The Role of Bot Squads in the Political Propaganda on Twitter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MOZIONE ZINGARETTI È Tempo Di Scegliere. Prima Le Persone I. Un Congresso Per Riaccendere La Speranza
MOZIONE ZINGARETTI È tempo di scegliere. Prima le persone I. Un congresso per riaccendere la speranza Ora è tempo di scegliere. Possiamo continuare a lamentarci, dividerci, isolarci fino all’irrilevanza, oppure decidere di combattere perché l’avvenire torni ad essere un luogo della speranza, della solidarietà, della giustizia, della libertà, delle opportunità per tutti. Il cuore del problema è come reagire, cambiare, offrire un futuro all’Italia e all’Europa. Il nostro Paese, guidato dal primo governo nazionalpopulista dell’Europa occidentale, egemonizzato culturalmente e politicamente dalla nuova destra, rischia un declino inarrestabile, isolato nell’Unione europea e diviso al suo interno, impaurito, incattivito e avvitato in sé stesso. In questa Italia, il Presidente della Repubblica, Sergio Mattarella, rappresenta il più solido punto di riferimento democratico. Impediremo il declino se sapremo cambiare. Cambiare molto, se non tutto. Riconoscere senza reticenze gli errori, affrontare le ragioni delle sconfitte e offrire soluzioni concrete e una nostra visione e una nostra proposta per l’Italia. Il primo passo sarà tornare a incontrarci, in tanti, per cercare e trovare insieme le soluzioni e la radice profonda del nostro stare insieme e del costruire un’idea di società giusta. Abbiamo perso troppo tempo. Ma non sarà troppo tardi se riusciremo a cogliere la portata della sfida. Il nostro congresso si svolge in una situazione di emergenza della Repubblica. Dopo il 4 marzo 2018, è cambiato il panorama politico e sono scosse le istituzioni. Ci sono state reazioni importanti, nelle piazze, tra le donne, tra gli studenti, nel mondo produttivo, tra gli intellettuali. Nonostante i primi fallimenti del governo e la gravità di atti e comportamenti dei suoi esponenti, l'orientamento prevalente degli italiani non è cambiato, la sfiducia verso il Pd si è ulteriormente aggravata. -

Print This Article
PA rtecipazione e CO nflitto * The Open Journal of Sociopolitical Studies http://siba-ese.unisalento.it/index.php/paco ISSN: 1972-7623 (print version) ISSN: 2035-6609 (electronic version) PACO, Issue 13(1) 2020: 633-664 DOI: 10.1285/i20356609v13i1p633 Published in March 15, 2020 Work licensed under a Creative Commons At- tribution-Non commercial-Share alike 3.0 Italian License RESEARCH ARTICLE POLICY FRAMING AND PARTY COMPETITION The Italian Political Debate on Local Public Services since the Eco- nomic Crisis Valeria Tarditi University of Bologna ABSTRACT: In recent years many European governments reacted to the economic crisis intro- ducing austerity measures that particularly affected Local Public Services (LPSs) through out- sourcing, privatization and marketization. While several studies have analysed the logics of in- struments choice also in this policy sector, the political discourses and policy frames that ac- companied the tools selection for the management of LPSs in the last years have been paid lim- ited attention in the scholarly literature. Starting from these premises, the article analyses the debate on LPSs that has developed in Italy since 2008, reconstructing the frames used by the main parties through the analysis of both electoral manifestos and press reviews of articles rele- vant to LPSs in three newspapers. Particular attention is paid to the 2011 referendum against the privatization of LPSs and the 2018 referendum on local public transportation management in Rome. The paper concludes that the economic crisis and subsequent transformations of party politics and participation encouraged a politicization of the issues around local public services, as well as a shift in the related policy discourse. -

The Center-Right in a Search for Unity and the Re-Emergence of the Neo
The center-right in a search for unity and the re-emergence of the neo-fascist right Elisabetta De Giorgi a and Filippo Tronconi b aPortugese Institute of International Relations (IPRI), Universidade Nova de Lisboa, Lisbon, Portugal; bDepartment of Social and Political Sciences, University of Bologna, Bologna, Italy ABSTRACT In 2017, the parties of the centre-right camp – Silvio Berlusconi’sForza Italia, Matteo Salvini’s (Northern) League and Giorgia Meloni’sFratelli d’Italia – faced the puzzle of deciding whether to participate in the imminent general elections as allies or as rivals. On the one hand they had partially different aims (especially in relation to the European Union issue) and the problem of choosing the leadership of the alli- ance; on the other, the new electoral system, partially based on single- member districts, forced them to present common candidates in order to maximize their chances of reaching a majority of seats in parliament. In this article, we outline the stages through which the centre-right parties attempted to solve this puzzle over the course of the year, finally reaching an agreement to make a formal electoral alliance. In the final section of the article, we focus on one additional political actor of the right wing: the neo-fascist movements, notably Forza Nuova and CasaPound, which received significant media coverage during 2017. We describe how these movements were able to gain center stage and what this implied for the mainstream centre-right parties. In a way, the year 2017 began for the center-right on January 21 in Koblenz. On that date the leaders of the main extreme right parties in Europe came together in the German city for an event showcasing the visions and political aims that they shared. -

