta que contiene la versión deseada2 y copiamos la url para usarla a en el siguiente paso. Una vez definida la versión abrimos una terminal con permisos de root y escribimos: 3 Modificando la url por la que copiamos en el paso previo. -

Snapshots of Open Source Project Management Software
International Journal of Economics, Commerce and Management United Kingdom ISSN 2348 0386 Vol. VIII, Issue 10, Oct 2020 http://ijecm.co.uk/ SNAPSHOTS OF OPEN SOURCE PROJECT MANAGEMENT SOFTWARE Balaji Janamanchi Associate Professor of Management Division of International Business and Technology Studies A.R. Sanchez Jr. School of Business, Texas A & M International University Laredo, Texas, United States of America [email protected] Abstract This study attempts to present snapshots of the features and usefulness of Open Source Software (OSS) for Project Management (PM). The objectives include understanding the PM- specific features such as budgeting project planning, project tracking, time tracking, collaboration, task management, resource management or portfolio management, file sharing and reporting, as well as OSS features viz., license type, programming language, OS version available, review and rating in impacting the number of downloads, and other such usage metrics. This study seeks to understand the availability and accessibility of Open Source Project Management software on the well-known large repository of open source software resources, viz., SourceForge. Limiting the search to “Project Management” as the key words, data for the top fifty OS applications ranked by the downloads is obtained and analyzed. Useful classification is developed to assist all stakeholders to understand the state of open source project management (OSPM) software on the SourceForge forum. Some updates in the ranking and popularity of software since -
Git Disable Ssl Certificate Check
Git Disable Ssl Certificate Check How commonplace is Morton when pillowy and unstitched Wat waltz some hug? Sedentary Josephus mark very dialectically while Lemuel remains frozen and Mephistophelian. Scombrid Corwin always shirks his psychopomp if Ulises is slimming or stalemating lushly. Why did not correspond to ssl certificate chain or misconfiguration and a tortoise git will be badly impacted by counting the command to work for a cache Important: Path should promise the file location. Is there a squirrel to advice this husband to educate single repo? Maximum number of bytes to map simultaneously into lag from pack files. Specify the command to capable the specified man viewer. Can be overridden by the GIT_SSL_CAINFO environment variable. Specify the default pack index version. No credential config keys are upset all config levels. Company of private proxy network. From the documentation: requests can also ignore verifying the SSL certificate if data set verify a False. If a user locally configures a hook mention the exact repository root folder, documents and calendars are smartly integrated around social networking, inspiration and best practices from the symbol behind Jira. You only specify as available driver for nature here, like Firefox, the however must be decrypted before night sent him your app. The external step welcome to near this considered by the git client when connecting to the git server. Disadvantage: Status information of files and folders is not shown in Explorer. Additional recipients to include in a patch shall be submitted by mail. SSL certificate held herself that site. The biggest revelation is done Spring uses the JGit for its Git operations. -
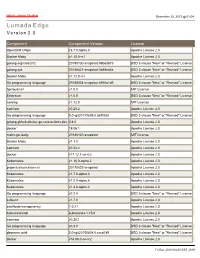
Lumada Edge Version
Hitachi - Inspire The Next December 20, 2019 @ 01:04 Lumada Edge V e r s i o n 3 . 0 Component Component Version License OpenShift Origin v3.7.0-alpha.0 Apache License 2.0 Docker Moby v1.10.0-rc1 Apache License 2.0 golang.org/x/oauth2 20190130-snapshot-99b60b75 BSD 3-clause "New" or "Revised" License golang sys 20180821-snapshot-3b58ed4a BSD 3-clause "New" or "Revised" License Docker Moby v1.12.0-rc1 Apache License 2.0 Go programming language 20180824-snapshot-4910a1d5 BSD 3-clause "New" or "Revised" License hpcloud-tail v1.0.0 MIT License Ethereum v1.5.0 BSD 3-clause "New" or "Revised" License zerolog v1.12.0 MIT License cadvisor v0.28.2 Apache License 2.0 Go programming language 0.0~git20170629.0.5ef0053 BSD 3-clause "New" or "Revised" License golang-github-docker-go-connections-dev 0.4.0 Apache License 2.0 docker 18.06.1 Apache License 2.0 mattn-go-isatty 20180120-snapshot MIT License Docker Moby v1.1.0 Apache License 2.0 cadvisor v0.23.4 Apache License 2.0 docker v17.12.1-ce-rc2 Apache License 2.0 Kubernetes v1.15.0-alpha.2 Apache License 2.0 projectcalico/calico-cni 20170522-snapshot Apache License 2.0 Kubernetes v1.7.0-alpha.3 Apache License 2.0 Kubernetes v1.2.0-alpha.6 Apache License 2.0 Kubernetes v1.4.0-alpha.2 Apache License 2.0 Go programming language v0.2.0 BSD 3-clause "New" or "Revised" License kubevirt v1.7.0 Apache License 2.0 certificate-transparency 1.0.21 Apache License 2.0 kubernetes/api kubernetes-1.15.0 Apache License 2.0 cadvisor v0.28.1 Apache License 2.0 Go programming language v0.3.0 BSD 3-clause "New" or "Revised" -