Una Lettera Inviata a Suo Tempo All'allora Ministro Della
Federazione Nazionale degli Ordini delle Professioni Infermieristiche Protocollo P-5782/I.12 A Giuseppe Conte, Presidente del Consiglio dei ministri Data 1° giugno 2018 Roberto Fico, Presidente della Camera dei Deputati Rif. Vice Presidenti Camera dei Deputati Maria Elisabetta Alberti Casellati, Presidente del Senato della Oggetto Repubblica Vice Presidenti Senato della Repubblica Giulia Grillo, Ministro della Salute Giulia Bongiorno, Ministro della Pubblica amministrazione Giovanni Tria, Ministro dell’Economia Lorenzo Fontana, Ministro della Famiglia e Disabilità Barbara Lezzi, Ministro per il Mezzogiorno Marco Bussetti, Ministro dell’Istruzione, Università e Ricerca Alfonso Bonafede, Ministro della Giustizia Matteo Salvini, Ministro dell’Interno Luigi Di Maio, Ministro del Lavoro e dello Sviluppo economi- co Erika Stefani, Ministro degli Affari regionali e Autonomie Illustri Presidenti, onorevoli Ministri, in Italia ci sono 447mila infermieri di cui circa 270mila alle dipendenze del Servizio sanitario naziona- le: molto meno della media Ocse (5,4 per mille abitanti contro la media di 9), in particolare se rapportato al numero dei medici(1). Inoltre, l’OCSE sostiene che un maggior coinvolgimento dei pazienti nei processi deci- sionali, una migliore informazione sulle prescrizioni inadeguate e l’introduzione di più infermieri potrebbero migliorare un sistema già tra i migliori dei 29 Paesi OCSE. La situazione analitica nel nostro paese è tuttavia anche più netta: di infermieri dal 2010 al 2016 (secondo i dati del Conto annuale della Ragioneria generale dello Stato) se ne sono persi circa 13mila e di medici circa 6mila. In ospedale, a titolo di esempio, il rapporto infermiere/pazienti è pari a 1/12 (un re- cente studio pubblicato sul British Medical Journal ha evidenziato come il tasso di mortalità in ospedale ri- sulti del 20% inferiore quando il rapporto infermiere/pazienti è pari a 1/6). -

Moneygram Awarded Exceptional Foreign Entrepreneurs in Italy
May 25, 2017 MoneyGram Awarded Exceptional Foreign Entrepreneurs in Italy The 2017 edition for the first time featured European-wide category ROME, ITALY (May 25, 2017) - MoneyGram, a global provider of innovative money transfer services, today awarded the winners of the ninth edition of the MoneyGram Awards, that recognize foreign entrepreneurs living and running successful businesses in Italy. The award ceremony took place at Plaza Hotel in Rome, with the attendance of MoneyGram representatives and prominent guests, including Laura Boldrini, President of Italian Chamber of Deputies, and Emma Bonino, former European Commissioner responsible for the European Community Humanitarian Office. MoneyGram Awards is a unique recognition program that represents MoneyGram's commitment to migrant communities living and working across Europe. Prizes are distributed in the following categories: Profit Growth, Innovation, Employment, Social Responsibility and Young Entrepreneur. An absolute winner, selected by a jury from category winners, receives a prestigious title of Foreign Entrepreneur of the Year. "With the MoneyGram Awards we want to recognize all those unique entrepreneurs who, in addition to helping families in their country of origin, have added value to the Italian economy and the prosperity of our country. This year, we're also hosting foreign entrepreneurs from the U.K., France and Germany. I hope that in future we'll be able to move this award even further and cover the whole European Union," said Massimo Canovi, MoneyGram’s head of Southern Europe. In 2017 edition, the prestigious title of Foreign Entrepreneur of the Year was handed over to Yafreisy Berenice Brown Omage from Dominican Republic. In 2013, she overtook a supermarket with a little bakery. -

Ecco L'identikit Del Governo Conte: Dai 3 Ministri Under 40 Agli Incarichi In
Data 08-06-2018 Pagina Foglio 1 / 3 NAVIGA HOME RICERCA ABBONATI ACCEDI italia ATTUALITÀ PARLAMENTO POLITICA POLITICA ECONOMICA DOSSIER BLOG Il debutto di Conte al Moda e lifestyle per il Imu e Tasi, come Governo Conte: ecco G7 nuovo Sole 24 Ore del prepararsi al le ipotesi in campo per sabato e della pagamento le nuove pensioni domenica dell’acconto DENTRO LA POLITICA Ecco l’identikit del governo Conte: dai 3 ministri under 40 agli incarichi in società e think tank –di Nicoletta Cottone | @NikiCottone | 08 giugno 2018 VIDEO 08 giugno 2018 Da Napoli parte tour itinerante della salute di Fondazione Ania I PIÙ LETTI DI ITALIA Palazzo Chigi ultime novità Dal catalogo del Sole 24 Ore ai nella storia repubblicana un esecutivo aveva avuto SCOPRI ALTRI PRODOTTI così tante matricole. Nel governo targato Giuseppe Conte l’89,5% dei ministri è al primo incarico. Solo 2 dei M 19 membri (dunque il 10,5%) hanno avuto un precedente incarico: sono il ministro Paolo Savona (oggi agli Affari europei, ma LE GALLERY PIÙ VISTE all’Industria nel governo Ciampi) e il ministro degli Esteri Enzo MONDO | 7 giugno 2018 Moavero Milanesi (agli Affari europei nei governi Monti e Letta). Un Hawaii, l’eruzione del vulcano Kilauea ripresa dal satellite 104061 risultato notevole se si considera che nella prima Repubblica il tasso Codice abbonamento: Data 08-06-2018 Pagina Foglio 2 / 3 di ricambio era del 22,7% e che dal 1994 in poi il tasso, pur screscendo, MODA | 5 giugno 2018 La moda americana premia si era fermato al 56,7%. -

Analisi Di Un Risultato Inatteso: Le Elezioni Regionali Del 2005 in Puglia
Saggio 1 Page 5 Tuesday, November 14, 2006 11:35 AM ANALISI DI UN RISULTATO INATTESO: LE ELEZIONI REGIONALI DEL 2005 IN PUGLIA di MARCO GIAFFREDA 5 Saggio 1 Page 6 Tuesday, November 14, 2006 11:35 AM 6 Saggio 1 Page 7 Tuesday, November 14, 2006 11:35 AM 1. Introduzione Le elezioni regionali del 3-4 aprile 2005 in Puglia possono essere annove- rate di diritto tra quelle di maggior interesse politologico sia per gli aspetti inno- vativi presenti, sia per il sorprendente esito. In una complessa tornata elettorale, per la prima volta in Puglia, un candidato alla carica di presidente della Regione è stato scelto attraverso elezioni primarie che hanno coinvolto la base dei partiti del centrosinistra, fornendo, come vedremo, una delle chiavi per il successo finale. Inoltre, dopo le elezioni del 2000, come del resto prevedeva il lungo processo di decentramento delle funzioni amministrative e di maggiore autonomia degli organi periferici dello Stato, si era aperta nella Regione una fase riformatrice che ha portato all’approvazione del nuovo Statuto regionale e di una nuova legge elet- torale per l’elezione del presidente e del consiglio. Sul fronte strettamente eletto- rale i due principali candidati, Nichi Vendola per la Grande alleanza democratica (GAD), formata dall’Ulivo più Rifondazione comunista, e Raffaele Fitto, per la Casa delle Libertà (CDL), hanno dato vita ad una campagna fortemente persona- lizzata e speculare in cui sono emerse le profonde differenze tra i due e tra due modi (e concezioni) diversi di fare politica. La vittoria di Vendola, tutt’altro che scontata ma in qualche modo prevedibile, ha rappresentato, inoltre, un forte ele- mento di discontinuità rispetto al passato e alla tradizione politico-elettorale della Puglia. -