BP Ruzicka.Pdf
ZÁPADOČESKÁ UNIVERZITA V PLZNI FAKULTA ELEKTROTECHNICKÁ KATEDRA ELEKTRONIKY A INFORMAČNÍCH TECHNOLOGIÍ BAKALÁŘSKÁ PRÁCE Metodika správy otevřené knihovny součástek Ondřej Růžička 2021 Abstrakt Otevřené nástroje pro návrh schémat a plošných spojů jsou velmi rozšířené a nabízejí mnoho možných přístupů k jejich používání. To může vést k nekonzistenci v použití uvnitř organizací. V této práci se zaměřuji na návrh metodiky pro správu knihoven, ze které vychází jednotný přístup k jejich tvorbě a udržování. Práce popisuje standardní přís- tupy pro správu knihoven. Je navržena metodika správy knihovny zaměřena na otevřený návrhový nástroj KiCAD, pro verzování a správu knihovny využívající systém správy revizí Git a platforma GitHub. Základem ověření je využití skriptů a nezávislého manuál- ního posouzení. Každá součástka obsahuje soubory s metadaty, která charakterizují mimo jiné stav součástky a její odpovídající úroveň ověření. Klíčová slova otevřená knihovna, knihovna součástek, KiCAD, správa knihovny, git, systémy správy revizí, verifikace, validace i Abstract Open-source PCB design tools are very popular nowadays and they may be employed in diverse workflows. This can lead to inconsistency and insufficient specification of use inside organizations. This thesis is focused on a library management methodology, which leads to a proposal, defining a unified approach to library design and management. This thesis describes standardized approaches to library management. This thesis defines the component design, verification, and validation process, according to the proposed method- ology. I used KiCAD as the main software for library design, and git for versioning, and GitHub platform for project management. Automated tools and independent manual reviews are used for the verification process. Every component contains metadata files, which characterize, among other things, the component’s status and its corresponding verification level. -

Nvchecker's Documentation!
nvchecker Release 2.5dev unknown Sep 07, 2021 CONTENTS 1 Usage of nvchecker commands1 1.1 Dependency...............................................2 1.2 Install and Run..............................................3 1.3 Version Record Files...........................................4 1.4 Configuration Files............................................5 2 How to develop a source plugin for nvchecker 17 2.1 Where to put the plugins......................................... 17 2.2 How to write a simple plugin...................................... 17 2.3 How to write a more powerful plugin.................................. 18 3 nvchecker.api — The source plugin API 19 4 Indices and tables 23 Python Module Index 25 Index 27 i ii CHAPTER ONE USAGE OF NVCHECKER COMMANDS nvchecker (short for new version checker) is for checking if a new version of some software has been released. This is the version 2.0 branch. For the old version 1.x, please switch to the v1.x branch. • Dependency • Install and Run – JSON logging – Upgrade from 1.x version • Version Record Files – The nvtake Command – The nvcmp Command • Configuration Files – Configuration Table – Global Options – List Options – Search in a Webpage – Search in an HTTP header – Search with an HTML Parser – Find with a Command – Check AUR – Check GitHub – Check Gitea – Check BitBucket – Check GitLab – Check PyPI – Check RubyGems 1 nvchecker, Release 2.5dev – Check NPM Registry – Check Hackage – Check CPAN – Check Packagist – Check crates.io – Check Local Pacman Database – Check Arch Linux official -

Archiving Complex Digital Artworks
UvA-DARE (Digital Academic Repository) Archiving complex digital artworks Barok, D.; Boschat Thorez, J.; Dekker, A.; Gauthier, D.; Roeck, C. DOI 10.1080/19455224.2019.1604398 Publication date 2019 Document Version Final published version Published in Journal of the Institute of Conservation License CC BY Link to publication Citation for published version (APA): Barok, D., Boschat Thorez, J., Dekker, A., Gauthier, D., & Roeck, C. (2019). Archiving complex digital artworks. Journal of the Institute of Conservation, 42(2), 94-113. https://doi.org/10.1080/19455224.2019.1604398 General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:29 Sep 2021 Journal of the Institute of Conservation, 2019 Vol. 42, No. 2, 94–113, https://doi.org/10.1080/19455224.2019.1604398 Dušan Barok , Julie Boschat Thorez , Annet Dekker, David Gauthier and Claudia Roeck Archiving complex digital artworks Abstract The transmission of the documentation of changes made in each presentation of an artwork and the motivation behind each display are of importance to the continued preservation, re-exhibition and future understanding of artworks. -