Egr. Ministro Della Salute, On. Giulia Grillo [email protected] [email protected] [email protected]
Egr. Ministro della Salute, On. Giulia Grillo [email protected] [email protected] [email protected] Egr. Ministro dell’Economia e Finanze, Prof. Giovanni Tria [email protected] [email protected] Egr. ministro degli Affari Esteri, Prof. Enzo Moavero Milanesi [email protected] Egr. Ministro del Lavoro e delle Politiche Sociali On. Luigi Di Maio [email protected] [email protected] [email protected] Egr. Presidente della Regione Lazio Nicola Zingaretti [email protected] Egr. Assessore Sanità e Integrazione Socio-Sanitaria Dott. Alessio D’ Amato [email protected] [email protected]@legalmail.it [email protected] e p.c. Egr. Presidente del Senato, Sen. Maria Elisabetta Alberti Casellati [email protected] [email protected] [email protected] Egr. Presidente della Camera, On. Roberto Fico [email protected] Egregi Ministri, Vi scriviamo questa lettera come ultimo disperato grido di allarme, alla fine di un percorso paradossale, che va avanti da più di due anni e che, senza un Vostro intervento immediato, si concluderà con il licenziamento di tutti noi: siamo i lavoratori della Fondazione Ime (Istituto Mediterraneo di Ematologia). La Fondazione Ime nasce nel 2003, su iniziativa congiunta della Regione Lazio e dei Ministeri della Salute, degli Affari Esteri e dell’Economia. Dal marzo del 2005 la sua sede è stata individuata all’interno del Policlinico di Tor Vergata e qui – in un reparto con day hospital e 22 posti letto – vengono effettuati trapianti di midollo osseo in bambini, affetti da patologie ematologiche, provenienti da tutto il mondo. -

Il Proclama Di Zingaretti «Rinnoviamo Il Partito»
LA PROVINCIA 2 LUNEDÌ 18 MARZO 2019 Politica I temi Anno record Ben 538 milioni di euro, cioè 29 in più ca Jfc. «Questo fenomeno - spiega media è stata pari al +29,7%, natural- hanno introdotto ex novo l'imposta di quanto previsto e 70 oltre gli incas- Massimo Feruzzi, amministratore mente facendo riferimento ai soli di soggiorno». Per l'anno in corso, Boom per la tassa di soggiorno si del 2017. È un vero tesoro quello unico di Jfc - si deve sia ai 155 Comuni Comuni che hanno variato l'imposta. infatti, le prime previsioni di incasso incassato in Italia nell'anno appena che hanno introdotto l'imposta nel Tra questi si segnalano Firenze (che indicano una cifra complessiva pari a Nel 2018 quasi 540 milioni trascorso grazie all'imposta di sog- 2018, sia all'aumento alle tariffe ap- raggiunge la cifra record di 41 milio- 604 milioni, ma restano le criticità giorno, secondo i calcoli dell'Osserva- portato da diverse amministrazioni ni), Genova, Riccione, Matera, Jeso- sull’utilizzo di questi fondi, spesso torio nazionale sulla tassa di soggior- locali (circa dal 16%)». Per quanto lo. «Riguardo al 2019 - spiega ancora non destinati al supporto dell'attivi- no della società di consulenza turisti- riguarda l'incremento tariffario, la Feruzzi - sono ben 51 i Comuni che tà turistica. Il proclama di Zingaretti «Rinnoviamo il partito» La nomina. Il Pd ratifica il risultato delle primarie e incorona il nuovo segretario Gentiloni scelto come presidente, Zanda è il tesoriere. Apertura agli sconfitti ROMA M5S complice»; il Movimento LUCA LAVIOLA «non rappresenta più le speran- I L'incoronazione di Ni- ze che ha suscitato, ma non è cola Zingaretti a segretario del detto che i voti torneranno al Il segretario del PD, Partito Democratico avviene in Pd». -
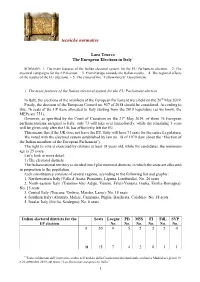
Tecniche Normative
tecniche normative Lara Trucco The European Elections in Italy* SUMMARY: 1. The main features of the Italian electoral system for the EU Parliament election. – 2. The electoral campaigns for the EP election. – 3. From Europe towards the Italian results. – 4. The regional effects of the results of the EU elections. – 5. The crises of the “Yellow-Green” Government. 1. The main features of the Italian electoral system for the EU Parliament election In Italy, the elections of the members of the European Parliament were held on the 26th May 2019. Firstly, the decision of the European Council no. 937 of 2018 should be considered. According to this, 76 seats of the EP were allocated to Italy starting from the 2019 legislature (as we know, the MEPs are 751). However, as specified by the Court of Cassation on the 21st May 2019, of these 76 European parliamentarians assigned to Italy, only 73 will take over immediately, while the remaining 3 seats will be given only after the UK has effectively left the EU. This means that if the UK does not leave the EU, Italy will have 73 seats for the entire Legislature. We voted with the electoral system established by law no. 18 of 1979 (law about the “Election of the Italian members of the European Parliament”). The right to vote is exercised by citizens at least 18 years old, while for candidates, the minimum age is 25 years. Let’s look in more detail: 1) The electoral districts The Italian national territory is divided into 5 plurinominal districts, in which the seats are allocated in proportion to the population. -

Ritorno Al Centro Di Gravità. Le Elezioni Regionali in Puglia, Tra Candidati Sicuri E Riconferma Del Bipolarismo Back to the Centre of Gravity
Regional Studies and Local Development (May. 2021) Ritorno al centro di gravità. Le elezioni regionali in Puglia, tra candidati sicuri e riconferma del bipolarismo Back to the centre of gravity. The regional elections in Apulia, between reliable candidates and the return to bipolarism Federica Cacciatore DOI: 10.14658/pupj-rsld-2021-1-7 Astract. Le elezioni svoltesi in Puglia nel settembre 2020 hanno visto un lieve aumento della partecipazione malgrado la pandemia, e la riconferma di Emiliano, presidente uscente di centrosinistra. Il suo diretto sfidante, Fitto, era sostenuto da una coalizione di centrodestra ricompattatasi dopo un decennio di spaccature interne. La sconfitta del M5s ha decretato il superamento del sistema politico tripolare emerso dalle precedenti elezioni, verso un modello bipolare favorito anche da una peculiare legge elettorale. La riconferma di Emiliano avvia il centrosinistra a compiere un ventennio alla guida della regione. La competizione elettorale si è svolta principalmente virtualmente e sui social media, anche alla luce delle misure di contenimento anti-contagio. Più ricorrenti sono state soprattutto le issues regionali, fra cui la gestione del Covid-19 da parte della giunta uscente e gli scontri col governo nazionale. Ciò, tuttavia, non ha svantaggiato il presidente uscente, conferendogli anzi ulteriore visibilità e ulteriore sostegno elettorale. Abstract. Apulian regional elections, held in September 2020, saw a slight increase in participation despite the containment measures and Emiliano’s reelection as centre-left President of the Region. His main competitor, Fitto, was supported by a centre-right coalition reunited after a decade of internal fragmentation. The Five star movement’s defeat sealed the overcoming of a tripolar political system, as it emerged in the previous elections, for the sake of a return to bipolarism, also favoured by a peculiar electoral law. -

Roberto Giachetti Ospite Di “Ci Vediamo a Via Veneto”
Roberto Giachetti ospite di “Ci vediamo a via Veneto”: emergenza coronavirus e le proposte di Italia Viva per la ripartenza L’onorevole Roberto Giachetti ospite del programma settimanale “Ci vediamo a via Veneto” per l’intervista con Chiara Rai. Una puntata, quella di sabato 16 maggio 2020 che sarà trasmessa dall’esterno dello storico locale dell’Harry’s Bar, direttamente dalla strada della “Dolce Vita”. La trasmissione, può essere seguita direttamente su questa pagina oppure su YouTube su Facebook o su Instagram a partire dalle ore 18 di Sabato 16 maggio 2020 IL CANALE YOUTUBE DI “CI VEDIAMO A VIA VENETO” CI VEDIAMO A VIA VENETO 16/05/2020 – ROBERTO GIACHETTI CI VEDIAMO A VIA VENETO 16/05/2020 – ROBERTO GIACHETTIL’onorevole Roberto Giachetti ospite a “Ci vediamo a via Veneto” per l’intervista con Chiara Rai.Una puntata, quella di sabato 16 maggio 2020 che sarà trasmessa dall’esterno dello storico locale dell’Harry’s Bar, direttamente dalla strada della “Dolce Vita”. Roberto Giachetti comincia a fare politica da giovane, nei movimenti studenteschi e poi a 18 anni nel Partito Radicale fino al 1989 (ha la doppia tessera); in quegli anni è anche redattore di Radio Radicale In seguito aderisce ai Verdi ed è eletto consigliere circoscrizionale a Roma. Dal 1993 al 2001 è prima capo della segreteria e poi capo di gabinetto del sindaco di Roma Francesco Rutelli. Viene allora incluso nel novero dei "Rutelli boys" assieme a Paolo Gentiloni, Michele Anzaldi e Filippo Sensi, in seguito sostenitori di Matteo Renzi. Nel 1999 lascia la Federazione dei Verdi e segue Rutelli nei Democratici.