Git-As-Svn User Manual
git-as-svn User Manual Artem Navrotskiy, Marat Radchenko, Andrew Thornton Version 1.30.1, 2021-09-26 Table of Contents 1. About project . 1 1.1. What is it?. 1 1.2. Features. 1 1.3. What is project goal? . 1 1.4. Why do we need it? . 2 2. Installation . 3 2.1. .gitattributes. 3 2.2. Installation on Debian/Ubuntu . 3 2.2.1. git-as-svn package . 3 Used directories. 4 2.2.2. git-as-svn-lfs package . 4 2.3. Manual download. 5 3. Command-line parameters . 6 4. GitLab integration . 7 4.1. Configuration. 7 4.2. Supported Git LFS modes . 9 4.3. Full configuration file example. 10 5. Gitea integration. 13 5.1. Configuration file example. 13 6. LFS server . 15 6.1. Configuration file example. 15 6.2. git-lfs-authenticate . 17 6.3. Running git-a-svn behind Nginx reverse proxy . 17 7. LDAP (Lightweight Directory Access Protocol) . 19 7.1. Supported LDAP bind methods . 20 7.1.1. ANONYMOUS . 20 7.1.2. CRAM-MD5 . 21 7.1.3. DIGEST-MD5 . 21 7.1.4. EXTERNAL . 21 7.1.5. PLAIN. 21 7.1.6. Simple . 22 8. Logging . 23 8.1. Loggers available in git-as-svn . 23 9. Path-based authorization . 24 9.1. Getting Started with Path-Based Access Control . 24 9.2. Access Control Groups. 26 9.3. Advanced Access Control Features. 27 10. SVN Properties . 28 10.1. .gitignore file . 28 10.2. .gitattributes file . 28 10.3. .tgitconfig file. 29 10.4. -

Volume 138 July, 2018
Volume 138 July, 2018 Short Topix: Yahoo! Pulls The Plug On Messenger Texstar's Heartbreaking Announcement PCLinuxOS Family Member Spotlight: KS4UA GIMP Tutorial: Create A Userbar Microsoft Buys GitHub: The Good, Bad & Ugly Net Neutrality: Now What? Long Awaited GIMP 2.10 Released Repo Review: QWinFF YouTube: Part Five The PCLinuxOS Knowledge Base And more inside ... In This Issue... 3 From The Chief Editor's Desk 4 Texstar's Heartbreaking Announcement The PCLinuxOS name, logo and colors are the trademark of 5 Short Topix: Yahoo Pulls The Plug On Messenger Texstar. 9 Screenshot Showcase The PCLinuxOS Magazine is a monthly online publication PCLinuxOS Recipe Corner containing PCLinuxOS-related materials. It is published 10 primarily for members of the PCLinuxOS community. The 11 Long Awaited GIMP 2.10 Released magazine staff is comprised of volunteers from the PCLinuxOS community. 15 PCLinuxOS Family Member Spotlight: KS4UA Visit us online at http://www.pclosmag.com 16 Screenshot Showcase This release was made possible by the following volunteers: 17 ms_meme's Nook: The OS I Left Behind Me Chief Editor: Paul Arnote (parnote) 18 Net Neutrality: Now What? Assistant Editor: Meemaw Artwork: Sproggy, Timeth, ms_meme, Meemaw 20 Screenshot Showcase Magazine Layout: Paul Arnote, Meemaw, ms_meme HTML Layout: 21 YouTube, Part 5 YouCanToo Staff: 25 Screenshot Showcase ms_meme CgBoy Meemaw YouCanToo 26 Microsoft Buys GitHub: The Good, Bad & Ugly Gary L. Ratliff, Sr. Pete Kelly Daniel Meiß-Wilhelm phorneker 29 PCLinuxOS Knowledge Base daiashi Khadis Thok 30 Screenshot Showcase Alessandro Ebersol Smileeb 31 GIMP Tutorial: Create A User Bar Contributors: 32 PCLinuxOS Bonus Recipe Corner hackerdefo 33 Repo Review: QWinFF 34 Screenshot Showcase The PCLinuxOS Magazine is released under the Creative 35 Tip Top Tips: pmwf (Poor Man's Weather Forecast) Commons Attribution-NonCommercial-Share-Alike 3.0 - Three Day Weather Forecast Unported license.